June 2017. One of the world’s largest container shipping companies, Maersk, was hit by malware that made 1200 applications inaccessible, destroyed 49000 laptops, and impacted 3500 servers. The shipping line was at a standstill. This incident highlighted the critical importance of risk mitigation strategies in minimizing damage and restoring operations swiftly.
This was short-lived, however. They started taking bookings online within a week. And within two, every global application was restored. This was considered an excellent response because Maersk worked tirelessly to implement their risk mitigation strategies without delay.
The business landscape today is increasingly complex and there’s huge exposure to a number of risks like malware attacks, natural disasters, security breaches, etc. Having a strong risk mitigation strategy in place can go a long way in preparing your organization against such incidents.
In this blog, we cover various kinds of risks that can occur and how your risk mitigation strategies can help you overcome them.
What is Risk Mitigation?
Risk mitigation is the process of reducing the impact of potential threats to a business by identifying, assessing, and addressing risks before they escalate. It involves developing strategies to manage, minimize, or eliminate vulnerabilities, ensuring business continuity and protecting critical assets.
Effective risk mitigation helps organizations safeguard operations, limit disruptions, and maintain resilience against unforeseen events.
What are Risk Mitigation Strategies?
Risk mitigation strategies are action plans to avoid, transfer, reduce exposure, or develop a recovery plan to control the impact of risks. The goal is to ensure business continuity and reduce the threat surface of the business.
Different risks call for different response mechanisms, and the speed at which organizations respond can greatly improve decision-making and risk mitigation.
Risk mitigation strategies can vary depending on the complexity of risks and the nature of the organization.
What is a risk mitigation plan?
A risk mitigation plan is a tactical process to identify, foresee, gauge impact, and define mitigation workflows to address and contain risks as they arise. It develops action items to minimize the impact of risks so that business processes remain unaffected and sensitive assets are protected.
What is the difference between a risk mitigation strategy and a risk mitigation plan?
The difference between a strategy and a plan lies in their focus:
- Strategy (Long-term) – A high-level framework focused on reducing overall exposure to risk across the organization. This might involve decisions like diversifying suppliers, investing in cybersecurity infrastructure, or training employees on risk awareness.
- Plan (Short-term) – A detailed playbook that activates during a risk event or as part of ongoing risk management. It includes specific procedures for identifying vulnerabilities, responding to incidents, and implementing recovery measures.
A risk mitigation plan includes:
- Risk identification – A detailed list of potential risks that could impact the organization, categorized by likelihood and severity.
- Risk assessment – Evaluation of each risk to determine its potential impact on business operations.
- Response strategies – Actionable steps to avoid, transfer, mitigate, or accept risks based on the organization’s risk tolerance.
- Roles and responsibilities – Clear assignment of personnel responsible for monitoring and executing the mitigation plan at different stages.
- Contingency and recovery plans– Backup measures to restore operations if risks materialize, minimizing downtime and loss.
- Monitoring and review – Ongoing review of the mitigation plan to ensure it remains relevant as new risks emerge or existing risks evolve.
A solid risk mitigation plan reduces exposure and enhances confidence in the organization’s ability to manage crises effectively.
Types of Risks That You May Face in 2025
There have been fluctuations in the global economy. Data security is becoming a significant threat to organizations. Climate changes are impacting the world. In 2024, both individuals and organizations are exposed to a number of such risks.
7 Types of common risk that might face:

1. Market risks
Any volatility in market conditions such as changes in interest rates, market demand, technological breakthroughs, etc. can bring market risks. So if an increase in the market rate of interest impacts your borrowing costs or the entry of a new competitor affects your sales, it is a market risk.
2. Regulatory and compliance risks
Regulatory and compliance risks refer to any issues that the organization faces due to violations of regulatory laws or compliance failures. These can be legal proceedings, financial damages, cancellation of certification, business disruptions, negative publicity, etc.
3. Financial risks
The risks of financial losses because of the impact on your investments, income, expenditure, or credit are known as financial risks. There can be various reasons for such risks. A failure on the part of a borrower to repay debt can for example, bring credit risk, while improper management can bring liquidity issues.
4. Operational risks
Operational risks are associated with hindrances in day-to-day activities of the organization. A human error leading to a data breach can pose a business continuity risk. Similarly, system or process failures, regulatory infringements, some external events etc. can bring operational risks for an organization.
5. Cybersecurity risks
Risks that affect the confidentiality, integrity and availability of information assets of the organization are cybersecurity risks. Social engineering, malware, password attacks etc are some examples. Cybersecurity risks can result in financial losses, regulatory issues, theft of information security etc.
6. Reputational risks
Risks that can tarnish your brand image and pose a threat to its reputation are categorized as reputational risks. An ethical or compliance lapse may put you in negative stories or an employee behaviour such as harassment can put a dent in your public perception.
7. Environmental risks
Any unanticipated environmental changes like pollution, calamities, land use patterns, etc. that can impact the environment and in turn bring operational hiccups for your organization are environmental risks. Any resource depletion for example, can affect the dependent supply chain.
Easy Automated Risk Insights
Top 9 Risk Mitigation Strategies For 2025
Risk mitigation has a definitive objective—to protect the company and its stakeholders from the various types of risk while preventing financial losses, ensuring minimal operational disruption, and protecting the organization’s reputation. The strategies adopted hinge on the nature and severity of risk and the complexity of the organization.
List of top 4 Risk mitigation strategies:
- Risk avoidance
- Risk transfer
- Risk reduction
- Risk acceptance
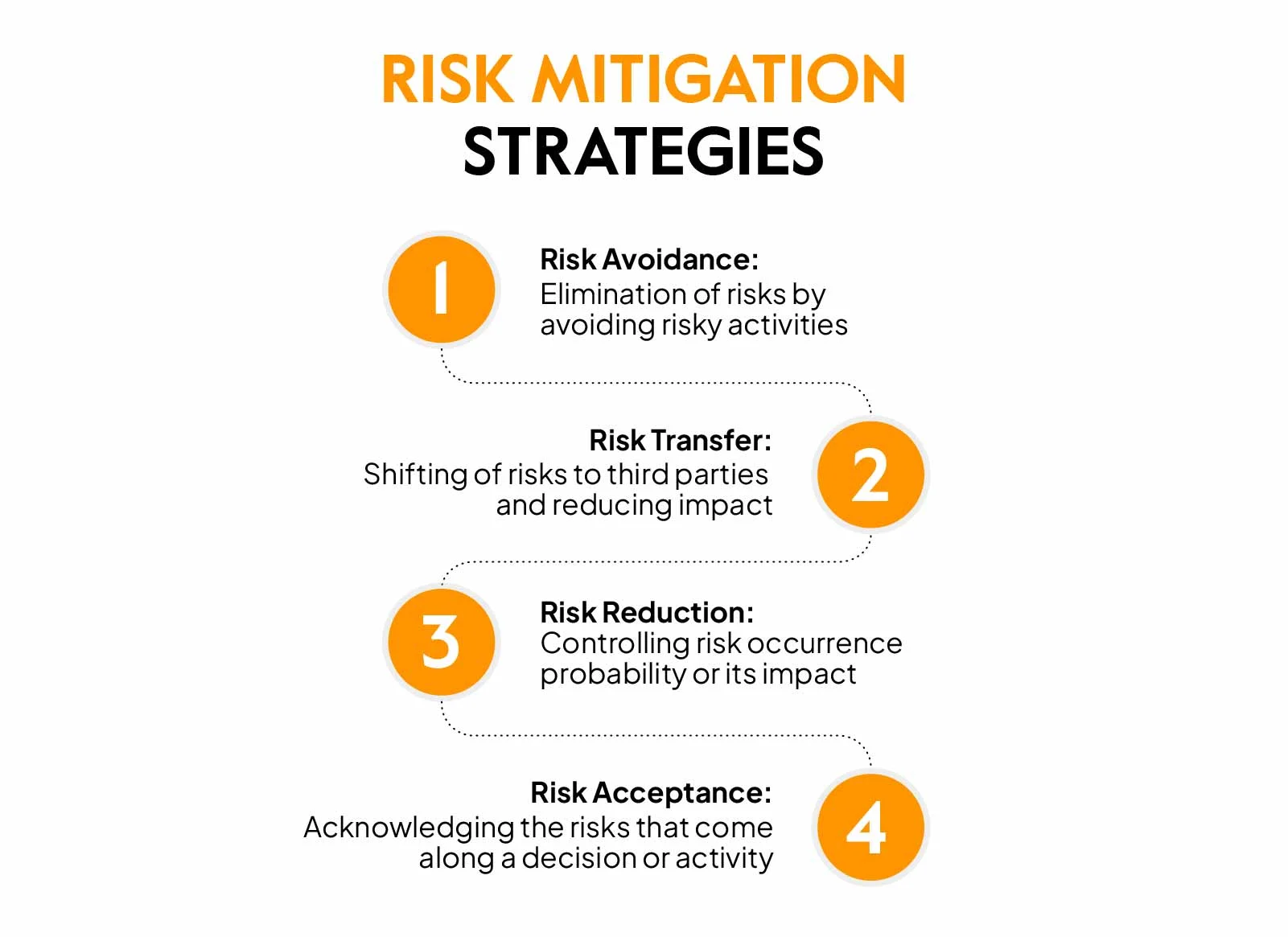
1. Risk avoidance
Risk avoidance strategy calls for the elimination of activities or withdrawal from situations that pose a risk to the organization. Any business project that has a high probability of bringing along negative consequences such as legal, financial, or operational trouble must be avoided.
However, this strategy only applies if the severity of the potential risk is too high. Ceasing an activity is an easy solution but the business may miss out on big business opportunities.
2. Risk transfer
Risk transfer is the strategy of passing on the risk to a third party through contracts, insurance, or any other transfer arrangement.
Signing a contract with the third-party or purchasing an insurance policy can help shift the financial burden of a potential risk. But it can be expensive and the risk coverage may not include complete coverage.
3. Risk reduction
Risk reduction is the strategy of controlling or lessening the probability of risk occurrence or its impact. This involves implementing various mitigation controls to minimize the likelihood of risk or to protect the organization from its impacts.
The strategy helps in safeguarding the organization from financial, market, and reputational risks etc. and building organizational strength against such risks. It can however be heavy on the company’s pocket and difficult to monitor. If the risk still occurs, it can be hard to analyze how effective the measures were and how much risk was reduced.
4. Risk acceptance
Risk acceptance is when the organization chooses to bear the impact of a potential risk that comes from a decision, activity, or project. It is a deliberate act where the key stakeholders decide to proceed with a risky endeavour, resisting the urge to avoid mitigation.
Often, the decision for risk acceptance is taken when the cost of reduction, avoidance, or transfer is too high or when the outcomes the risk brings can bring about positive change.
Also check out these top risk assessment tools
Comprehensive Risk Monitoring & Mitigation
Other risk mitigation strategies
5. Risk buffering
Risk buffering involves creating a safety net to absorb and reduce the impact of risk. This requires the organization to add additional resources, time or personnel to reduce the likelihood of significant disruptions. For example, employing additional staff to manage work loads and minimize employee burnout.
6. Risk diversification
Risk diversification involves spreading risk across various investments, projects, or products to ensure that no one area is significantly impacted by a failure. The strategy is mostly used to manage financial and operational risks. Portfolio diversification is an example.
7. Shared risk management
Shared risk management involves distributing risks among multiple parties such as vendors and partners so that no single party bears the risk. It also enhances the risk management process as different parties bring their expertise and resources to manage their share of risks. For example, entering into a contract with a vendor for a critical function and including clauses for compliance audits and liability for non-compliance.
8. Contingency planning
Contigency planning is a risk mitigation strategy that involves creating an alternative or contingency plan for unforeseen events that could impact an organization. For example, creating a disaster recovery plan for a system failure.
9. Risk automation
Risk automation is the process of automating the process of risk identification, scoring and initiating remediation workflows to mitigate the risks. This requires organizations to use tools and technologies that leverage machine learning and artificial intelligence (AI) to rapidly address issues and minimize potential impact. For example, leveraging integrated risk management with compliance automation tools like Sprinto.
Risk Mitigation Strategy Examples
Examples are a great way to understand what each strategy brings along. Here, look at some risk mitigation strategy cases:
Example 1: How to avoid risk?
A highly volatile investment that carries along the risk of huge losses may be avoided and the organization may choose to invest in a low-risk investment like bonds or real estate.
Entering a new market may bring a lot of regulatory and legal risks. So, the company may cancel the business move to avoid the consequences.
Similarly, blocking risky websites for avoiding cybersecurity risks is another example.
Most of the times, security is about discipline and processes around crucial activities that you do continuously. These include common things such as how you onboard or offboard employees or how you just push code to production.
Girish Redekar, Co-Founder at Sprinto
Great advice adds up. Get more from the brightest minds in GRC — Subscribe to our newsletter
Example 2: Transfer risk when you can
Getting insurance for machinery is an example of risk transfer. In this case, any damages or loss to machinery will be covered by the insurance company in exchange for the premium paid.
Outsourcing is a great way of transferring risks to third parties. By outsourcing a service, say IT functions or security, the risks associated with cyber attacks or infrastructure failure are assumed by the vendor.
Example 3: Control or reduce risks
Employing safety protocols and controls for employees to reduce chances of injury and training employees to avoid human errors is a risk reduction strategy.
Similarly, if an organization includes an indemnification clause in an agreement with a third-party contractor, then, in case of non-performance of obligations by the contractor, the organization will be compensated for the loss. This is risk reduction.
Example 4: When to accept risks?
When a business chooses to diversify its operations and enter a new product line, there’s an acknowledgment of the risk of slow sales initially. This is risk acceptance.
Likewise, switching technology for production will pose a risk of resistance from the workforce and underutilization of capacity in the training period. When a business makes such a strategic move, these kinds of risks are accepted.
Ensure integrated risk management with Sprinto
Risks are inevitable but not having risk mitigation strategies in place can slow down the speed of responses to risks. Risks are also interrelated. One cyber security breach can bring along financial, reputational, operational, legal and other compliance risks. Having a detailed risk management strategy helps you identify the potential threats, assess the degree of impact, and lay down a strong action plan for the same. And tools like Sprinto make this easy.
As a next-gen GRC tool Sprinto has integrated risk management capabilities that enable you to manage risks unique to your business. The platform features a comprehensive risk library to scope out risks and enables you to score them for likelihood while visualizing their true impact. It automatically suggests whether you should accept, reject or transfer risks and mitigating actions that would remediate it.
The risks are also mapped to compliance criteria and continuously monitored to send notification alerts in case of any deviations. And all of this is managed without spreadsheets, from one centralized place.Want to ace security and compliance? Speak to our experts today.
FAQs
What is risk mitigation under compliance?
Risk mitigation under compliance involves implementing processes to identify and manage compliance-related risks. Compliance risks here refer to fines, penalties, lawsuits, reputational damages, productivity losses, or any other disruptions on regulatory adherence failure.
What steps can you take to mitigate risks?
Risk mitigation begins with identifying the potential risks associated with a decision, activity or project. Next, the likelihood, severity and impact of each risk are assessed. A risk management plan is then developed for guiding mitigation implementation. Once the risk mitigation strategies are executed, there’s monitoring and improvement.
Why is risk mitigation important?
Risk mitigation is important to protect the organization from financial losses, reputational damages, continuity risks, compliance risks, etc. It is also important to keep the confidence of customers, stakeholders, and investors intact.
Which risk mitigation strategies include outsourcing services and purchasing insurance?
Outsourcing services and purchasing insurance are a part of risk transfer strategies. They transfer a portion of risk to other entities. For example, when outsourcing services, the risk of operational disruptions is managed by the provider. Similarly, with insurance, a significant portion of the financial burden from a loss is transferred to the insurer.
Payal Wadhwa
Payal is your friendly neighborhood compliance whiz who is also ISC2 certified! She turns perplexing compliance lingo into actionable advice about keeping your digital business safe and savvy. When she isn’t saving virtual worlds, she’s penning down poetic musings or lighting up local open mics. Cyber savvy by day, poet by night!
Explore more
research & insights curated to help you earn a seat at the table.



















