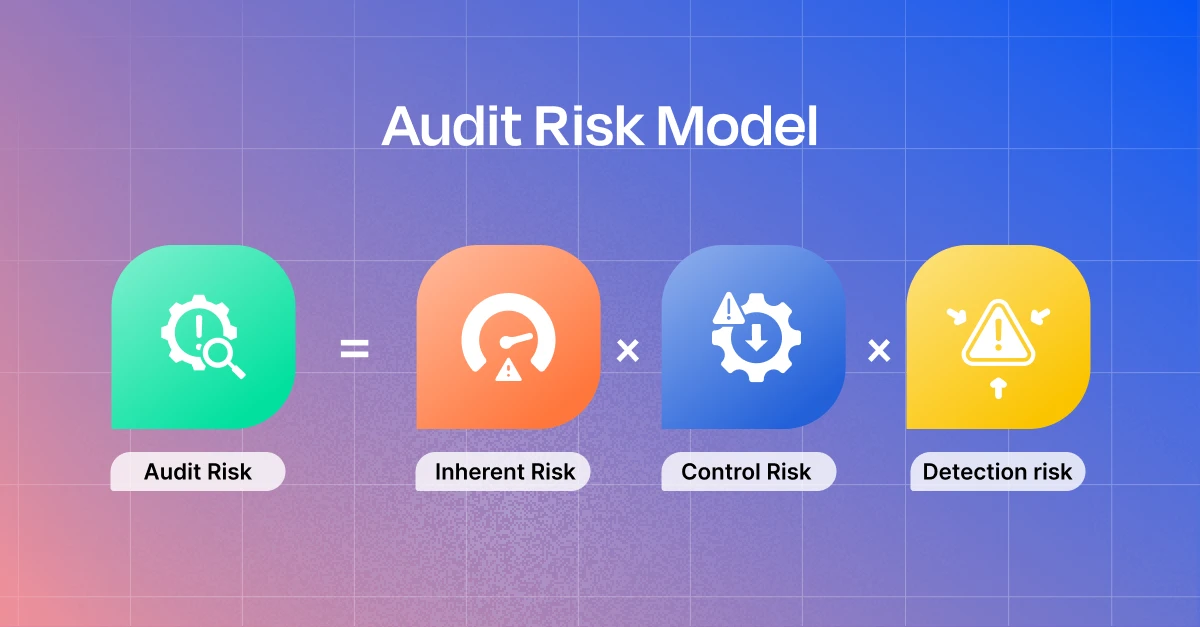
The audit risk model brings out the mathematics behind an auditor’s discretion of your security controls and the confidence they have in your cybersecurity posture.
The model revolves around the uncertainty that exists within every business transaction, financial statement, security control and corporate decision. Having said that, it’s still not a rigid rule book.
This article explores the core meaning of ARM, the types of risks incorporated within it, the formula used for calculation, a cybersecurity audit risk example, and how it differs from audit assurance. Let’s dive in.
- The audit risk model uses a mathematical formula to calculate the different types of audit risks that the audit may come across.
- The overall audit risk score is obtained by multiplying inherent risk, control risk, and detection risks.
- Audit assurance is the percentage on how confident an auditor is about the audit results and the risks associated.
What is an Audit Risk Model (ARM)?
An Audit Risk Model (ARM) is a classical tool used by external auditors to assess and manage potential types of risks that may appear during an audit. ARM breaks the audit into inherent risks, control risks, and detection risks.
An audit risk model helps auditors decide what and how much evidence is required against different types of risks. It forms part of the strategic decision-making process before conducting an audit.
Breaking down an audit into 3 risks
Auditors are responsible for planning and conducting audits to ensure that audit reports do not contain major errors or fraud (also called material misstatements). To do this, they focus on three types of audit risks: inherent, control, and detection risks.
1. Inherent risk
Inherent risks are mistakes that may happen naturally due to the complexity of the business, industry, or transactions.
In cybersecurity, inherent risk could point to the likelihood of a material misstatement or non-compliance with regulatory frameworks. This is even before the auditor considers any internal controls.
For example, meeting compliance standards like HIPAA or GDPR may have higher inherent risks due to their strict requirements and complex measures. A higher inherent risk indicates a greater chance of failing to meet compliance obligations.
2. Control risk
The second type of audit risk is control risk. These are the most common types and refer to the likelihood that an organization’s internal controls fail to detect or prevent non-compliance.
Auditors usually assess this risk at the overall compliance level and for specific assertions. However, they can only do so if they deeply understand the business’s internal control systems.
So, they require a holistic view of the control architecture of the organization. Here’s an example:
3. Detection risk
The third and final type of audit risk is detection risk. It occurs when an auditor’s testing and procedures fail to uncover material non-compliance. A high detection risk score means that errors are more likely to be found during an audit, so the auditor suggests less rigorous control testing.
Conversely, a low detection risk score points to a lower likelihood of catching errors. So, the auditor required more thorough tests of control.
Auditors can manage detection risk by carefully planning the scope, timing, and depth of their processes and evident collection so that any material misstatements are identified and addressed early on.
The formula used in an audit risk model
The main audit risk formula used in this model is:
Audit risk = Inherent risk * Control risk * Detection risk
This brings us to the question of how the above risks are actually quantified so that a business or auditor can calculate the overall audit risk.
Audit risk model calculation and example
Although the audit risk model is generally used for financial businesses, it can also be beneficial for evaluating compliance audits.
Let’s imagine a scenario where a healthcare entity based in the U.S. has hired an external auditor or an audit firm to perform a cybersecurity audit based on SOC 2 security trust service criteria.
Calculating the inherent risk:
The business operates on the cloud, exposing it to a wide threat landscape of cyberattacks and breaches. Plus, it handles sensitive customer data like PII (personally identifiable information), adding to its regulatory requirements (HIPAA) complexity.
So, the auditor finds an inherent risk of 70%, considering its complexity and industry.
Control risk assessment:
While the business has implemented basic security controls like firewalls and access management, it missed out on a dedicated SOC team, and there is no workflow set for logging and reviewing security incidents.
After the risk assessment, the control risk score reaches 60% due to gaps in the execution and governance of controls.
Assessing detection risk score:
In most cases, an auditor would use a tool to review evidence provided by the business. Even if the audit process is thorough, complexity and limited access to log data may cause gaps in identifying intricate information.
Suppose the detection risk is set at 24%, which is moderate, taking into account system and procedural limitations.
As per the audit risk model formula,
Audit Risk = Inherent Risk × Control Risk × Detection Risk
= 0.70 × 0.60 × 0.24
= 0.1008 (10.08%)
Acceptable audit risk vs audit assurance
Acceptable audit risk is the amount of risk an auditor will take when giving a “clean” report. A “clean” report means the auditor believes the controls are accurate and free of significant errors.
Even then, the auditor accepts a certain level of risk that there might still be some unnoticed mistakes, but they believe it’s low enough that it won’t affect the overall accuracy of the report.
In contrast, the audit assurance score is the level of confidence an auditor has in the security controls implemented by the business and aggregate audit risk. It is calculated simply by subtracting the audit risk from 100%.
For example, referring to the above example, suppose the auditor has decided to accept the final audit risk at 10.08%. Then, the audit assurance score is 100%—10.08% = 89.92%.
Elevate your audits– A dedicated auditor’s dashboard
Audits come with multiple pain points like endless manual checks, an overwhelming number of Excel sheets, slow and error-prone workflows, etc. Even with methods such as an audit risk model, the chances of getting it wrong are high due to the sheer volume of information that can easily be overlooked or misinterpreted.
Now, combine this with the pressure to meet business compliance deadlines while managing multiple stakeholders. (Let’s take a deep breath.)
The solution? A GRC (Governance, Risk, and Compliance) automation tool like Sprinto, with its dedicated audit dashboard, makes things easier for both the business and the auditor.
You can expect higher accuracy and faster execution with features like
- Audit review status: Track progress in real-time, ensuring efficiency and clarity.
- Compliance gap report: Areas needing attention are highlighted to prevent overlooking issues.
- Risk reports: Provides a clear picture of vulnerabilities, helping prioritize actions.
- Vendor analysis: Assesses third-party risks efficiently.
Sprinto doesn’t just simplify the process; it empowers auditors to work smarter and more confidently, reducing the strain of missing key details.
With the combination of a powerful tool like the audit risk model along with a dedicated auditor’s dashboard, you can transform the way audits are conducted. Embrace the power of automation and elevate your audits to new levels of precision and ease.
Frequently asked questions
1. What are some common types of audit risks?
Audit risks are potential issues that could lead to incorrect audit conclusions. The common types include:
- Inherent risk: The susceptibility of an assertion to a material misstatement before considering any related controls.
- Control risk: The risk that a material misstatement could occur in an assertion and not be prevented or detected on a timely basis by the entity’s internal controls.
- Detection risk: The risk that the auditor’s procedures will not detect a material misstatement that exists in an assertion.
2. What is a risk-based audit model?
A risk-based audit model prioritizes audit efforts on areas with the highest risk of material misstatement. The auditor assesses the business’s internal controls and inherent risks to focus resources on areas most likely to have significant errors, thus enhancing the audit’s effectiveness and efficiency.
3. What is the relationship between the audit risk model and materiality?
Materiality is the threshold above which a misstatement is considered significant. The auditor adjusts detection risk based on the assessed levels of inherent and control risks, with materiality guiding the threshold of what constitutes a significant misstatement. Higher materiality levels can allow for higher detection risk, whereas lower materiality levels require lower detection risk to keep the overall audit risk within acceptable limits.
4. How to measure audit risk?
Audit risk is measured through the assessment of its components: inherent, control, and detection risks. The auditor combines these assessments to gauge the overall audit risk and adjusts their audit approach accordingly to ensure the risk remains within acceptable levels.
5. What are the components of the audit risk model?
The audit risk model is usually expressed as an audit formula that shows how the three types of risk multiply together to determine overall audit risk.:
Audit Risk (AR) = Inherent Risk (IR) × Control Risk (CR) × Detection Risk (DR)
Each component reflects a distinct dimension of audit uncertainty and helps auditors structure their testing strategies.
6. How do I calculate audit risk using the audit risk model?
To calculate audit risk:
- Assess Inherent Risk (IR): Likelihood of misstatement before controls.
- Assess Control Risk (CR): Likelihood that internal controls fail to detect/prevent misstatements.
- Assess Detection Risk (DR): Likelihood that audit procedures fail to catch misstatements.
- Multiplying these factors provides the overall Audit Risk (AR).
7. What role does the audit risk model play in internal controls?
The audit risk model highlights the importance of internal controls in mitigating risks. Strong internal controls reduce control risk, allowing auditors to adjust detection risk upward (reducing the extent of detailed audit testing). Conversely, weak internal controls increase the auditor’s testing burden.
8. How can auditors use the audit risk model to plan audit procedures?
Auditors apply the audit risk model during audit planning to:
- Identify areas of high risk that require greater focus.
- Determine the extent, timing, and nature of audit tests.
- Balance substantive procedures and reliance on controls.
- Align audit resources with the areas most likely to impact financial statement reliability.
Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Explore more
research & insights curated to help you earn a seat at the table.