When you grow to mid-market status, compliance is no longer about just passing audits. In fact, for many of you reading this, passing an audit barely represents a baseline for security. Instead, your goals revolve around keeping up with a risk-first world and maintaining market trust that you’ve worked hard to build.
With growing vendor networks, evolving regulatory requirements, and your own growth moves into new markets and new sectors, the real question is, “Do we have eyes on how the compliance system is holding up across our entire organization?”
That’s what compliance visibility gives you. Not just reports or checklists, but a real-time view into whether your controls are working. It’s about spotting gaps before they turn into issues, and being able to act before they turn into issues.
This is crucial because a compliance gap can result in financial penalties, a data breach can hugely impact business operations and erode years of client trust, and a system failure may amount to downtime impacting your service/product delivery.
Without visibility that connects the dots across frameworks, processes, and teams, you start losing track of where risk is building up, who’s responsible for the build-up, and what the potential impact is.
With visibility being so critical, understanding where visibility is breaking down is the first step toward building a stronger, more resilient compliance posture.
- Lack of compliance visibility doesn’t just delay audits, it quietly builds risk across teams, tools, and timelines.
- When you can’t see how controls are holding up, small issues like outdated access, missed reviews, or ownerless controls can escalate into major business threats.
- Understanding where visibility breaks down and how to build it into your workflows is key to staying ahead of risk, not just reacting to it.
5 Critical risk scenarios to watch out for
So where does visibility break down most often? Here are 5 critical risk moments where visibility gaps can turn into serious problems:
1. Inability to identify emerging risk patterns
Risks don’t appear out of nowhere and build over time through similar types of incidents under slightly different circumstances. These incidents are typically treated as isolated events, while the underlying weakness keeps resurfacing.
Let’s take the example of data breaches. It starts with user activity from an unfamiliar location, followed by suspicious activities like unauthorized access to sensitive data, unauthorized changes to network infrastructure, and/or locked-out accounts.
Together, these events show clear, escalating patterns pointing towards an active data breach in progress. Spotting and acting on these patterns early can help contain incidents before they turn into full-fledged crises. Moreover, it’s not just about catching one-off anomalies. The fact that an unauthorized account gained/ has access, or that a login that originated from an unusual geography didn’t flag a different workflow, already points to a repeating gap in process or control. Those aren’t isolated glitches—they’re early signs of a risk pattern forming.
Compliance visibility solves this problem by alerting teams to these incidents in real time.
So, even before the breach can escalate, your team can take containment measures.
2. Delayed response to material risk events
The longer a risk goes unnoticed, the harder and costlier it is to contain. Without control telemetry and timely alerts, critical risk events like third-party breaches, access misuse, and system misconfigurations can unfold quietly in the background.
Not having a timely response to security incidents opens your organization to potential legal, financial, and/or reputational damage. Consider the example of an employee accidentally clicking on a phishing email and unknowingly sharing their login credentials. Without any alerts for unusual activity, no anomalous-login or data-access alerts fire, so the attacker would be able to access sensitive internal files for days without anyone noticing. On the other hand, with compliance visibility in place, the same sequence should trigger correlated detections and a playbooked response:
- The identity provider flags the unusual sign-in (new geo/device/IP reputation) and forwards it to your SIEM.
- A response workflow runs: step-up auth or block the session per policy, revoke active tokens, and force a password reset.
- Temporarily restrict access to sensitive systems and notify the control owner/IR on-call to review.
- If malicious activity is confirmed, suspend the account and rotate affected keys/secrets.
Outcome: you reduce dwell time and limit blast radius—often moving from “days unnoticed” to a prompt, policy-driven containment. It’s not an automatic lockout by default; it’s measured, auditable actions that kick in quickly.
Delayed incident response is a clear recipe for legal and financial troubles. Without compliance visibility, even minor issues can spiral into full-blown crises with long-lasting consequences.
Get continuous compliance monitoring and visibility
3. Missed timelines across domains
Timelines in compliance aren’t just about meeting audit dates. They’re signals that inform you whether your controls are working, how quickly you can respond to risk, and whether you’re staying ahead of regulatory obligations.
With no real-time visibility into task status, deadlines quietly slip and remediation efforts pile up all at once. Let’s see how this could play out in reality. A company uses a basic spreadsheet to keep track of vendor reviews. One of their key vendors handling API keys and system-level access hasn’t been reassessed in over a year. The lapse is only caught on by a regional regulator after the incidence of an industry-wide breach.
Meanwhile, the compliance team was scrambling to fix SOC 2 controls, including missing attestations and outdated risk assessments. But none of it addressed the risk that had already gone undetected.
That’s the real cost of poor visibility– the damage happens even before you realize there’s a problem. So, if you’re only understanding the risk in hindsight, you’re only managing the impact in hindsight and not managing the risk.
With compliance visibility, vendor review timelines wouldn’t slip under the radar. Each vendor is tied to an owner and a defined review schedule, with automated reminders and escalation if deadlines are missed. Real-time dashboards highlight overdue reviews across domains, while alerts flag critical lapses early—so the team can reassess vendors on time and address risks before regulators or breaches expose them.
4. Failure to catch control drift overtime
Nobody likes it, but the fact remains that security controls slowly drift from their original, intended state. A few manual changes here, an undocumented update there, a missed patch or policy explanation — all this leaves gaps in your security posture. No one flags it in the moment because it doesn’t break anything right away.
Without real-time visibility, these changes stay under the radar until an incident or audit exposes them. And the longer the drift goes unchecked, the harder it is to fix.
With compliance visibility, those manual tweaks, undocumented updates, or missed patches wouldn’t stay hidden. Each change to a control is logged against its intended state, and deviations trigger alerts to the control owner. Instead of discovering drift months later in an audit, the team would have been prompted to patch, document, or roll back the change immediately before it could turn into costly security gaps or audit issues.
5. Misaligned control ownership
When no one owns a control, no one’s watching it. Critical areas like data encryption, third-party access, or incident response often lack clearly assigned owners. If no one’s clearly responsible, no one’s keeping it up or stepping in when things go wrong.
This lack of ownership shows up at the worst times, during audits, assessments or after an incident. Even the right controls won’t work if no one is accountable for them.
With compliance visibility, those critical areas like data encryption, third-party access, or incident response wouldn’t be left floating. Each control is mapped to a named owner, and if activity stalls or issues arise, the system flags it directly to them. In practice, that means when encryption policies need updating or a vendor’s access review comes due, responsibility doesn’t get lost—someone is accountable, and action happens before an auditor or incident forces the issue.
Avoiding the visibility pitfalls: What strong risk management actually looks like
The best kind of teams don’t rely on last-minute scrambles or scattered spreadsheets to stay in control. Navigating risk becomes a lot easier when you have visibility built into your controls, systems, and timelines.
Here’s what that kind of visibility looks like:
- End-to-end control lineage: Let’s start with solving the problem of control drift. You can map each control to frameworks, people responsible for it, and the risk it addresses. So if there are any breaks, gaps, or misconfigurations, it doesn’t stay hidden. You catch it early and fix it fast.
- Live ownership and accountability models: If your team is still grappling with the question, who’s going to sign off on this, you’re actively wasting time. Every control should have a name next to it, and every owned control should be kept active through system reminders.
- Exception-aware monitoring: Whether it’s an expired vendor review, an access that shouldn’t exist, or rushed hotfixes, all these exceptions should not be brushed aside. They must be flagged, tracked, and surfaced with context, so you know what’s worth fixing and when.
- Real-time posture insights awareness: Control monitoring and compliance visibility become easier when you have a centralized view of everything. Instead of having to switch between SOC 2, ISO 27001, and internal controls, you should have an overview of where controls stand for each framework and what needs your attention.
- Predictive exposure windows: Most importantly, a strong risk management program should ideally help you see where risk is building before it materializes. The goal is to forecast which controls, vendors, or systems are nearing non-compliance, so you can act before they trigger an incident.
Strategic shifts GRC leaders must drive
GRC and security leaders who want to move beyond reactive compliance need to drive deeper shifts in how their programs are designed, owned, and scaled. The strongest GRC leaders are making 5 key shifts in how they manage compliance:
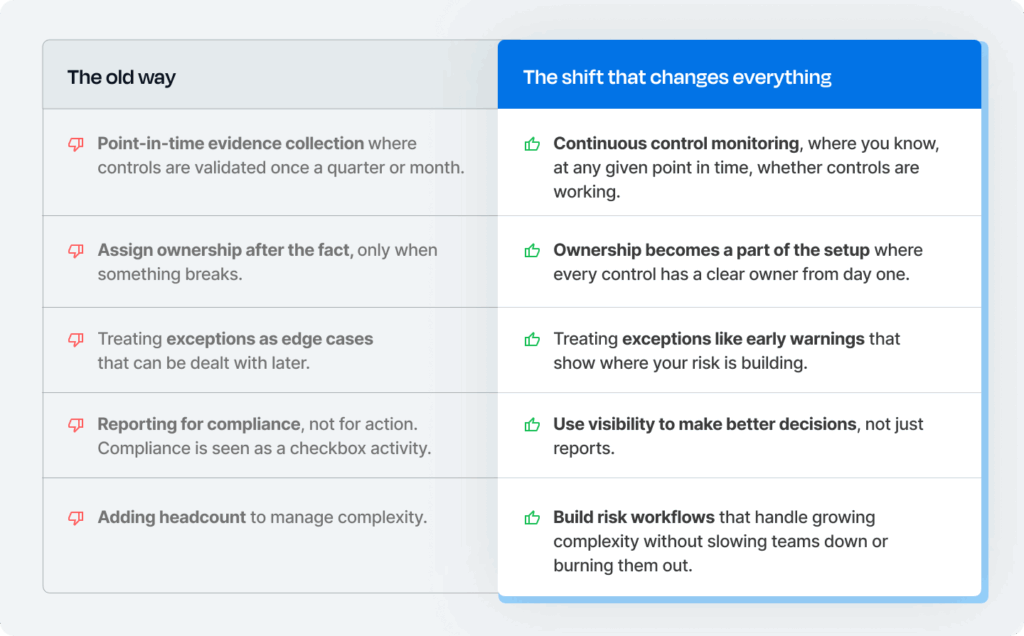
It’s these shifts that separate reactive teams from resilient ones. And visibility forms the foundation on which such teams can build their risk management efforts.
Move your risk management from reactive to resilient with Sprinto
Let’s be real. Staying compliant while keeping up with business growth goals shouldn’t feel like chasing loose ends. Sprinto helps you move from reactive checklists to proactive risk control without adding chaos to your workflows by giving you all the visibility you need. Sprinto delivers this visibility by:
- Bringing your controls, frameworks, vendors, and owners into one unified view, so nothing’s scattered or siloed.
- Tying system-level telemetry to your control health so you catch issues like missed reviews early.
- Showing you what’s off track or amiss with real-time triggers and continuous control monitoring.
- Putting names to controls so that you don’t have to chase updates or rebuild timelines every audit cycle.
- Automating reassessments and evidence collection so you never have to rebuild timelines from scratch again.
Let Sprinto handle the heavy lifting so you can focus on building a stronger, smarter compliance posture. Book a demo and see how Sprinto gives real, actionable compliance visibility.
Builder a stronger, smarter, risk-aligned compliance posture with Sprinto
FAQs
1. How do I move from control-level visibility to enterprise risk intelligence?
To move from control-level visibility to enterprise risk intelligence, you must zoom out from monitoring controls in isolation. Instead, you should adopt a strategic, organization-wide lens on risk. This means building a culture that prioritizes risk awareness.
2. What frameworks or standards support risk-centric compliance visibility?
Several frameworks like ISO 31000, NIST Cybersecurity Framework and COSO ERM are meant to support risk-centric compliance visibility. They help organizations align compliance efforts with overall business objectives, prioritize risk based on impact, and establish monitoring practices across functions and frameworks.
3. What architectural elements enable cross-framework visibility without control duplication?
Architectural elements like common control mapping, centralized control repositories, and meta-tagging of risks, assets, and frameworks enable cross-framework visibility without duplication.
4. How can I quantify the ROI of enhanced compliance visibility for my board?
Start by tying visibility to tangible outcomes like fewer audit surprises, faster risk response, and better use of your team’s time. With Sprinto, you can surface these gaps early, automate checks and workflows, and stay ahead of compliance gaps, all of which translates to measurable business impact.
5. How does visibility support risk-based decision-making in vendor selection, M&A, or market expansion?
When you have real-time insight into control effectiveness, policy exceptions, and third-party compliance gaps, you’re better equipped to spot hidden risks early. This allows teams to assess vendors, acquisitions, and new markets based on actual risk posture, not assumptions, speeding up decisions without compromising security.
Raynah
Raynah is a content strategist at Sprinto, where she crafts stories that simplify compliance for modern businesses. Over the past two years, she’s worked across formats and functions to make security and compliance feel a little less complicated and a little more business-aligned.
Explore more
research & insights curated to help you earn a seat at the table.


















