A single click can bypass every tool in your security stack. That’s the risk social engineering poses today. Modern attackers no longer need to exploit vulnerabilities in code. They exploit vulnerabilities in behaviour—fatigue, familiarity, urgency, and routine.
Despite continued investments in zero trust frameworks, SIEM (Security Information and Event Management) systems, and endpoint security, organizations are still being compromised through everyday interactions.
To help CISO leaders see the full picture, we’ve compiled 50 data-driven statistics exposing how social engineering attacks unfold, who they target, and the financial impact they incur.
TL;DR
| Social engineering is the manipulation of people into revealing confidential information or taking actions that compromise security, often by exploiting trust, urgency, or routine instead of software vulnerabilities. |
| In 2025, it’s the top initial access vector (36% of incidents), with phishing making up 65% of cases; 66% target privileged accounts, 60% cause data leaks, and nearly half the world faces scams weekly. |
| AI, deepfakes, and automation are making attacks more convincing; 82% of phishing emails now use AI content, deepfake tool trading is up 223%, and new methods like FileFix exploit everyday user behavior. |
What is social engineering?
Social engineering is the manipulation of people into revealing confidential information or performing actions that compromise security, often by exploiting trust rather than hacking technology.
Instead of exploiting software vulnerabilities, attackers use deception to exploit human trust.
For instance, a scammer might pose as an IT support agent and request wire transfers or login credentials via email or phone call.
These tactics often bypass technical controls and pose a significant risk to organizations, as the stats below highlight.
Types of social engineering attacks
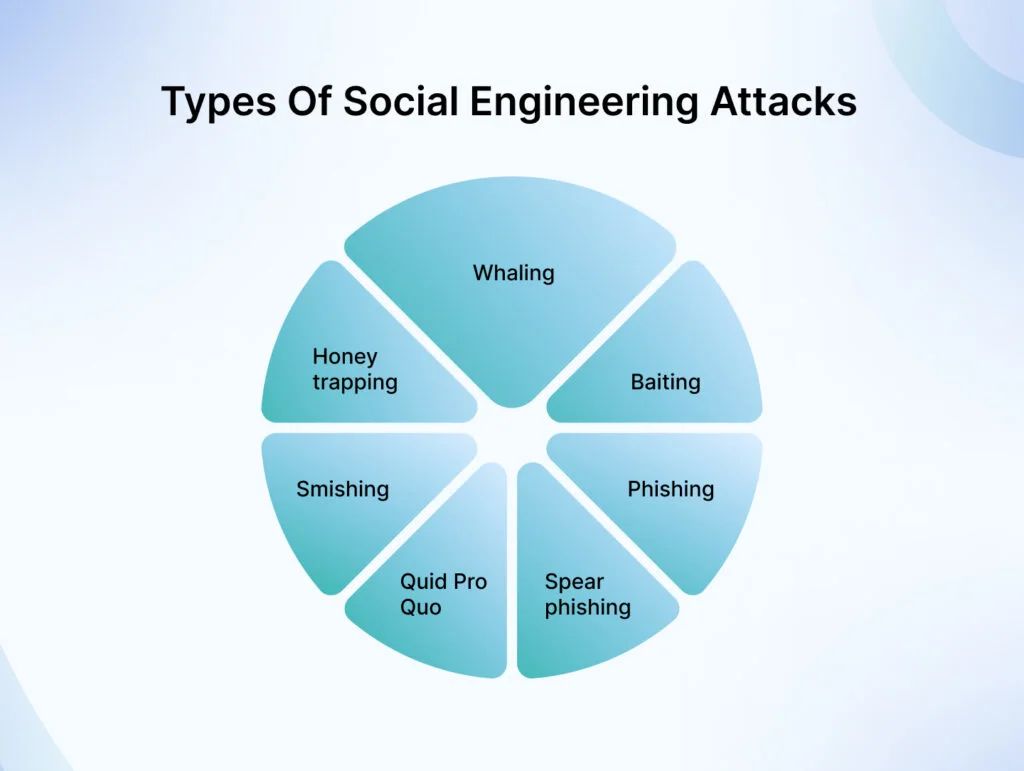
There are different types of social engineering attacks, and each differs in the medium, nature, and ultimate target.
Phishing
Phishing is a sophisticated attack that aims to deceive individuals into revealing sensitive information or doing something harmful. Cybercriminals draft convincing emails or texts, pretending to be banks, governments, or other well-trusted sources.
Phishing poses a significant threat to businesses as it targets the weakest links in an organization, the human element. A successful phishing attack can destroy the entire network, leading to data breaches, financial losses, or reputational damages.
Spear phishing
Spear phishing attacks is a type of a social engineering attack wherein cybercriminals specifically target organizations to get access to confidential and sensitive information.
The difference between phishing and spear phishing is the target. Phishing, in general, is a “bulk” activity—think of it like shooting aimlessly—but spearfishing targets a specific individual or a group of individuals in an organization to divulge sensitive data that the bad actor wants.
Smishing
Smishing, or SMS phishing, uses text messages to trick people into downloading malware or sharing sensitive information. It is a quite popular form of social engineering, as mobile phone open rates range between 8% and 14%, compared to email open rates that hardly go above 2%.
The critical difference between phishing and smishing lies in the medium of the attack.
Quid Pro Quo
“Quid pro quo” means “something for something” in Latin. It is a social engineering attack type wherein a threat actor offers a service in exchange for information or access. It is reciprocity at its finest. The social engineer impersonates an IT technician, offering assistance. They get in touch with potential victims by providing help or service. In exchange for addressing the issue, they ask for sensitive information and login credentials or request the employee to temporarily disable security features like 2FA.
Honey trapping
Honey trapping is a type of social engineering wherein the bad actor creates a fake profile that appeals to the target. Threat actors often use flattery to build a connection with the victim. The attacker cultivates a relationship, usually an emotionally manipulative one. Once the relationship is built, the target exploits the connection to extract sensitive information.
Whaling
Whaling is a phishing attack that targets high-profile company employees, commonly referred to as “whales” in cybercrimes. These attacks are personalized, as threat actors invest a fair amount of time researching the target.
While it seems like an easily avoidable attack, whaling isn’t as apparent as it seems.
Baiting
Baiting is a social engineering attack type that uses temptation to lure victims and manipulates them into divulging secret or sensitive information. These messages often use false promises or curiosity hooks to grab readers’ attention.
Baiting’s delivery mechanisms include emails, social media, text messages, or USB drives. The threat actors leave infected USB drives in locations, potentially tempting curious individuals to plug them into their devices.
While these tactics seem like elaborate schemes of the past, their prevalence in today’s world is all too real. The statistics paint a concerning picture of how social engineering attacks have risen and the impact they have created.
Key social engineering statistics for 2025
From phishing to impersonation, the statistics below reveal just how deeply social engineering techniques have embedded themselves into the threat landscape.
- Social engineering is the most common initial access vector, with phishing attacks accounting for 65% of these cases.
- 36% of all incidents in the incident response (IR) caseloads began with a social engineering tactic.
- In early 2025, social engineering caused 39% of initial access incidents, driven by a 1450% spike in fake CAPTCHA attacks like ClickFix campaigns.
- External attackers pose the biggest threat, causing 81% of breaches.
- Among these external attacks, 22% were social engineering-driven cases, highlighting how tricking people is still a popular tactic.
- Phishing caused 25% of social engineering incidents in 2024. Thankfully, it’s down from 29% in 2023 and 46% in 2022.
- PDFs were the most common bad attachment at 45.2%, followed by HTML at 17.4% and ZIP at 10.4%
- In malicious PDFs, 42% hid links with obfuscation, 28% hid links in streams, and 7% used passwords.
- Stolen credentials became the second most common entry path in 2024, used in 16% of intrusions, overtaking email phishing at 14%.
- In cloud intrusions, initial access most often came from email phishing (39%), then stolen credentials (35%), SIM swapping (6%), and voice phishing or vishing (6%).
- “Adversary-in-the-middle” kits and MFA-bypass tools were widely sold to weaken two-factor protections.
- 66% of phishing attacks in social engineering cases target privileged accounts, while 45% of them involve the impersonation of internal personnel.
- Ransomware made up 28% of malware cases and 11% of all security cases.
- Dark-web ransomware chatter rose 25% year over year in 2024.
- The most common end result was credential theft at 29%, then data theft at 18% and extortion at 13%.
- Manufacturing was the most attacked sector again, accounting for 26% of incidents in 2024.
- Attackers now move laterally within 60 minutes, sometimes in under 15, making response time more critical than ever.
- Over 90% of social engineering-based attacks pretend to start with friendly collaboration or engagement.
- Social engineering attacks led to data leaks in 60% of cases, 16% more than other attack methods. About half of these cases were business email compromise (BEC), and nearly 60% of those also exposed sensitive data.
- In 2023, overall, 97% of organizations were successfully able to retrieve encrypted data post a ransomware attack, using different methods. While 46% of them paid ransom to recover the data, the remaining 70% and 2% of organizations relied on backups and used other methods, respectively.
- Microsoft Teams is reportedly a common social engineering vector among the key movers and shakers for initial access vectors (IAVs).
- Criminals increasingly used cloud services to host mass phishing, with Latin America hit especially hard in 2024.
- Attackers used AI to write emails, build fake sites, and create deepfakes that boost persuasion.
27. AI is making phishing attacks more convincing and harder to detect, even for seasoned security professionals, with a 17.3% increase in phishing emails.
How common are social engineering attacks?
Social engineering has become a routine experience for people and organizations around the world. Here’s a collection of stats that reflect just how frequently these attacks occur and who they’re targeting.
- Almost half of the world encounters a scam at least once a week.
- In 2025, advanced fee fraud increased by nearly 50%.
- In the time it takes to read a sentence, Microsoft defends against about 27,860 password attacks.
- 20% of companies experience at least one account takeover (ATO) incident every month.
- Social engineering is used in 25% of all advanced cyberattack campaigns.
- The top three most vulnerable industries are: Healthcare & Pharmaceuticals (41.9%), Insurance (39.2%), and Retail & Wholesale (36.5%).
- Between 2023 and 2024, 389 healthcare institutions were hit by ransomware, delaying operations and forcing appointment rescheduling
- On average, about one-third of employees are vulnerable to phishing and social engineering attacks across industries, with an industry-wide baseline Phish-prone Percentage1 (PPP) of 33.1%.
- From January to June 2024, over 1.5 million credentials were discoverable in code and other locations; 18% of repositories exposed secrets.
- Microsoft mitigated 1.25 million DDoS attacks in the second half of the year, a fourfold increase over last year.
- Smaller businesses remain the most common targets for ransomware, with over half (55.8%) of attacks aimed at companies with 1-50 employees.
- Espionage-motivated attacks now make up 52% of social engineering breaches.
- Financial motives appear in 55% of social engineering breaches.
- The two most common break-in methods are exploiting internet-facing apps (30%) and using stolen or misused logins (30%).
| 1 Phish-prone Percentage (PPP) is the percentage of employees likely to click on a fake phishing email. It helps measure how at risk a company is to phishing and how well its security training is working. A higher PPP means employees are more likely to fall for phishing scams, which can put the company’s security in danger. |
Human element in cybersecurity breaches
It’s important to note that the human element remains a major factor responsible for cybersecurity breaches. From overlooked alerts to simple misclicks, these studies shed light on human involvement in security incidents.
- 68% of data breaches were due to accidental actions, the use of stolen credentials, social engineering, and malicious privilege misuse.
- Human involvement in breaches is at 60% in 2025, as compared to 61% in 2024
- Credential abuse causes 32% of breaches linked to human actions, followed by social tactics like phishing at 23%, user errors at 14%, and malware-related actions, often triggered by clicks or downloads, at 7%.
- End-users were involved in 9% of all actor categories, and among them, 72% of actions were misdeliveries.
- User mistakes make up 14% of breaches, usually caused by sending data to the wrong person, misconfiguring systems, or mishandling sensitive info. (2025 Data Breach Investigation Report)
- In phishing simulations, a stubborn median of 1.5% of employees still click dangerous links even after repeated awareness training.
- This is expected as over half of consumer-targeted phishing impersonates software and service brands to raise the likelihood of successful deception.
Malware-related breaches tied to human actions account for 7%, usually when someone clicks a bad email attachment or downloads a file from an unsafe site. (2025 Data Breach Investigation Report)
Cost and impact of social engineering attacks
Social engineering doesn’t just target systems. It preys on trust, curiosity, and even disrupts everyday communication.
The financial toll is massive, with scams ranging from billion-dollar frauds to nation-state-level losses, and research shows these attacks deliver a direct blow to the bottom line.
- The average global data breach cost reached $4.88 million in 2024, raising the price of credential-driven compromises.
- This figure dipped slightly this year — in 2025, the average data breach costs organizations $4.4 million. (a 9% decrease from last year).
- Global cybercrime damage costs are projected to reach $10.5 trillion USD annually this year.
- More than $1 trillion globally has been lost to online scammers in 2024.
- U.S. consumers reported $12.5 billion in fraud-related losses in 2024 alone. Government impostor scams alone cost consumers $789 million in that period.
- Investment scams were the costliest online fraud; this category topped $4.5 billion in losses in 2023.
- Over 90% of malicious traffic in the Edge browser is tied to technical scam activity (2022–2024).
- Call center scams targeting seniors and crypto traders raked in a sickening $1.9 billion in reported losses in 2024.
- Socially engineered investment scams caused more than $4.5 billion in losses during 2023-24.
- Credential theft, often enabled by phishing and infostealers, appeared in 29% of investigated incidents in 2024.
- Malicious ZIP attachments in phishing fell 70% year over year in 2024, and RAR files fell 45%, as attackers favored links and PDFs.
- Extortion after data theft appeared in 13% of cases, using stolen data to pressure victims.
- The average cost of a ransom was found to be almost $115,000 in 2024.
- On the bright side, 64% of organizations refused to pay ransomware demands, up from 50% two years prior.
- Scammers have siphoned away more than $1 trillion globally in the past year, costing certain countries losses of more than 3% of their gross domestic product (GDP).
- Only 4% of scam victims worldwide were able to get their money back. While recovery rates are highest in the U.S. and U.K., they are still low overall, leaving most victims without a way to recover their losses.
- For 2024 ransomware victims, 54% had their domains appear in credential dumps, and 40% had corporate emails exposed.
- Among systems with corporate logins in stolen data, 46% were non-managed devices hosting both personal and business credentials.
- Among the affected small businesses, about 1 in 5 small businesses chose to pay the ransom—60% of them paid between $10,000 and $100,000 to recover their data.
- In manufacturing, extortion hit 29% of victims and data theft 24%, risking finances and intellectual property.
- Business Email Compromise cost organizations over $6.3 billion in 2024, based on victim-reported transfers to the FBI IC3.
- The median BEC loss is around $50,000 across roughly 19,000 complaints.
- Targeted BEC increasingly uses local languages and role-specific lures, improving compromise rates in IT, finance, and legal teams.
Social engineering trends for 2025
Social engineering continues to be a top concern for security leaders.
But in 2025, the tactics are becoming more advanced, more personalized, and harder to detect.
The rise of AI-generated content, deepfakes, and automation is reshaping how attackers engage with targets, making traditional detection methods less effective.
Evolving threats demand smarter responses. The trends below highlight a critical shift: threat actors are adapting quickly. Organizations must be equally proactive in how they prepare, respond, and defend.
- The global average cost of a data breach is $4.4 million in 2025, a 9% drop from 2024, driven by faster detection and response.
While this is a positive sign, it also highlights how critical early action and strong incident response have become in reducing overall impact. - The share of AI-assisted malicious emails roughly doubled over two years, from about 5% to about 10%.
- 15% of employees routinely accessed AI services on corporate devices, at least once every 15 days.
- Of those accessing AI, 72% used non-corporate emails, and 17% used corporate emails without integrated authentication.
- On the other hand, AI is making phishing attacks more convincing and harder to detect, even for seasoned security professionals. In fact, 82.6% of phishing emails now leverage AI-generated content.
- Leveraging this vantage point, threat actors are also diligently adding AI to their toolboxes.
- Cybercriminals are openly harnessing the efficiency of AI to automate and personalize deceptive communications.
- Moreover, the percentage of AI-assisted malicious emails has doubled from around 5% to roughly 10% over the past two years.
- Cloud-hosted phishing also grew, borrowing trusted domains and IPs that are harder for companies to block.
- Attackers also increasingly weaponize legitimate SaaS services, like email, storage, and marketing tools, to host phishing and evade blocking
- QR code phishing spiked in late 2023, then attackers altered QR visuals after a 94% detection-driven drop.
- Collaboration apps like Teams and Skype are being abused more and more for AiTM links, MFA prompts, and file-based phishing.
- SIM swapping and helpdesk impersonation are rising to sidestep MFA by resetting passwords or registering new devices.
- BEACON was the most frequently seen malware family, appearing in 5.4% of intrusions in 2024.
- Backdoors were the most common observed malware family category (35%); ransomware families represented 14% of observed families.
As synthetic content becomes more realistic and accessible, it’s quickly rising on the list of cyber risks that leaders can’t afford to ignore. - Over half (55%) of CISOs surveyed at the 2024 Annual Meeting on Cybersecurity said deepfakes pose a moderate to significant threat to their organizations.
Additionally, the extensive use of AI raises concerns, especially as threat actors are now harnessing deepfake tools and betting their money on highly efficient deepfake tools. - With a staggering 223% increase in deepfake tool trading on dark web forums between Q1’23-Q1’24, threat attackers are now paying up to $20,000 per minute for high-quality deepfake videos.
While 66% of cybersecurity leaders believe AI will impact their organization within the next 12 months, yet only 37% have processes in place to deploy AI safely. This gap reveals a growing concern: while many recognize AI’s influence, few are fully prepared to manage its risks.
Employee awareness and prevention measures
Social engineering thrives on unpreparedness, but there’s good news: awareness training works.
With the right education, employees become empowered to pause, question, and report.
These stats highlight just how powerful well-informed teams can be, and why building a culture of security awareness is no longer optional. It is the need of the hour!
- Without security awareness training, 34.3% of employees are likely to click on malicious links or comply with fraudulent requests.
- Organizations that implement security awareness training (SAT) see a dramatic reduction in phishing risk—over 40% in just 90 days, and up to 86% within a year.
- 67% of people globally feel confident in their ability to detect scams, reflecting the success of some awareness campaigns.
- China (84%), followed by Australia (72%), reported high confidence in spotting scams, while Japan shows lower awareness, pointing to a need for better education in some areas.
- Ransomware is usually discovered within one week in 56.5% of cases, which highlights the importance of rapid internal reporting and practiced response drills.
- Attackers themselves triggered 49% of ransomware notifications, so teams should rehearse communication and recovery before extortion demands arrive.
- Because phishing and credential theft drove 16% of intrusions and 35% of cloud initial access, FIDO2-compliant MFA and credential hygiene are critical.
“While the success of any security and compliance program can be attributed to various teams, failures will always fall on business owners. Therefore, the involvement of senior management and business owners is crucial in security and compliance programs.”
Gurudev Mallesha, ISO Lead Auditor at Sprinto
Notable social engineering incidents in 2024–2025
Social engineering has shifted from opportunistic phishing to strategic infiltration. Attackers are no longer just deceiving individuals. They’re embedding themselves into systems, roles, and routines with alarming ease. These recent cases show how human trust and everyday tools continue to be repurposed for high-impact breaches:
- In a rapid attack investigated by NCC Group, threat actors posing as IT support used Windows QuickAssist to gain remote access and compromise systems in under five minutes. They deployed NetSupport Manager malware via PowerShell, extracted it from a JPEG using steganography, and harvested credentials through a fake login screen. The attackers relied on trusted tools, making the breach hard to detect.
- A 30-year-old CoinDCX engineer was arrested for allegedly enabling a $44 million crypto theft via a social engineering attack using his work laptop. The breach exposed internal weaknesses, highlighting the need for tighter employee vetting and stronger cybersecurity protocols in the crypto industry.
- In July 2025, threat actors began actively testing a new social engineering method called FileFix, which tricks users into pasting disguised PowerShell commands into Windows File Explorer. Unlike earlier ClickFix attacks, FileFix is subtler, leveraging trusted user behavior without exploiting software vulnerabilities. First spotted by Check Point Research, this evolving tactic shows how quickly attackers adapt and underscores the urgent need for better user awareness and endpoint protection.
- In April 2024, Midnight Blizzard posed as “Microsoft Security” inside Teams and sent targets to adversary-in-the-middle (AiTM) credential-harvesting pages. Campaigns commonly used one-to-one chats from newly created attacker-owned tenants and, in some waves, paired links or QR codes with urgency tactics. In some cases, attackers had already password-sprayed accounts and pushed MFA prompts through Teams.
- Octo Tempest (also known as Scattered Spider) evolved from SIM-swapping and social engineering to full ransomware operations. After affiliating with ALPHV/BlackCat by mid-2023, the group deployed BlackCat payloads, and by the second quarter of 2024 it had added Qilin and RansomHub.
- In 2024, attackers increasingly impersonated Help Desk or IT support staff in Teams, persuading users to initiate remote monitoring and management (RMM) sessions with attacker systems. These live-support ruses shifted the story from simple credential theft to hands-on keyboard access, and several incidents culminated in ransomware deployment.
- In spring 2024, UNC5537 used stolen Snowflake client credentials to reach multiple organizations’ data warehouses. After quietly exfiltrating large datasets, the actor sought monetization through extortion emails and attempted listings on criminal forums.
- Throughout 2024, UNC3944 repeatedly phoned enterprise service desks to reset passwords and multifactor protections, then abused single sign-on to fan out across connected apps. The group escalated from credential abuse to hands-on extortion, using RANSOMHUB in at least one incident to threaten data exposure and disruption.
“Most of the time, security is about discipline and processes around crucial activities that you do continuously. These include common things such as how you onboard or offboard employees or how you just push code to production.”
Girish Redekar, Co-Founder at Sprinto
Great advice adds up. Get more from the brightest minds in GRC — Subscribe to our newsletter
What makes social engineering so effective?
“All that the intellect does is to enable me to perceive, without affirming or denying anything, the ideas which are subjects for possible judgments.” – René Descartes.
To Descartes, the mind’s role is to hold ideas in suspension, to scrutinize them before accepting or rejecting them. In other words, sound judgment depends on pause and reflection.
Social engineering works precisely because it disrupts that pause. Instead of giving us time to think, it targets basic instincts. We trust familiar voices, help people in distress, and follow those who appear to be in charge.
Attackers use simple cues like politeness, urgency, and confidence to trigger automatic responses. They don’t need to hack systems. All they do is simply follow the same social rules we respond to every day. When someone sounds rushed or worried, we feel the pressure to act, not question.
This is what makes social engineering so effective: it turns our strengths (empathy, cooperation, trust) into vulnerabilities, simply by removing space for judgment.
FAQs
Social engineering is extremely common. 98% of cyberattacks involve social engineering tactics, making it the primary attack vector, accounting for 36% of all security incidents in 2025.
Latest tactics include ClickFix campaigns (fake CAPTCHA prompts), AI-powered deepfake impersonation, callback phishing schemes, help desk manipulation, SEO poisoning, and voice cloning for executive impersonation.
Phishing uses fraudulent emails and fake websites to steal information. Vishing (voice phishing), on the other hand, uses phone calls or voicemails to manipulate victims into revealing sensitive data.
Studies imply that human error contributes to 60% of all data breaches.
Companies can reduce risk through regular employee training, implementing multi-factor authentication, establishing clear verification protocols, creating a security-aware culture, conducting phishing simulations, and using behavioral analytics for threat detection.
The four most common types of social engineering attacks are:
1. Phishing: Phishing attempts are social engineering attacks that use fraudulent emails, websites, or messages to trick people into divulging sensitive information by clicking on malicious links.
2. Pretexting: Pretexting is when bad actors create a fabricated scenario to manipulate victims into revealing sensitive information or performing actions they usually wouldn’t do.
3. Scareware is deceptive software designed to trick users into believing their device is infected with malware or facing a serious security breach or threat. It typically sends out fake alerts or warnings to scare users into purchasing unnecessary software or services.
4. Ransomware: Ransomware is malicious software that encrypts the target’s files and locks them out of their devices, demanding a ransom for the decryption key that enables them to regain access. It is a direct attack that can spread through various vectors.
Social engineering data is the information that is gathered and used by threat actors to craft convincing social engineering attacks. This data includes:
1. Personal information
2. Professional details
3. Social media activity
4. Public Records
5. Recent events or news related to the target.
This data is collected from sources like open-source intelligence, data breaches, and social media research.
The 4 phases of a social engineering attack namely are:
1. Gathering information: Attackers collect data about their victims through various sources. The phase aims to build a comprehensive profile.
2. Developing a relationship: The attackers connect with the target, building rapport and gaining the user’s trust.
3. Exploiting: Once the attacker has established trust, the bad actor manipulates the target. It could involve requesting sensitive information, persuading the target to click on malicious links, or gaining access to the control network.
4. Execution: Once the attacker can achieve its goal, it starts covering tracks to avoid detection.
Heer Chheda
Heer is a content marketer at Sprinto. With a degree in Media, she has a knack for crafting words that drive results. When she’s not breaking down complex cyber topics, you can find her swimming or relaxing by cooking a meal. A fan of geopolitics, she’s always ready for a debate.
Explore more
research & insights curated to help you earn a seat at the table.