
Evidence Mapping: The Ultimate Guide
Keeping track of all the collected evidence for audits or compliance can be tricky. With hundreds of internal documents, reports, and records, it’s easy to feel lost or unsure where to start. That’s where evidence mapping comes in. It organizes information clearly, highlights what’s complete, and makes it easier to spot gaps. In this blog,…
What is Risk Management? A Complete Guide for Growing Businesses
If you run a growing company, things will go wrong at some point: systems fail during peak loads, rules change mid-quarter, or a vendor can trip controls. To avoid panic, you must operate a risk program that turns surprises into planned responses. Risk management helps spot and shorten incident response before they become disasters. As…
Understanding Risk Mitigation: Purpose, Strategies, and Best Practices
What if a single cyberattack or supply chain failure could halt your operations overnight? Preventing such scenarios requires a sophisticated security framework for organizations managing vast data stacks and complex processes. This is where risk mitigation becomes essential! It helps you prepare today so risks don’t derail business operations tomorrow. In this blog, we’ll explore…
A complete guide for Audit-grade Evidence Collection
Frantic strokes battering keyboards, spreadsheets cramming up the screens, screenshots getting pulled from scattered Slack threads, and last-minute emails begging for old logs flooding inboxes. That’s how audit seasons look for most teams – not a process, but a last-minute scramble that drowns everyone in chaos. And when the audit fails, it’s rarely from a…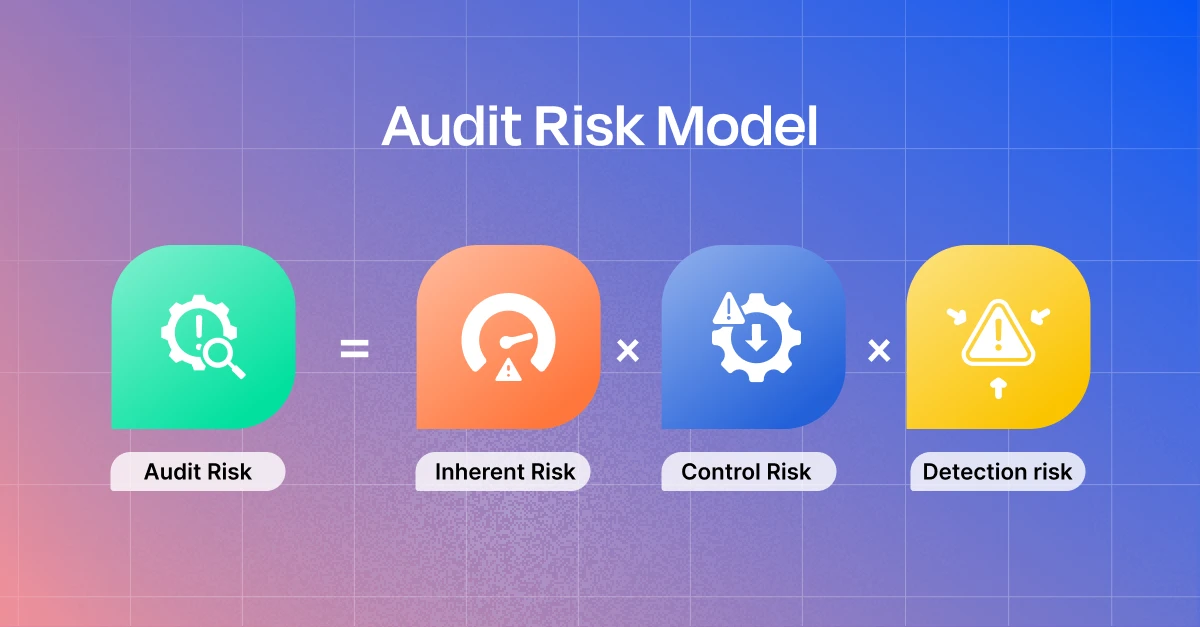
Audit Risk Model: Risk Types, Formula, Calculation, Score
The audit risk model brings out the mathematics behind an auditor’s discretion of your security controls and the confidence they have in your cybersecurity posture. The model revolves around the uncertainty that exists within every business transaction, financial statement, security control and corporate decision. Having said that, it’s still not a rigid rule book. This…
