According to a report by Accenture, 43% of cyberattacks were aimed at SMBs, but only 14% were prepared to defend them. This is a direct indication of how important it is to have the right technological infrastructure. And so, what comprises of a good cybersecurity stack? Businesses are asking themselves this question more frequently with cybersecurity evolving into an infinitely complex space.
Effective cybersecurity stack implementation requires striking a balance. Theoretically, it is simple to assume that your defense will be more robust with more tools you use. This is true up to a degree, but then the benefits start to fade.
Adding too many tools can overly complicate your infrastructure and expose weaknesses in your system. The objective is to create an IT security stack that has as many practical capabilities as feasible without detracting from its main function.
What is a cybersecurity stack?
A cybersecurity stack combines several tools, technologies, and procedures to safeguard systems, networks, and data against potential online threats. It is intended to offer multiple defense layers against various attacks, weaknesses, and vulnerabilities.
Your cybersecurity stack functions as a central hub that connects all your systems and aligns them with the company’s security posture. A good stack should enable you to view all the tools you are using and the network systems they communicate with.
What are the key components of the cybersecurity stack?
A cybersecurity stack comprises many tools and processes that are put in place to strengthen the security of the organization.
Here are some of the tools used in a stack:

Identity and Access Management (IAM)
IAM systems manage user identities, access rights, and authentication procedures. You can use tools like privileged access management (PAM) solutions, single sign-on (SSO), and multi-factor authentication (MFA) to make sure that only authorized users may access resources.
Endpoint Security
Every end-point or managed device needs to be made secure to ensure there are no vulnerabilities while accessing sensitive data outside the primary network. This includes laptops, mobile devices, and desktops. A few examples of common components of endpoint security are firewalls and endpoint detection and response (EDR) systems.
Network Security
Enhancing network security aims to monitor and manage network traffic, identify suspicious activities, and stop unauthorized access. Installing tools like firewalls, network segmentation programs, and intrusion detection and prevention systems (IDS/IPS) can improve network security.
Security Information and Event Management (SIEM)
SIEM software collects and analyses security logs and events from multiple systems and applications in order to look for possible risks. To help identify security incidents, they offer real-time monitoring, correlation, and alerting capabilities.
Data Loss Prevention (DLP)
DLP tools keep track of sensitive data and guard against unauthorized access, transmission, or leaking. They can enforce encryption rules or find and stop efforts at data exfiltration.
Security analytics
In order to find trends, recognize abnormalities, and expose possible security events or threats, security analytics systems use machine learning and data analysis approaches. They are capable of conducting extensive data analysis to find sophisticated attacks and other advanced persistent threats (APTs).
Vulnerability management
Vulnerability management tools scan networks and systems for known vulnerabilities, prioritize them based on severity, and provide remedial guidance. Compliance automation tools, such as Sprinto, help organizations in their vulnerability management by enabling them to monitor their security controls from a central dashboard.
The specific tools vary depending on the organization and their needs however, the objective is to put in place a complete set of measures that cooperate to mitigate risks and protect the company’s digital assets.
How to build a cybersecurity stack?
It is essential to have a robust cybersecurity governance framework before you start developing your stack. According to PwC’s 2018 Global State of Information Security Survey, 44% of 9,500 executives lacked a comprehensive information security plan.

Here are the four steps to build a cybersecurity stack:
1. Assess your business risk areas
Prioritize the cybersecurity risks that will have the greatest long-term impact on the organization by identifying the most significant issues. It is also recommended to use the NIST framework, which provides five principles for addressing cyber risks from start to finish: identification, detection, protection, response, and recovery.
2. Implement multiple levels of security
The next step in creating a robust stack is by investing in technology to ensure that your data and employees are safe from cyber-attacks.In order to minimize the risk associated with your network being one large entity, consider breaking it down into smaller segments and implement security measures for each one of them. Your system should have many layers of protection, with stronger security measures added to each one.
Recommended: Guide to VAPT in cyber security.
3. Plan for interoperability and integration
Make sure the various parts of your cybersecurity stack can integrate and cooperate efficiently. Think about the information sharing, data exchange, and comprehensive perspective of your security posture that these products offer. Integration can increase the effectiveness of security measures overall and in detecting threats and responding to incidents.
4. Keep your stack updated
For a cybersecurity stack to stay effective, it needs constant maintenance, updating, and monitoring. Implement procedures for keeping an eye on security occurrences, reviewing logs, and handling emergencies.
Update and patch your systems frequently, and stay informed of new threats and weaknesses. To improve your security capabilities, think about setting up a security operations center (SOC) or collaborating with a managed security service provider (MSSP).
Building a robust cybersecurity stack is part of the spectrum. Maintaining it, however, requires continuous time and effort from the organization. There are regulatory frameworks such as ISO 27001 and SOC 2 that focus heavily on the security posture of a company. To make things easier, you can invest in a compliance automation tool such as Sprinto. Its continuous monitoring feature keeps track of any failing controls and notifies you beforehand.
Check out a complete guide to cyber security compliance.
Benefits of a cybersecurity stack
For businesses of all sizes, putting in place a solid cybersecurity stack has several advantages.
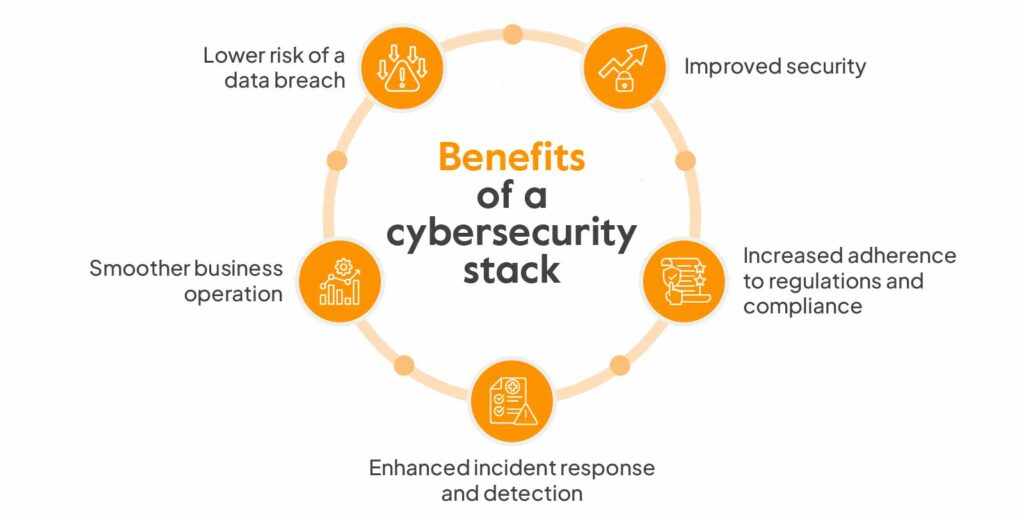
Here are some of the key benefits:
Lower risk of a data breach
The stack works to safeguard sensitive data from unauthorized access, leakage, and theft by combining various security techniques. This is especially crucial for businesses that deal with sensitive consumer information, financial information, or intellectual property.
Improved security
In order to defend against different threats, a cybersecurity stack offers numerous layers of protection, which lowers the possibility of cyberattacks. Each part of the stack addresses a different security issue, resulting in a more thorough and durable security posture.
Recommended: Best cybersecurity practices.
Increased adherence to regulations and compliance
Regulatory obligations and industry standards frequently align with a strong cybersecurity stack. By putting such procedures in place, businesses can comply with data privacy laws and regulations and prevent fines and reputational harm.
Enhanced incident response and detection
Security analytics and SIEM allow for the quicker detection of risks and security incidents. This enables quicker reactions to possible threats, cutting down on the amount of time an attacker may go unnoticed within the network.
Smoother business operation
Data breaches and ransomware attacks can seriously impair corporate operations. Organizations face numerous problems, such as loss of data, financial losses, supply chain disruptions, operational downtime, and more because of these attacks. With a cybersecurity stack in place, the organization is better prepared to handle incidents and disasters while minimizing disruptions.
Sprinto’s take on the cybersecurity stack
It is evident by now that a cybersecurity stack offers a multi-layered defense against cyber threats, helping organizations by boosting security, lowering the risk of data breaches, improving incident detection and response, guaranteeing compliance, and preserving business continuity.
However, a major reason SMBs go to such heights and lengths to improve their cybersecurity posture is that they need to get compliant with regulatory frameworks. Frameworks such as ISO 27001 and SOC 2 focus heavily on the security posture of the organization.
Sprinto is a compliance automation solution that allows organizations to become compliant in a matter of weeks. It provides a single dashboard where you can access all the controls that are tailored to your compliance needs. Sprinto streamlines the flow of compliance processes with features such as evidence collection, internal audits, and remediations.
Talk to our experts to embark on an error-free, automated journey of cybersecurity compliance.
FAQs
Yes, because cybersecurity is dynamic, a cybersecurity stack needs constant upkeep, upgrades, and periodic assessments to react to new threats and technological advancements.
A crucial component of a cybersecurity stack, cloud security safeguards data and applications housed in cloud environments and provides a safe cloud computing environment.
By monitoring and limiting access to sensitive data, components like data loss prevention and access controls assist limit the risk of insider threats while minimising the potential harm caused by malicious or negligent insiders.
Shivam Jha
Shivam is our in house cybersecurity sage with over six years of experience in cybersecurity under his belt. He is passionate about making the digital world safer for everyone and whipping up Indian delicacies on the weekend.
Explore more
research & insights curated to help you earn a seat at the table.






















