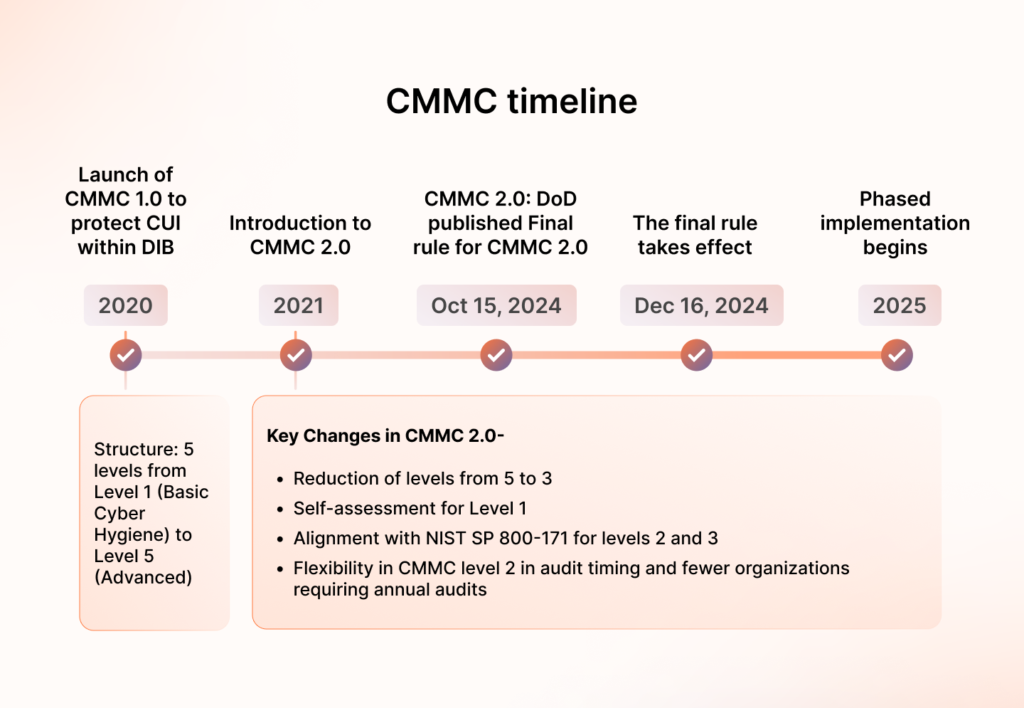
With the official publication of the CMMC 2.0 final rule taking effect on December 16, 2024, contractors now have the much-needed nuance on the requirements. The phased implementation is set to begin in 2025 and gives you time but make no mistake—the clock is really ticking. The US Department of Defense (DoD) offered contracts worth $456 billion for FY2023, and you really don’t want to miss such promising avenues due to non-compliance. The best time to prepare for the CMMC audit is now; we’re here to help.
This blog will help you easily navigate the CMMC audit intricacies, including the pre-audit engagements, auditor checklists, best practices, and even the post-audit actions.
TL;DR
| Get clarity on assessment methodology, timeline, and other expectations from your C3PAO before the audit |
| Key best practices include closing the POA&M, working on documentation, staying transparent, focusing on NIST SP 800-171, building a security culture, and collaborating transparently |
| Post-audit, work on improvements, wait for the certification approval, and continuously monitor and maintain for reassessment |
CMMC Audits at a Glance
Developed by the DOD, the Cybersecurity Maturity Model Certification (CMMC) is a framework mandated by the government for defense contractors. It ensures that organizations working with the Defense Industrial Base (DIB) implement robust cybersecurity practices to protect Controlled Unclassified Information (CUI) from cyber threats and attacks.
CMMC builds upon the NIST SP 800-171 requirements while adding additional measures to ensure comprehensive protection. It defines multiple cybersecurity maturity levels, from foundational to advanced, depending on the risks associated with various types of contractors.
Overview of CMMC audits
CMMC audits are independent assessments conducted by a Certified Third-Party Assessor Organization (C3PAO) that assess the cybersecurity posture of the contractor. The process usually involves:
- Self-assessments and Preparation: Organizations evaluate their current cybersecurity practices and implement measures to remediate the gaps and achieve the desired maturity level
- Audit: The C3PAO reviews documents, tests control implementation, and evaluates practices against the compliance requirements
- Final Report and Certification: The assessor compiles and submits a report to the accreditation body. Upon successful review, the Organization Seeking Compliance (OSC) is awarded the certification, valid for three years
Here is Jacob Hill from GRC Academy walking us through the requirements of CMMC:
Setting up for Success: Pre-Audit Engagements
Think of pre-audit engagements as setting the stage for the CMMC audit. They ensure that both parties’ expectations are aligned and that there is agreement on scope, methodology, and timelines.
Here’s what happens during the session:
Initial kick-off meeting
The initial meeting is between the organization’s representatives (mainly from the C-suite), key personnel (including the CISO, IT staff, and compliance officers), and the C3PAO’s representatives. It aims to give a quick rundown of the organization’s business, the type of information it deals with, and the key point of contact for the assessment.
Interview the C3PAO (Why not?)
Organizations often believe that the assessors are the only ones who should interview the company. But it must be a two-way conversation, and you must ask the assessor about the approach and methodology they’ll use, the assessment duration, and the remediation expectations, if any.
Define the scope of the assessment
The pre-audit engagements also include discussions about the scope of the assessment. Both parties must sync on the system boundaries, processes, and areas that will be covered under the evaluation, and any exclusions must also be discussed along with the reasons for them.
Discuss self-assessment review
The organization can also discuss key points from self-assessment before a formal audit to provide more context to the assessor and to demonstrate that necessary actions have been taken to close the existing gaps.
Continuously track controls with Sprinto
Your CMMC audit checklist: What auditors will review?
The next step is to understand what the auditor will expect during the assessment. We’ve got you the CMMC audit checklist for this.
But before we dive in, note that a level 1 certification is a minimum requirement for a DoD contract, which can be achieved with an annual self-attestation.
Level 2 certifications are generally performed by C3PAO and level 3 certifications require government-led assessments.
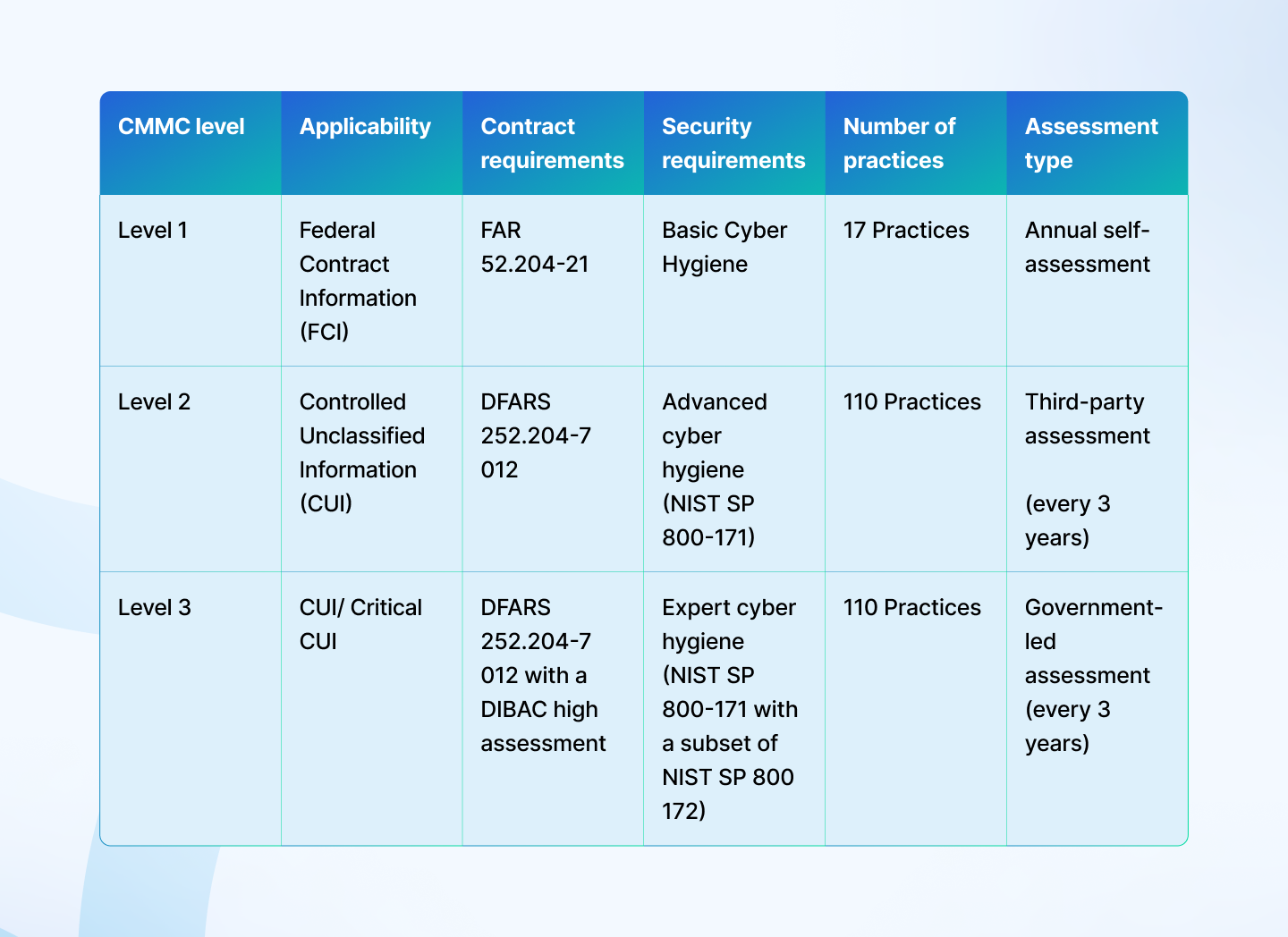
Let’s talk about level 2 and 3 audits here. Broadly, the auditor wants to understand the following:
- Does the organization have the necessary documentation and document enforcement in place?
- Are there proper governance structures in place?
- How well are the employees trained?
- Are the necessary controls implemented and regularly tested?
- What is the organization’s level of disaster preparedness?
- Are gaps identified and corrective actions initiated?
For this, the auditor will verify documents, conduct interviews, make observations, and test controls in-depth.
Following is the checklist of documents that you must have in place:
General documentation
- Cybersecurity policies aligned to CMMC
- System Security Plan
- Plan of Action and Milestone
- Risk assessment report
For the rest of the documents, you can refer to the table below aligned to CMMC 2.0 controls:
| CMMC Domain | Relevant documents |
| Access Control (AC) | Access control policies Implementation of Role-based Access Control (RBAC) Multi-factor authentication (MFA) Access logs and reviews |
| Audit and Accountability (AU) | Audit policies and procedures Audit Log Retention |
| Awareness and Training | Evidence of employee awareness training (policies, records, completion rates etc.) |
| Configuration Management | Baseline configurations Change management process Software version control policy |
| Identification and Authentication | Identification and authentication procedures Password management policies |
| Incident Response | Incident response plan Evidence of IRP testing Communication plan in case of an incident Post-incident reports |
| Maintenance | Maintenance procedure documents |
| Media Protection | Procedure for handling sensitive data on the media device Encryption standards Procedure for media disposal |
| Physical Protection | Access management for physical facilities Surveillance mechanisms Visitor management |
| Personnel Security | Background checks Processes for onboarding and termination |
| Risk Assessment | Risk management methods and results Risk mitigation strategies |
| Security Assessment | Policies for periodic assessments Pen test results Third-party assessment results |
| Systems and Communications Protection | Network segmentation Encryption for data in transit and at rest Secure system development practices |
| Systems and Information Integrity | Vulnerability and patch management procedures Malware protection system evidence |
Note that this may not be an extensive list, and the requirements may vary based on the contractor’s information and business.

Proven CMMC Audit Best Practices for Excellence
A successful audit requires more than meeting a list of technical requirements—it demands strategic planning and execution and a commitment to cybersecurity. Industry best practices can help set the foundation of the process and help you breeze through audits.
Following are the only CMMC audit best practices you need:
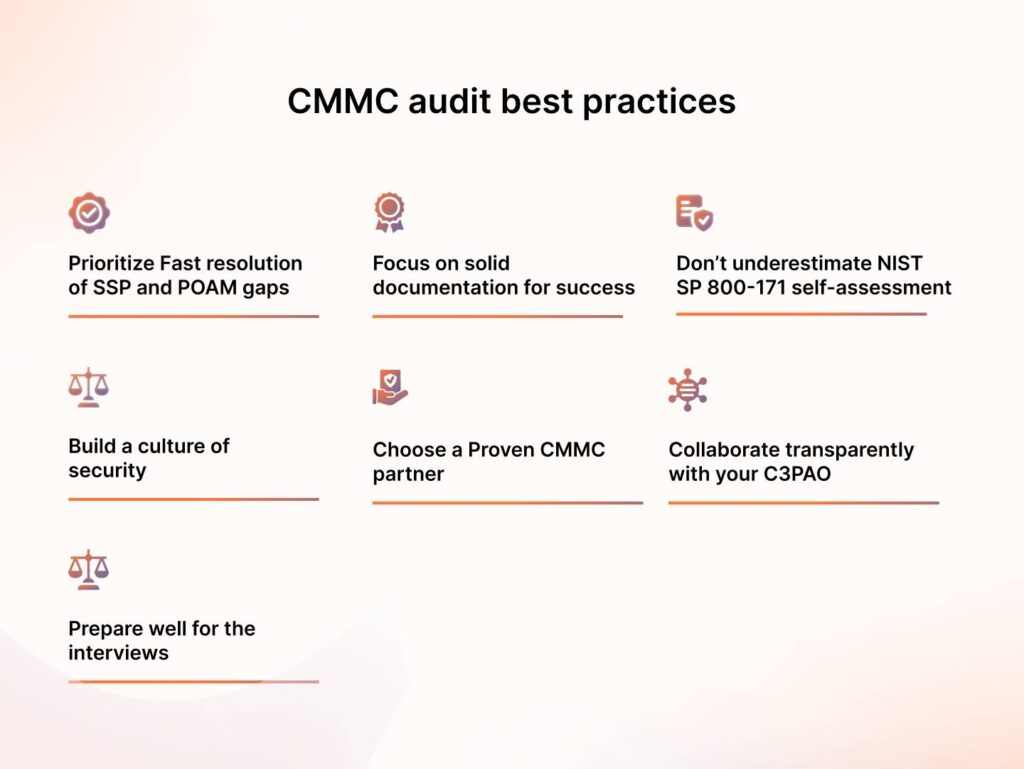
1. Prioritize Fast resolution of SSP and POAM gaps
Your System and Security Plan (SSP) and Plan of Actions and Milestones (POAM) must be on point with minimal to no deficiencies. For a level 2 audit, this means around 330+ assessment points, which can be pretty comprehensive. The deficiency resolution must not take more than 180 days, no matter the organization’s size. If anything is not being closed, it must be removed from the SSP or POAM (at the time of pre-assessments) so you don’t attract fines or additional on-site visits.
2. Focus on solid documentation for success
The auditors spend much time on documentation—Standard Operating Procedures (SOPs), training plans, incident response plans, network diagrams, and more. It is best to ensure everything’s on point during the internal assessments to avoid back-and-forth with the auditor and to demonstrate that you respect their time and yours.
3. Don’t underestimate NIST SP 800-171 self-assessment
Defense contractors must submit a self-assessment of NIST SP 800-171 compliance and report the Supplier Performance Risk System (SPRS) score to the DoD. A CMMC level 2 audit requires a score of 88/110 to pass. However, your goal should be to achieve the maximum possible score, as the NIST 800-171 will help you win half the audit battle. It’ll enable you to close the deficiencies well in advance, and the CMMC audit process will become relatively smoother.
4. Build a culture of security
A culture of security differentiates sustainable compliance programs from checklist-based adherence. Ensure that security measures are embraced org-wide and not just by IT teams. Practices like password management or secure communication must be integrated into daily operations to minimize human errors and create a sense of accountability.
5. Choose a Proven CMMC partner
Working with someone who has walked the walk will save time and effort and minimize stress and ambiguity. Most organizations struggle with championing the gap analysis, getting the documentation right, and implementing the right controls. A CMMC expert can fast-track this process as they are familiar with it, reducing the timeline for gap analysis from months to days and helping with custom document templates and guided implementation.
6. Collaborate transparently with your C3PAO
When engaging with a C3PAO before the final assessment, you must have an OSC point of contact so they do not have to find different people for the same communication. Next, contractual agreements must specify an anticipated timeline and cost for clarity between the parties, along with an NDA (non-disclosure agreement). Lastly, the OSC must not try to hide anything under the cover—staying transparent with the assessor will help you get to the certification stage faster. We promise they are equally invested in getting you certified!
7. Prepare well for the interviews
Have a set of people designated for the audit interviews—individuals who understand the company and its processes. Ensure they provide concise and accurate answers to common questions, but avoid making responses sound scripted. Well-prepared participants can significantly enhance the audit process.
Maximize savings on your CMMC audit
CMMC Post-audit actions
What happens once the C3PAO is done with the assessment? Let’s find out:
You address the feedback
The assessor’s report contains feedback on identified gaps and deficiencies. The organization must address these concerns and submit a POA&M if significant corrective actions are required. These may involve updating policies, enhancing controls, or reworking training programs. Once the gaps are addressed, you may be required to submit evidence of remediation.
Wait for certification confirmation
The C3PAO will then submit the report findings to the CMMC accreditation body (also known as Cyber AB) for final review and approval. The assessing body may take a few weeks to confirm the certification formally. Stay in touch with the C3PAO during the process for any follow-ups and clarifications.
Continuously monitor and maintain
Implement a continuous monitoring mechanism to stay compliant and set up automated alerts to address any deviations quickly. Conduct regular internal audits to maintain compliance, as any failure can lead to cybersecurity incidents, contractual breaches, loss of certification, and damage to reputation.
Prepare for reassessment
The CMMC certification is valid for 3 years, and you must ensure continuous compliance to stay prepared for reassessments. Proactively address any gaps, changes to processes, or regulatory requirement updates to ensure sustained output with minimal inputs.
Switch to an Automation-led enablement with Sprinto
The CMMC cybersecurity framework is all about reducing risks across the defense supply chain, but let’s be honest—it can feel pretty overwhelming. Between meeting stringent security standards and juggling costs and admin work, it’s a lot for contractors to handle. That’s why so many turn to experts and automated tools to make the process easier.
If you want to eliminate CMMC implementation’s stress, Sprinto’s got you covered. Our platform helps you set up a security plan that aligns with NIST standards, automates risk assessments, and monitors your environment to catch threats early and ensure ongoing compliance. It even runs control tests to spot anomalies, making collecting evidence for corrective actions a breeze.
The best part? Sprinto frees up your engineering team so they can focus on what really matters—mission-critical tasks.
Can Sprinto make CMMC compliance simpler? Let’s hop on a call and chat!
FAQS
Do subcontractors on a DoD contract also need CMMC certification?
Yes, if the subcontractors on the DoD contract handle Federal Contract Information (FCI) or Controlled Unclassified Information (CUI), a CMMC certification is required. However, the CMMC level depends on the information type and the main contractor’s requirements.
How long does it take to achieve CMMC certification?
The CMMC certification can take anywhere from 6 to 18 months (preparation, remediation, and formal assessment), depending on the CMMC level, the current cybersecurity posture, and the complexity of operations.
What are the rules for Cloud Service Providers (CSPs) and External Service Providers (ESPs) under CMMC?
If the CSPs and ESPs handle FCI or CUI, they must abide by specific rules under CMMC:
- A CSP handling CUI must be FedRAMP moderate or equivalent compliant for DoD requirements
- The providers must have the ability to protect data as per NIST SP 800-171
- Subcontractors handling CUI must meet the exact requirements as contractors and align with the required CMMC level
- Managed Service providers and CSPs must have an updated SSP and incident response plan
- A contractual agreement must include the providers’ responsibilities, and the organizations must ensure that they have the required security controls.
Payal Wadhwa
Payal is your friendly neighborhood compliance whiz who is also ISC2 certified! She turns perplexing compliance lingo into actionable advice about keeping your digital business safe and savvy. When she isn’t saving virtual worlds, she’s penning down poetic musings or lighting up local open mics. Cyber savvy by day, poet by night!
Explore more
research & insights curated to help you earn a seat at the table.






















