
A CDC report states, ‘the number of telehealth service providers in the United States went up by 154% in 2020 compared to 2019’. This radical spike kept climbing even after the COVID-19 pandemic. Large volumes of medical data were transmitted over electronic mediums in this period alone. With this unexpected influx of ePHI (e- Protected Health Information) transactions, it became imperative for companies processing ePHI to introduce policies and measures to ensure that the integrity and security of sensitive patient health information aren’t violated over the electronic transmission medium.
If your organization is a telehealth company that processes ePHI, this article is a must-read. In this article, we dive deep into HIPAA compliance for telehealth organizations, understand the scope of the process, go over pro-tips to become/remain compliant, the HIPAA audit process, and the penalties involved with HIPAA non-compliance.
What is Telehealth?
Telehealth is when entities use remote channels for non-medical services activities. Non-medical services activities include Clinical healthcare, Patient and professional health-related education, and public health and health-related education.
Source
Any organization or medical professional (doctor, nurse) that provides health care services from a remote location comes under the purview of being a telehealth service provider according to HIPAA privacy rule.
For example, any organization providing healthcare information services over video calls, mobile apps, and secure messaging platforms is a telehealth service provider.
Why ePHI is important for telehealth companies as per HIPAA
As more healthcare providers adopt practicing medicine through online or socially-distanced channels, it becomes essential for service providers accessing electronic patient records to deploy security measures to safeguard ePHI.
The channels used for electronic communications should be HIPAA compliant, and companies must deter from using non-secure channels.
The HIPAA security rule details the aspects of the scope of HIPAA compliance for telehealth service providers.
HIPAA Security Rule
The security rule of HIPAA about telehealth companies states that:
- Access to ePHI should be exclusive to authorized users only
- Secure communication channels should be used when transmitting ePHI
- All communication should be monitored to ensure that no transmissions are intercepted and breached
The HIPAA security rule emphasizes the need for role-based access to ePHI. It also draws attention to the importance of secure communication between telehealth companies and patients. Lastly, it details the need for monitoring and remote access systems to detect unauthorized access to electronic transmissions and enable organizations with the means to remotely wipe ePHI in the event of a breach to protect critical patient data.
Companies should deploy physical and technical safeguards to ensure only authorized access to ePHI.
Technical Safeguards
To remain HIPAA certified when processing ePHI, companies should deploy the below-mentioned technical safeguards to ensure patient data integrity.
- User identification: To enable easy identification of user sign in
- Encryption: Any communication sent to or received from the patient should be encrypted, and the telehealth organization should facilitate this service.
- Staff training for emergencies: Staff members of the organization should be trained to react and respond to ePHI emergencies and execute the recommended course of action.
- Data integrity: Any electronic record of patient data could easily get altered or deleted. Companies must, therefore, deploy policies and measures to protect patient’s data integrity and maintain accurate records
Physical Safeguards
For telehealth companies to be HIPAA compliant, they must deploy a series of physical safeguards to ensure patient data is protected when stored in physical form. The safeguards are:
- Physical security: A plan to safeguard physical patient data must be documented and implemented
- Access control: Based on an employee’s role and a justified need to perform their jobs efficiently, access to sensitive PHI should be granted
- Record maintenance activities that happen in the business environment. For example, record activities when the doors or locks in the office premises are changed
- Document your organization’s media usage policy. Include details on how reusable media is used and how media is discarded, among others
- Policies should be documented and implemented on how workstations with access to PHI should be used. Access to such endpoints should be restricted to authorized users only.
Also read: Who does HIPAA apply to
7 Steps to help telehealth companies become HIPAA compliant
The HIPAA law does not explicitly dictate the measures telehealth companies should include in their data security systems to become/remain HIPAA compliant. However, here are the seven steps to get your organization started in its compliance journey. Based on your organization’s risk assessment, you can implement additional policies and controls if needed.
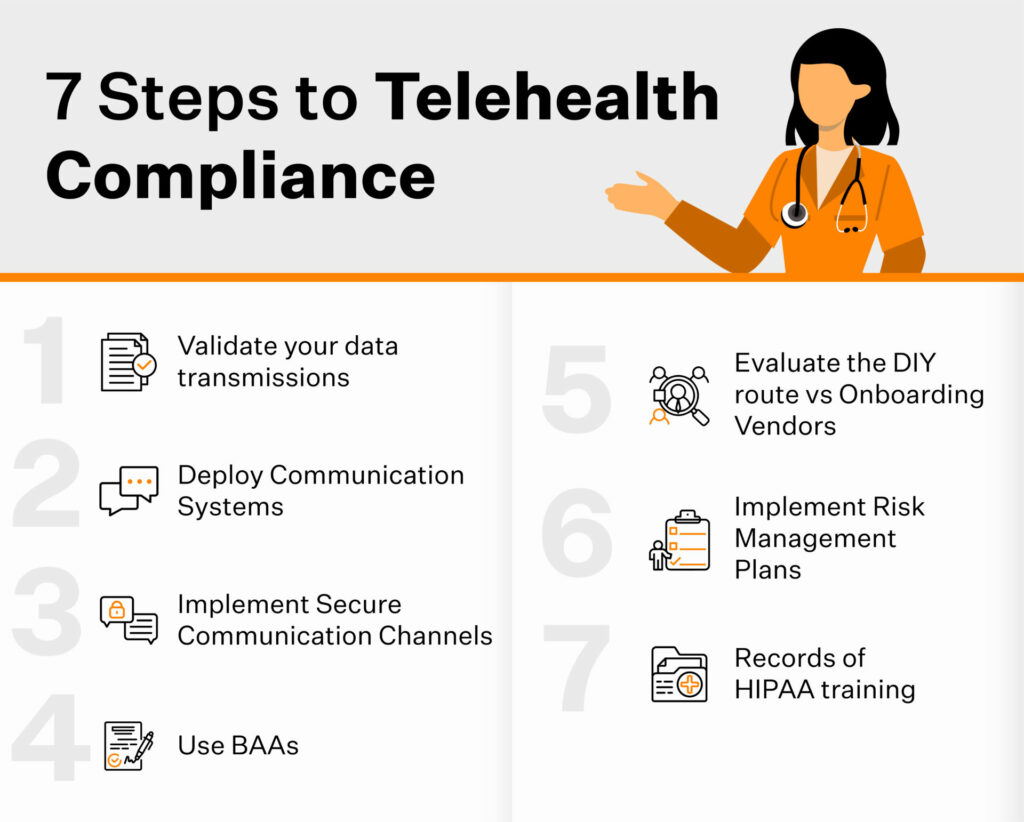
Step 1: Clear The Air
Often companies need clarification on whether the information they transmit qualifies as PHI. This confusion often delays the onset of their compliance journey, making them susceptible to the penalties involved with HIPAA non-compliance.
Your organization processes PHI if your data set contains the following:
- Name of the patient
- Billing information and address of the patient
- Contact information (Phone number & email address)
- Genetic information: Fingerprints, IRIS scans
- The SSN (Social Security Number) of the patient.
Step 2: Set up a system for communicating ePHI with customers from a distance
This combines the physical and technical safeguards we discussed earlier in the article. Set up a system within your organization that prevents unauthorized access to endpoints (workstations) that can be used to access ePHI. Also, ensure that the electronic communication channel is HIPAA compliant and has the plugins required to monitor and execute emergency protocols if any unauthorized access to that secure transmission is detected.
Step 3: Use a secured messaging network for communication with patients
SMS and emails through regular service providers are not considered secure messaging channels by HIPAA. Therefore, when communicating, ensure that HIPAA-compliant communication channels are used.
Skype for Business, Office 365, and mobile apps with secure sign-in are a few examples of HIPAA-compliant channels. You can explore more HIPAA-compliant communication service providers if you wish to explore other available options.
Step 4: Sign BAA if the vendor manages ePHI
A Business Associate Agreement (BAA) is a legal contract that covered entities and third-party service providers agree upon to ensure that the third-party organization accessing ePHI or PHI will uphold the data integrity and privacy of the patient data they access in a HIPAA compliant manner.
A BAA ensures that the service providers adhere to HIPAA and acts as a medium to repossess or destroy PHI shared with them in the event of non-compliance.
Insurance providers, telehealth vendors, or any other service provider/vendor offering its services to covered entities are examples of third-party providers.
Step 5: Evaluate the vendor managing your telehealth activities
A telehealth vendor offers companies a platform to conduct all their telehealth processing activities. If you are unsure on whether or not to onboard a telehealth service provider, evaluate their service offerings and compare them to your current management tool and identify the improvements you will need to make to your existing platform. Also find out the development cost and the time it will take to implement those changes.
To make an informed decision, you can compare multiple service providers and their pricing plans, features list, and integrations and gain insights into their encryption methods, security posture, and multi-channel accessibility options.
Often building custom solutions consumes time and resources and companies tend to onboard HIPAA-compliant service providers to expedite their timelines.
Step 6: Implement a risk management policy
A risk assessment and management policy lets your organization know the potential risks associated with your processing activities. You could either do this in-house or onboard a specialist to do it for you.
Your risk management policy should focus on these primary points :
- Track where ePHI is stored and the security measures deployed to ensure its security. It should also collate data to help you analyze the desired efficiency in security vs. the current efficiency metrics.
- Evaluate how safe or vulnerable are the endpoints (mobile devices, laptops, desktops) with access to PHI and regularly implement remedial measures where required*In the event of a breach, project an estimate of the extent of damage your organization would face.
- Evaluate your current security measures and assess the different kinds of security breach attempts your organization can withstand and identify the kinds that could potentially penetrate your security measures and gain access to secure data.
Step 7: Records of HIPAA training
Employees of every organization must undergo training on the best practices of cyber security. Training enables employees to contribute to the strengthening of the overall security posture of the organization. Maintaining a record of all the training activities and documenting the course for future reference is the recommended best practice.
Training models should include insights on how to:
- Educate all employees about HIPAA and its guidelines
- Process or handle ePHI
- Leverage security to boost the organization’s credibility
- Identify the most common errors that occur when processing ePHI and how to avoid them
- Assure patients by educating them on steps you’ve taken to ensure the security of their ePHI
Does HIPAA apply to every telehealth provider?
As long as any telehealth provider processes ePHI and uses an electronic channel for transmitting them, they come under the purview of the HIPAA law and are required to be HIPAA compliant. We’ve discussed earlier how companies need clarification on their need to be HIPAA compliant. This lack of coherence is often the ground for non-compliance, thus subjecting them to penalties and administrative fines in the event of a data breach.
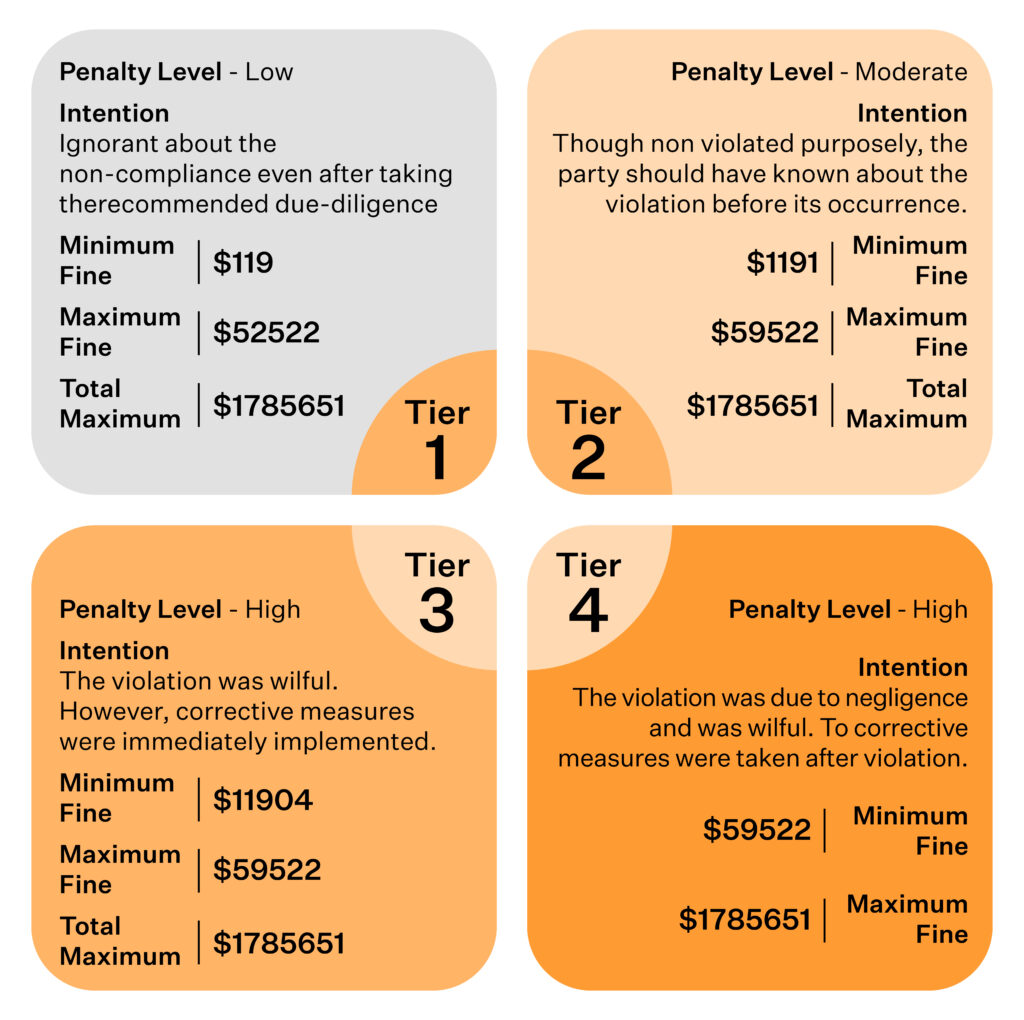
Penalties associated with a breach of information
HIPAA compliance penalties are classified into four tiers based on the severity of non-compliance and the intention behind it.
Criminal Penalties
Sometimes along with monetary and administrative fines, criminal penalties are also levied. Certains violations by companies or entities of an organization are considered as criminal offences. For example, let’s assume that an illegal sale of PHI is detected, parties involved in that violation are sentenced to serve prison sentences ranging from one year to ten years depending on the intention.
The duration of the sentence depends on the non-compliance activity’s classification and the steps implemented to implement remedial measures.
How does the telehealth HIPAA audit happen?
A HIPAA telehealth audit occurs when the regulatory body of HIPAA, the OCR (Office for Civil Rights), finds signs of HIPAA non-compliance within an organization. These audits are usually triggered when a breach is reported or when patients report instances where the integrity of their PHI was violated.
The OCR audits the organization in context, reviews its compliance posture, and issues correction plans if applicable.
Who performs HIPAA audits to certify your telehealth?
Internally a HIPAA telehealth audit can be conducted by any of your employees. You can also hire a HIPAA telehealth auditor to review your current policies and standards and map them to HIPAA requirements.
Such an audit measures the policies and controls deployed within your organization. It assesses if they are in coherence with the regulation. It also identifies areas of improvement for a better security posture.
However, when an actual HIPAA telehealth audit occurs, it is conducted by the OCR.
The Sprinto way to HIPAA compliance
Sprinto makes your telehealth compliance journey a breeze by automating the heavy lifting involved in implementing controls required to become compliant.
Companies are on top of their compliance process by leveraging Sprinto’s Vendor Risk assessment due diligence process. The Vendor Risk Assessment due-diligence process helps them gain complete visibility on their active and dormant partner portfolios and implement HIPAA-compliant communication methods where applicable.
Our Automated Risk assessment and Risk Management Policy is extensively used by companies to identify existing vulnerabilities and automatically deploy remediation measures to maintain a strong compliance posture.
Sprinto’s perfect fusion of automation and human intervention has enabled organizations to become HIPAA-compliant in four to six weeks.
Talk to our experts today to see how you can leverage Sprinto to breeze through your telehealth and HIPAA compliance journey.
FAQs
Who should comply with HIPAA?
Every covered entity processing and transmitting PHI over electronic and non-electronic channels should be HIPAA compliant.
Is there a difference between HIPAA telehealth and telemedicine?
Telemedicine is when patients consult with physicians and medical staff for medical services remotely.
Do you need to provide telehealth-centric HIPAA training to your staff?
Yes, your staff will need to undergo HIPAA training for telehealth. This training educates them on the dos and don’ts of processing ePHI, public health emergency protocols and more.
How much will it cost to become HIPAA-compliant as a telehealth provider?
If you take the DIY route to become HIPAA compliant as a telehealth provider, the cost ranges between $4000 – $12,000 for small organisations and $50,000 to $120,000 for medium and large organizations. Thus estimate does not factor in opportunity cost. Alternatively, you can work with a service provider specializing in this. While their prices vary, they are significantly cheaper when compared to the DIY route.
Vimal Mohan
Vimal is a Content Lead at Sprinto who masterfully simplifies the world of compliance for every day folks. When not decoding complex framework requirements and compliance speak, you can find him at the local MMA dojo, exploring trails on his cycle, or hiking. He blends regulatory wisdom with an adventurous spirit, navigating both worlds with effortless expertise
Explore more
research & insights curated to help you earn a seat at the table.









![HIPAA Certification Cost [Updated 2024 + Free Checklist]](https://sprinto.com/wp-content/uploads/2024/04/HIPAA-Certification-Cost-Updated-2024-Free-Checklist-1024x675.jpg)











