Mastering the Strategic Elements of Audit Readiness in the Modern Enterprise
Today, a critical paradox confronts compliance leaders. Despite significant investments in sophisticated GRC (Governance, Risk, and Compliance) platforms and automation tools, many mid-market and enterprise organizations continue to experience unexpected friction during audit cycles.
Our research across 200+ organizations has identified what we call the “invisible compliance gap”—the human, cultural, and contextual dimensions of audit readiness that exist beyond the reach of even the most sophisticated compliance tools. For executive leaders navigating increasingly complex compliance environments, mastering these invisible dimensions isn’t just about audit efficiency—it’s a matter of strategic organizational resilience and competitive advantage.
This comprehensive guide examines the four hidden dimensions driving audit pain and provides a strategic framework to transform compliance from a perpetual pain point into a genuine competitive advantage.
Introduction: The Compliance Excellence Paradox
Organizations today face an unprecedented compliance burden. The proliferation of frameworks—from SOC 2 and ISO 27001 to GDPR, HIPAA, and industry-specific requirements—has transformed compliance from a periodic exercise into a continuous business function. In response, organizations have invested heavily in GRC platforms, automation tools, and specialized compliance personnel.
Yet a troubling pattern persists: despite these investments, audit cycles continue to create significant organizational strain. Project timelines extend beyond projections, resource requirements exceed allocations, and findings emerge despite apparent control effectiveness.
This paradox demands explanation. If organizations are investing in compliance tools and implementing required controls, why does the audit process remain so painful?
Our research across mid-market and enterprise organizations reveals that traditional compliance approaches address only the visible dimensions of audit readiness—documented controls, collected evidence, and tracked remediation items. However, the most significant sources of audit friction exist in invisible dimensions that tools cannot detect or measure.
The Four Hidden Dimensions Driving Audit Pain
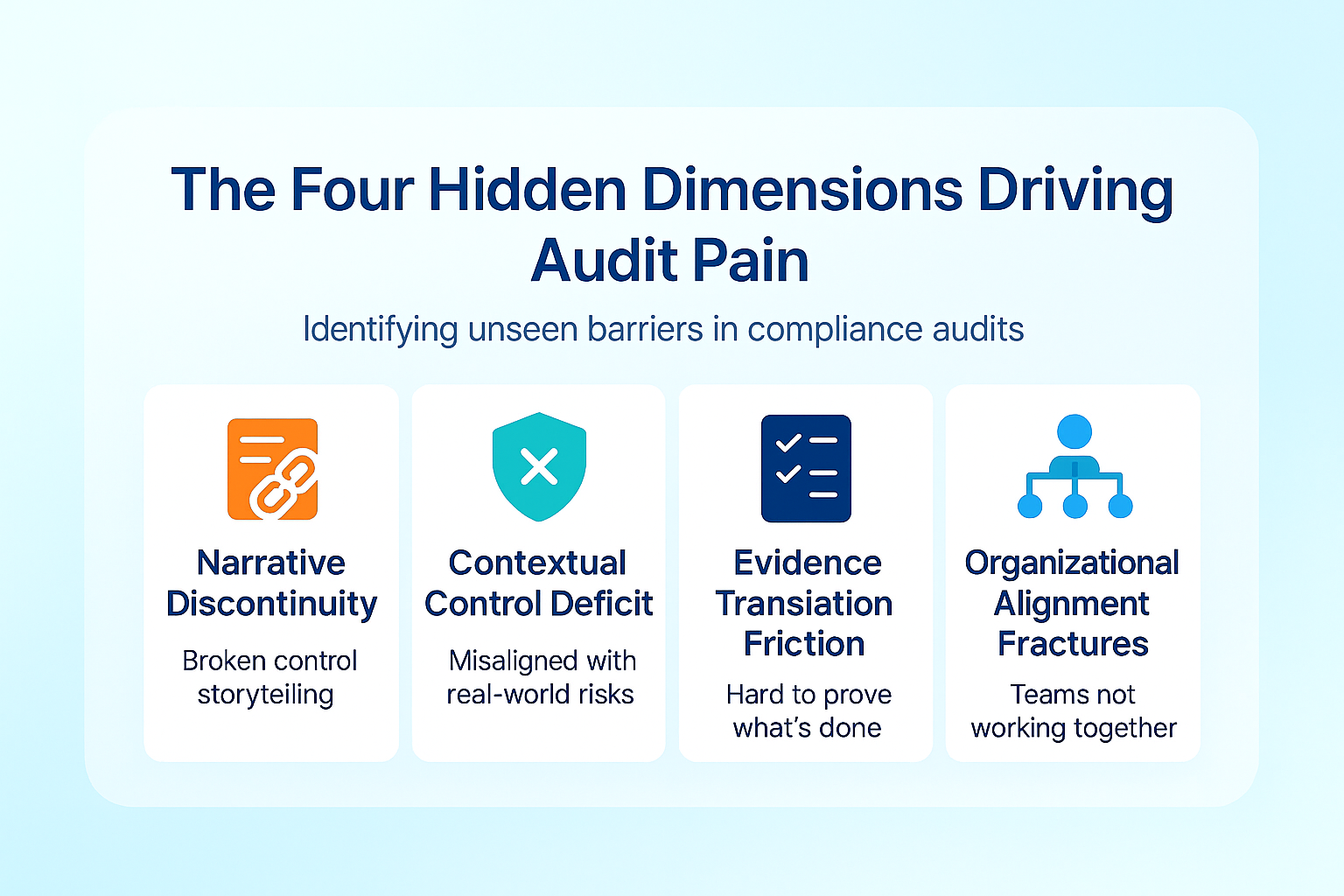
1. Narrative Discontinuity: The Broken Storytelling Challenge
At its core, an audit is fundamentally a narrative exercise—an organization telling the cohesive story of how it protects its assets, customers, and data. When this narrative lacks coherence across control domains, auditors must work harder to connect disjointed evidence into a compelling security story.

What is Narrative Discontinuity?
Narrative discontinuity occurs when control documentation, evidence, and explanations lack a cohesive thread that ties them together. Rather than presenting a unified security strategy, organizations with narrative discontinuity offer fragmented control descriptions that fail to show how individual controls work together to address specific risks.
For example, an organization might have excellent access control mechanisms (who can access systems) and strong encryption protocols (how data is protected at rest), but if these controls aren’t explained as complementary parts of a comprehensive data protection strategy, auditors struggle to evaluate their collective effectiveness.
The Business Impact
According to our research study, organizations experiencing high narrative discontinuity face:
- Extended audit timelines (average increase of 40%)
- 3.5x more evidence requests than comparable organizations
- Expanded testing samples (from typical 25 samples to 40+ samples)
- Contradictory interpretations of control effectiveness between audit teams
Why Tools Can’t Solve This Problem
Compliance platforms excel at tracking control implementation and evidence collection but cannot evaluate narrative coherence. The connection between controls exists in how they’re explained and contextualized—a fundamentally human communication challenge that no dashboard can measure.
2. Contextual Control Deficit: Technically Compliant, Strategically Vulnerable
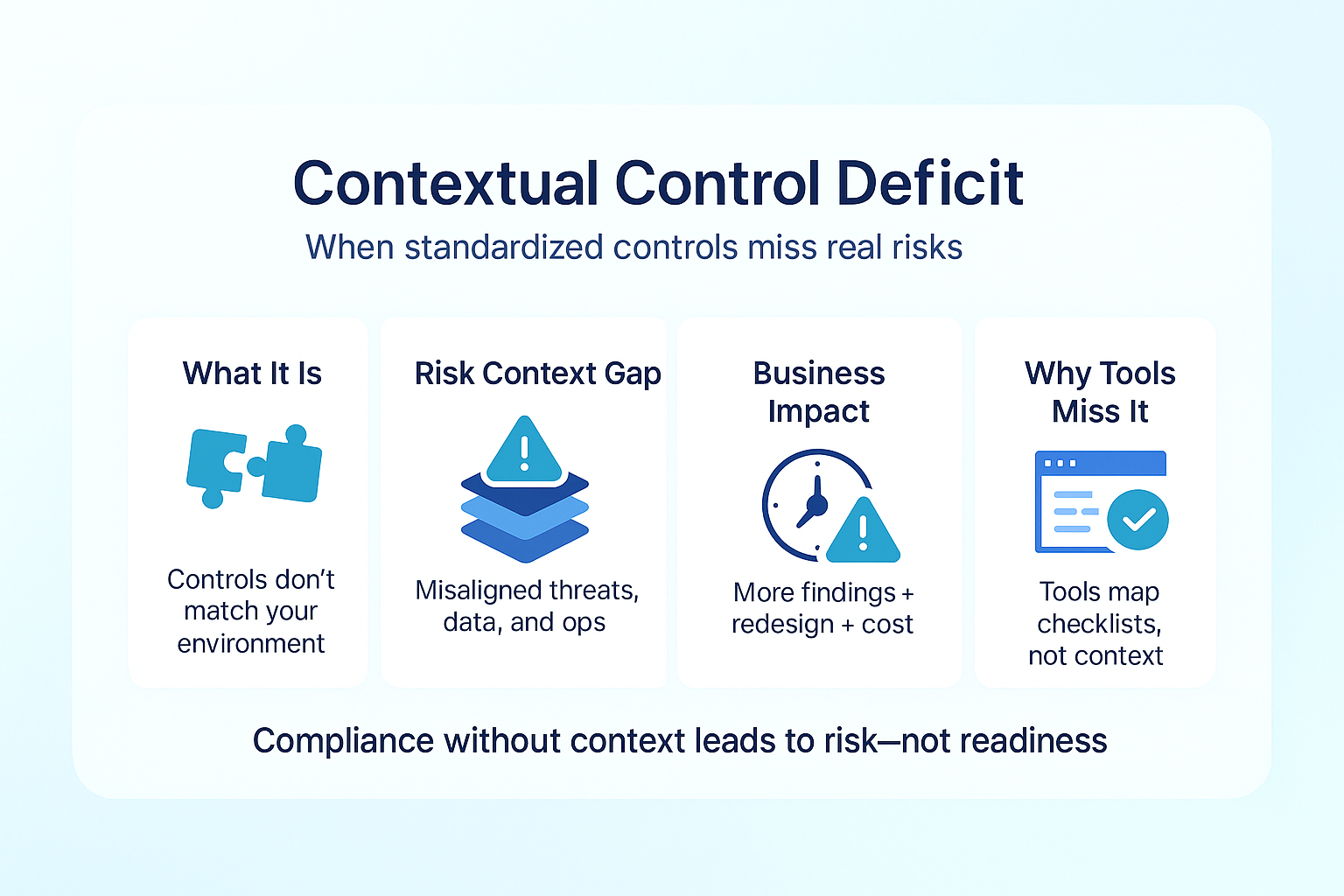
Compliance frameworks necessarily standardize controls across diverse organizations. However, auditors evaluate control effectiveness not just against framework requirements but within the unique risk context of each organization. This creates an insidious challenge: controls that meet technical requirements but fail to address organization-specific threat models, data flows, or business processes.
What is Contextual Control Deficit?
Contextual control deficit occurs when organizations implement standardized framework controls without adapting them to their specific risk environment. The result is controls that satisfy checklist requirements but miss the underlying security objectives given the organization’s unique circumstances.
For example, a standard control might require “regular vulnerability scanning,” which an organization implements as quarterly scans. However, if that organization has a rapid development cycle with weekly code releases, quarterly scanning creates extended periods of potential vulnerability—a gap immediately apparent to auditors familiar with the company’s deployment practices.
The Business Impact
Organizations experiencing high contextual control deficit typically face:
- Repeated findings on controls despite documentation completeness
- Multiple rounds of remediation focusing on fundamental control redesign
- Increased audit scope as auditors identify contextual gaps
- Higher audit costs due to expanded testing and follow-up activities
Why Tools Can’t Solve This Problem
GRC tools excel at mapping controls to framework requirements but cannot evaluate whether those controls adequately address organization-specific risks. This contextual evaluation requires deep understanding of both the business environment and the spirit behind framework requirements—a nuanced assessment no tool can perform.
3. Evidence Translation Friction: Doing the Work but Missing the Proof
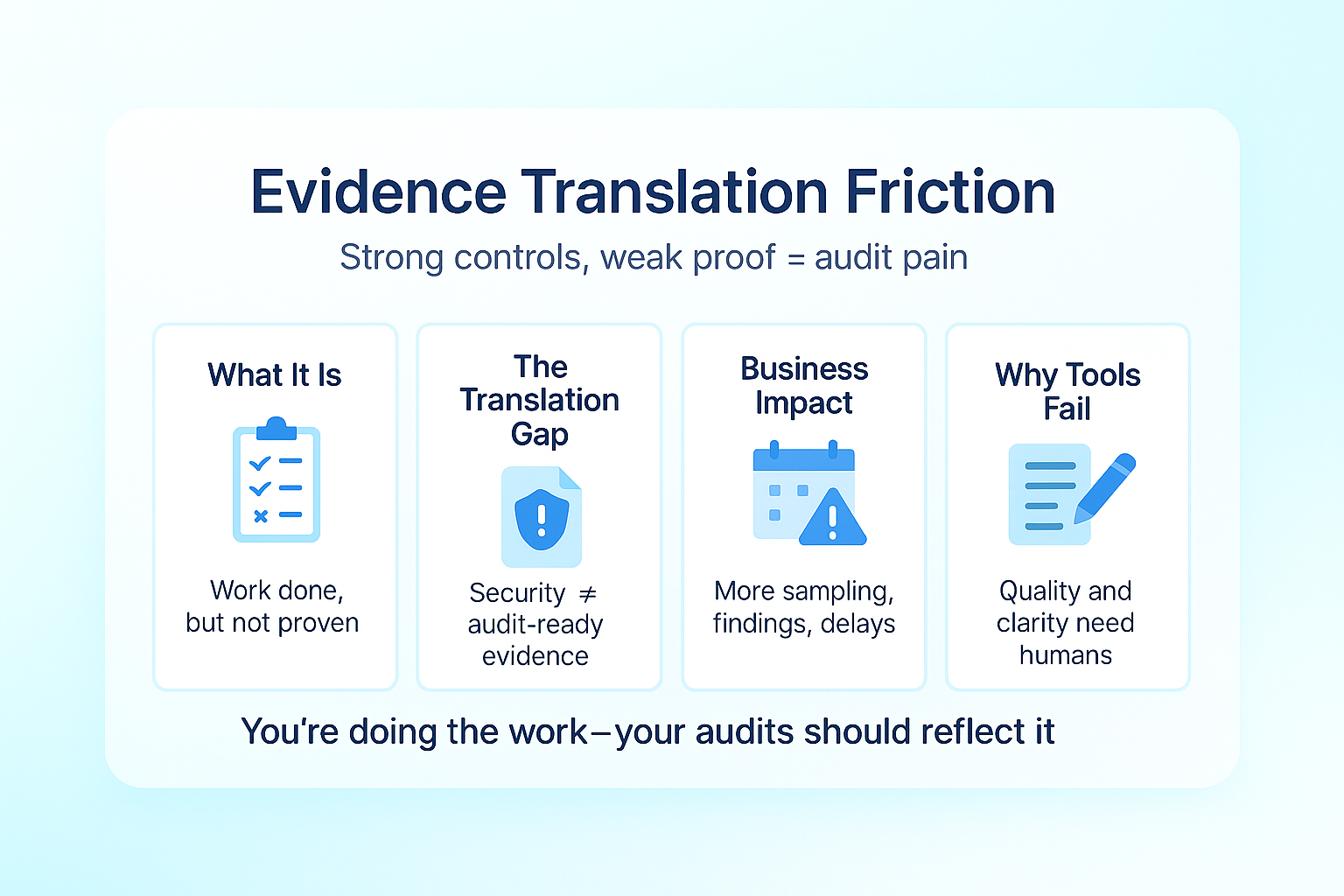
Perhaps the most common yet overlooked audit pain stems from a fundamental disconnect: organizations frequently possess robust security practices but struggle to translate operational reality into audit-ready evidence. This translation gap creates a situation where actual security exceeds documented security, yet audit findings suggest the opposite.
What is Evidence Translation Friction?
Evidence translation friction occurs when security and operational teams perform necessary security activities but don’t document them in ways that clearly demonstrate control effectiveness to auditors. The gap isn’t in doing the work—it’s in proving the work was done effectively.
For example, an organization might diligently review access privileges quarterly, but if they don’t document the methodology, exceptions identified, actions taken, and business justifications for decisions, auditors cannot validate that the review was comprehensive and effective.
The Business Impact
Organizations with high evidence translation friction typically experience:
- Repeated requests for alternative evidence
- Expanded control testing and sampling
- Findings that don’t reflect actual security posture
- Resource-intensive last-minute evidence gathering
Why Tools Can’t Solve This Problem
While compliance platforms can store evidence and track collection status, they cannot evaluate evidence quality or translate operational activities into auditor-friendly documentation. This translation requires understanding not just what evidence to collect, but how to present it in ways that clearly demonstrate control effectiveness—a fundamentally human communication skill.
4. Organizational Alignment Fractures: The Cultural Compliance Gap
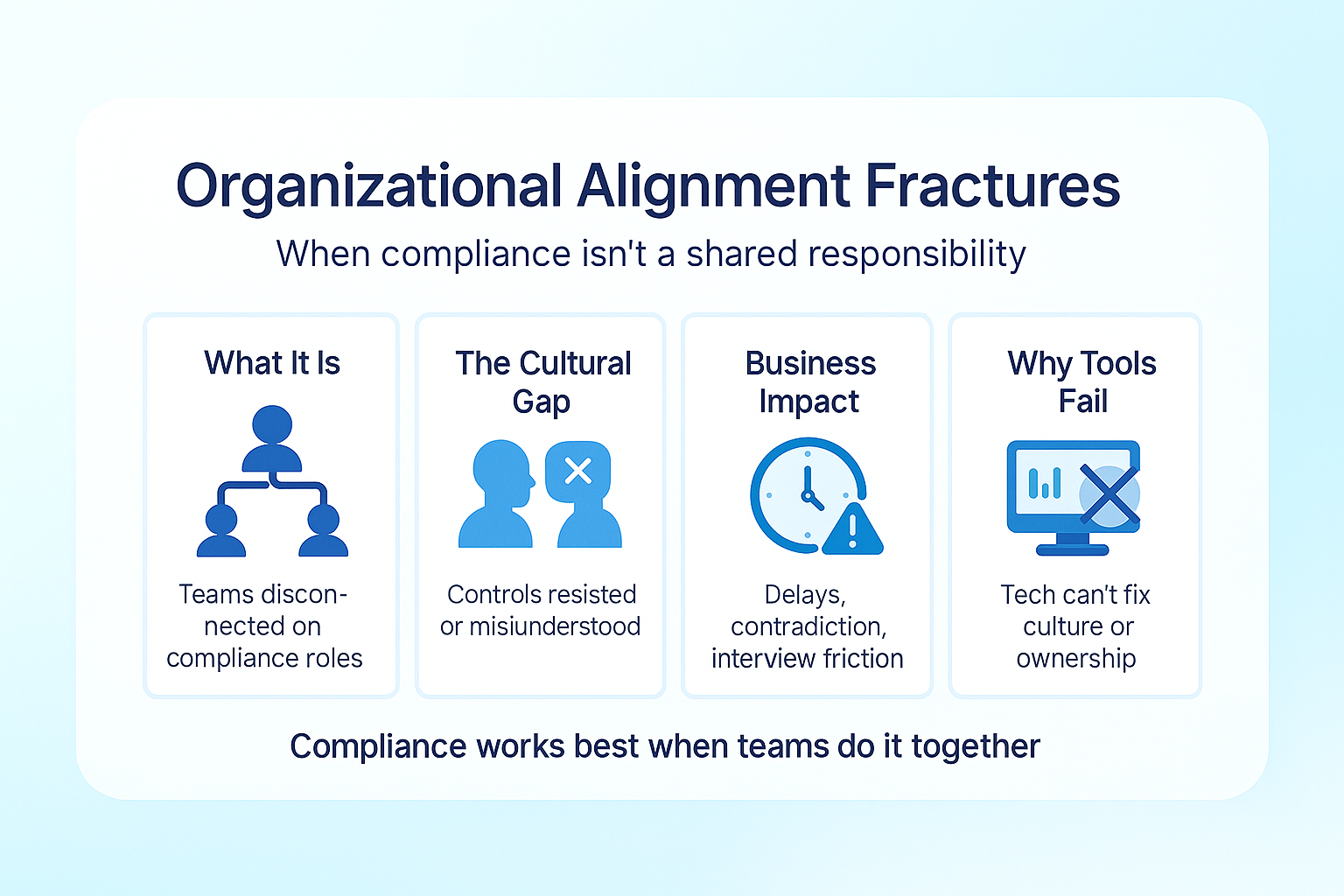
The most elusive dimension of audit pain stems from misalignment between compliance functions and operational teams. When compliance is perceived as an isolated function rather than an integrated business process, even perfect technical controls encounter resistance during validation.
What is Organizational Alignment Fracture?
Organizational alignment fracture occurs when there’s disconnection between teams responsible for compliance oversight and those responsible for executing control activities. This misalignment manifests as delays, inconsistencies, and contradictions during the audit process.
For example, if the security team designs access control procedures without input from development teams, developers may create workarounds that undermine control effectiveness—a contradiction immediately apparent when auditors interview personnel across departments.
The Business Impact
Organizations with significant alignment fractures experience:
- Delayed evidence collection and inconsistent responses
- Contradictory information provided to auditors
- Defensive postures during auditor interviews
- Extended audit timelines due to clarification needs
Why Tools Can’t Solve This Problem
No compliance platform can detect or bridge cultural gaps between teams. These alignment issues exist in organizational culture, communication patterns, and shared objectives—invisible dimensions that significantly impact audit experience but remain outside the scope of technological solutions.
The Strategic Framework: Building an Integrated Compliance Ecosystem
Addressing these invisible dimensions of audit pain requires a strategic approach that transcends traditional compliance tooling. Our research identifies four pillars that, when implemented together, transform compliance from a perpetual pain point to a strategic advantage.
Pillar 1: Narrative Architecture
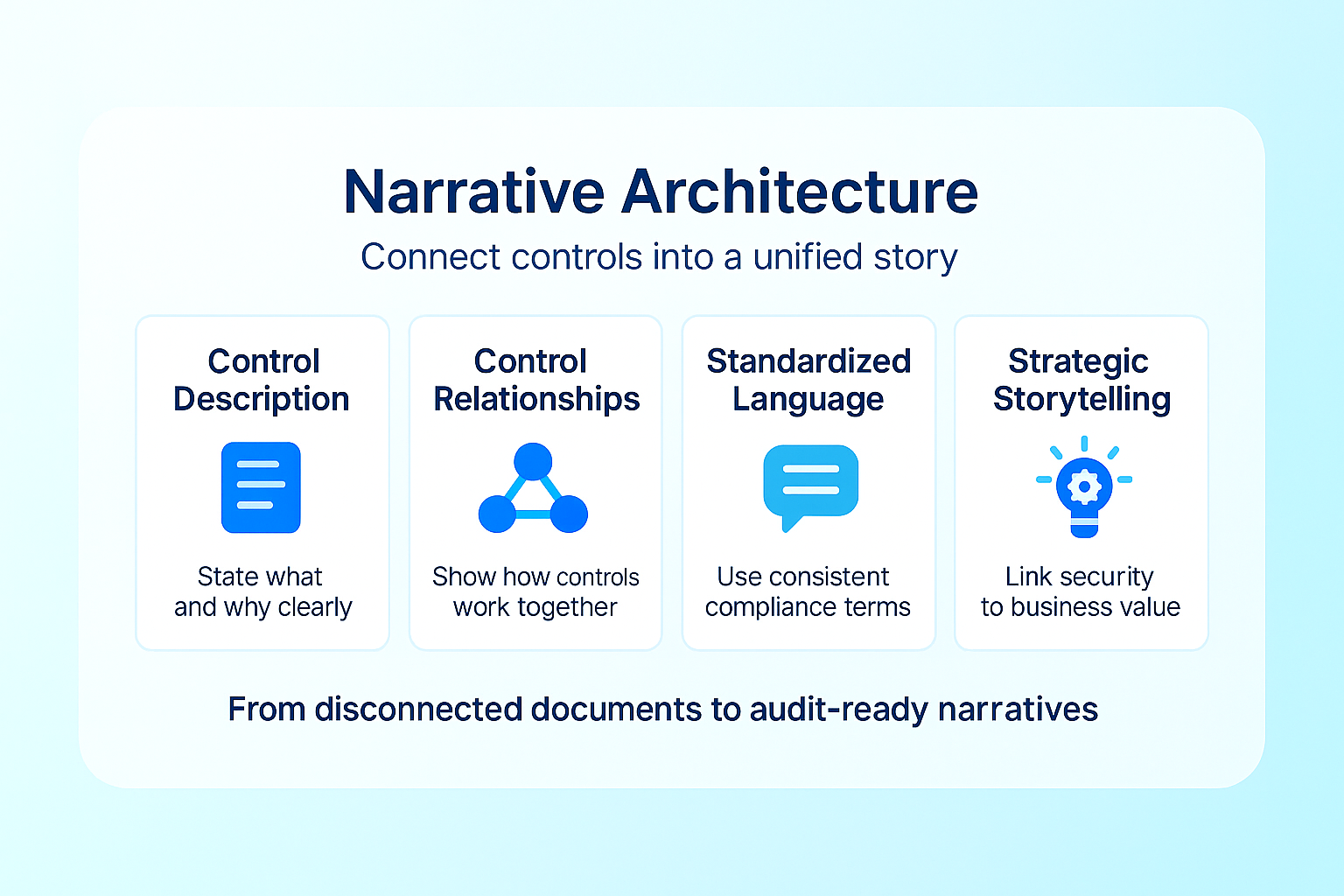
Building a coherent compliance narrative requires deliberate design of how controls are described, connected, and contextualized within the broader security strategy.
What is Narrative Architecture?
Narrative architecture is the intentional design of control documentation to tell a cohesive security story. This approach ensures that controls aren’t presented as isolated requirements but as integrated components of a comprehensive risk management strategy.
Implementation Strategy:
- Develop Risk-Centered Control Descriptions: For each control, create concise descriptions that explain the specific risk addressed and how the control mitigates that risk.
- Establish Explicit Control Relationships: Document how controls in different domains work together (for example, how access management, monitoring, and change management collectively protect critical assets).
- Create Control Families: Group related controls into logical families that address specific risk categories, making it easier for auditors to understand your overall approach.
- Implement Consistent Terminology: Develop a standardized glossary of terms used across all control documentation to eliminate confusion and contradiction.
Maturity Assessment Questions:
- Do your control descriptions explain both how the control works and why it exists?
- Can stakeholders from different departments consistently explain how controls relate to each other?
- Would an auditor seeing your controls for the first time understand your overall security approach?
- Do you have a consistent terminology framework used across all compliance documentation?
Pillar 2: Contextual Control Design
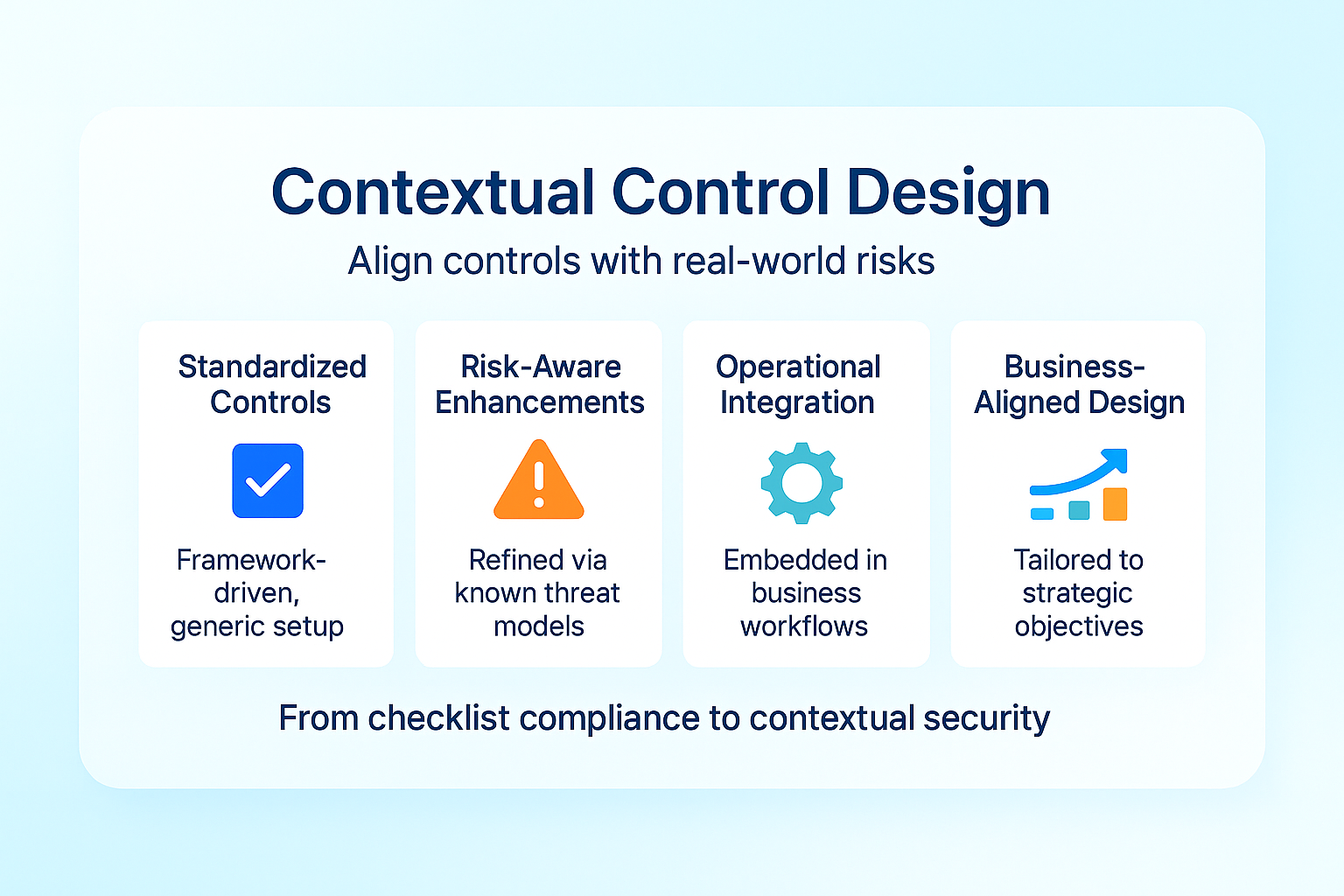
Moving beyond generic framework requirements to organization-specific control implementations dramatically improves both security effectiveness and audit experience.
What is Contextual Control Design?
Contextual control design involves adapting standardized framework controls to address the specific risk profile, operational model, and threat landscape of your organization. Rather than implementing controls exactly as described in frameworks, this approach focuses on achieving control objectives in ways aligned with organizational realities.
Maturity Progression:
- Framework-Driven (Basic): Controls are mapped directly from compliance requirements with minimal customization.
- Risk-Aware (Intermediate): Controls are enhanced based on general risk assessment but may not reflect specific operational contexts.
- Context-Integrated (Advanced): Controls are designed specifically for organizational threats and operational models.
- Business-Aligned (Optimal): Controls are embedded in business processes rather than maintained as separate compliance activities.
Implementation Strategy:
- Control Context Documentation: For each key control, document the specific organizational context that influences its design and implementation.
- Risk-Based Enhancement: Analyze standard controls against your specific threat model and enhance them to address organization-specific risks.
- Operational Integration Assessment: Evaluate how each control integrates with existing operational processes and identify opportunities for seamless embedding.
- Business Impact Analysis: Document how each control supports business objectives beyond compliance requirements.
Pillar 3: Evidence Translation Excellence
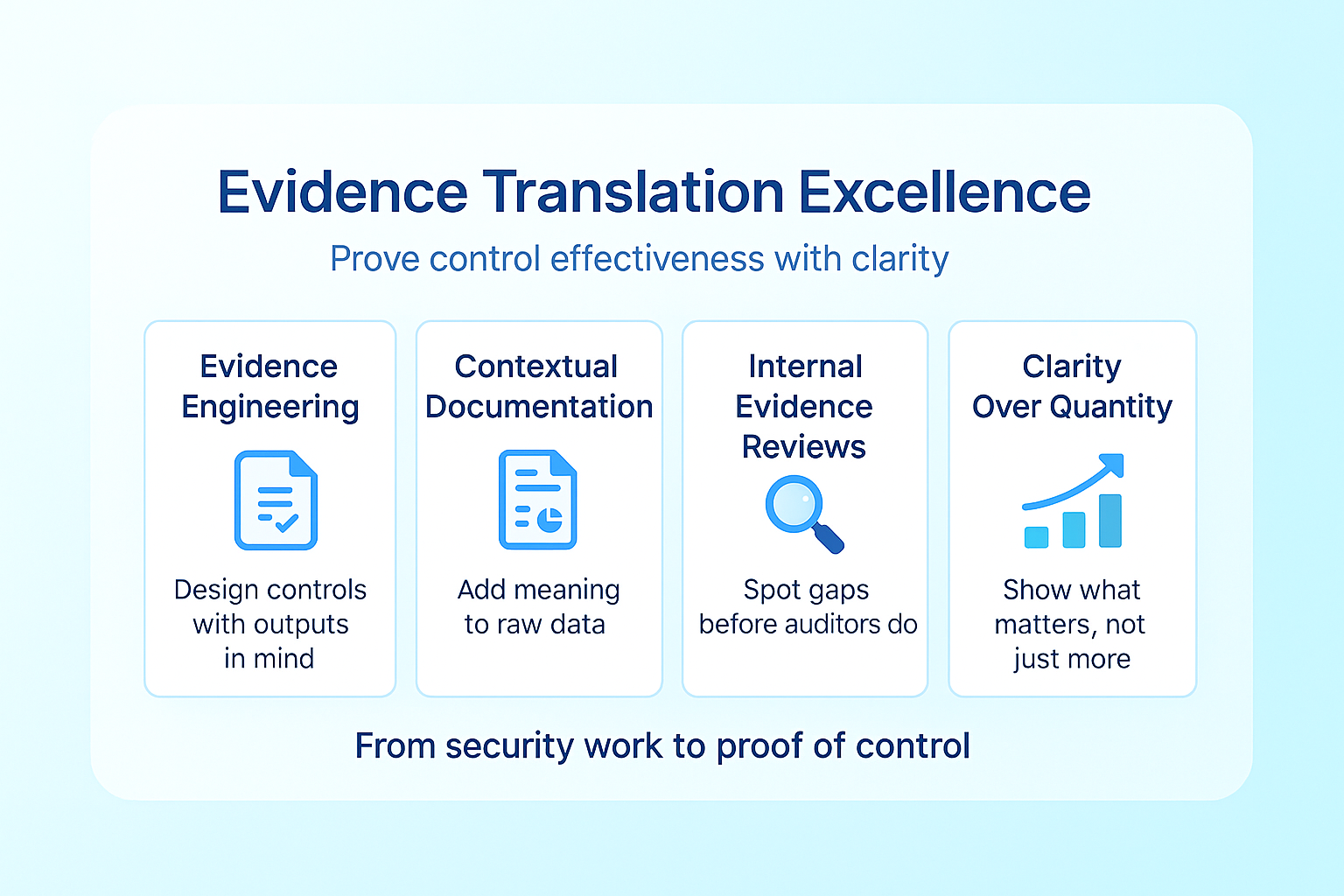
The ability to translate operational security practices into compelling audit evidence represents perhaps the highest-leverage improvement opportunity for most organizations.
What is Evidence Translation Excellence?
Evidence translation excellence is the organizational capability to systematically convert security activities into clear, convincing evidence that demonstrates control effectiveness to auditors. This approach focuses not just on doing security work but on documenting it in ways that make control effectiveness immediately apparent.
Three Critical Components:
- Evidence Engineering: Designing controls with evidence generation in mind and creating templated outputs for recurring activities. This approach builds evidence collection into control execution rather than treating it as a separate activity.
- Contextual Documentation: Providing business context alongside technical evidence. Rather than submitting raw system outputs, this approach includes explanations of what the evidence demonstrates and why it matters.
- Proactive Evidence Reviews: Conducting quarterly internal evidence assessments that simulate the auditor perspective. These reviews identify gaps in evidence clarity or completeness before auditors arrive.
Evidence Quality Assessment Checklist:
For each piece of evidence, organizations should answer:
- Does this evidence clearly demonstrate how the control operates?
- Is the scope of the control activity immediately apparent?
- Are exceptions documented with clear justification?
- Would someone unfamiliar with our environment understand what this evidence demonstrates?
- Does the evidence format allow for easy verification of completeness?
Organizations that systematically improve evidence quality experience dramatically different audit outcomes even without changing their actual security practices.
Pillar 4: Organizational Alignment Mechanisms
Creating unified ownership of compliance outcomes across operational, security, and business functions transforms the audit experience from confrontational to collaborative.
What is Organizational Alignment?
Organizational alignment refers to the degree to which different teams understand, value, and contribute to compliance objectives. In aligned organizations, compliance isn’t viewed as the responsibility of a dedicated team but as an integrated aspect of everyone’s role.
Transformation Roadmap:
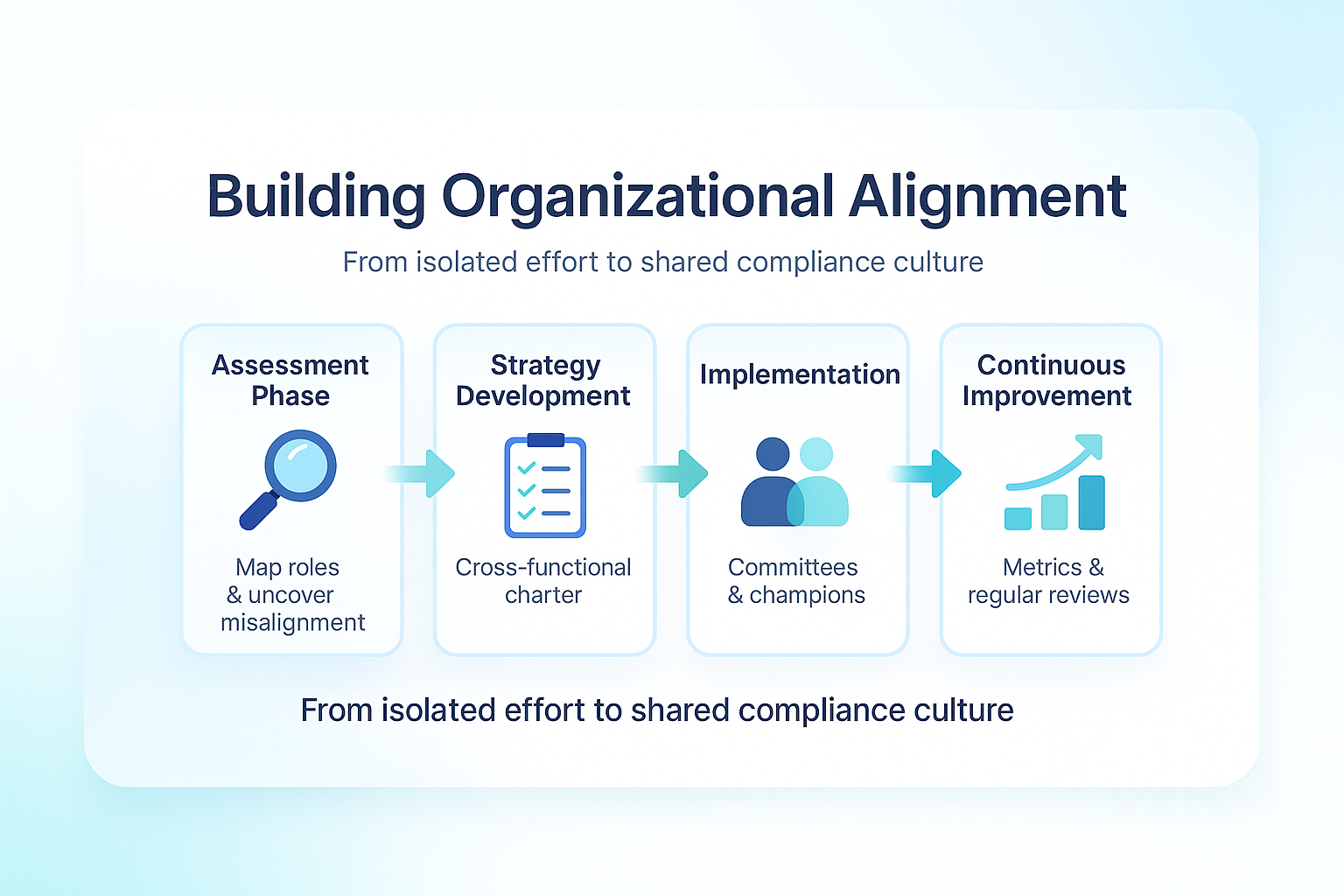
- Assessment Phase (Months 1-2): Map current compliance responsibilities and identify alignment gaps by surveying team members across departments about their understanding of and involvement in compliance activities.
- Strategy Development (Months 2-4): Create a cross-functional compliance charter and integrated governance model that clearly defines responsibilities and establishes collaborative processes.
- Implementation (Months 4-7): Establish compliance committees with representation from all key departments and deploy a compliance champions program to embed compliance perspective across the organization.
- Continuous Improvement (Months 7+): Conduct regular alignment assessments and track metrics that measure cross-functional collaboration on compliance activities.
Alignment Indicators:
Organizations can assess their alignment maturity by evaluating:
- How quickly teams respond to evidence requests
- Consistency of messaging about controls across departments
- Whether compliance considerations are integrated into project planning
- Level of proactive engagement from operational teams during audit preparation
Beyond Basic Compliance Metrics: Measuring What Matters

Traditional compliance metrics focus on control implementation percentages and finding counts. Leaders addressing invisible audit pain require more sophisticated measurement approaches that capture the dimensions that truly impact audit experience.
Leading Indicators of Excellence:
- Narrative Coherence Score: Measures the consistency of control descriptions across domains through periodic assessments where cross-functional team members evaluate control documentation for consistency and clarity.
- Evidence Quality Index: Assesses completeness and consistency of evidence against predefined templates by tracking characteristics like context inclusion, format consistency, and explanation clarity.
- Organizational Readiness Metrics: Tracks response time and quality of evidence preparation by measuring metrics like average time to fulfill evidence requests and percentage of evidence provided without follow-up.
- Evidence Acceptance Rate: Percentage of evidence accepted without follow-up requests, providing a direct measure of evidence quality from the auditor’s perspective.
- Control Maturity Assessment: 5-level maturity evaluation for key controls that goes beyond binary “implemented/not implemented” to assess design appropriateness, operational effectiveness, and continuous improvement.
- Compliance-Enabled Revenue: Deals accelerated or enabled by compliance posture, tracking instances where compliance certifications directly contributed to sales velocity or customer expansion.
The Strategic Imperative: From Compliance Cost to Competitive Advantage

As regulatory requirements intensify and compliance frameworks multiply, organizations that address only the visible dimensions of compliance find themselves in perpetual remediation cycles. The strategic advantage belongs to those who recognize that true compliance excellence exists in the invisible space between controls and culture.
Organizations that master the four pillars gain:
- Operational Efficiency: Dramatically reduced resource requirements for audit preparation and execution
- Strategic Focus: Less time spent on remediation allows more focus on strategic initiatives
- Market Advantage: Accelerated sales cycles due to demonstrated compliance excellence
- Audit Confidence: Predictable, consistent audit outcomes with minimal surprises
The most sophisticated compliance tools will never eliminate audit pain if they fail to address these invisible dimensions. But leaders who build organizational capabilities around narrative coherence, contextual controls, evidence translation, and cross-functional alignment will discover that compliance excellence becomes not just achievable but inevitable, transforming compliance froma cost center to a strategic advantage.
Conclusion: The Future of Compliance Excellence

The future belongs to organizations that recognize compliance not as a technical challenge but as a strategic capability. By addressing the invisible dimensions that tools cannot measure, forward-thinking organizations transform compliance from a perpetual struggle into a genuine competitive advantage.
The path forward requires not just investment in tools but in the human, cultural, and contextual elements that determine audit experience. Organizations that make this shift discover that compliance excellence doesn’t just reduce audit pain—it creates strategic opportunities that extend far beyond regulatory requirements.
Harsh
Explore more
research & insights curated to help you earn a seat at the table.

















