Cloud Service Providers (CSPs) aiming for FedRAMP authorization must categorize their systems’ security impact levels as per FIPS 199, a NIST standard. However, there’s always an initial confusion of how accurately you can categorize systems.
Misclassifying systems, either by over-securing or under-protecting, often cause a delay in authorization or expose sensitive data to risks. So, before we dig into differentiating between the FedRAMP impact levels, let’s get an overview of the framework and why it’s such a hot topic right now.
| TL;DR FedRAMP categorizes security levels into Low, Moderate, and High, per sensitivity and impact of the data handled. The FIPS 199 assessment uses the CIA triad (Confidentiality, Integrity, and Availability) to determine an IT system’s security impact level. The security level for FedRAMP depends on the data’s sensitivity and potential breach impact. |
Who needs FedRAMP authorization?
Any Cloud Service Provider (CSP) that wants to offer their services to U.S. federal agencies needs FedRAMP authorization. Getting ATO (Authorization to Operate) guarantees that their services meet stringent security standards required for government use. Without FedRAMP authorization, CSPs cannot work with federal agencies.
As of January 2025, there are 357 ATO services in the FedRAMP marketplace. Service models include IaaS (Infrastructure as a Service), PaaS (Platform as a Service), and SaaS (Software as a Service).
What are the FedRAMP impact levels?
For all impact levels under FedRAMP, the security controls list revolves around 18 unique families:
- Access Control
- Awareness And Training
- Audit And Accountability
- Security Assessment And Authorization
- Configuration Management
- Contingency Planning
- Identification And Authentication
- Incident Response
- Maintenance
- Media Protection
- Physical And Environmental Protection
- Planning
- Personnel Security
- Risk Assessment
- System And Services Acquisition
- System And Communications Protection
- System And Information Integrity
- Supply Chain Risk Management Family
As you explore CSPs in the AWS marketplace, you can filter them by impact levels: low, moderate, and high. Let’s understand what these mean.
1. Low impact level
A low-security baseline means that the loss of confidentiality, integrity, or availability of information would have minimal impact on your CSP. This would result in only minor disruption to the agency’s customers, operations, assets, employees, or vendors.
FedRAMP offers two levels for data systems with minimal impact:
- Low Impact (LI)-SaaS Baseline: Meant for SaaS applications that only store basic login information without any sensitive personal information (PII).
- Low Baseline: Covers less risky data for public use, where a breach wouldn’t harm safety, reputation, mission, or financial stability.
FedRAMP low-level controls
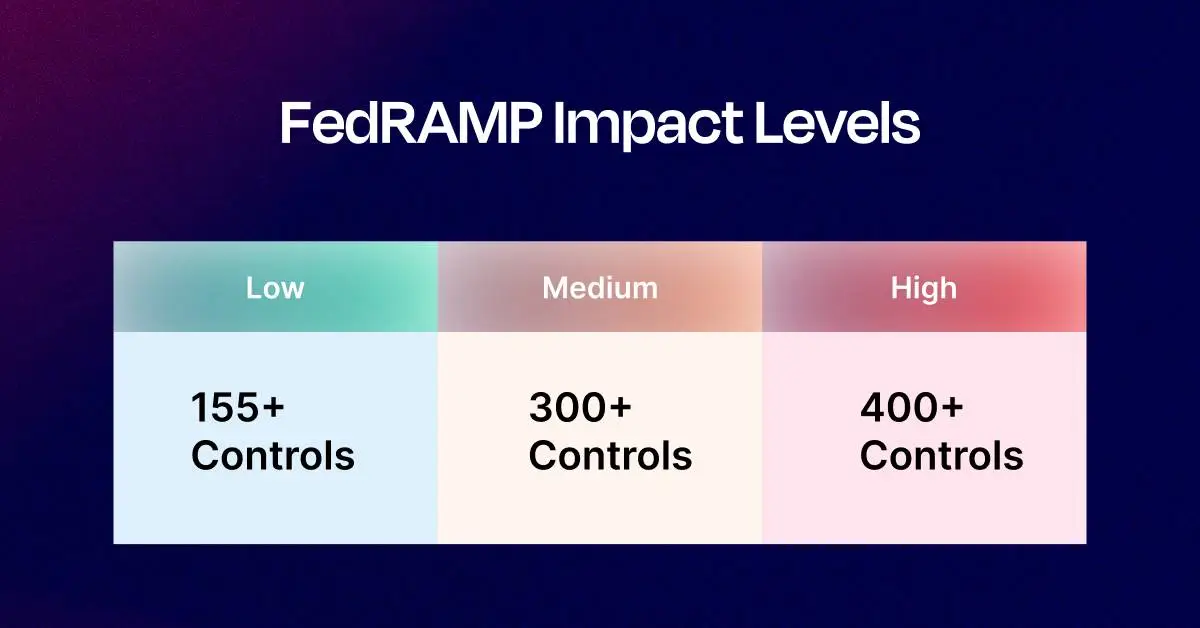
FedRAMP low impact level has 155+ security controls. Here are some examples:
- Policy and Procedures
- Account Management
- Access Enforcement
- Unsuccessful Logon Attempts
- System Use Notification
- Permitted Actions Without Identification or Authentication
- Remote Access
- Wireless Access
- Access Control for Mobile Devices
- Use of External Systems
- Publicly Accessible Content
- Role-based Training
- Training Records
- Policy and Procedures
- Event Logging
- Content of Audit Records
- Time Stamps
- Audit Record Generation
2. Moderate impact level
Most (80%) CSPs with FedRAMP authorization are registered under a moderate impact level. These providers handle information where the loss of confidentiality, integrity, or availability could significantly disrupt an agency’s workflows, devices, assets, or customers.
If you fall into this category, failing to protect your information could lead to significant damage to agency assets, financial loss, or harm to individuals, though not life-threatening or physical harm.
FedRAMP moderate-level controls
Moderate FedRAMP level controls have more than 300 security controls. These have all the security controls covered under low-level in addition to more controls like:
- Authentication feedback
- Controlled maintenance
- Incident Handling
- Incident Reporting
- Information Spillage Response
- Personnel Screening
- Risk Response
- System Backup
- Timely Maintenance
- Water Damage Protection
- Acquisition process
- Supply chain risk assessment
- Personnel termination
3. High impact
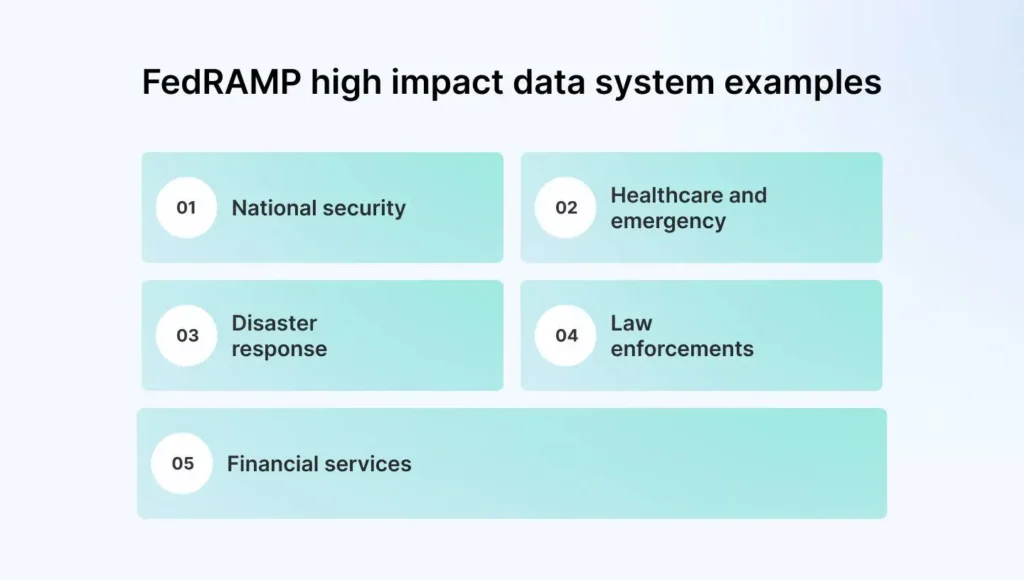
FedRAMP’s High Baseline is designed for SaaS, cloud environments that work with sensitive information for the government, including data critical for protecting lives and preventing financial ruin. If your data is compromised, it could cause severe or catastrophic damage to your operations, assets, employees, and customers.
FedRAMP high-level controls
High FedRAMP level baseline has more than 400 security controls. These include all controls listed under low and moderate level in addition to:
- Unsupported System Components
- Transmission Confidentiality and Integrity- Cryptographic Protection
- Tamper Resistance and Detection- Multiple Stages of System Development Life Cycle
- System Time Synchronization- Synchronization with Authoritative Time Source
- System Monitoring – 14 controls
- Supply Chain Risk Management Plan- Establish SCRM Team
- Supply Chain Controls and Processes
- Supplier Assessments and Reviews
- Spam Protection- Automatic Updates
- Software, Firmware, and Information Integrity – 7 controls
- Session Authenticity
- Separation of System and User Functionality
- Security Function Isolation
- Security and Privacy Function Verification
- Security Alerts, Advisories, and Directives- Automated Alerts and Advisories
- Secure Name/address Resolution Service (recursive or Caching Resolver)
- Secure Name/address Resolution Service (authoritative Source)
- Public Key Infrastructure Certificates
- Protection of Information at Rest- Cryptographic Protection
- Process Isolation
- Notification Agreements
- Network Disconnect
- Mobile Code
- Memory Protection
- Malicious Code Protection
- Inspection of Systems or Components
- Information Management and Retention
- Information Input Validation
- Information in Shared System Resources
- Flaw Remediation- Time to Remediate Flaws and Benchmarks for Corrective Actions
- Flaw Remediation- Automated Flaw Remediation Status
- Fail in Known State
- Error Handling
- Developer Security and Privacy Architecture and Design
- Developer Screening
- Denial-of-service Protection
- Cryptographic Protection
- Component Disposal
- Component Authenticity
- Collaborative Computing Devices and Applications
- Boundary Protection – 10 controls
- Architecture and Provisioning for Name/address Resolution Service
- Acquisition Strategies, Tools, and Methods
Comparing high vs moderate baselines side by side
Here’s a table with all the differences between FedRAMP high and moderate baselines based on multiple factors:
| Factor | FedRAMP High | FedRAMP Moderate |
| Target systems | Sensitive systems (e.g., law enforcement, national security, healthcare, financial) | Systems with less sensitive data (e.g., many cloud services for federal agencies) |
| Data Sensitivity | Involves life-critical, financial, and security data | Low to moderate-risk data, typically non-life-threatening |
| Security controls | 400+ controls to protect highly sensitive data | 300+ controls but still comprehensive for moderate-risk data |
| Frequency of Use | Less common; used for systems with highly sensitive or mission-critical data | More common; covers about 80% of FedRAMP-authorized CSPs |
| Implementation Time | Longer, due to the higher number of controls and more detailed security requirements | Shorter, as fewer controls are needed and the process is less complex |
| Continuous Monitoring | Requires more extensive and frequent monitoring to ensure ongoing compliance | Regular monitoring, but fewer requirements for frequency and detail compared to High |
| Authorization Process | More rigorous and time-consuming due to the sensitive nature of the data and more controls | Faster than High, as the process involves fewer controls and less complex security requirements |
Comparing high vs low baselines side by side
Here’s a table with all the differences between FedRAMP High and FedRAMP Low baselines based on multiple factors such as data sensitivity, security controls, complexity, and use cases:
| Factor | FedRAMP Low | FedRAMP High |
| Data Sensitivity | Handles public or low-impact data where a breach would cause minimal harm. | Manages high-impact data that could lead to severe or catastrophic consequences if compromised. |
| Impact Level (per FIPS 199) | Low – Limited adverse effect on operations, assets, or individuals. | High – Severe or catastrophic adverse effect on operations, assets, or individuals. |
| Number of Security Controls | Around 125 controls focusing on basic safeguards like access control and authentication. | Over 400 controls including continuous monitoring, advanced encryption, and incident response mechanisms. |
| Security Oversight | Minimal oversight with simpler authorization and monitoring requirements. | Rigorous oversight with ongoing assessments, audits, and real-time monitoring. |
| Implementation Complexity | Easier and faster to implement with lower resource requirements. | More complex and resource-intensive, requiring advanced security tools and processes. |
| Typical Use Cases | Public-facing systems, general informational websites, or low-sensitivity cloud services. | Defense, law enforcement, healthcare, and critical infrastructure systems managing sensitive data. |
| Cost and Time | Lower costs and shorter authorization timelines. | Higher costs and longer implementation timelines due to strict compliance demands. |
How to select your FedRAMP authorization level?
The two main factors that affect your FedRAMP authorization level are the sensitivity of data your systems handle and the potential impact of a data breach. However, this cannot be solved subjectively. Hence, there are standardized assessments that determine your information security level.
One such example of an assessment is the FIPS (Federal Information Processing Standards) 199 assessment developed under NIST.
The (FIPS) 199 assessment helps categorize the FedRAMP level of the data your organization handles.
FIPS 199 uses the CIA triad (Confidentiality, Integrity, Availability) to assess the impact level of an IT system. Each component is rated as High, Moderate, or Low based on how the loss affects the system’s functionality and mission. The security category formula is:
SC information system = {(confidentiality, impact), (integrity, impact), (availability, impact)}
The FIPS 199 assessment can be conducted with the help of the security controls under NIST 800-53. The following section talks about how this can be done.
Taking the faster and smarter route to compliance
The process of obtaining FedRAMP authorization (ATO or P-ATO) can be complex and time-consuming. As we already saw, there are more than 100 security controls even in the lowest security baseline.
However, the good news is that these controls take their base from NIST 800-53 controls and hence can be mapped using compliance automation tools with ease. Sprinto can be useful here, especially for monitoring ongoing compliance with FedRAMP.
Compliance with frameworks like FedRAMP and NIST 800-53 not only opens doors to government contracts but also demonstrates to nonfederal customers that your system meets the highest security standards.
Frequently asked questions
1. What is a cloud service offering or CSO in the context of FedRAMP?
In the context of FedRAMP, a cloud service offering (CSO) refers to cloud computing environments like IaaS, PaaS, or SaaS that are evaluated and authorized to meet federal government security standards for handling sensitive data.
2. Why is a standardized approach essential for FedRAMP in cloud computing environments?
FedRAMP’s standardized approach ensures that cloud service offerings consistently meet stringent security controls, reducing risks of unauthorized access and operational damage across federal government agencies.
3. How does FedRAMP protect financial systems from unauthorized access?
FedRAMP enforces strict security controls to protect financial systems within cloud service offerings, ensuring that only authorized users can access sensitive data, thus preventing financial losses and individual harm.
4. What is the role of the FedRAMP program in monitoring cloud products for government agencies?
The FedRAMP program provides a continuous monitoring framework for cloud products used by government agencies, ensuring these products maintain compliance and security over time, minimizing risks to organizational operations.
5. What are the potential impacts of operational damage in health systems under FedRAMP?
Under FedRAMP, operational damage in health systems can be mitigated by adhering to high-security controls, ensuring that critical health data is protected from breaches, which could otherwise result in individual harm and disrupted healthcare services.
6. What is the difference between StateRAMP and FedRAMP?
FedRAMP targets federal agencies, whereas StateRAMP is designed for state and local governments, with governance and processes tailored to their specific contexts. The authorization processes differ, with FedRAMP requiring an ATO or P-ATO from the Joint Authorization Board (JAB), while StateRAMP CSPs must achieve a StateRAMP Authorized status through third-party assessments.
Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Explore more
research & insights curated to help you earn a seat at the table.