ISO 27001:2013 (An In-Depth Overview)
Anwita
Mar 27, 2024

In response to growing security concerns and breaches, the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) published ISO 27001 in 2005.
It was revised in 2013 to keep the document to sync with global changes in technology and processes, and most recently in 2022. The 2013 version is not significantly different from 2022 one and is relevant for the next three years.
What is ISO 27001:2013?
ISO 27001:2013 is an international standard that provides the requirements and guidelines for organizations to effectively manage and improve information security.
This framework offers best practices to secure data and boost security posture that helps manage a wide range of sensitive data related to their financial assets, intellectual property, and customer information. Organizations can use it to establish and implement their ISMS.
Importance of ISO 27001:2013
As more organizations embrace a digital approach, cloud security is needed more than ever. Data helps to measure the effectiveness of strategies, make decisions, and much more – it’s an essential asset for all functions. Malicious actors know this and are motivated to steal it.

Cyber resilience: Data losses are expensive and not easy to recover from. Most small and medium enterprises lack effective security measures and are likely to make common security mistakes.
An effective ISMS solves this by helping you address the existing gaps. The ISO guidelines cover all possible aspects of your digital infrastructure that need to be secured.
Kickstart compliance journey: The security requirements of ISO 27001 2013 are similar to that of related frameworks like SOC 2 and GDPR. When you implement ISO 27001, it acts as a baseline to add more security guidelines in the future.
Competitive advantage: Data security is not important to me and I don’t mind if it is stolen – said no customer ever.
While an ISO certification is not a legal requirement, it is good to have added credibility to showcase to customers. When your rivals don’t have one, it acts as a USP to build your brand.
In short, there are numerous benefits to ISO 27001 certification.
What does the ISO 27001:2013 standard include?
ISO 27001:2013 standard includes ten sections to help you holistically implement, establish, maintain, and improve your ISMS. These cover topics like planning, operation, improvement, and more. Section 6 (Planning) is critical as it addresses how organizations can identify risks and reduce them.
ISO 27001 2013 has Annex A, which consists of 14 controls. Organizations can choose the ones that apply based on a risk assessment.
- Information Security Policy
- Organization of Information Security
- Risk Assessment and Treatment
- Asset Management
- Access Control
- Cryptography
- Physical Security
- Operations Security
- Communications Security
- System Acquisition, Development and Maintenance
- Supplier Relationships
- Compliance with Legal Requirements and Industry Standards
- Information Quality Management
- Risk Monitoring and Review
Check out: In-depth Guide on ISO 27001 controls
What is the difference between ISO 27001:2013 and ISO 27001 2022?
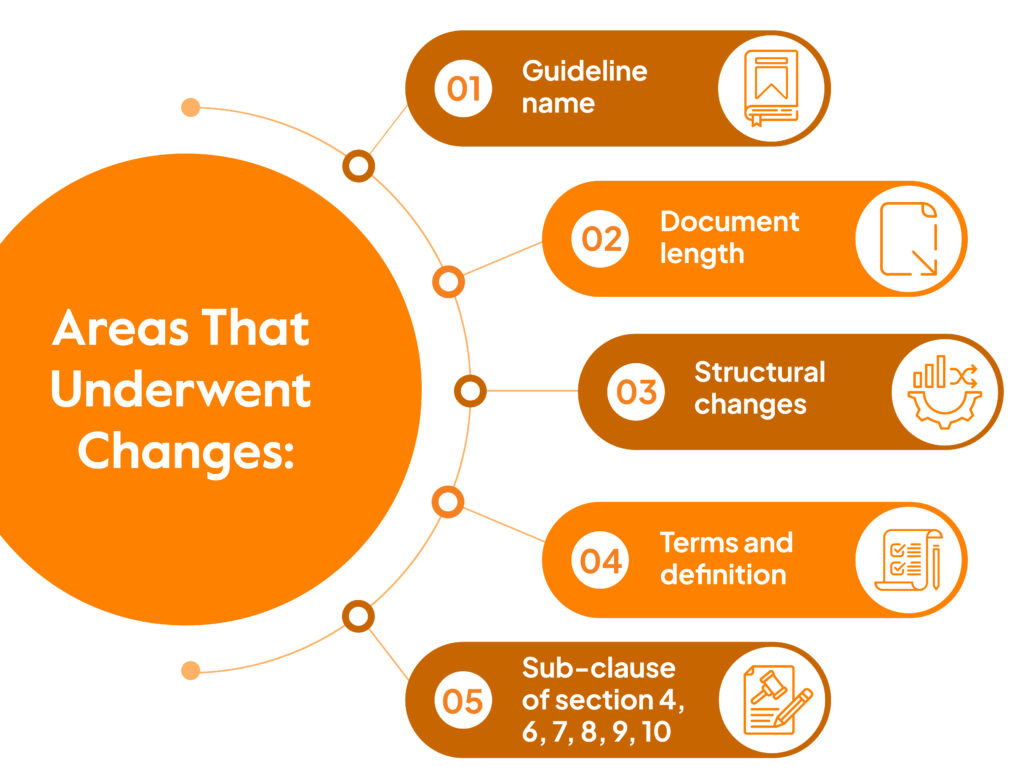
In short, nothing significant. There are a few structural changes and few updates in the Annex A controls. The notable differences between ISO 27001: 2013 and 2022 versions are changes in:
- Guideline name (now includes the term cybersecurity)
- Document length (decreased)
- Structural changes (now has better clarity)
- Terms and definition (now includes reference to ISO and IEC)
- Minor changes in the sub-clause of the following sections of the document:
- Context of organization
- Planning
- Support
- Operation
- Performance evaluation
- Improvement
- Category
- Number of controls
In Annex A, the number of controls has reduced to 93 and includes 11 new controls.
Also, check out: ISO 27001 audit checklist
Conclusion
ISO 27001 has a long list of requirements. While these guidelines help you identify gaps and list what to implement, it is not sufficient to keep everything up and running.
Whether you want to update your existing ISMS or implement one from scratch, Sprinto helps you with the end-to-end process. It puts your compliance program on autopilot, enables you to customize the minor functions, and continuously monitors the system for non-compliance.
Talk to our experts on how we can help you succeed in your ISO journey.
FAQs
What is ISMS?
An Information Management Security System (ISMS) is a set of policies and procedures that helps you manage and secure sensitive data.
The main goal of ISMS is to help security or IT administrators identify and mitigate risks in their system. It addresses behavior and technical controls to maintain the confidentiality, availability, and integrity of information assets.
What are the principles of ISO 27001:2013?
The three principles of ISO 27001 are:
Integrity, meaning the information is accurate and complete.
Confidentiality, meaning that only authorized people can view and manage that information.
Availability, meaning authorized personnels can view information as and when they require.
What are the ISO 27001:2013 controls?
Annex A of ISO 27001 2013 has 114 security controls. When you conduct a risk assessment and find gaps in your system, you can choose the appropriate controls to address those.
What are the benefits of ISO 27001:2013 certification?
ISO 27001:2013 certification helps organizations strengthen their security posture, gives a competitive advantage, reduces costs associated with data loss, and creates a base to gain certification for similar frameworks.
Anwita
Anwita is a cybersecurity enthusiast and veteran blogger all rolled into one. Her love for everything cybersecurity started her journey into the world compliance. With multiple certifications on cybersecurity under her belt, she aims to simplify complex security related topics for all audiences. She loves to read nonfiction, listen to progressive rock, and watches sitcoms on the weekends.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


