NIST asserts significant influence on a number of standards. It provides a framework for security teams to identify, detect, and respond to threats. As a widely recognized security standard, it specifies guidelines for federal security systems. One of its most widely used publications is the 800 series, concerned with computer security.
In this article, we discuss what NIST compliance is, who is required to follow it, basic controls, price, and more.
What is NIST compliance?
NIST compliance is adherence to The National Institute of Standards and Technology, a U.S government agency. It lists measurable standards, develops technology, and provides metrics that aim to drive innovation and industrial competitiveness. NIST seeks to promote these in a way that boosts economic security and improves the overall quality of life.
Also, remember that NIST standards are crafted from the best practices in various security documents, organizations, and publications. They serve as a framework specifically tailored for federal agencies and programs that demand robust security measures.
NIST also helps federal agencies conform to the requirements of the Federal Information Security Management Act (FISMA), a legislation that protects government data and operations.
NIST’s core competencies include measurement of science, rigorous traceability, and development and use of standards.
History of NIST
NIST was established in 1901 and now functions within the U.S. Department of Commerce. As one of the oldest laboratories for physical science, NIST was designed to counter challenges in the industry. It aimed to boost infrastructure capabilities to match German, U.K, and other big players.
One of the key areas of its functioning was the standardization of measurements across industries. Enterprises that utilize measurement and technology in any capacity, like advanced nanomaterials, electric power grids, manufacturing, and transportation use NIST standards.
Who is required to be NIST compliant?
If you are a federal government agency, contractor, or subcontractor who manages or processes government data or operates a federal system, you should be NIST 800 171 compliant. NIST SP 800-171 is concerned with the protection of controlled unclassified information (CUI).
In other words, if your business has access to sensitive government data, you are contractually obligated to comply. It is important to know that NIST 800-181 applies to systems or networks that contain CUI.
NIST also extends to individuals or third-party government contractors to work on projects. Non-compliance or failure to self-certify can result in loss of the contract.
If you are a federal agency or government contractor operating federal systems, you should be NIST 800-53 complaint. If you provide cloud services to the federal government,
Examples of organizations that should be compliant include government staffing agencies, academic institutions, defense contractors, financial service providers, heal data processors, and manufacturers who supply to the government.
For the private sector, it is not compulsory but recommended to mature the security posture and enhance organizational procedures.
What does the NIST cybersecurity framework entail?
The NIST Cybersecurity Framework provides guidelines to secure data, thus enhancing the security of an organization. It uses a systematic approach to prevent the evils of malicious people and code. 5 functions that apply to cybersecurity risk management and your general risk in this regard are as follows.
5 core components of NIST

- Identify
- Protect
- Detect
- Respond
- Recover
Identify
The Identify function lays the ground for a robust cybersecurity program. It helps you know the cybersecurity risks to your systems, people, assets data and capabilities.
After conducting this audit and identifying the most critical systems, this core component will serve as a guideline in developing your cybersecurity strategy whereby protecting these important processes gets prime consideration.
| Identify | Which of your processes and assets need protection |
| It entails | Asset Management Business environment GovernanceRisk assessment Risk management strategy Supply chain risk management |
Protect
The NIST cyber compliance’s protect function is concentrated on protecting your business critical assets from various cybersecurity threats.
After identifying the central systems and planning a defense strategy, putting cybersecurity safeguards and practices into effect is the next important step.
This may be through communicating with your stakeholders and employees to ensure a collaborative effort in ensuring the protection of sensitive data and systems.
| Protect | Put in place the right measures to secure the company’s assets. |
| It entails | Identity Management and Access Control Awareness and Training Data SecurityMaintenance Protective Technology Information Protection Processes & Procedures |
Detect
You must implement monitoring and detection systems to spot threats as soon as possible in this function. This may include a better understanding of the company’s systems, networks and devices possibly using applications that manage or engage with data as part of regular business operations.
| Detect | Establish effective mechanisms to identify cybersecurity incidents promptly. |
| It entails | Anomalies and Events Security Continuous Monitoring Detection Processes |
Respond
In this stage, it’s time to draft a contingency or response plan if cybersecurity threats occur. You should outline methods and tools for efficient mitigation. And if you want this to work as optimally, having a dedicated cybersecurity professional team ensures that your organization will be always ready for the current and future threats.
| Respond | Create strategies to lower the impact of cybersecurity events and limit their effects on your company. |
| It entails | Response Planning Analysis Mitigation Communications Improvements |
Recover
Recovery is the last step in the NIST CSF to restore resilience after a cybersecurity incident. It involves implementing measures to bring back normal operations and reduce the impact on your operations.
For example, disaster recovery plans and business continuity plans will help you guide in the next steps in case of a successful cyberattack.
| Recover | Implementing processes and measures to bring back full functionality, ensuring a swift recovery from any disruptions caused by the incident. |
| It entails | Improvements Communications Recovery planning |
Types of NIST compliance frameworks
As per the official website of NIST, it develops and maintains an extensive collection of standards, guidelines, recommendations, and research on the security and privacy of information and information systems.
The most sought after guidelines from these publications include the cybersecurity framework, NIST 800-171, and NIST 800-53.
NIST cybersecurity framework or CSF: Offers guidelines and best practices to manage and reduce risks to their networks and applications. Divided into three parts; core, profile, and tiers, NIST CSF helps businesses with activities, outcomes, references, and approach. The core functions are divided into five activities; identify, protect, detect, respond, and recover.
Check out this video on NIST CSF 2.0
NIST 800-171 compliance: Provides guidelines to protect the confidentiality of CUI of manufacturers bound with government contracts. It comprises 110 requirements in 14 categories that include access control, security training, incident response, and audit log system.
NIST 800-53 compliance: Offers a catalog of security controls and privacy controls for US federal information systems. It specializes in risk management as per the requirements of the Federal Information Processing Standard (FIPS) 200. The control list of NIST 800 53 consists of 800-53A and 800-53B.
If you want to know more about the set of controls present in NIST 800 53, download the resource below:
Download your NIST 800 53 Controls List
How to prepare for NIST compliance?
The end goal for preparation is NIST certification. NIST does not officially certify contractors adherence against the relevant controls. There are three levels of assessment, depending on how the evaluation process was conducted.
In order to be compliant and certified, you must pass the audit round conducted by a certified third-party accredited certifying body such as the National Voluntary Laboratory Accreditation Program (NVLAP).
Here are the 4 steps you need to implement to become NIST compliant:
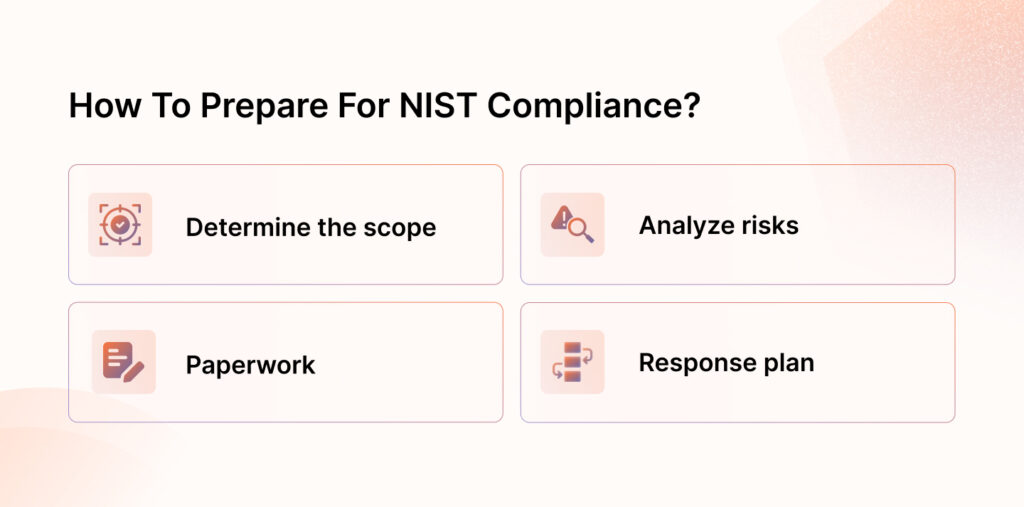
Determine the scope
Evaluate the current state of compliance. Understand what controls are already in place, what is working, where the gaps lie, and which systems should be compliant. Know where the CUI lies, the type of CUI and its flow across your infrastructure.
Paperwork
The proof is in the pudding. The chances of passing the audit lie on how well you demonstrate you are doing what you claim to. Document your systems, network architecture, where data is deployed, processes, tools, people, and changes.
Analyze risks
Section 3.11 of NIST 800 171 and 3.16 of NIST 800 53 deals with risk assessment and its remediation. NIST recommends using their seven step risk framework to meet FISMA requirements.
The steps include preparing the organization, categorizing systems and information, selecting, implementing, and assessing controls, authorizing the system, and continuously monitoring.
Response plan
Even the strongest security systems cannot detect and mitigate 100% breaches. Develop a plan to restore systems and ensure business continuity in case CUI is compromised.
Detangle the complexities of NIST compliance with Sprinto
Important of NIST compliance controls
As you already know by now, NIST publishes a huge collection of series. Of these, 800-171 is an important one that protects CUI. Heres are the 14 sections what each entails in brief:
- Access Control: Implement two factor authentication, privileged access, and secure data transfer
- Awareness And Training: Conduct security training programs and practical exercises for the same
- Audit And Accountability: Collect and review log events
- Configuration Management: Maintain a repository of approved and used system controls, implement technology to detect misconfiguration, and update system components
- Identification And Authentication: Authenticate users before establishing connection, use automated systems to manage passwords and prevent connecting to unauthorized organization systems
- Incident Response: Implement a security operations center and maintain a cyber incident response team
- Maintenance: Perform routine maintenance on systems, sanitize tools for system maintenance, and test for malicious codes before running
- Media Protection: Secure CUI media using access control, cryptographic mechanism, safe disposal, and backup
- Personnel Security: Secure systems containing CUI using individual screening and protect it during personal actions
- Physical Protection: Protect systems, operating environments, equipments and other physical facility using access control, audit logs, and more
- Risk Assessment: Conduct risk assessments to protect CUI. Scan and remediate vulnerabilities
- Security Assessment: Periodically assess and monitor security controls for vulnerabilities and efficiency
- System And Communications Protection: Monitor and protect data in transmission using access based control, network segmentation, traffic analysis, cryptography, and more.
- System And Information Integrity: Secure, protect, report, and correct system flaws
What are the benefits of NIST compliance?
NIST’s core competencies include innovation and competitiveness, but the framework offers much more than that. NIST compliance offers a number of advantages that include:
- Meet the requirements of several regulatory frameworks such as HIPAA or FISMA in a logical, sustainable, and simple manner
- Provides competitive advantages as when you are already complaint, it helps to unlock new contracts
- Secures critical systems against a range of threats like malwares, data theft, phishing, ransomwares, and more
- Enables IT teams and security administrators to efficiently detect, intercept, and mitigate threats
- Helps to reduce the impact of incidents and avoid legal complications due to lack of security compliance
NIST vs ISO vs SOC 2
With so many frameworks consisting of overlapping controls and requirements, it is natural to be confused. Which one is right for your organization? Which one aligns with your industry? What are your competitors certified with?
Let’s understand the applicability of the three most popular names in compliance: SOC 2, NIST, and ISO
| SOC 2 | NIST | ISO 27001 |
| Abbreviation of System and Organization Controls | Abbreviation of National Institute of Standards and Technology | Abbreviation of International Organization for Standardization |
| Developed by the American Institute of CPAs (AICPA) | It is an agency of the United States Department of Commerce | Developed by 67 technical committees from 25 countries |
| Recommended for service organizations who manage or process customer data. | Recommended for companies who offer a service to the US government | Recommended for any type of business who wishes to protect and secure their information assets. |
| It is not a compulsory but a voluntary compliance program | Takes about six months to be compliant | It is not mandatory, but a voluntary framework |
| SOC is an international program but is mostly used by North American organizations | NIST is meant to serve and support US based businesses | ISO is an international standard applicable to any country |
| The main purpose is to assess the internal criteria of a service organization based on five trust principles. | The main purpose is to support government contractors and subcontractors handling CUI | The main purpose is to develop, maintain, and manage Information Security Management Systems (ISMS) |
| SOC 2 attestation report process is conducted by a licensed CPA | NIST certification is provided by NVLAP through various laboratory accreditation programs (LAPs) | It is compulsory for federal agencies to process CUI data but not compulsory for other organizations |
| Takes about 6-12 to become compliant | Takes about 6 months to be compliant | Takes about 6-24 months to become compliant |
Also, check a detailed differentiation between NIST and ISO.
How much does NIST compliance cost?
Let’s clarify one thing – the total cost of compliance is not the same for all. The cost range is unique to every business and depends on a number of factors. Some of these key factors are:
Size matters: Larger organizations process and manage more tools, systems, and people, which impacts the overall cost. In general, the size is directly proportional to the expense.
Level: As per the Cybersecurity Maturity Model (CMMC), an extension of the NIST cybersecurity model, there are five levels of compliance. NIST 800-171 is equivalent to level 3. Higher the level, the greater the cost.
Current status: CMMC enables organizations to self-certify themselves if they are lagging behind. Defense contractors are likely to be already compliant. Non-compliant orgs seeking to gain certification may end up spending more.
CUI access: The goal of NIST 800-171 is to secure CUI wherever deployed. As mentioned above, the cost depends on the amount of infrastructure, processes, and people involved. Individuals, systems, and tools that do not access or process CUI don’t have to be upgraded.
Breeze through compliance with Sprinto just like our other (450+) happy customers
Challenges of NIST compliance
NIST CSF is definitely a useful tool for enhancing your system security. On the other hand, many organizations do experience some difficulties, and we can point out a few of them.

Your alignment with other standards
Your approach to compliance management depends on the standard you should meet, support of stakeholders and available resources. These elements provide the foundation to your compliance plan influencing roles, responsibilities and processes.
In this particular instance, NIST CSF is created to work with different cybersecurity standards such as ISO 27001 or PCI DSS.
However, aligning with the NIST CSF with these standards can be intricate and time-consuming, especially with multiple requirements and diverse stakeholders.
The solution is to streamline this process using tools like the NIST CSF Reference Tool or compliance automation tools like Sprinto, which help you map NIST CSF to other standards. These resources facilitate comparison, integration, and identification of any gaps that need attention.
Resistance to change
Introducing the NIST CSF, much like any organizational change, might face resistance from staff, especially if it’s seen as disrupting the workflow or adding to the workload.
Constant monitoring
NIST compliance is not a one-time task but an ongoing commitment. Organizations must consistently monitor their activities, ensuring sustained compliance.
This involves staying updated on regulatory changes, evaluating emerging risks, conducting internal audits, and promptly responding to incidents. The continuous nature of NIST management adds to the effort required.
Enter Sprinto.
Sprinto provides a centralized compliance source, showcasing maturity and ensuring accurate reporting.
With Sprinto, you’re always ready—surprises during audits become less common, allowing more focus on long-term goals. Connect with our experts to embrace smart monitoring without disrupting your workflow!
What’s Next?
For many businesses, cost, the confusing legal speak, and poor visibility into existing systems become the roadblock to compliance. Sprinto offers an all-in-one solution for businesses looking to get NIST compliant. It monitors all applicable controls, continuously scans for failing checks, documents processes for seamless audits, and much more from a centralized platform.
Say goodbye to costly security teams, manual evidence collection, and long audit processes. Connect with us today!
FAQs
What does NIST compliance mean?
NIST compliance means following the NIST standards and guidelines over time to ensure the business remains in line with regulations set by the U.S. Department of Commerce. It requires adapting to changes in vulnerabilities and the evolving cybersecurity landscape by making necessary adjustments.
What are the 5 principles of NIST?
The NIST cybersecurity framework has five core principles; Identify, Protect, Detect, Respond, and Recover.
What are NIST security standards?
Some of the most commonly used standards of NIST are NIST cybersecurity framework, NIST 800-171 compliance, and NIST 800-53 compliance.
What is the difference between NIST 800-171 and 800-53?
The key difference between NIST 800-171 and 800-53 is that 800-171 is concerned with requirements that non-federal computer systems store such as CUI, while 800-53 is concerned with federal institutions and their information systems.
Anwita
Anwita is a cybersecurity enthusiast and veteran blogger all rolled into one. Her love for everything cybersecurity started her journey into the world compliance. With multiple certifications on cybersecurity under her belt, she aims to simplify complex security related topics for all audiences. She loves to read nonfiction, listen to progressive rock, and watches sitcoms on the weekends.
Explore more
research & insights curated to help you earn a seat at the table.