Let me paint a picture for you: a world of cybercrime where instead of elaborate heists, people can buy goods that can freeze entire businesses. That is not a fantasy or an imaginary future shown on Black mirror, it is Ransomware as a Service (RaaS).
These are the dark web enterprises that are offering prepackaged ransomware kits along with the step-by-step instructions on how to use them to make cybercrime more accessible. RaaS operators also use conventional tactics by copying mainstream software firms’ business models, including providing support and profit splitting schemes for affiliates.
TL;DR
| Ransomware as a Service (RaaS) is turning cybercrime into a business, lowering the bar so that even those without technical skills can launch sophisticated attacks. |
| Perimeter-based security isn’t enough anymore—Zero Trust Architecture (ZTA) is becoming essential by requiring constant verification, removing blind trust, and locking down critical systems to stop attackers from moving freely. |
| Rolling out ZTA doesn’t have to happen overnight; starting with identity checks, network segmentation, and ongoing monitoring allows organizations to adopt Zero Trust without overhauling everything at once. |
The true cost of cybercrime
For cybercriminals, RaaS represents a low-risk, high-reward opportunity, often backed by anonymity and decentralized networks.
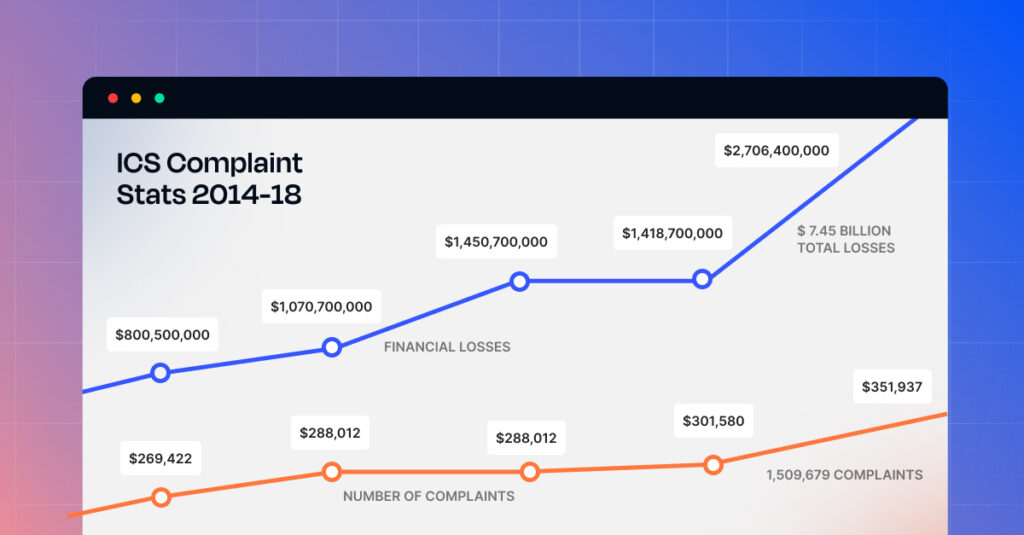
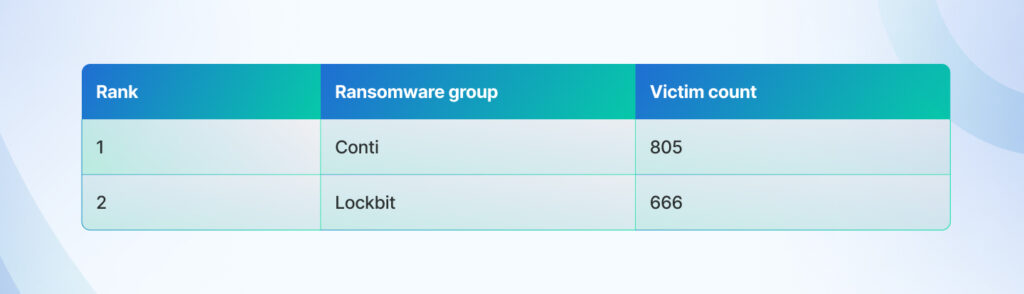
In 2022, the average ransom demand skyrocketed to $2.2 million, a staggering 144% increase from the previous year. Meanwhile, ransomware incidents targeted 14 out of 16 critical infrastructure sectors in the U.S., underscoring the far-reaching impact of this menace. RaaS groups like Conti and LockBit operate with a level of sophistication that rivals legitimate software enterprises, complete with customer support, subscription tiers, and even performance metrics for affiliates.
The proliferation of RaaS raises a pressing question: how can organizations defend themselves in a world where cybercrime is as easy as subscribing to Netflix?
Understanding the seedy ecosystem behind RaaS
To truly comprehend the rise and impact of Ransomware-as-a-Service (RaaS), it’s essential to unpack the organizational dynamics and the division of labor that fuels this growing underground economy.
RaaS has introduced a franchise-like model that distributes responsibilities across specialized roles. This division of labor is not only efficient but mirrors legitimate business structures, with each role contributing to the seamless operation of the ransomware ecosystem.
Creators
Creators are individuals who craft ransomware software, exploit kits, and other supporting technologies like encryption tools or blockchain interfaces. In some cases, tools originally designed for legitimate uses, such as penetration testing or data cloning, are repurposed for malicious intent.
Operators
Operators integrate various tools and create platforms where affiliates can easily access and deploy ransomware. These platforms range from simple encrypted communication channels to sophisticated web portals that provide dashboards for tracking infections, ransom payments, and affiliate earnings.
Affiliates
Affiliates often rely on phishing campaigns, social engineering, or exploiting known vulnerabilities to gain access to victim systems. Their success depends on their ability to exploit insider information, target critical systems, and pressure victims into paying ransoms.
Moles
In some cases, ransomware attacks are bolstered by Moles—individuals with direct access to the victim’s systems. These could be insiders, such as disgruntled employees, who deliberately introduce ransomware into an organization or provide sensitive information to affiliates.
Contact centers
Contact Centers play a critical role in victim interactions. These centers assist victims in navigating the ransom payment process, ensuring that transactions proceed smoothly. If victims resist paying, contact center agents escalate pressure by threatening to release stolen data or publicize sensitive information.
Bulletproof hosting centers
To ensure operational continuity, RaaS ecosystems rely on ‘Bulletproof’ Hosting Providers, which offer secure and anonymous hosting services for their platforms and command-and-control servers.
Currency exchange
Currency Exchanges play a pivotal role in monetizing the proceeds of ransomware attacks. Ransoms, typically paid in cryptocurrency, are processed through these exchanges to convert the funds into fiat currencies. This step often involves complex laundering techniques to obscure the transaction trail and evade scrutiny, adding another layer of sophistication to the RaaS model.
RaaS is an epidemic.
What began as opportunistic hacks by lone actors has evolved into a sophisticated, profit-driven economy, fueled by the accessibility and scalability of RaaS. This democratization of cybercrime is why RaaS is thriving. It’s not just hackers and tech-savvy criminals anymore; RaaS makes it possible for anyone with the right tools to participate. From the creator of the ransomware itself to the affiliate deploying the attack, to the “contact centers” managing victim negotiations, every part of this operation has been industrialized.
It would be a fair question to ask, why is Raas rising? What makes it a lucrative business, so to speak.
What makes RaaS a lucrative business?
It’s simple. Raas is thriving because it mirrors a legitimate business.
- RaaS lowers the technical barrier for entry, enabling individuals with no coding experience to orchestrate sophisticated attacks
- The financial incentives are staggering. In 2021, the average ransom demand surged to $2.2 million, with actual payments averaging $541,000. For RaaS operators, this means a steady stream of income by taking a percentage—typically 20-30%—of affiliate profits.
- Advances in encryption, anonymous payment systems like cryptocurrency, and “bulletproof” hosting have emboldened RaaS operators.
The carefully organized labor division makes RaaS highly efficient and adaptable, ensuring operators can focus on scaling their operations while affiliates handle the front lines.
How do we combat this epidemic?
For ages, cybersecurity hinged on the castle-and-moat model: build strong defenses at the edge, and everything inside stays safe. But RaaS thrives because this model assumes trust where none should exist. Zero Trust Architecture rejects trust entirely. Instead of assuming that insiders, devices, or systems are inherently secure, it verifies each interaction, every time.
“Every entity inside and outside the network must prove its legitimacy repeatedly”
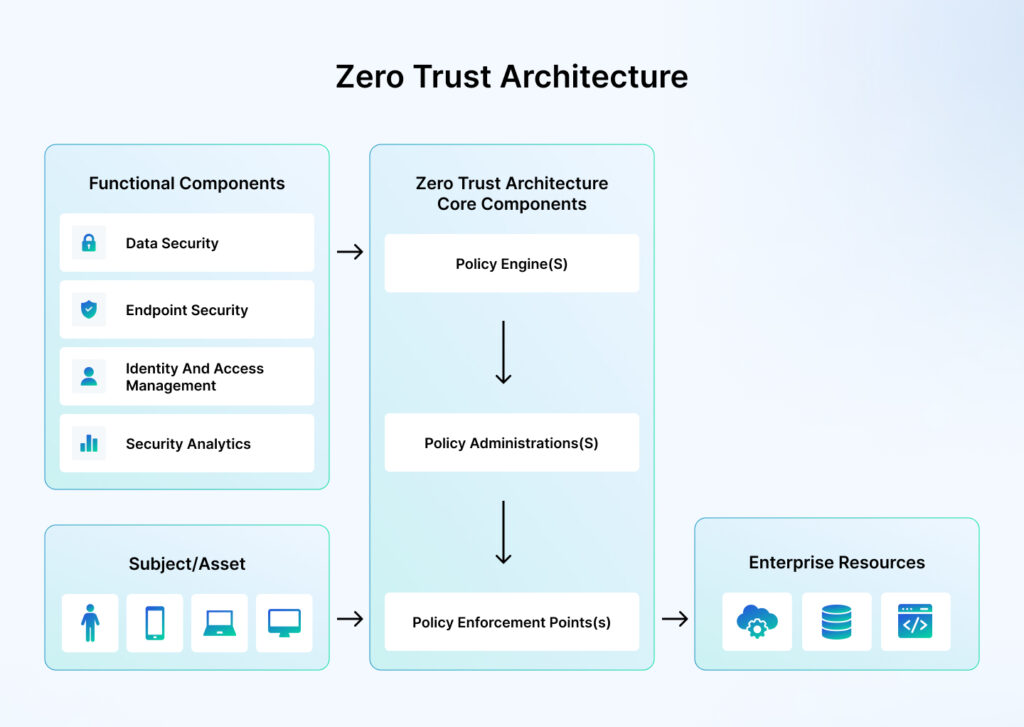
At the heart of a Zero Trust Architecture (ZTA) lie two critical components: the Policy Engine (PE) and the Policy Administrator (PA). Together, they form the decision-making and enforcement backbone of ZTA. The Policy Engine dynamically evaluates access requests based on a combination of criteria such as user identity, device security posture, and environmental factors. Once a decision is made, the Policy Administrator enforces it, ensuring that access controls are applied closer to the resource rather than relying on broad, implicit trust zones.
The core tenets of ZTA:
From theory to implementation, Zero Trust Architecture (ZTA) is more than a set of rules—it’s a mindset shift that treats every interaction within your network as potentially harmful until proven otherwise. To truly build resilience, it’s essential to ground your approach in a few guiding principles:

Regardless of the location, secure all communications
It doesn’t matter if the traffic is internal or external—every interaction must be verified. The traditional assumption of trust within the network perimeter no longer holds. By treating all activity as untrustworthy until authenticated, organizations can greatly minimize vulnerabilities.
Enforce dynamic policies
Access policies shouldn’t remain static; they need to adjust in real-time based on what’s happening. This could mean blocking access if a user’s device is suddenly flagged for suspicious behavior or allowing additional permissions when specific conditions are met.
Continuously monitor and assess
Simply granting access isn’t enough. By continuously watching over user activity, device health, and network behavior, subtle risks can be caught early—before they snowball into larger issues.
Building a Zero Trust environment isn’t about replacing everything you already have. It’s about layering scalable, adaptable deployment models that suit your operational needs. Here are a few practical ways to deploy ZTA:
- Device agent systems
These systems ensure that every endpoint—laptops, mobile phones, or IoT devices—has an agent installed to enforce security policies. This stops compromised devices from accessing sensitive resources, no matter where they are. - Enclave gateways
Think of these as digital barricades. They segment your network into smaller zones, protecting critical data by isolating it from less secure parts of your environment. If an attacker breaches one section, they’re stopped from moving deeper. - Resource portals
Portals act like security checkpoints, managing access to resources. Users interact with a secure interface that handles their requests without exposing the underlying infrastructure.
When implementing Zero Trust Architecture, governance, risk, and compliance (GRC) becomes the glue that binds these components together. Endpoints, gateways, and resource portals are critical control points, but their effectiveness relies on clear policies, risk assessments, and continuous compliance checks.
Sprinto seamlessly integrates these elements into your Zero Trust journey by automating compliance management, ensuring that every device, system, and access point aligns with your security and regulatory requirements—without adding operational friction.
Build a trust architecture that you can trust!
These deployment models aren’t one-size-fits-all. Most organizations combine them to address specific scenarios:
- Remote work
Endpoint security ensures employees working from home can’t unintentionally open doors for attackers. - Multi cloud environment
Fine-tuned access controls enable teams to collaborate securely across different cloud platforms. - Contractors and visitors
Temporary credentials limit what external users can access and prevent them from moving laterally within the network. - Cross enterprise collaboration
Dynamic enforcement makes it possible to share data securely with partners, without exposing your sensitive systems.
For most organizations, the transition does not and cannot happen overnight. Most operate in hybrid environments during the transition, combining traditional perimeter defenses with Zero Trust elements. This gradual adoption allows enterprises to:
- Identify and secure critical resources first.
- Test and refine ZTA components in controlled environments.
- Integrate Zero Trust principles with existing workflows without disrupting business operations.
But how do you implement ZTA
Breaking down the build
Step 1: Identity at the core
Identity verification is non-negotiable. Start with enforcing multi-factor authentication (MFA) for every user, every access attempt. Go beyond static credentials—leverage contextual factors like location, device health, and behavior patterns to verify users dynamically.
Step 2: Segmentation and isolation
Don’t let attackers move laterally once they’re in. Break your network into zones with strict access controls. High-value systems—financial data, intellectual property, or backups—should be in isolated segments, accessible only to a select few under tightly monitored conditions.
Step 3: Least privilege access
Audit permissions across your organization. Over-permissioned accounts are low-hanging fruit for attackers. Implement role-based access controls (RBAC) and ensure users only have the access they need to do their jobs—nothing more.
Step 4: Build in monitoring
Visibility isn’t just about compliance audits; it’s the lifeblood of ZTA. Deploy tools that provide continuous monitoring of traffic, user activity, and data flows. Anomalous behavior—like a spike in file encryption—should trigger automated containment.
Choose the right algorithm for your ZTA
The trust algorithm (TA) forms the backbone of ZTA by determining who gets access, under what conditions, and how access is maintained or revoked in real time. Trust algorithms broadly fall into two categories:
- Criteria based algorithms: These enforce access through binary decisions. If predefined criteria are met—such as valid credentials, a healthy device posture, and location-based rules—access is granted. This approach is straightforward but lacks the nuance needed for evolving threats or anomalous behavior.
- Example: Granting access to employees within the office premises during standard working hours.
- Score based algorithms: These calculate a dynamic confidence score by analyzing multiple data points, such as user history, device behavior, and environmental signals. Access is granted or restricted based on whether the score crosses a pre-set threshold. This model is more flexible and adaptable to changing circumstances.
Example: Detecting and flagging unusual login attempts outside normal patterns, such as a sudden midnight login from an unrecognized IP.
Another consideration is whether the TA evaluates access requests individually (singular) or within the context of historical patterns (contextual).
- Singular TAs: Ideal for organizations where speed and simplicity are paramount, these algorithms treat each request independently. While faster, they may overlook sophisticated threats like insider attacks or credential misuse.
- Contextual TAs: These analyze user behavior over time, comparing current activity against historical trends. For instance, an accountant accessing financial systems outside work hours from a foreign IP would trigger an alert. While resource-intensive, this approach significantly reduces the risk of undetected breaches.
Tailoring it to your fit
Implementing a trust algorithm isn’t just a one-time setup; it’s an iterative process. Start small—secure your most critical resources first and expand gradually. Monitor its performance, collect feedback, and refine the algorithm over time. By doing so, your TA becomes not just a gatekeeper but a dynamic safeguard, ensuring resilience against even the most sophisticated ransomware attacks.
The road ahead
Zero Trust Architecture isn’t just a defensive posture—it’s a calculated disruption of the assumptions that allow threats like RaaS to flourish. It takes the very foundation of implicit trust and replaces it with unyielding verification, granular access control, and relentless monitoring.
But the beauty of ZTA lies in its pragmatism. It doesn’t demand that you tear down and rebuild; it encourages incremental, strategic implementation. Start with securing identities, segment high-value systems, and gradually expand your zero-trust footprint across hybrid environments. Tailor your trust algorithms—be it criteria-based for simplicity or contextual for nuance—to reflect the unique demands of your organization. The power of ZTA isn’t just in its principles but in how those principles are adapted to the realities of your enterprise.
Frequently Asked Questions
Why is Ransomware as a Service (RaaS) so dangerous compared to traditional cyberattacks?
RaaS takes the complexity out of launching ransomware attacks, letting almost anyone get involved—no coding skills required. This means more attacks, more often, and from a wider range of actors. It’s like handing out blueprints for bank heists to anyone willing to pay. The scale and ease of access make RaaS a bigger threat than isolated ransomware incidents in the past.
How is Zero Trust different?
Zero Trust flips the traditional “trust but verify” mindset on its head. Instead of assuming that systems or users inside the network are safe, Zero Trust assumes nothing is secure by default. It constantly checks identities, monitors activity, and limits access to only what’s necessary. Think of it as having security guards at every door rather than just at the front gate.
Who are the typical targets of RaaS attacks?
RaaS affiliates go after organizations of all sizes, but critical infrastructure, healthcare, financial services, and large enterprises are frequent targets. However, small and medium businesses aren’t safe either—attackers know they often lack the resources to defend against ransomware, making them easier to exploit.
Heer Chheda
Heer is a content marketer at Sprinto. With a degree in Media, she has a knack for crafting words that drive results. When she’s not breaking down complex cyber topics, you can find her swimming or relaxing by cooking a meal. A fan of geopolitics, she’s always ready for a debate.
Explore more
research & insights curated to help you earn a seat at the table.


















