A subtle shift is taking shape in cybersecurity regulation. NIS2, the European Union’s new directive, introduces obligations that may appear modest initially but have far-reaching implications for organizations across various sectors.
Slowly and almost imperceptibly, these requirements can affect every corner of operations. The question is whether teams are ready to meet this gradual rise in expectations.
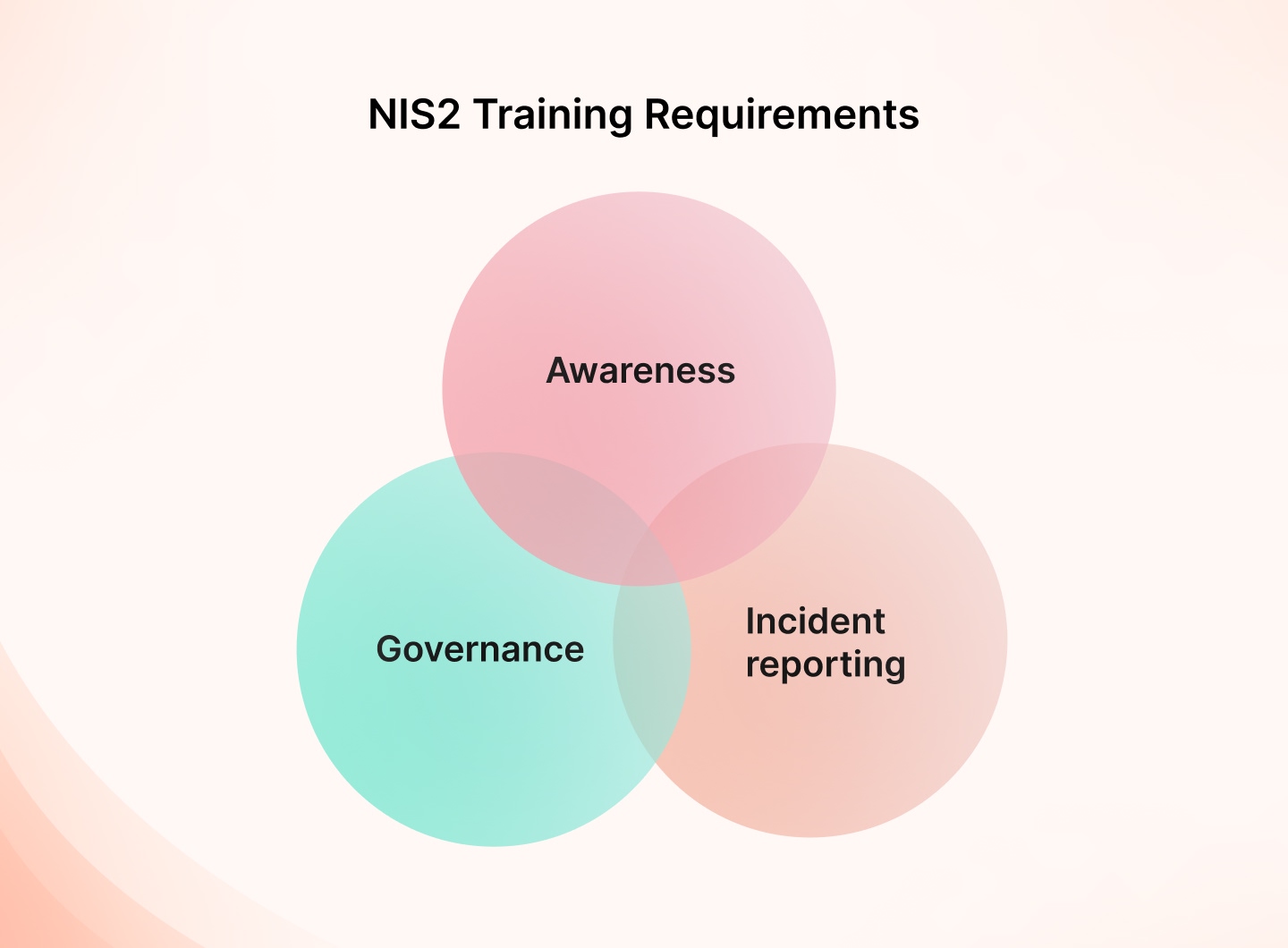
NIS2 compels organizations to adopt stronger practices, and a central component is employee training and awareness.
This blog explains what those requirements are and how to implement them effectively. Let’s dive in.
TL; DR
| What NIS2 training includes: Security basics, incident reporting, risk management |
| Who needs it: IT teams, management, third-party vendors |
| Why it’s required: Legal mandate to avoid penalties and strengthen resilience |
NIS2 Training Requirements 101
The main NIS2 training requirements are under Articles 20, 21, and 23. This ensures stronger cybersecurity measures across multiple sectors in the European Union.
Let’s take a closer look at those requirements:
1. Check key articles under the directive
The initial step is to carefully read the original text of Articles 20 and 21.
Article 20 highlights senior management’s accountability and the need for company-wide awareness programs.
Article 21 covers the technical and organizational measures, network management, access control, and incident handling. It also focuses on reporting obligations, including how quickly an organization must share alerts when an incident arises.
How to implement:
- Gather the actual text of these articles and extract each requirement.
- Create a simple chart or matrix that lists these requirements alongside the team or individual in your organization who is responsible for each line item.
- Confirm that every point in Articles 20, 21, and 23 has at least one owner in the company.
2. Map requirements to relevant roles
A requirement addressing senior management decisions goes to the board or C-suite. Cyber hygiene for everyone might look like basic instructions on password management or how to spot phishing messages.
More specialized tasks like incident handling are best suited to the IT team or security managers. This targeted approach ensures employees get only the necessary training, preventing overload.
How to implement:
- Organize a quick survey or interview process with department heads to clarify who does what.
- Match each directive’s specific requirements to a department’s daily responsibilities.
- Use color-coding to ensure it is clear which group handles which topic.
3. Plan content
Each topic should address a genuine need: governance training for executives, user-access best practices for management, and password or phishing awareness for everyone else.
The more directly the training connects to everyday tasks, the more likely employees are to engage and retain the information.
Example:
- Executive Module: A 30-minute session on accountability, decision-making about cybersecurity investments, and how to review incident reports.
- IT Technical Module: Step-by-step courses on configuring secure authentication, reviewing logs, and responding to alerts.
- General Awareness: Short videos on identifying suspicious emails, storing sensitive data correctly, and reporting incidents promptly.
How to implement:
- Draft an outline of modules: “Senior Management Responsibilities,” “Incident Handling Basics,” “Access Control Essentials,” etc.
- Validate each module’s relevance by checking it against the specific wording in Articles 20, 21, and 23.
- Aim for concise, topic-focused sessions rather than one large bundle of content.
- Choose a GRC platform that offers these courses.
4. Choose a delivery format
In-person sessions offer high interaction but can be inconvenient for large or scattered teams. Real-time online instruction (via Teams, Zoom, or similar) simplifies scheduling but fixes a single time slot.
Prerecorded videos allow employees to learn at their own pace, though questions may not receive an immediate response.
For example, a larger organization with employees scattered across multiple time zones might take a mixed approach. Complex topics like incident handling could be taught live for the IT team. Meanwhile, general awareness modules might be delivered via short, prerecorded videos for employees who work different shifts.
How to implement:
- Consider scheduling constraints. If the workforce is geographically centralized, in-person or live sessions might work.
- Where employees are widespread, incorporate on-demand modules that can be accessed at any time.
- If your employees vote for asynchronous options, set up a “Q&A hour” or an online forum to ensure that employees can still clarify concerns.
5. Determine frequency and duration
Specialized sessions involving heavy discussion might span half a day or more. General instruction can be split into shorter modules, released incrementally over weeks or months.
Hence, consistent reinforcement helps sustain awareness without overwhelming the schedule.
How to implement:
- Examine the depth of each topic. Technical or high-level governance issues may need extended workshops.
- Break common topics (like social engineering risks) into 5–15-minute videos.
- Create a content calendar to ensure the systematic release of modules weekly, biweekly, or monthly, depending on their complexity.
6. Use a Learning Management System (LMS)
An LMS organizes training material, tracks completion, and can handle tests. Automatic reminders reduce the administrative load and provide a standardized learning experience.
For example, many platforms let users assign training paths. The IT team might receive an “Advanced Security” track, while the general workforce sees a “Security Essentials” playlist. A management dashboard shows who completed which module, along with quiz scores.
How to implement:
- Compare available LMS platforms; look for features like automated notification emails, progress tracking, and grouping users by department or seniority level.
- Set up different modules based on the role matrix.
- Activate reporting features so the compliance officer can retrieve proof of training anytime.
7. Incorporate testing and feedback
Short tests or scenario-based challenges help confirm that employees understand each requirement.
You can have feedback sessions, in-person or in writing, to highlight any existing gaps.
For example, after a short video on phishing, employees answer a three-question quiz: “Which of these email subjects look suspicious?” “What steps do you take if you accidentally click on a malicious link?” This tells you whether they absorbed the content.
How to implement:
- Build quizzes at the end of each module. Keep them brief.
- Encourage open communication. If staff repeatedly fail certain questions, review the content or offer an FAQ session.
- Track test results in the LMS for compliance audits.
8. Maintain evidence of compliance
Article 20 explicitly states that management must oversee these measures. Keeping thorough records shows that the directive’s training aspect has been honored.
Proof of attendance and quiz results can be critical if regulators request documentation.
How to implement:
- Log every participant’s attendance, quiz scores, and completion dates.
- Centralize documents so they can be shared or exported without complications.
- Revisit the records regularly to ensure nothing is missing or inaccurate.
9. Review and update regularly
Threat landscapes evolve, and regulations can shift. An ongoing review ensures the training stays relevant and the company is prepared for emerging requirements. Any updates to NIS2 should immediately be reflected in the training materials.
How to implement:
- Schedule a formal review, perhaps annually, to assess whether the topics and materials need revising.
- Monitor cybersecurity news or bulletins for noteworthy threats that should be included.
- Stay in contact with industry peers to see how others adapt. This will allow you to factor any best practices into internal sessions.
Get access to a security training program worth $10,000+ in the bundle
How do you obtain an official certification?
There are two distinct routes that one can take to obtain an official certification. The first revolves around independent study and ends with an online exam. Those who pass earn a certificate that demonstrates measurable knowledge of the directive’s key principles.
The second path opts for a more direct approach: instructor-led training, either at your own site or via live virtual sessions, covering core content in real-time.
The other route involves instructor-led sessions in person at your workplace or through live online classes.
Each path matches different learning preferences, whether you favor independent study or value real-time interaction. Whichever option fits best results in a credential that highlights your professional grasp of cybersecurity and compliance.
Option 1: Distance learning with a certificate of completion
An online study track culminating in an exam leads to recognition as a NIS2 Directive Trained Professional (NIS2DTP). This course is structured to clearly understand NIS2 Directive requirements and provide practical methods for supporting compliance.
Participants who complete the exam receive a Certificate of Completion, reflecting measurable knowledge of the directive’s provisions.
Further details are available here.
Option 2: In-house instructor-led sessions or online live training
This option brings experienced trainers to your workspace or delivers live instruction virtually.
The content is easily adapted to specific needs, offering maximum interactivity through real-time discussions and Q&A.
Possible modules in a tailor-made program
Introduction
- Explanation of the NIS2 Directive Trained Professional (NIS2DTP) exam requirements
- Overview of the Certificate of Completion and how it benefits career paths
Part 1: Context of the European Union Legislative Process
- Key EU Institutions
Explores the roles of bodies such as the European Commission, European Data Protection Supervisor, and European External Action Service. - Legislative Framework
Examines how laws, delegated acts, and technical standards are formed under the Treaty of Lisbon. - Supervision and Oversight
Covers agencies like the European System of Financial Supervision (ESFS), Committee of European Auditing Oversight Bodies (CEAOB), and others involved in shaping and monitoring regulatory compliance. - Security and Defence
Reviews the Common Foreign and Security Policy (CFSP), Common Security and Defence Policy (CSDP), and specialized initiatives like the European Multidisciplinary Platform Against Criminal Threats (EMPACT). - Cyber-Specific Initiatives
Introduces ENISA (the EU Agency for Cybersecurity), TIBER-EU for threat intelligence exercises, and CIISI-EU for intelligence sharing.
Part 2: Foundations of EU Cyber Resilience and the NIS Directive
- EU Strategy for a Secure Cyberspace
Outlines five critical aims: building cyber resilience, reducing cybercrime, and fostering industrial and technological cybersecurity capabilities. - NIS Directive (EU 2016/1148)
Reviews this first EU-wide cybersecurity legislation, detailing national capabilities, cross-border collaboration, and methods of supervising critical sectors. - NIS Directive Cooperation Group
Focuses on the role and significance of the collaboration framework that facilitates joint cyber initiatives across Member States.
Part 3: Introducing the NIS2 Directive
- General vs. Special Laws
Explains how NIS2 operates as a broad requirement (lex generalis) and what this entails when specific sectoral laws (lex specialis) are already in place. - Interactions with Other Regulations
Discusses the Digital Operational Resilience Act (DORA), the Critical Entities Resilience Directive (CER), and the General Data Protection Regulation (GDPR). - Scope and Structure
Examines Annex I (sectors of high criticality) and Annex II (other critical sectors), emphasizing how these lists shape compliance obligations.
Source: NIS2 Directive training
NIS2 Training: Need a Helping Hand
Kaspersky’s research points toward worrying trends—misusing IT resources and ignoring security measures remain some of the biggest dangers. A single incident can cost an organization an average of $337,561.
The data also suggests that 38% of cyber incidents stem from honest human mistakes, while 26% result from violations of security policies.
Adopting a strong security awareness program can address these concerns. It lowers the frequency of breaches tied to human error, reduces response costs, and helps everyone learn to safeguard client information and browse online safely. NIS2 underscores these goals by demanding serious attention to compliance.
Sprinto’s built-in security training modules and the option for tailored training campaigns streamline awareness and compliance organization-wide. Their course catalog supports teams by providing straightforward sessions, while integrations with leading training platforms centralize tracking and monitoring.
Don’t get bogged down by NIS2’s complexities. See Sprinto in action. Talk to our experts for more.
Meeba Gracy
Meeba, an ISC2-certified cybersecurity specialist, passionately decodes and delivers impactful content on compliance and complex digital security matters. Adept at transforming intricate concepts into accessible insights, she’s committed to enlightening readers. Off the clock, she can be found with her nose in the latest thriller novel or exploring new haunts in the city.
Explore more
research & insights curated to help you earn a seat at the table.


























