November 12, 2021. A former South Georgia Medical Center employee made an unauthorized copy of a patient’s private data before leaving the company. The center had to provide patients with free credit monitoring and identity restoration to compensate for the disgruntled ex-employee’s actions.
While this is the case of a malicious insider, there are other incidents where negligent users or attackers compromise the integrity of user credentials and data. Anyone with authorized access to an organization’s data and systems is a potential threat. That is why having a formal access review system is crucial.
This blog discusses access reviews’ importance, how the user access review process works, and the everyday challenges. Read on to also find out how you can save 80% of your cost and time.
What is access review?
Access review is the process of evaluating the privileges and permissions granted to employees of a company with respect to sensitive information and assets of the organization. The review process involves assessing individuals, user groups, and third-party vendors on access levels and aims at minimizing the risk of unauthorized or inappropriate data usage.
Why are access reviews important?
Access reviews are important to ensure minimum interactions with critical assets by keeping an eye on permissions and privileges. Regular access reviews minimize security risks posed by insider threats and also ensure compliance.
More often than not, humans are the weakest link in cybersecurity. According to a report by Verizon, 20% of data breaches are carried out by business insiders because of poor access management. This is mostly attributed to excessive or mismanaged permissions. Another threat report published by Palo Alto Networks found that 99% of cloud users had excessive permissions. With that in mind, here are some reasons why access reviews are important.
Promoting data security
Leaving sensitive information exposed to unnecessary individuals can lead to data breaches. Regular access reviews ensure that access is granted to the right individuals as per their job functions and reduce the attack surface area.
Meeting compliance requirements
Regulatory standards and compliance frameworks like HIPAA, PCI DSS, GDPR, and ISO 27001 require periodic access reviews. Not carrying them out can attract fines and other repercussions.
Preventing privilege exploitation
Review of access rights prevents:
Privilege creep: Privilege creep is the accumulation of unnecessary access rights because new rights are granted without removing old permissions. An example could be temporary access given to an employee for a specific project that was not revoked later.
Privilege misuse: Privilege misuse occurs when an individual tries to use the permissive settings for a malicious or unethical purpose. This could be intentional or unintentional (out of negligence). For example, viewing sensitive patient information that employees are not authorized to view.
Abuse of privilege: Privilege abuse is an intentional and fraudulent exploitation of access rights that aims to harm others or bypass ethical standards. For example, stealing credentials to tamper with critical data.
Third-party risk management
Access reviews involve regularly monitoring the access granted to third-party vendors and applications. Any overly permissive setting that goes beyond contractual obligations could lead to a cyber incident.
When should you use access review?
Access reviews should be ingrained into the organization’s security and compliance mandate. Carry out access reviews during the following situations:
- When there are a large number of administrators with special privileges
- At the time of onboarding and offboarding
- When there are changes in job roles/promotions
- In case of significant changes in policies/business structure/operations/technology infrastructure
- Periodically, during internal audits and for compliance adherence
How does the access review process work?
The user access review procedure is a structured set of steps to validate access rights and privileges. The existing practices are analyzed against a formalized access policy, and access controls are implemented. These are regularly reviewed to identify any further gaps and ensure ongoing improvement.
Here’s how the user access review procedure works:
1. Create an access management policy
The access management policy should broadly cover the following aspects:
- Data, systems, and applications under access review scope
- Define roles and responsibilities and map them to the level of permissions (read-only, admins, etc.)
- Access control protocols that must be in place
- Requirements for authentication, authorization, and raising access request tickets
- Access revocation process
- Frequency and access review period
- Documentation requirements
There should be a periodic management review of the policy, and it must be updated to accommodate regulatory or business context changes.
2. Begin the access assessment
After defining the policy, assess the current state of employee access rights. Check whether every job function within the scope has been granted the minimum required access for carrying out their respective operations. Also look for hidden admins, access to dead accounts or ex-employees, privilege changes because of changes in job roles, and other critical aspects.
3. Train the workforce
Security awareness training related to access management must be arranged for the workforce. The training should cover access management best practices, access control procedures, raising access requests, compliance requirements, and non-compliance repercussions.
4. Implement user access review controls
Revoke access permissions for ex-employees, dead accounts, and hidden admins discovered above. Implement role-based user access review controls to eliminate the need for manually checking permissions mapped to job configurations. Also ensure the principle of least privilege is followed where employees are granted minimum permissions to carry out their job functions effectively.
5. Document results and ensure improvement
Regularly analyze if the issues identified in the assessment have been rectified and the access controls have been implemented as a part of the procedure. Document the review results and identify opportunities for further improvement.
Types of access review
There are different ways to look at user access review classification. We have segregated the types on the basis of time and level of permissions.
Based on time:
Periodic user access reviews: A periodic user access review is carried out regularly and is intended for compliance purposes. For example, Annex 5.18 under ISO 27001:2022 talks about access rights and requires the level of access to be in accordance with the access control policy. This should be reviewed regularly and aligned with the segregation of duties. So, the periodic access review process includes:
- Defining the scope of review
- Generating a user list to map with the scope
- Validating access rights and permissions with job responsibilities
Continuous user access reviews: Continuous user access review involves real-time monitoring of access rights and permissions to ensure no security breaches or unauthorized intrusions. The primary goal is maintaining a strong security posture and minimizing access rights risk.
It is conducted continuously to monitor the enforcement of security policies and raise alerts for events that require attention. While the approaches are distinct, they complement each other and must be used together.
Based on permission levels:
Role-based access review: This user access review ensures access rights are mapped to the suitable job functions. The review is mainly carried out for employees in the organization.
Privileged access review: Privileged access review is carried out for system administrators, team leaders, IT staff, etc., who have been granted special privileges.
Third-party access review: Third-party access review verifies and validates the permissions granted to third-party vendors and applications who have access to sensitive company data. The access rights should be minimum necessary and must not extend beyond contractual obligations.
The challenges of access review
Access reviews are seen as daunting because they involve a large volume of data across complicated environments. If the roles and responsibilities are not segregated well, it becomes a significant administrative burden. Maintaining documents for audit purposes can also feel challenging when done manually.
Here are 4 common challenges organizations face during access reviews:
Time and resource-intensive
Access reviews can require a lot of bandwidth and resources if done manually. There has to be a step-by-step validation of users and permissions to ensure data accuracy. Also, defining the scope of items under access review and complex cases can require thorough investigation, which can be time and cost-demanding.
Multifaceted infrastructure
With the sophistication of the digital world on the rise, IT infrastructure has become complex and multifaceted. Reviewing access to multiple systems, applications, databases, and other key information assets can feel exhaustive and energy-draining. This is often called identity governance fatigue.
Too many users and permissions
Large organizations have a massive volume of users and permissions. This includes both insider and third-party permissions and can be time-consuming. Additionally, there can be resistance from user groups because it is often a repetitive exercise to manage a large set of permissions.
Frequent changes in roles
New onboarding, offboarding, promotions, and special projects may require continuous access reviews. It can be hard to manage these frequent permission changes and record updates.
How to automate user access review?
Manual methods of access review, as mentioned above, can lead to delays. Misses can result in errors if permissions are granted without thorough vetting. The best way to take away the administrative burden and ensure accuracy is to automate user access reviews.
Here are the 5 steps to automate access reviews:
1. Determine objectives
Determine the scope and objectives of the access review. Is the objective short-term compliance or long-term security? Make a list of systems, applications etc. that must be considered for access review.
2. Choose an automation tool
Based on the decided outcomes, create a list of automated tools and undergo demos or free trials to understand key features and pricing. If the goal is to achieve compliance and security, choose a comprehensive compliance automation tool over an Identity and access management platform. Choosing the right IAM tool depends on how it complements other tools within the tech stack such as cloud service providers or endpoint management solutions.
3. Integrate
Integrate your critical assets with the software so that it can access the required data related to access rights and permissions. This enables the software to run checks on these assets throughout the day and send alerts in case of any deviation.
4. Establish roles and responsibilities
Define various job functions and responsibilities and create critical system owners. Define the people for whom the access is valid. This further helps in enforcing login protection mechanisms, multi-factor authentication, etc.
5. Add workflows and track results
While the software will continuously monitor access rights, you can also add automated workflows for periodic reviews. Set a frequency, assign a reviewer, and check the evidence.
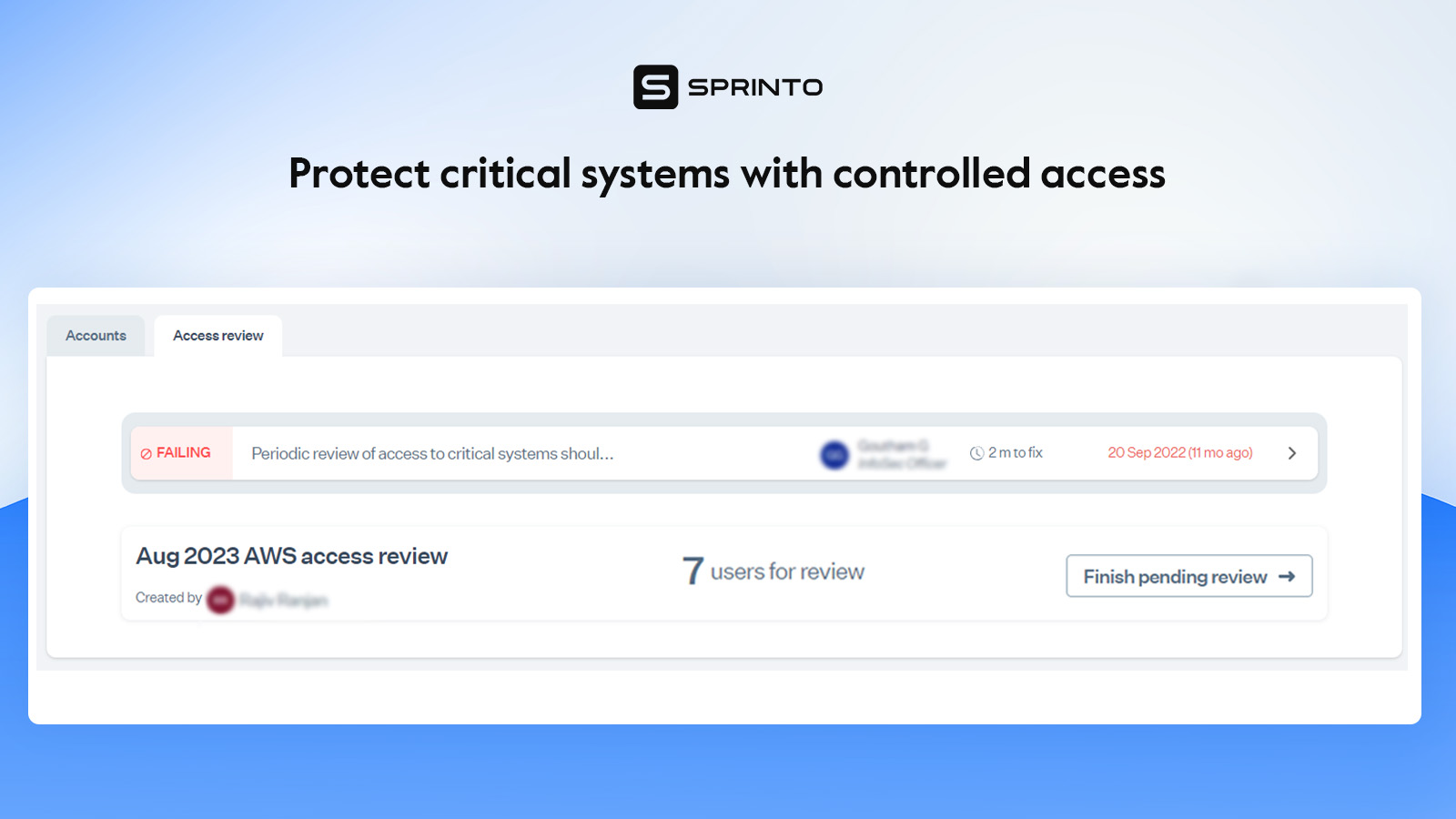
How Sprinto automates user access review process:
- Sprinto automatically suggests which critical systems must be a part of access reviews. You can also add other critical systems and avail access review support for manually managed systems.
- It has in-built access management and role-based user access review controls to simplify segregating duties and managing rights.
- Sprinto supports integration with other IAM (Identity and access management) tools.
- 24/7 monitoring of access granted to critical systems provides real-time insights.
- Sprinto sends alerts for revoking access at the time of employee offboarding.
- You can create automated workflows for periodic access reviews.
- There’s automated evidence collection of access reviews.
Automate user access reviews with Sprinto
Access reviews are a business essential. They enhance security, help meet compliance requirements, and mitigate cyber risks, speeding up the sales cycle. However, they can be challenging in practice when done manually.
Sprinto automates the user access review process and addresses these challenges, as we highlighted above. Just add your critical systems, assign job roles and get started to put access management on autopilot. Remove the guesswork from security and compliance operations. Speak to our compliance experts today to understand how you can manage access reviews and expand the scope of your compliance program.
Check out the complete review of Sprinto.
FAQs
How often should access be reviewed?
This can depend on various factors like the size and complexity of the organization, regulatory requirements, security maturity, etc. The general recommendation for IT access reviews is at least once a quarter and overall access reviews at least annually (for small-scale businesses). Reviews should also be conducted in case of events like security incidents, infrastructural changes, etc.
What is least privilege?
Least privilege suggests granting the minimum access required to execute job functions. This reduces attack surface area and minimizes risk of data breaches while ensuring practical functionality.
What are some best practices for managing access reviews?
Best practices for managing access reviews include:
- Regularly reviewing and updating access policies.
- Implementing role-based access controls.
- Maintaining adequate documentation.
- Training the workforce.
- Involving key stakeholders to create a structured process around access reviews.
Payal Wadhwa
Payal is your friendly neighborhood compliance whiz who is also ISC2 certified! She turns perplexing compliance lingo into actionable advice about keeping your digital business safe and savvy. When she isn’t saving virtual worlds, she’s penning down poetic musings or lighting up local open mics. Cyber savvy by day, poet by night!
Explore more
research & insights curated to help you earn a seat at the table.