What are Metrics & KPIs in Cyber security – Detailed Guide

As a seasoned security professional, you understand the struggles of convincing the board to approve an increase in the cybersecurity budget or obtain that data privacy compliance certification. You are also familiar with the perplexed faces of non-technical stakeholders when emphasizing the importance of cybersecurity best practices.
Edwards Heming aptly states, “Without data, you’re just another person with an opinion.” This is why cybersecurity metrics and KPIs make communicating the value of security efforts easier. They substantiate your observations, requests, and claims with numbers and are essential to drive action.
This blog provides an exhaustive list of cybersecurity metrics that organizations can track to proactively address cyber threats and progress toward becoming a resilient organization.
What are cybersecurity metrics?
Cybersecurity metrics are quantifiable measurements that provide insights into the strength of internal controls and the effectiveness of security best practices. These performance or risk indicators are tracked periodically, laying the foundation for strategic decisions.
How are cybersecurity metrics helpful?
Cybersecurity metrics can be helpful when communicating the security goals to the key stakeholders. Metrics help establish a baseline for benchmarking and evaluating performance. These also help with making more informed choices to power your cybersecurity program and demonstrate regulatory adherence.
Here are 4 reasons why cybersecurity metrics are helpful:

1. Understanding risk profile
Several cybersecurity metrics are key risk indicators, such as the number of pending patch updates, intrusion attempts, phishing click-through rates, etc. These metrics help organizations understand the risk profile and create a risk matrix for prioritizing efforts toward high-impact items.
2. Performance analysis
The cybersecurity KPIs, such as training completion rates and authentication success rates, help assess the effectiveness of cybersecurity practices. These metrics also serve as the baseline for facilitating monthly, quarterly, or annual comparisons to understand improvements over a period.
3. Compliance reporting
Cybersecurity metrics can serve as evidence to demonstrate adherence to security policies. For example, you can present compliance metrics like mean time to detect (MTTD) and mean time to respond (MTTR) for standards that necessitate proactive redressal of incidents.
4. Decision-making and improvement
Cybersecurity metrics facilitate data-backed decisions concerning various areas surrounding cybersecurity. They guide the next strategic move for improvement by laying the foundation for informed decisions such as policies that need to be updated, security controls that require to be tightened, new initiatives to be undertaken, resource allocation, and more.
List of cybersecurity metrics and KPIs
The choice of cyber security metrics and KPIs dictates your focus for the next set of security initiatives so it must be made with due diligence. Select the metrics that best align with your security objectives, and never get tempted to measure everything.
Here’s a list of 22 cyber security KPI examples that you can track for your organization:
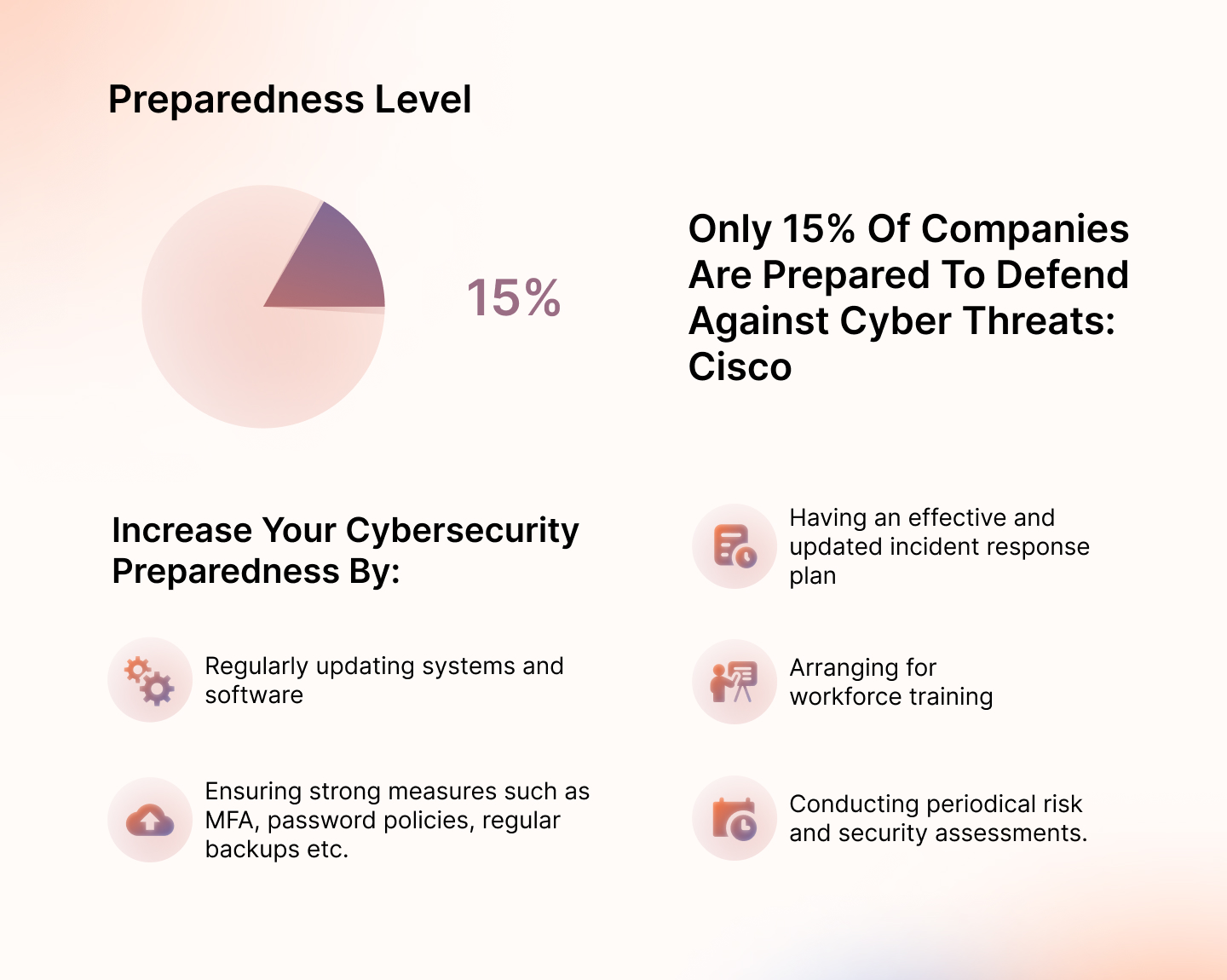
1. Preparedness Level
The preparedness level metric assesses an organization’s readiness against cyber incidents and attacks. It ensures an organization is fully equipped to respond and recover from a security event. You must review the following, for example, to evaluate the level of preparedness:
- Number of devices on the network that are fully patched
- Security awareness training completion rate
- Number of high-risk vulnerabilities identified
- Number of devices and software that are continuously updated
- Number of policies that are periodically updated
- Frequency of backups
- Time taken to identify and resolve incidents
- Frequency of security assessments etc.
These KPIs to measure preparedness can vary based on security maturity and the needs of the organization.
2. Number of unidentified devices on the internal network
Identifying vulnerabilities in internally and externally accessible systems gives valuable insights into the risk posture of critical assets and helps prioritize gap fixing. These vulnerabilities are identified using automated assessments, manual scans, and other security tools. It is a key cybersecurity metric because the results are used to update security policies, prioritize patch management, and are helpful for compliance requirements.
Also, review if there are:
- Logs and events of associated network devices
- Strong measures for device authentication
- Tools and measures for network segmentation
- Regular device inventory updates
3. Intrusion attempts and responses
Intrusion attempts are intentional and unauthorized efforts to gain access to a network or systems for malicious purposes like exploiting vulnerabilities, stealing data, etc. Evaluating the number of intrusion attempts provides much-needed visibility into security weaknesses.
After finding out the number of intrusion attempts, also evaluate:
- How many of these were flagged by intrusion detection systems in real-time?
- What is the frequency of intrusion attempts?
- What was the time taken to respond to these intrusion attempts?
- How many intrusion attempts were reported, along with suspicious URLs or other indicators of malicious activity?
4. Number of known vulnerabilities
Identifying vulnerabilities in internally and externally accessible systems gives insights into the risk posture of critical assets and helps prioritize gap fixing. These vulnerabilities are identified using automated assessments, manual scans, and other tools. It is a key cybersecurity metric because the results are used to update security policies, prioritize patch management, and are helpful for compliance requirements.
A compliance automation tool like Sprinto can aid you with vulnerability management by running automated checks throughout the day. The platform showcases you the live status of your security posture at any given time and raises automated alerts for any deviations. The platform also allows you to track vulnerabilities till closure.
Also check: Top 10 Vulnerability scanning tools
5. Security incidents
Security incidents are unauthorized attempts by hackers to gain access to networks and devices that result in a breach, malware infection, or a sensitive information compromise. The number of security incidents detected and reported serves as a crucial cyber security metric to understand the effectiveness of security controls and practices.
Best Read:A Complete Guide on Security Incident Management
For deeper insights and comparison, you can have the number of incidents reported for month, quarter, and year. Classify them based on severity and note down the impact. Additionally, find out the cost per incident to resolve the attack.
6. Mean time to detect
Mean time to detect is a cybersecurity key performance indicator for an effective incident response plan. It measures the average time to detect a threat or security incident from the moment it occurs. A low MTTD value suggests strong incident response measures in place.
MTTD is calculated by adding detection time for all incidents and dividing it by the number of incidents.
Here’s an example: Calculating MTTD for Q1 for ABC Company
| Date | Incident occurrence time | Incident detection time | Time to detect (minutes) |
| 2023-05-01 | 8:05 AM | 8:37 AM | 32 |
| 2023-27-01 | 1:27 PM | 2:15 PM | 48 |
| 2023-10-02 | 3:56 PM | 4:20 PM | 24 |
| 2023-03-03 | 4:06 PM | 5:15 PM | 69 |
| 2023-18-03 | 6:18 AM | 7:10 AM | 52 |
The MTTD will be: (32+48+24+69+52)/5 = 45 minutes

7. Mean time to acknowledge
The Mean time to acknowledge is the time taken to confirm the existence of an incident from the time an alert was generated. A lower MTTA indicates the organization is proactive in response to incidents like service outages, downtime, attacks, etc.
MTTA is calculated by dividing the sum of the acknowledgment time of incidents by the total number of incidents. So if the acknowledgment time for 3 incidents is 15 minutes, 18 minutes, and 12 minutes, respectively, the MTTA will be (15+18+12)/3 = 15 minutes
8. Mean time to resolve
Mean time to resolve is another cybersecurity metric related to incident management. It is the time taken to resolve the incident from its identification fully and ensures that the systems return to normal operations.
To calculate MTTR, divide the total time taken to resolve incidents by the number of incidents.
For example, if an organization takes 15 hours to resolve 2 incidents a week, the MTTR for that week is 7.5 hours.
9. Mean time to contain
The Mean time to contain measures the time security teams took to minimize the spread of damage from an incident after detection and acknowledgment. It is crucial to reduce the MTTC for building efficient incident response mechanisms.
MTTC is calculated by taking the sum of containment time for failures and dividing it by the total number of incidents.
So, if the containment time for isolating the affected systems for 3 incidents is 120 minutes, the MTTC will be 40 minutes.
10. Mean time between failures
The mean time between failures is a maintenance KPI that measures the average time a system or component operates before failing. This helps assess the reliability of these systems or components to reduce downtime and other disruptions. MTBF is calculated by dividing the total operational time by number of failures.
For example, if a server is operational 24 hoursX365 days, the total number of operational hours will be 8760. If the system breaks 5 times during the year, MTBF will be 8760/5= 1752 hours.
11. Mean time to recover
Mean time to recover is the time taken to recover from an incident and restore systems for routine business activities. Mean time to recover considers only the recovery phase after containment and is different from mean time to resolve, which measures the entire time taken for incident resolution from detection.
So if it took 10 minutes to recover a system from incident 1 and 30 minutes to recover the system from incident 2, the mean time to recover will be 20 minutes.
12. First-party security rating
The security rating quantifies and objectively measures an organization’s security maturity and cybersecurity posture. It indicates the organization’s effectiveness in protecting against security threats and vulnerabilities. Several security components like network security, patch management capabilities, endpoint security, etc. are evaluated through data analysis, reviews, and tests, to assign a security rating to an organization.
Several tools provide letter-based or numerical score security ratings for businesses, making it easy to communicate the strength of security practices to clients and non-technical stakeholders.
13. Vendor security rating
Vendor security ratings help understand risks associated with third-party relationships. These ratings may be expressed as a score, grade, or other form of rating to assess the vendor’s risk posture quantitatively. When looking at vendor security rating it is crucial to understand:
- The criteria used for evaluating performance such as incident response times, compliance with standards, patch management etc.
- The frequency and process of security assessments used for assigning scores
A compliance automation tool like Sprinto can further help with third-party risk management. The platform automatically creates a list of vendors based on your active integrations. It facilitates vendor risk calculation by analyzing the type of data accessed by the vendor. You can also manage vendor due diligence reports and risk assessments centrally from the tool.
14. Patching cadence
Patching cadence is a cybersecurity metric that assesses the frequency of security patches, updates, and other fixes for networks, systems, and devices to mitigate known vulnerabilities. It is crucial to have visibility into patch cadence to improve vulnerability management and adjust the patch schedules as per the organization’s evolving security needs.
Take the following key metrics into consideration for evaluating patch cadence effectiveness:
- Time taken from patch release to patch application
- Adherence rates of patching schedule
- The prioritization of vulnerabilities for patch deployment
- Number of critical vulnerabilities that haven’t been patched
15. Vendor patching cadence
Vendor patching cadence evaluates the frequency of security patches and updates the software vendor releases. These patches or updates are released to fix any weaknesses or enhance performance. The frequency of vulnerability scans and patch releases and the communication about new updates is a testament to the vendor’s reliability. You must also consider the time taken to deploy these patches after release as a metric to gauge the effectiveness of risk management procedures.
16. Mean time for vendor incident response
The mean time for vendor incident response is the time vendors take to respond to security incidents. This cybersecurity key performance indicator is crucial for efficient vendor management and minimizing third-party breaches. The lower the time the vendor takes to manage incidents, the more responsive your vendor is. Mention your expectations regarding incident management in service level agreements (SLAs) to establish vendor accountability.
17. Security awareness training
Cybersecurity awareness training is a knowledge management process where employees are educated about cybersecurity best practices and trained to deal with incidents. Some key training components include password security basics, phishing awareness, device security, compliance with regulations etc.
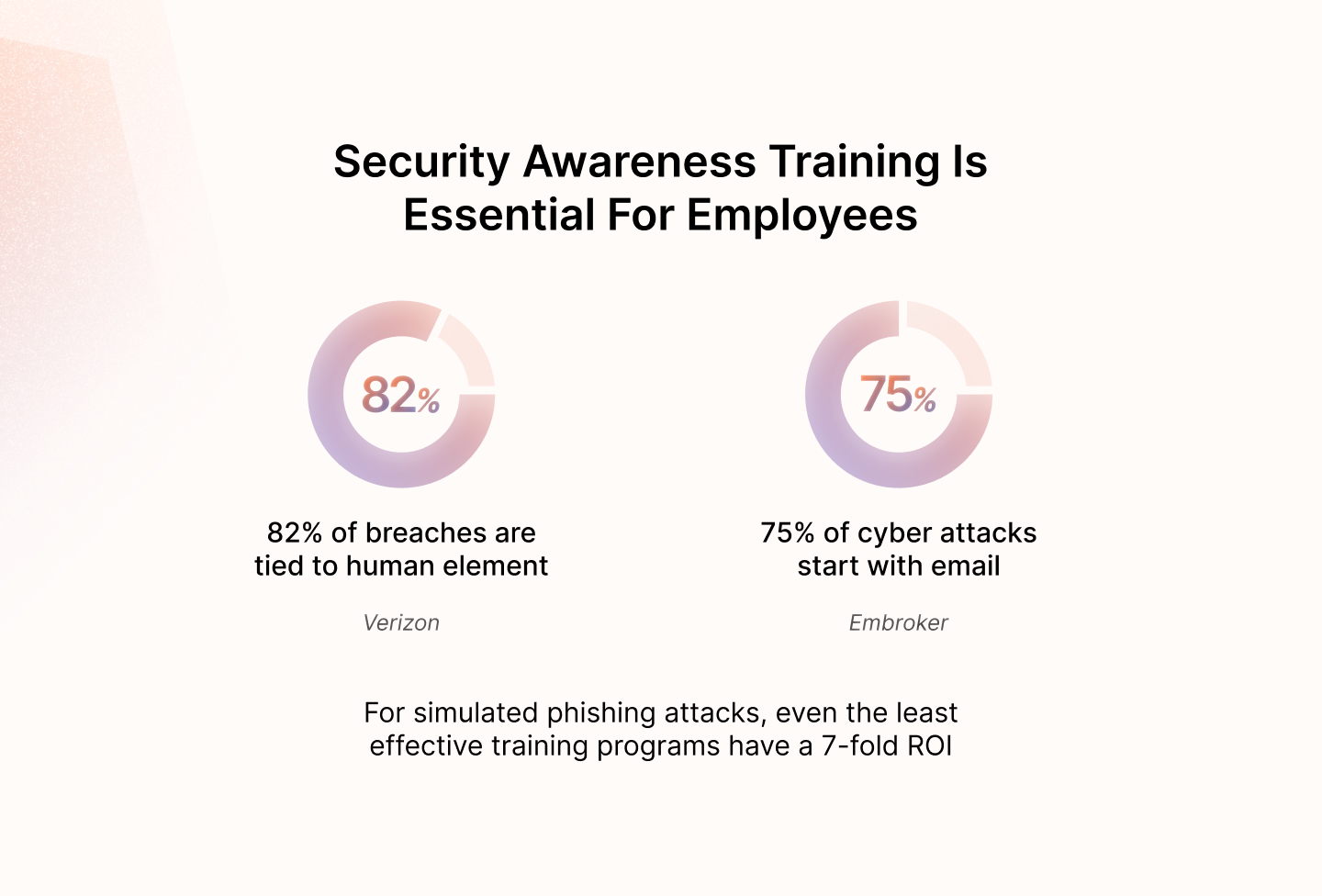
Tracking training completion rates and any results from post-training assessments is a vital cybersecurity metric to ensure a resilient security posture.
18. Access Management
Access management as a metric evaluates the effectiveness of access controls and identity management policies to protect sensitive information assets and minimize unauthorized access. The following KPIs and checks are associated with access management:
- Number of accounts with admin access to systems
- Frequency of access reviews
- Authentication success rate (Enforcement of multi-factor authentication or MFA, password policies, single sign-on etc.)
- Compliance adherence to access policies
- Access revocation success rate
19. Non-human traffic
Non-human traffic refers to network or website activity initiated by malicious bots and poses a potential threat. This traffic can lead to a sudden surge in traffic numbers (analytics skewing), exploit vulnerabilities, inject suspicious code, or conduct fraudulent activities.
Calculating the percentage of non-human traffic compared to overall traffic is essential to prevent bot attacks.
20. Company Vs peer performance
Company Vs peer performance compares an organization’s cybersecurity performance metrics with industry peers. This is done to assess the effectiveness of internal controls compared to industry standards. For example, you can compare the following metrics with industry benchmarks to understand areas of improvement:
- Number of security incidents
- Investment in cybersecurity
- Compliance with data privacy and security standards
- Time taken to patch vulnerabilities etc.
21. Antivirus monitoring
Antivirus monitoring is a cybersecurity KPI that analyzes the frequency of application, system, and endpoint scans for detecting potential viruses, malware, or any other infections. You can also consider the antivirus software’s virus/malware detection rates and time taken to respond to viruses for deeper insights.
22. Phishing attacks
Phishing attacks involve tricks that entice users to click malicious links, directing them to suspicious websites to benefit the attacker. These objectives may include obtaining sensitive information, injecting malware and more. The hackers use deceptive communication methods like legitimate emails and emotionally manipulative messages to achieve their malicious goals.
To assess the organization’s preparedness about phishing attacks, consider using the following metrics:
- Percentage of employees who fell victim to phishing links (phishing click rate or phishing test success rate)
- Percentage of phishing attacks detected
- Number of phishing emails reported by employees
- Cost of phishing incident
How Sprinto can help you show off your security posture?
While tracking and monitoring these cybersecurity KPIs is essential, these are not easy to understand by non-technical stakeholders and customers. Metrics are mostly for security teams and internal understanding. Demonstrating a compliance certification for strong security posture is an easier way to communicate the effectiveness of cybersecurity metrics when dealing with clients.
Sprinto can help you with automated tracking and monitoring of several cybersecurity KPIs and translate them to live compliance status and security posture. The Sprinto trust center can enable you to create a public or private profile and exhibit your security and compliance standing to clients and partners. This helps foster greater transparency and trust amongst the stakeholders and unlocks better business opportunities.
You can expand the scope of your compliance program with features such as security training modules, in-built policy templates, access management, integrated risk management and automated evidence collection.
FAQs
How to select the right cybersecurity metrics for my organization?
You must select cybersecurity metrics that align with your business objectives, the regulatory requirements that are important for your business and the security priorities defined. These will depend on the current security maturity of the organization and will keep evolving as per emerging requirements.
What are some common challenges in using cybersecurity metrics?
Some challenges associated with using cybersecurity metrics are:
- Identifying the right metrics. Organizations that are tempted to track too many metrics get distracted from focus areas.
- Most metrics focus on measuring activities instead of outcomes. For example, the number of incidents rather than the severity/impact of incidents.
- Large amounts of data and metrics can be overwhelming for security teams considering the interconnected nature of many metrics
- The dynamic nature of the landscape necessitates the constant creation of new metrics
Which standards or frameworks provide guidance on cybersecurity metrics?
The ISO 27001 standard covers various aspects of measuring infosec metrics to maintain an effective ISMS. Similarly, NIST Cybersecurity framework guides using cybersecurity metrics to improve security posture.
Payal Wadhwa
Payal is your friendly neighborhood compliance whiz who is also ISC2 certified! She turns perplexing compliance lingo into actionable advice about keeping your digital business safe and savvy. When she isn’t saving virtual worlds, she’s penning down poetic musings or lighting up local open mics. Cyber savvy by day, poet by night!
Related blogs
research & insights curated to help you earn a seat at the table.




















