The traditional security strategies focused on securing the perimeters to protect internal networks. Often referred to as the Castle and Moat approach, these tactics emphasized the creation of defenses (Moats) to prevent external access (into the castle or data centers) while trusting internal sources.
Fast forward to the days of multi-cloud environments and blurred boundaries with distributed environments, remote work, and mobile access, we find ourselves in an era of shared responsibility and zero trust. Data Security Posture Management, DSPM for short, is a clear response to cloud adoption.
With cloud adoption by 94% of enterprises among companies with more than 1000 employees, comprehensive security strategies like DSPM are an absolute must-have. Broadly, a DSPM solution helps secure different data components across cloud environments and is a reliable approach for the evolving threat landscape.
Read on to understand how DSPMs work, some of their use cases for maintaining cloud data security and how they differ from other solutions like CSPM and CIEM.
What is data security posture management?
Data security posture management is the process of incorporating a set of practices and deploying necessary tools to protect local and cloud data assets. The approach aims to implement airtight security controls to safeguard sensitive information from unauthorized access, theft, and disclosure.
How is DSPM helpful for modern businesses?
Given the fragmented nature of cloud infrastructure, modern organizations require a deep-rooted understanding of data and its role in aiding better security decisions.
Leveraging data-driven insights for enhanced security translates into a strong security posture. This also allows organizations to portray a high level of confidence at contract engagements, allowing for better business opportunities.
The following are the benefits of DSPM for modern organizations:
Data security across the lifecycle
DSPM security solutions help classify sensitive data and safeguard it across lifecycle stages—discovery, storage, transmission, and disposal. These tools gauge aspects such as policy enforcement, misconfigurations, overly permissive settings, etc., and implement strong controls to ensure tighter data security.
Meeting compliance requirements
DSPM solutions streamline compliance processes around data protection, such as mapping regulatory requirements, ensuring access controls, encryption, firewall rules, etc. This ensures that the organization checks multiple boxes with respect to data protection frameworks like HIPAA and GDPR.
How Sprinto enables this function:
Pairing your DSPM solution with Sprinto can help you continuously monitor your compliance status while helping you manage compliance risks to a greater degree. Sprinto is purpose-built for cloud-first companies and helps expedite the time needed to get audit-ready.
Cost reduction
Data security management enables cost efficiency on multiple fronts. It directly results in fewer regulatory and legal penalties as a result of continuous compliance, more efficient resource allocation, and reduced downtime. It also helps organizations bring down long-term cost since it only requires a single instance of setup.
Drive scalability
DSPM tools can ensure the same data hygiene and security practices while accommodating increasing volume and functionality. Forward-thinking organizations count on DSPM’s centralized management capabilities, automation capabilities, and scalable systems for their evolving needs.
How does Data Security Posture Management work?
Database security management provides transparency and understanding about sensitive data. It affords complete visibility across data activity, access, usage and compliance and gives a comprehensive review of the security posture.
Essentially, a DSPM solution works in four phases:
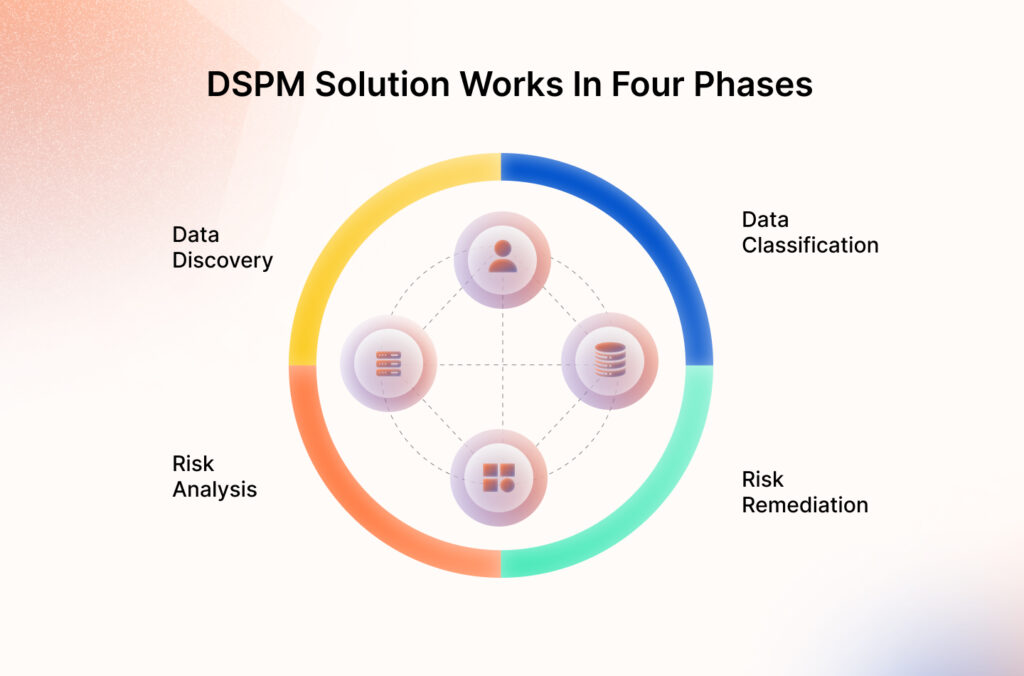
Data discovery
On-cloud data is typically stored in silos. It is spread across IAAS, PaaS, virtual machine databases etc. DSPM consolidates all the data, whether structured, unstructured, at rest, or in transit, and catalogs it along with the source. This is done using a combination of integration with the organization’s data management and security tools and in-built automated data discovery mechanisms.
Data classification
Next, the DSPM tool classifies data sets across sources based on sensitivity. This is done using a combination of content analysis techniques, AI, Machine learning, metadata or tagging, any user classification (such as a document named as confidential) etc. Information such as PII, PHI, credit card details etc. is classified as sensitive information to prioritize access controls and encryption.
Risk analysis
DSPM then conducts an analysis of the risks associated with misconfigurations, excessive permissions, compliance violations, and other threats or vulnerabilities that could compromise data security. Critical issues are highlighted in the risk assessment along with impact scenarios. There may be risk scores or visual representations of risks to facilitate better understanding.
Risk remediation
Lastly, DSPM facilitates remediation guidance for minimizing risk impact. The remediation recommendations include policy changes, restricting any user or account privileges, and implementation of other security controls. An audit trail of actions initiated is maintained, which is helpful during compliance audits.
Also, read: Data Privacy Week in 2025
Key components of DSPM
The key components of a DSPM solution consist of elements that shape the scope of the program. These are a combination of tools, processes, and mechanisms that help enhance overall data security posture.
Here are the 5 key components of DSPM you should know:

Continuous data monitoring and data lineage
DSPM facilitates tracking of data-related events that impact security and compliance. This is done post data discovery and classification. Logs of user activities are maintained and the solution flags potential risks, vulnerabilities, or suspicious behavior.
Continuous data monitoring also includes the data lineage component. Data lineage tracks the transformation of data throughout its lifecycle. Any changes in data at the time of processing at any stage of the ecosystem are assessed for risks and documented for reporting security gaps.
Control management
The control management component of database security management ensures the enforcement of security policies. Controls such as access permissions, multi-factor authentication, data encryption, backup and recovery etc. are implemented across data sets to maintain a strong security posture.
Incident response workflows
A DSPM solution has in-built workflows to identify security incidents, raise alerts for triage, and initiate recovery mechanisms for efficient response. Some advanced tools also have forensic capabilities for root-cause analysis.
Integration with threat intelligence
DSPM tools can integrate with threat intelligence feeds to stay abreast of emerging threats and fine-tune control management. Rule-based adjustments can be made to optimize security checks to accommodate evolving requirements.
Compliance management
The compliance management function of DSPM ensures the adherence to data privacy and protection laws by providing users with a nuanced understanding of the compliance environment. Compliance requirements are mapped to the classified data categories, monitored regularly, and reported on a unified compliance dashboard.
Checkout: 7 Best Compliance Automation Tools in 2023
Sprinto can help you with continuous compliance monitoring to ensure 100% audit success.
Use cases of Data Security Posture Management
From analyzing security risks impacting data to real-time response to a threat, DSPM solves several data problems for businesses.
Here are a few use cases of data security posture management:
Threat detection
DSPM can automatically discover and categorize data stored on cloud or on-prem data stores. Both data repositories and data flows are analyzed to identify scenarios like shadow databases (created without the organization’s knowledge/approval), unsecured data pipelines, and other security issues.
Data Access Governance
DSPM tools have data access intelligence to monitor access rights across diverse data stores. Cloud environments facilitate a lot of data sharing and collaboration. This mandates the monitoring of access, permissions, and privileges in order to preserve the confidentiality, integrity, and availability of data. For example, if an organization deals with PHI, DSPM will monitor access to ePHI, ensure strict access control, and encrypt or mask critical data.
Compliance with privacy regulations
DSPM solutions map regulatory requirements with the organization’s data policies to ensure compliance. Data privacy laws like GDPR, HIPAA, PCI compliance, etc. mandate the protection of sensitive data, and DSPM can identify the processes that govern data to detect any compliance violations.
Data loss prevention
DSPM facilitates the prevention of unauthorized access, data leakage, theft, or malicious processing of sensitive data. Measures like data encryption, endpoint detection, user behavior analytics etc. are employed to safeguard data. So if a disgruntled ex-employee tries to exfiltrate confidential data by exploiting delayed access removal, DSPM can raise an alert and prevent theft.
How to implement DSPM?
Implementing a DSPM complements your traditional security practices by bringing in better data awareness and tighter controls. It is crucial to clearly understand the organization’s security priorities in order to choose and deploy the right solution.
Here are the steps to implement an effective DSPM program:
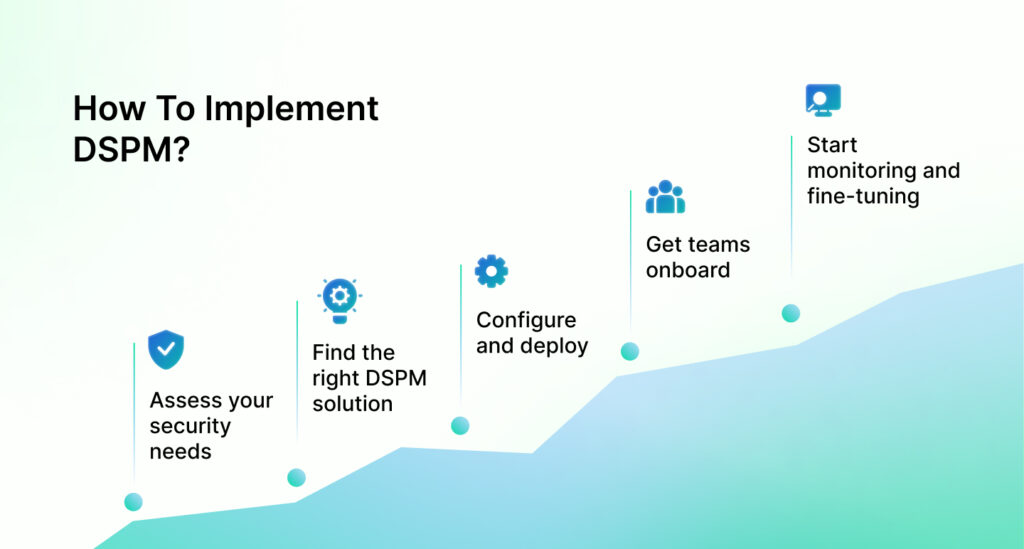
Assess your security needs
Before investing in a DSPM solution, assess the security challenges that need to be addressed. Take stock of the data that needs to be protected and the security mechanisms in place. Make a checklist of questions like:
- What are the current access controls?
- Are there any data backup and recovery processes?
- Is the data encrypted during transmission?
Additionally, understand the data privacy and protection regulations that apply to your organization.
Find the right DSPM solution
Research reputable DSPM vendors and send Request for Information (RFI/RFP). Arrange for demos and trials after screening solutions on:
- Budget friendliness: Confirm if add-on features cost extra and evaluate ROI
- User-friendliness: Evaluate if the non-technical stakeholders will be able to navigate easily through the platform
- Feature set and key capabilities: Look for key features like data classification, access governance monitoring, encryption etc.
- Integration options: Analyze integration capabilities with existing security infrastructure
- Scalability: Assess if the DSPM’s performance will be impacted by increased volume of data
- Support: Ask for training and vendor support
Configure and deploy
Integrate your tech stack with the solution and create an inventory of data assets. Tag data to help the DSPM classify data more accurately. Configure other settings to tailor the solution as per needs and map relevant controls. Set up a real-time monitoring mechanism and create a phased deployment plan.
Get teams onboard
Once you are done with the setup, get your teams on board to roll out the implementation plan that includes all policies and SOPs. Set up a training program to empower security teams to get onboard and initiate work. Establish roles and responsibilities and prioritize tasks based on criticality.
Start monitoring and fine-tuning
Establish key performance indicators and define a review period for monitoring performance. Conduct vulnerability assessments, penetration testing and internal audits to evaluate DSPM effectiveness and encourage stakeholder feedback. Review and refine policies to ensure continual improvement.
How much will it cost to implement DSPM?
Apart from the organization’s size, DSPM costs can vary based on factors like specific regulatory requirements and choice of solution, customization requirements, support and maintenance required, etc. DSPM solutions can cost a small and mid-sized business about $50000 a year. For large enterprises, the costs can go up to $500,000 per year.
The benefits of a DSPM can outweigh the costs. Streamlined operations and right resource allocation can go a long way in avoiding penalties and fines while reducing the probability of data breaches.
What’s the difference between DSPM, CSPM, and CIEM?
Cloud Security Posture Management (CSPM) helps organizations secure their cloud infrastructure. It scans for misconfigurations, vulnerabilities, enforcement of security policies and compliance adherence across the cloud environment.
Checkout: Most Recommended CSPM Tools in 2023
Cloud Identity and Entitlement Management (CIEM) helps automate privilege management across multiple cloud environments. It manages user identities, access controls, and flags overused or ineffective privileges that could affect the security of the cloud infrastructure.
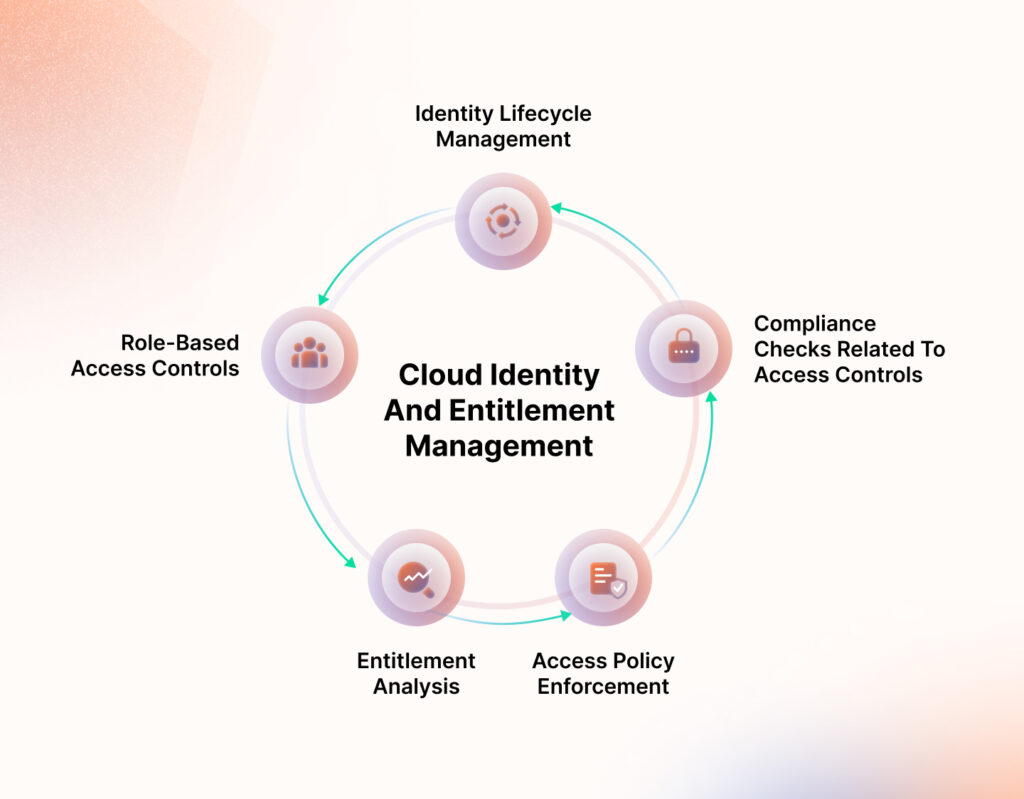
While both of these are cloud-infrastructure-centric, DSPM is a data-centric approach. CSPM and CIEM do not have context about the data—where it comes from, what type of data is affected, is it sensitive? etc.
Let us look at the key differences between the three:
| DSPM | CSPM | CIEM | |
| Focus | Ensuring better control over on-premise and cloud data | Enhancing the security of cloud infrastructure by preventing misconfigurations, faulty settings, etc. | Managing access, privileges, and entitlements across cloud environments |
| Scope of Coverage | Visibility into the location of sensitive data and raising contextual alerts | Visibility into policy enforcement and cloud infrastructure without providing the context of data affected | Visibility into cloud identity and access management controls |
| Key capabilities | Data discovery & classification Data encryption Managing access controls Risk analysis and remediation Compliance checks | Security posture monitoring Misconfiguration remediation Security policy enforcement Compliance management | Identity lifecycle management Role-based access controls Entitlement analysis Access policy enforcement Compliance checks related to access controls |
| Tools | Varonis data security platform, Securiti data security posture management, Dig security platform etc. | Prisma Cloud, Microsoft defender for cloud, Lacework etc. | Wiz, Sonrai, Okta identity cloud etc. |
Pairing your DSPM with Sprinto
While DSPM can be an excellent tool to provide context-rich information about data security, it cannot be used as a standalone tool for highly regulated industries. If you are subject to strict requirements from compliance standards like HIPAA, GDPR PCI DSS etc., you must pair your DSPM with a comprehensive compliance management solution.
Sprinto, a compliance autoation solution, goes beyond data security. It eliminates all the manual effort that goes into creating a compliance program by streamlining workflows, automating compliance checks, and ensuring the right controls are in place and working correctly.
Sprinto integrates with 100+ cloud services to enhance the scope of your compliance program across 15+ compliance and regulatory frameworks boasting a 100% audit success rate.
Read how Hubengage achieved ISO 27001 readiness in 15 hours and took an additional 10% effort to prepare for GDPR, HIPAA and SOC 2.
Get audit readiness in weeks rather than months. Talk to our experts today.
FAQs
DLP tools are designed to prevent data leaks and unauthorized disclosures. DSPM is a broader approach encompassing overall data protection beyond leaks, including access governance, encryption, compliance and security posture management.
The efficiency of the DSPM security solutions can be enhanced by integrating it with other technologies. These solutions include endpoint detection and response systems, identity and access management solutions, data loss prevention tools, network security and firewalls and vulnerability management tools among others.
DSPM can be limited in its coverage as it is data-centric and not infrastructure-centric. Next, there can be alert fatigue and notifications leading to false positives. Tasks like arranging workforce training and updating policies can feel time-consuming. The best way to solve these challenges is to take the automation route and pair DSPM with comprehensive solutions like Sprinto.
Payal Wadhwa
Payal is your friendly neighborhood compliance whiz who is also ISC2 certified! She turns perplexing compliance lingo into actionable advice about keeping your digital business safe and savvy. When she isn’t saving virtual worlds, she’s penning down poetic musings or lighting up local open mics. Cyber savvy by day, poet by night!
Explore more
research & insights curated to help you earn a seat at the table.






















