In 2016, the U.S. Department of Homeland Security (DHS) listed Defense in Depth (DiD) as a recommended strategy for improving ‘industrial control system cybersecurity’ practices. This was done in a bid to make systems less attractive to attackers during a period experiencing a sharp increase in cyber incidents.
So, is DiD a new concept or has it been around? Layering of multiple security measures to monitor and protect our information and devices has definitely been considered a best practice since military strategies. In fact, that’s were we root this concept from.
Let’s take a deeper look at it, how it’s defined, its effect on modern risk management, its architecture, how it compares to other security models, and more.
| TL;DR Defense in depth applies to businesses of all sizes, offering scalability and robust protection, especially when implemented early. Modern DiD supports proactive and predictive risk management through tools like AI/ML, behavioral analytics, and threat intelligence. Its architecture comprises physical, administrative, and technical controls, ensuring comprehensive security coverage. |
The evergreen philosophy of Defense in Depth
Defense in Depth is a security strategy that combines multiple layers of cybersecurity measures and controls to protect your assets and mitigate risks and threats. The concept revolves around the fact that if one line of layer of security is compromised, there is another one protecting above it.
DiD is also called a ‘castle approach’ since castles in the early days used layered defenses like moat, walls, towers and the same can be compared to modern cybersec steps like firewalls, encryption, access controls for holistic defense.
“The methodology involves layering heterogeneous security technologies in the common attack vectors to ensure that attacks missed by one technology are caught by another.” – NIST.IR.8183 under Defense-in-depth from ISA/IEC 62443, ISO/IEC 62443.
Can all types of businesses benefit from Defense in Depth?
Yes. Regardless of the size of your business or the industry you operate in, you can benefit from a Defense in Depth strategy. In fact, small businesses can be at an advantage to implement this approach from the very beginning while building up their security posture to make it stronger.
The architecture of Defense in Depth: 3 core layers
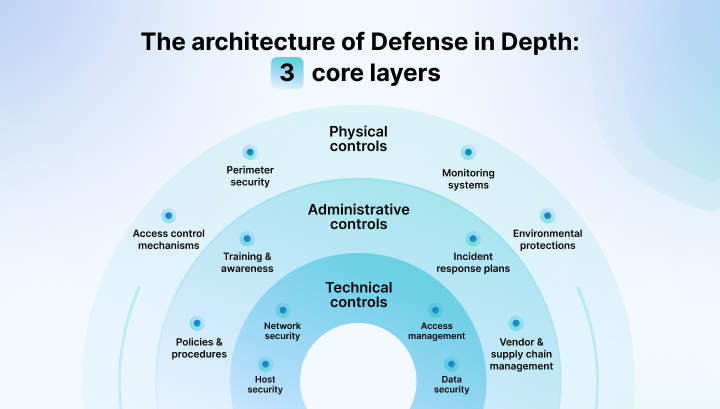
1. Physical controls
Physical controls form the outermost layer of Defense in Depth. It focuses on preventing unauthorized physical access to systems and infrastructure. These controls safeguard assets such as servers, network devices, and ICS components through measures like:
- Access control mechanisms: Key cards, biometric authentication, and PINs for restricted areas.
- Perimeter security: Fences, gates, locked cabinets, and reinforced barriers around sensitive locations.
- Monitoring systems: Security cameras, motion detectors, and intrusion alarms for continuous surveillance.
- Environmental protections: Ensuring systems operate in stable conditions with proper HVAC, dust filters, and vibration-proof setups to prevent environmental damage.
2. Administrative controls
Administrative controls establish the policies, procedures, and training necessary for a robust security posture. They align human behavior with security goals through:
- Policies and procedures: Written guidelines on system use, incident response, and risk management practices.
- Training and awareness: Regular cybersecurity training programs to educate employees about threats like phishing and social engineering.
- Incident response plans: Clearly defined steps for detecting, responding to, and recovering from security breaches.
- Vendor and supply chain management: Ensuring third-party partners adhere to security standards and practices.
3. Technical Controls
Technical controls form the backbone of your cybersecurity defenses, employing tools and configurations to protect systems from digital threats. It is also the innermost layer of your defense in depth strategy. Key elements include:
- Network security: Firewalls, intrusion detection systems (IDS), and demilitarized zones (DMZs) to segment and secure networks.
- Access management: Role-based access control, secure authentication methods, and user privilege restrictions.
- Host security: Regular patch management, antivirus solutions, and system hardening to reduce vulnerabilities.
- Data security: Encryption for data at rest and in transit, alongside backup solutions to ensure data integrity.
How does Defense in Depth relate to modern risk management strategies?
Defense in Depth follows the principles of predictive and proactive risk management in cybersecurity. Although, traditionally, most businesses followed a reactive security approach, things have changed lately.
Reactive risk management deals with a problem after they occur in terms of incident response or remediation activities. However, this approach cannot be the only defense mechanism of an organization.
Modern risk management defense mechanisms go to the lengths of predicting and analyzing events in the future before they even manifest.
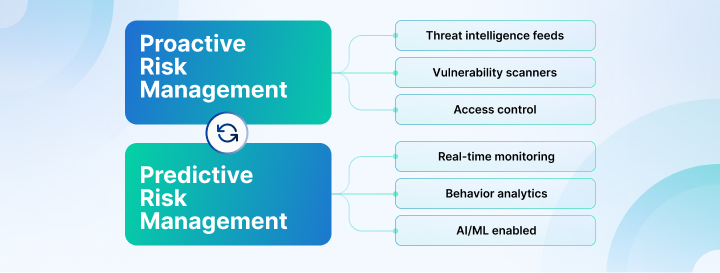
Proactive security: Anticipating threats before they strike
Proactive risk management goes beyond responding to incidents. It involves actively seeking potential risks before they can materialize in your system. This approach mitigates risks in advance. It is done through solutions like:
- Threat intelligence feeds: Gathering data on potential threats and vulnerabilities in real-time to stay ahead of cybercriminals.
- Vulnerability scanners: Identifying weaknesses in systems and networks before they can be exploited.
- Access control: Limiting user access and monitoring for suspicious activities that may indicate a future risk.
Predictive security: foreseeing and preventing future threats
Predictive risk management takes anticipation a step further by using technologies like AI and Machine Learning (ML) to predict, analyze, and prevent threats before they even happen.
In this case, instead of waiting for an attack to manifest, you identify patterns and indicators that suggest a future risk. This is done with the help of features like:
- Real-time monitoring and response: Predictive tools often include automated responses to threats, allowing for quick action before damage occurs.
- Behavioral analytics: By monitoring user and system behaviors, predictive systems can detect deviations from the norm that indicate a security threat might be on the horizon.
- AI/ML-enabled security: These technologies analyze vast amounts of data, helping security teams predict potential breaches based on historical behavior and trends.
Comparing defense in depth with other security models
Defense in depth is an approach that we’ve been following since a long time, whether knowingly or unknowingly, even though the concept is not talked about a lot. Let’s see how it compares to other security models like zero trust and its almost equivalent layered security, which are more commonly known.
Defense in Depth vs ZeroTrust Security
The zero trust security model differs from defense in depth by fundamentally never trusting any entity (inside or outside the network). Instead, it relies on strict identity verification and constant risk monitoring, focusing on reducing access to only what is necessary.
Here’s a table highlighting the key differences between the two.
| Aspect | Defense in Depth (DiD) | Zero Trust Security |
| Core philosophy | Uses multiple layers of security controls to protect systems and data. | Trust is never implicit; verification is required for every user, device, and connection. |
| Focus | Protects both internal and external assets with overlapping controls. | Ensures strict identity verification and access controls for all resources. |
| Approach to trust | Assumes that internal systems may already be compromised and secures them with layers of defense. | Assumes that no one, inside or outside the network, can be trusted and requires verification at every step. |
| Risk mitigation | Mitigates risk by creating redundancies, using various security mechanisms across different layers. | Mitigates risk by enforcing strict access policies and continuous monitoring to limit exposure. |
| Key controls | Physical, administrative, and technical controls across multiple layers. | Identity and access management, continuous monitoring, strict access controls, and network segmentation. |
| Use of technology | Uses firewalls, IDS/IPS, encryption, etc., to create layers of protection. | Relies heavily on multi-factor authentication, role-based access control, and micro-segmentation. |
| Security architecture | Layered defense model designed to delay, detect, and respond to attacks. | Architecture built around trust verification, minimizing internal attack surfaces, and least privilege access. |
Defense in depth vs Layered Security
Layered Security, while similar to DiD, does not emphasize redundancy and may not involve overlapping security measures as much. It is about applying different security controls at various layers, but not necessarily with the proactive mindset that DiD provides.
| Aspect | Defense in Depth (DiD) | Layered Security |
| Core philosophy | A holistic approach that uses multiple layers of security mechanisms to provide comprehensive protection. | Similar to DiD but focuses more on stacking multiple security layers without an emphasis on redundancy. |
| Focus | Focuses on a multi-layered, redundancy-driven approach that protects assets and data in depth. | Focuses on applying different security measures at different layers (physical, administrative, technical) without necessarily overlapping them. |
| Risk mitigation | Uses redundancy in each layer (e.g., firewalls, intrusion detection) to reduce risk. | Focuses on applying multiple, separate security measures at each layer, assuming that attackers might penetrate one layer but will be stopped by another. |
| Key controls | Incorporates physical, administrative, and technical controls in a redundant, overlapping way. | Often involves technical controls like firewalls, encryption, and access controls, but may not always overlap across layers. |
| Adaptability | Highly adaptable, with an emphasis on responding to evolving threats at multiple levels. | Adapts to specific threats, but can be less comprehensive than DiD because it doesn’t emphasize redundant layers. |
| Response to attack | Layers work together to detect and respond to attacks at different stages of an incident. | Layers are more independent, and may not always coordinate or respond together to mitigate a breach. |
How does GRC enable DiD?
Governance, Risk, and Compliance (GRC) plays a crucial role in enabling and optimizing Defense in Depth strategies. In fact, these two concepts have a lot of overlapping features.
Here are three ways in which GRC paves the way for true defense in depth.
1. Integrates policies with multiple security layers
DiD focuses on deploying multiple security layers to address threats, while GRC provides oversight to ensure that each layer is aligned with an organization’s risk profile, compliance requirements, and security policies.
2. Provides oversight and accountability
GRC offers the oversight necessary to evaluate and monitor the effectiveness of each DiD layer, ensuring vulnerabilities are addressed promptly and security investments are optimized.
3. Enhances risk-based decision making
By linking security measures to an organization’s risk profile, GRC empowers businesses to prioritize resources and controls where they’re needed most, maximizing the impact of their DiD approach.
Defense in Depth with Sprinto
Without the help of proper GRC automation tools, the implementation of defense in depth can become overwhelming and may lead to missed security gaps or inefficiencies.
GRC tools, such as Sprinto, paired up with a well-defined defense in depth strategy is the answer to scaling your business. They not only help build an integrated DiD system but also ensure real-time visibility into your security operations.
With such a comprehensive approach, your business can offer customers enhanced confidence in your security practices, going beyond third-party audits to deliver continuous assurance and trust.
Devika Anil, ISC 2-certified compliance expert, and ISO 27001 lead auditor, talks about something similar in the following video.
Frequently asked questions
1. What are the main benefits of implementing defense in depth (DiD) in cybersecurity?
DiD enhances overall security by creating redundancies, making it harder for attackers to succeed. It provides better risk management, improved incident response, and compliance alignment.
2. How does DiD differ from traditional cybersecurity approaches?
Traditional approaches often rely on standalone solutions, such as firewalls or antivirus software, creating single points of failure. DiD, by contrast, integrates multiple, complementary security layers that work together. It adopts a proactive stance, addressing threats at various stages rather than responding only after an incident.
3. How should an organization begin implementing a DiD strategy?
Organizations should start by assessing their risk landscape and identifying critical assets that need protection. This is followed by layering security controls, including perimeter defenses, network segmentation, endpoint protection, access management, and employee training.
4. Can small businesses effectively implement DiD strategies?
Yes, small businesses can implement DiD strategies by prioritizing cost-effective and scalable solutions. Cloud-based security services, managed security providers, and integrating controls within existing tools like Microsoft 365 or Google Workspace can provide robust protection without overwhelming resources.
5. What are the implications of remote work and BYOD policies on DiD strategies?
Remote work and BYOD policies increase the attack surface, making DiD even more essential. Organizations must implement additional layers, such as endpoint security, VPNs, and strict access controls, to protect remote devices and ensure secure communication.
Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Explore more
research & insights curated to help you earn a seat at the table.