
A Beginner-friendly Guide to ISO 27001 Data Protection Policy
Somewhere, in a dusty corner of your office, lies a document titled ‘Data Protection Policy.’ It’s a well-intentioned file, full of dense paragraphs and legal jargon. As you expect, most employees have never read it, and those who have probably forgotten what it said moments later. This situation is too common, while it shouldn’t be. The…
Vanta vs Drata vs Delve: Which Compliance Tool Fits You?
When sales questionnaires pile up, or a potential client asks for SOC 2, you need a platform that pulls evidence automatically, keeps controls organized, and gets you over the audit line without stealing weeks. Vanta, Drata, and Delve all promise to do that, but they come at it differently—Vanta comes with scale and a big…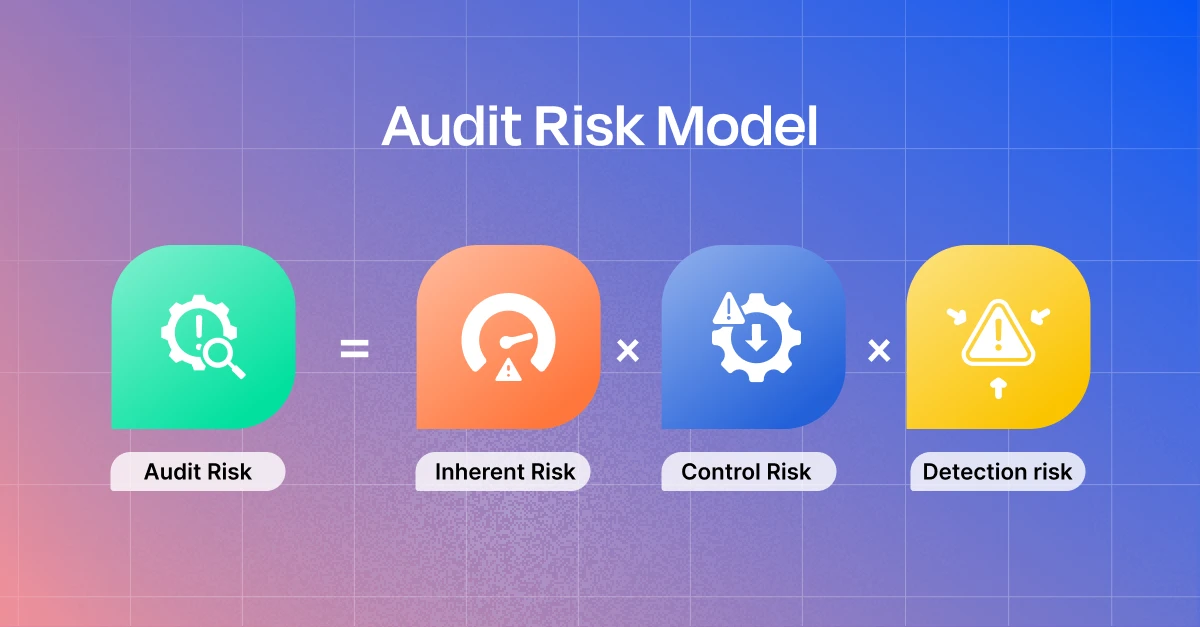
Audit Risk Model: Risk Types, Formula, Calculation, Score
The audit risk model brings out the mathematics behind an auditor’s discretion of your security controls and the confidence they have in your cybersecurity posture. The model revolves around the uncertainty that exists within every business transaction, financial statement, security control and corporate decision. Having said that, it’s still not a rigid rule book. This…
PCI DSS for Fintech: Requirements, Steps, Levels
Fintech companies handle sensitive financial data every day, often moving across multiple systems, partners, and geographies. For them, PCI DSS compliance is a legal requirement and a sign to customers that their payment information is safe. These standards safeguard Cardholder Data Environments (CDE) against breaches, fraud, and misuse. Yet, meeting them can be challenging in…
100+ Compliance Statistics You Should Know in 2025
We have noticed that over the past few years, compliance has become one of the biggest priorities for organizations of all shapes and sizes. And there’s good reason for that. A rapidly growing threat landscape, a series of high-profile data breaches, and the first AI-specific compliance, have raised both the scrutiny and the price of…
