IT is now fully integrated into business functions, and while this integration is a boon, it can quickly become the first piece of the domino effect that could cause a significant crash when left unchecked. Security audits are designed to monitor and repair the IT infrastructure to achieve optimum efficiency.
An information security audit checklist can assist you in navigating the process of securing digital data against malicious activity and unintentional abuse.
An information security audit checklist helps you find systemic flaws or openings that hackers might take advantage of. Additionally, it offers advice on how to protect your network from these dangers. This article will go over the components of an information security audit checklist and how they may be used to monitor your online safety.
What is a security audit?
An information security audit, sometimes referred to as a cyber security audit or an information technology audit, is an in-depth review of the systems and processes used by an organization.
It is carried out to evaluate the efficiency of information security policies and procedures as well as any potential system flaws. The information security audit also enables businesses to identify issues that might compromise their data security posture and address them.
Why do you need a security audit?
Security audits help protect sensitive data, identify security loopholes, create new security policies, and track the effectiveness of security strategies. Regular audits ensure adherence to security practices and identify new vulnerabilities.
Organizations incur heavy financial losses and damage to the brand as a result of a security breach. Security audits assist in minimizing vulnerabilities that can be exploited and help create policies and systems that ensure that the same vulnerabilities do not come up in the future.
An information security audit can also be used to verify compliance with information security guidelines and standards, as well as to check that systems are current and working as intended.
Comprehensive Risk Monitoring & Mitigation
What does the security audit checklist include?
An information security audit checklist is a list of security procedures that must be implemented to protect an organization’s information systems and data from various threats. This checklist intends to encourage best practices in information security and serve as a manual for managing, storing, and protecting information.
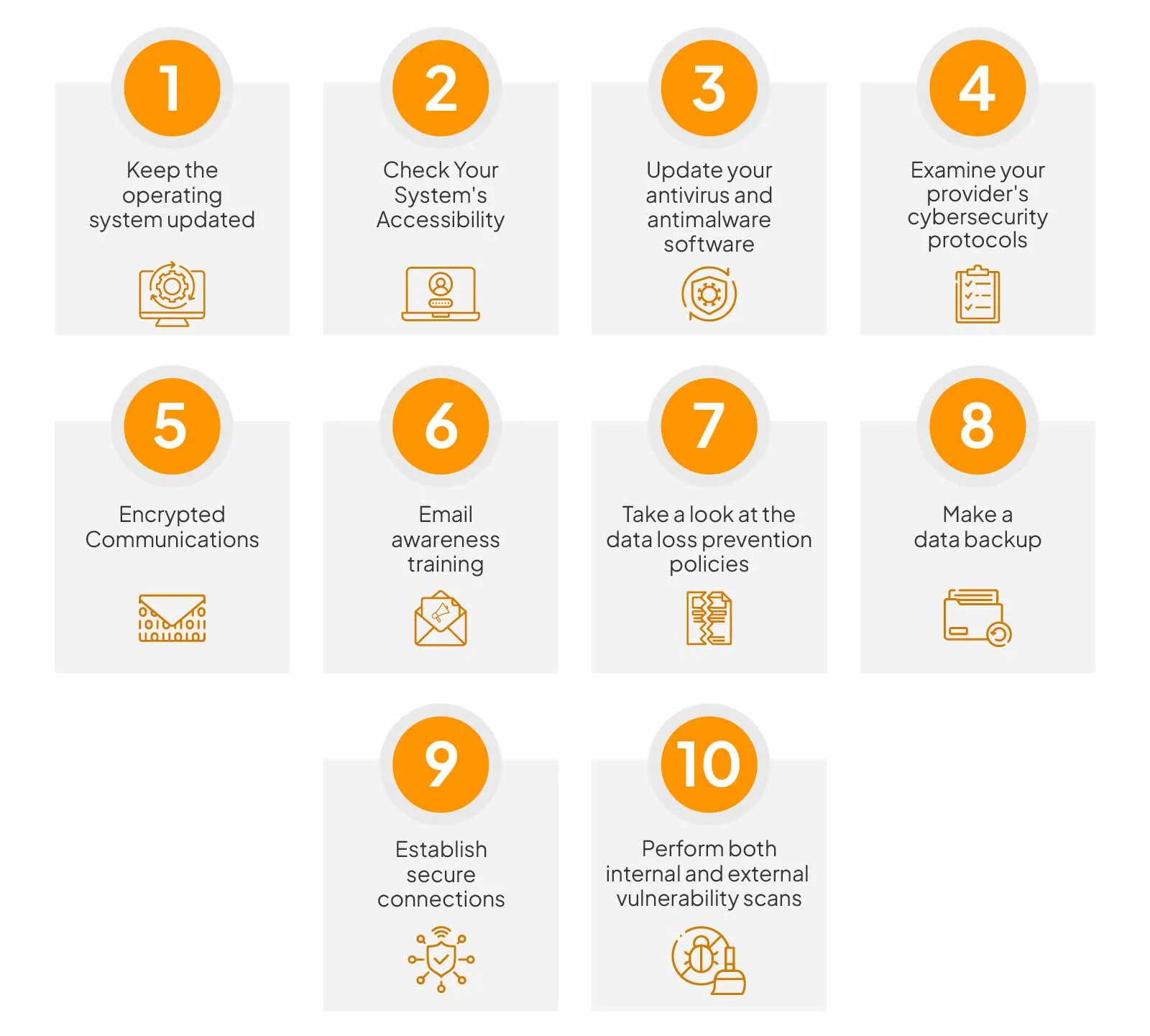
Here are the top 10 items that your security audit checklist should definitely have:
1. Keep the operating system updated
Your company’s operating system should receive automatic upgrades. According to your company’s policies, this means that the system will begin installing updates automatically as soon as they become available.
To ensure smooth corporate operations and processes, system updates are essential.
2. Check Your System’s Accessibility
It’s essential to limit who has access to your system because of the potential threats. Before granting anyone access to your system, run a complete background check on all of your employees and contractors.
Employee training should be prioritized along with reviewing and updating your IT policy. Remember, misconfigurations are the biggest threat to IT security, and they are a result of human errors.
It’s usually preferable to include frequent discussions on the most recent risks to IT security and preventive measures, including phishing drills. By doing this, you can greatly reduce potential loss. If staff are well aware of company policies and adhere to security procedures, the majority of malware or phishing attacks will be unsuccessful.
3. Update your antivirus and antimalware software
Antivirus and antimalware software should be updated regularly for businesses. Your data may be at risk if you miss an update.
Antivirus and antimalware programs regularly check for updates and schedule routine system and removable media scans. In larger organizations, the configurations of the workstations allow them to communicate the status of the updates to a centralized server, which can then send out updates automatically as needed.
4. Examine your provider’s cybersecurity protocols
Reviewing the rules and protocols of a managed security service provider (MSSP) is crucial to understand how they safeguard their data centers and cloud infrastructures.
Also check out: Best cyber security practices.
5. Encrypted Communications
Hackers often penetrate networks through insecure communication channels. Your organization needs to implement encryption methods to secure communications, particularly when sending and receiving sensitive data.
Every employee in your workforce should receive training on how to use the business portals or an encrypted email solution.
6. Email awareness training
Employees should report any and all questionable emails they receive, and training on identifying these emails should be included as part of the safety standards.
Employees with security training exercise caution before clicking on email links or examine the email’s attributes to see if the sender’s email address matches.
7. Take a look at the data loss prevention policies.
Review your company’s data loss protection policy and take the appropriate safeguards. If necessary, you should implement rules that restrict file sharing or require encryption before sharing.
8. Make a data backup
It’s best to routinely back up your data to a secure, encrypted, and off-site location to minimize the impact of any disruptions to your business operations.
The strategy can assist in ensuring a smooth recovery from a cybersecurity attack, human mistakes, and natural calamities. Additionally, it’s critical to abide by laws and regulations.
9. Establish secure connections
Another top concern is to make sure your system’s connections are secure. Employees should receive instruction from the IT team on how to use a virtual private network (VPN) or other secure connection to connect securely to your system’s information resources.
10. Perform both internal and external vulnerability scans
Conduct routine internal and external vulnerability scans to identify any potential future incidents in your system as part of maintaining security operations. Usually, a specialist runs these checks using monitoring solutions.
An internal scan highlights vulnerabilities in the system, while an external scan can assess the general effectiveness of network segmentation and segregation.
Also check out: Best vulnerability scanning tools.
Easy Automated Risk Insights
What is the main purpose of a security audit?
A security audit is a log of periodically testing the security controls and policies in place to ensure desired efficiency is achieved from each deployment. It is also used to record activities, ensure compliance with security policies and procedures, find security service breaches, and suggest any changes needed for countermeasures.
A security audit should be conducted for numerous reasons. These six objectives are among them:
- Determine system flaws as well as security issues and gaps.
- Create a security baseline against which subsequent audits can be measured.
- Adhere to the organization’s internal security policies.
- Adhere to the rules set forth by external regulators.
- See if the security training is sufficient.
- Determine any redundant resources.
How do you perform a security audit?
A cybersecurity audit comprises a thorough mapping of your digital ecosystem and an assessment of its strengths and weaknesses. Throughout the audit, processes for risk responses and recovering from cyberattacks will be examined and tested.
As a result, you can identify previously unknown vulnerabilities or outdated risk management procedures that are no longer effective against evolving cyber threats. To encompass all of these, it is important to know how a security audit is conducted.
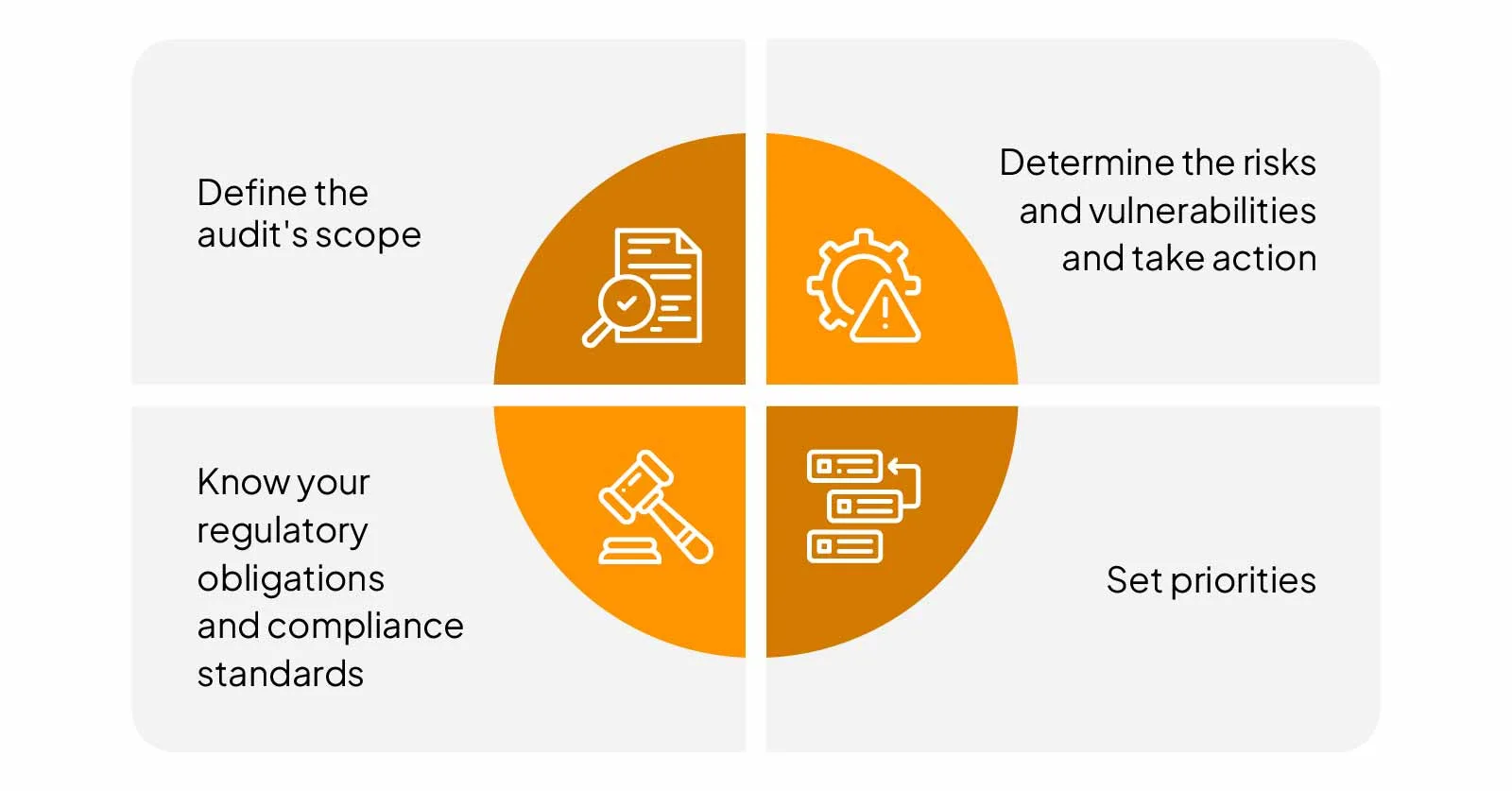
Here are the steps in conducting a security audit:
Define the audit’s scope
Which digital assets will you make securing a priority? What assets are exempt from auditing? What components of your IT infrastructure are poor, brand-new, or in need of maintenance right now? Before moving ahead, create an audit strategy with important stakeholders and executive decision-makers.
Know your regulatory obligations and compliance standards
You’ll save time and money by becoming familiar with major regulations like GDPR, HIPAA, and PCI DSS before starting the audit. Also, you should know which industry-specific regulations apply to you beforehand.
Determine the risks and vulnerabilities and take action
Your cybersecurity audit should highlight any current risks and vulnerabilities so you may discuss them with important stakeholders. Vulnerability analyses and a security posture assessment of your organization should be a part of the audit process.
Set priorities
You will only be able to coordinate some of your efforts simultaneously in a significant cyber attack. Determine the cybersecurity concerns your company views as having the highest priority, and make sure that your organization’s processes are efficient and current.
How frequently do you need to perform a security audit?
The frequency of a company’s security audits depends on the type of business it is in, the requirements of its corporate structure, the number of systems and applications that need to be audited, and the industry in which it operates.
Audits are conducted more frequently by companies that deal with a lot of sensitive data, such as financial services companies and healthcare providers. It will be simpler and more frequent to conduct security audits for those who only use one or two applications. Regulations and other external factors have an impact on audit frequency as well.
A security audit is something that many businesses perform at least twice a year. However, they can also be carried out every month or every three months.
Depending on the systems, apps, and data that each department uses, they may have various audit schedules. Regular audits, whether carried out yearly or regularly, can aid in the discovery of patterns or abnormalities in a system.
How does Sprinto help you with your audit?

Conducting an audit is no walk in the park, and we understand it. However, preparing for the audit is what takes the most time and resources.
Sprinto offers a tech-first solution that saves you the effort and does the work without human intervention. You will be audit ready in days (not months) with Sprinto’s automated evidence collection, structured implementation, and continuous monitoring!
From policy creation to mapping of controls to the audit, Sprinto’s got you covered with its hassle-free automation, integration, and clear checklist.
Book a demo with us and see how Sprinto can help you go through an uncomplicated, resource-light security audit and certification.
FAQ’s
Who uses a security audit checklist?
Security audit checklists are used by auditors, security experts, and businesses of all sizes and sectors. They are used either by external auditors hired to assess an organization’s security controls or internally by organizations to assess their own security practices.
Are there any industry-specific security audit checklists?
There are, in fact, industry-specific security audit checklists that take into account the various security laws and regulations that apply to various industries. For example, businesses managing credit card data, the Payment Card Industry Data Security Standard (PCI DSS) provides its own check list.
Can a security audit checklist ensure total security?
A security audit checklist is a useful tool, but it cannot provide total security. It acts as a guide to evaluate the application of security controls and find any weaknesses. Security is a process that needs to be continuously monitored, adjusted, and improved.
What are security audit examples?
Different security audit examples may be used depending on the audit’s aims and scope. Network security audits, application security audits, compliance audits, cloud security audits, etc., are a few instances of these.
Shivam Jha
Shivam is our in house cybersecurity sage with over six years of experience in cybersecurity under his belt. He is passionate about making the digital world safer for everyone and whipping up Indian delicacies on the weekend.
Explore more
research & insights curated to help you earn a seat at the table.






















