
Negligence in cybersecurity costs more than regulatory fines. It erodes your customer’s trust. This is precisely why most regulatory bodies, such as the International Organization for Standardization (ISO), PCI Security Standards Council (PCI SSC), or General Data Protection Regulation (GDPR), recommend a thorough compliance audit—aptly put, an assessment of your company’s first line of defense.
Compliance audits systematically evaluate your adherence to regulations. This includes evaluating your current position concerning laws, internal bylaws, regulations, and relevant industry practices. These audits not only protect you from threats but also help you identify and mitigate risks before they become catastrophic.
| TL;DR A compliance audit finds areas of non-compliance, helps to identify security or financial risks, and fills gaps that otherwise affect operational processes. The three types of compliance audits are internal, external, and surveillance audits. The process includes identification of scope, understanding the internal controls, conducting risk assessments, and documenting evidence. |
What is a compliance audit?
A compliance audit is a detailed review of an organization’s regulatory adherence to applicable laws, regulations, and internal guidelines. It assesses all documented procedures and reports of an organization’s activities, financial transactions, and information, and ascertains whether they comply with the defined rules and standards. The goal is to identify areas where compliance is lacking and address those gaps.
Why are compliance audits important?
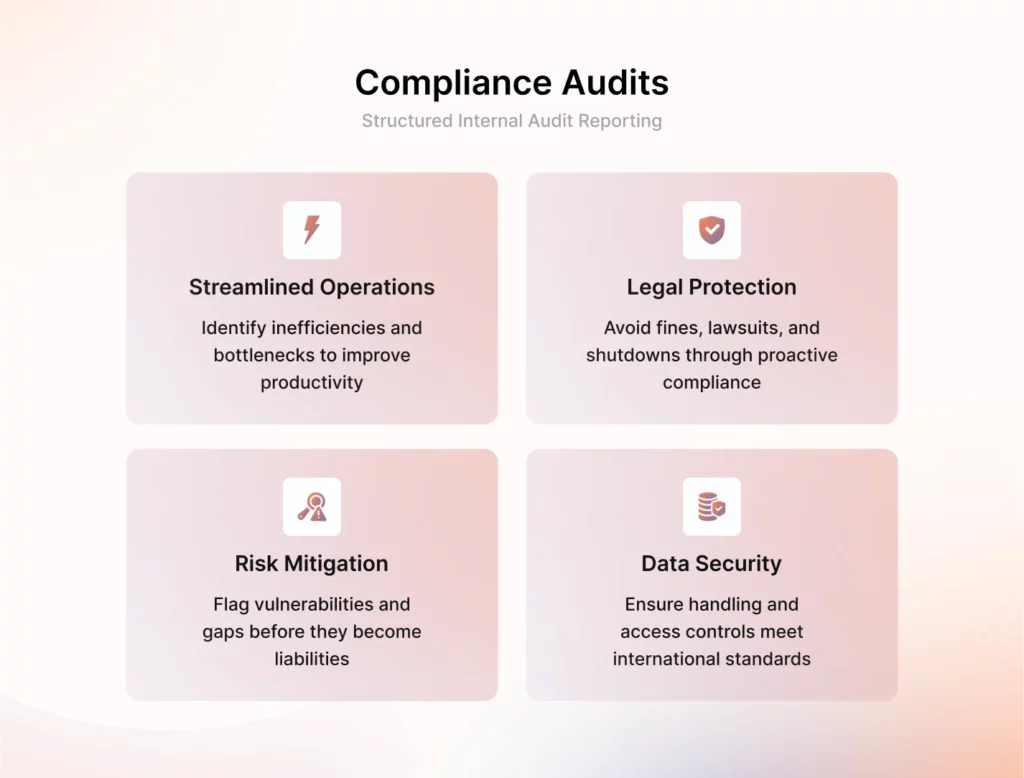
A compliance audit is important because it provides independent verification that an organization’s security controls meet required standards and are effectively implemented. A thorough audit aims to
- Identify or uncover inefficiencies and bottlenecks in the existing processes, thus paving the path for streamlined operations and improved productivity.
- Legally protects you from fines, lawsuits, and even shutdowns by proactively identifying areas of non-compliance early on in the system.
- Mitigates risks by flagging vulnerabilities and gaps before they become liabilities.
- Ensures data handling and access controls to ensure security practices are up to international standards.
What are the different types of compliance audits?
Compliance audits are divided into three broad categories: internal audit, external audit, and surveillance audit.

1. Internal audits
Internal compliance audits are self-assessments performed by organizations to evaluate their adherence to internal policies, procedures, control systems, and other processes.
| As per Rajiv Rajan, ISO Lead Auditor at Sprinto: An internal audit is like a litmus test for the effectiveness of controls. If you are at >90% mark, you are ready for an external audit. If not, you need to address the gaps it (internal audits) helps identify. |
2. External audits
An external audit is an independent evaluation of an organization’s internal controls, operations, security policies, and compliance with regulatory standards. Ideally, it is performed by an accredited independent third-party auditor to provide an unbiased evaluation.
3. Surveillance audits
Lastly, surveillance audits are periodic assessments that examine a company’s practices and ensure that they align with legal requirements, best practices, and business objectives. Surveillance audits are performed by organizations with a security certification (akin to ISO 27001). The principal idea behind the surveillance audits is to ensure that the organization continues to comply with the requirements and not just at the moment of initial certification.
What are the differences between internal and external audits?
Here’s how the supporting factors for internal and external audits differ from one another:
| Internal audit | External audit |
| Internal audits assess risk, internal controls that mitigate any risks, and compliance with internal guidelines. | An external audit evaluates compliance with external regulations and standards. |
| The scope of an internal audit can vary based on the company’s needs. | The scope of an external audit is generally dictated by a regulatory framework. |
| An internal auditor aims to identify areas for improvement and strategize accordingly. | In an external audit, the auditors scope out your position concerning the regulatory compliance that you have to follow. |
| The cost of an internal audit is generally low and can be a part of your operational expenses. | An external audit generally costs more as it requires external resources and specialized personnel. |
Compliance audit vs internal audit
Internal audit is a part of compliance audit and yet differs in several aspects. Here’s a drill-down on how a compliance audit differs from an internal audit.
| Feature | Compliance Audit | Internal Audit |
| Purpose | Verify adherence to external regulations or standards | Assess internal controls and processes proactively |
| Conducted by | External third-party auditors | Internal audit department |
| Scope | Specific frameworks (ISO 27001, GDPR, SOC 2) | Organization-wide security policies, risks, and controls |
| Stakeholders | Regulators, customers, and auditors | Management, board, security team |
The compliance audit process: 5 steps
The goal of a compliance audit is to build trust, reduce risks, and ensure long-term sustainability. The process is systematically divided into five key steps/phases, where each of these steps is aimed to be effective, economical, and comprehensive. Here are the 5 steps:

Step 1: Identify the scope and objective of your audit
A well-thought-out audit begins with established, clearly defined goals and boundaries. For the audit to be considered truly foundational and successful, here is what you need to do:
- Gain clarity about the subject of the audit
An audit begins with analyzing your company’s risk profile and prioritizing areas that significantly impact compliance and operations. For instance, this can be the assessment of the security of the electronic health record systems for healthcare companies or examining the process through which credit cards are transmitted for a financial company.
- Define the issue(s) that need to be examined
Define these issues based on the regulatory requirements, industry best practices, and risk factors specific to your industry.
- Identify patterns and draw inferences from previous audits
Your company’s previous audits could highlight potential issues like inconsistencies in data encryption standards, inadequate documentation, or gaps in following procedures. Next, understanding whether these issues have been persistent can help you look for emerging trends.
- Fix areas you want to focus on
Infosec measures data authentication, encryption, and authorization, and enables secure data transmission and access controls while maintaining the integrity of transactions. Having clarity about the areas to focus on saves both time and costs involved in the process.
- Ensure you have a comprehensive sampling strategy in place
Next, the strategy should consider the volume and complexity of the audit process. Having a solid sampling strategy helps auditors
- Ensure representativeness (reviewing the entire set of data and systems and not just a subset of it)
- Saves time and resources while reducing the risk of oversight
- And finally supports compliance with standards
Step 2: Understand the internal controls you have in place.
In the second step, the auditor thoroughly evaluates your implemented processes to ensure compliance with the laws, regulations, and internal policies. The entire process is carried out as follows:
- First, the auditor examines policies, risk assessments, and previous reports to understand the implemented compliance framework.
- The key personnel are then interviewed and examined about core processes and their real-life implementation.
- Next, a strategic sampling method is used to test whether controls function as intended.
- Finally, compliance gaps or deviations are identified and shared with the person in charge for clarification and initial feedback.
Step 3: Conduct a risk assessment
In the third step, the auditor recognizes all the areas and factors that could potentially compromise the organization’s security. The most commonly observed factors that could affect the safety measures of the organization are
- Changes in regulatory requirements
- Updates in compliance frameworks
- Alterations in the organizational structure
- Shifts in business operations
Next, the potential risks are identified and are scored based on the likelihood of occurrence and potential impact. The risks are prioritized based on a higher score, i.e,
| Risk = Probability x Impact |
In addition to defining the scope and objectives, the audit team implements an assessment technique to evaluate the current risk mitigation strategies. Further, focus on risk mitigation and governance is strengthened by
- Reviewing previous audits and corrective actions implemented by the company.
- Analyzing industry trends.
- Identifying patterns and spotting anomalies using advanced data analytics tools.
Step 4: Collect and document evidence
In this step, all the evidence is gathered and documented. The process begins with a review of all compliance frameworks and requirements, which then leads to a checklist of the necessary documents, logs, and records.
Meticulous evidence collection coupled with strategic documentation practices allows you to identify security gaps and seamlessly communicate them with external compliance auditors. Similarly, having a readily available audit trail allows you to efficiently verify and demonstrate compliance just by reviewing documentation.
Step 5: Maintain audit-grade evidence
Not all evidence is created equal; hence, when auditing, evidence that meets criteria for completeness, authenticity, and accuracy is considered. Maintaining evidence tells the auditors that you are adhering to the security protocols and regulations consistently and not just preparing for an audit.
To ensure your audience is receptive and can communicate effectively with an auditor, ensure the following steps:
- Establish clear policies on what needs to be retained, what qualifies as evidence, and how long before the evidence runs past its statute of limitations.
- Document the history of evidence collection, who handled it, timestamps, digital signatures, and other verification procedures to ensure the authenticity of the documents.
- Store these documents securely and reliably, making them tamper-proof. Auditors expect the highest reporting standards, so they suggest using data encryption methods and regular backups to prevent data loss due to corruption.
How to prepare for a compliance audit?
For most businesses, a compliance audit is a valuable opportunity to understand their stance on compliance, identify areas for improvement, and measure the effectiveness of controls. The process begins with a comprehensive review of the company’s compliance policies, security controls, management standards, external regulations, compliance audit software, and internal business processes.
Try identifying and addressing any gaps or inconsistencies in your findings. This can significantly reduce the compliance auditor’s time to complete the audit. Next, gather evidence and all relevant documentation that demonstrate your compliance efforts. This can include your company’s policies on risks, training records, incident response plans, and anything else that supports your claims of compliance.
If possible, conduct a mock audit. It will help you familiarize yourself with the process and address any vulnerabilities before the official audit.
Best practices for successful compliance audits
Here are three key things to consider to improve your chances for a successful compliance audit.
1. Leverage automation
Automate predictable and repeatable processes. Automation allows you to streamline tasks like evidence collection, improve your risk assessments, layer multiple frameworks on top of each other, and create compliance checklists, among a host of other functions.
For instance, Sprinto’s audit hub empowers users to manage multiple audits at once, automate evidence collection and sampling, and ultimately, collaborate with auditors in real-time. Watch Sprinto in action here.
2. Delegate
Once you are aligned with compliance checklists and standards, clear about the scope of work, and have identified the team’s strengths and challenges, delegate responsibilities and strategically distribute tasks. There should be a clear division of responsibilities, expectations, and deadlines to achieve the best possible results.
3. Document everything
Documentation serves as the backbone of an audit in action. Documentation accuracy retains tangible evidence of your compliance efforts and the effectiveness of the controls. These documents include policies, incident reports, procedures, and any other material you may possess.
Easing compliance audits with Sprinto
Audits are important, and there is no denying that. The challenges multiply as auditors find themselves in the middle of an audit with documents, each of thousands of pages, and scouring for evidence. On the other hand, most companies find themselves in a struggle to engage in a hard dialogue with the auditors. The absence of a common platform for viewing evidence and communication makes the entire process a hard path to tread.
Luckily, this is where a GRC platform like Sprinto comes in. Here’s why auditors prefer working with Sprinto:
- Centralized auditor dashboard: Sprinto provides a dedicated, role-specific dashboard for auditors to access all compliance data, eliminating back-and-forth and version control issues.
- Pre-mapped, verified evidence: All control-specific evidence is automatically collected and linked to relevant framework requirements, verified via Sprinto’s built-in workflows and audit trails.
- Minimal prep, maximum clarity: Policies, documents, and system logs are organized and accessible in just a few clicks, reducing manual collation time and chances of oversight.
- Audit-ready by design: Sprinto aligns evidence presentation with how auditors review it: structured, chronological, and framework-specific, so the review process is faster and frictionless.
- Reduced audit fatigue: By removing ambiguity and administrative overhead, Sprinto helps both teams focus on the controls that matter, enabling cleaner, faster certifications.

Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Explore more
research & insights curated to help you earn a seat at the table.
















