Three Main ISO 27001 Principles
Meeba Gracy
Feb 26, 2024

As a cloud-hosted organization, is your data secure? Can you be sure of its safety at all times? Do your data protection controls and measures align with those of the global requirement? The answer isn’t as simple as a yes or no; it’s something much more complex.
That is why implementing (International Organization for Standardization) ISO 27001 is important to protect your company’s information and processes.
In this post, we’ll take a closer look at the 3 main ISO 27001 principles and how they help you confidently meet your compliance and data protection goals!
Let’s dive in…
Overview of ISO 27001 principles
According to Ilia Kolochenko, CEO of ImmuniWeb, the root cause of most data breaches and incidents is typically attributed to inadequate information security protocols that are outdated or outdated.
This is why having an information security system in place for your business is paramount. The ISO 27001 standard allows you to protect your key assets while also making the process of managing and improving the security system easier and more efficient.
To say the least, the ISO 27001 principles offer a set of protocols to aid the whole process, from preparation to maintenance. Now, let’s take a look at the key principles of ISO 27001.
List of ISO 27001 principles
ISO 27001 thrives on these three principles – confidentiality, availability, and integrity of data. Let’s take a look at each one in detail:
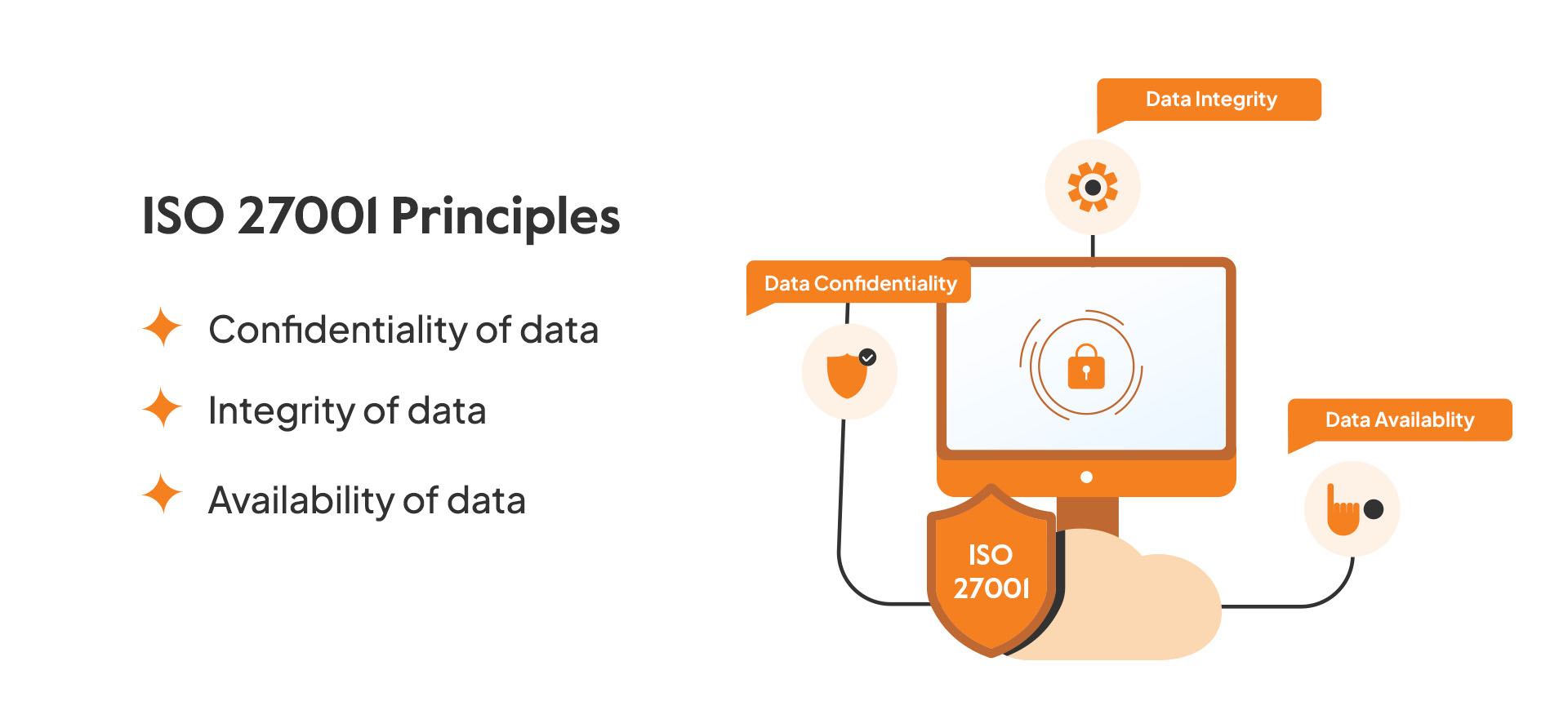
Confidentiality of data
The first principle deals with maintaining the confidentiality of the data. This pertains to the information of your company or any data from customers, prospects, shareholders, or any alliances you have with third parties.
Confidentiality of information mandates that you create a solid ISMS that helps protect all types of data. It also ensures that there are protocols in place to allow only those with administrative access are authorized to access sensitive data.
The principle highlights that the information should be so secure that neither anyone who does not have access nor hackers like keyloggers can ever access it.
Having a confidentiality principle may look like this:
- It ensures the safety and privacy of your data
- Protect your information during transmission
- Use passwords to protect files when sharing online
- Enable encryption method prevents third parties or hackers from accessing it during transmission
Integrity of data
Now, this second principle of ISO mandates that a company must not only protect data from unauthorized access but also ensure that the data remains accurate throughout its lifecycle.
This is referred to as the integrity of data principle and requires you to take steps to verify that the data has not been changed or tampered with in any way.
Of course, if there is a situation where some unauthorized changes are necessary, the backup of the data must be updated accordingly.
The best practice is to automate these changes, meaning if there is a change in one location, it should automatically update across all other locations and backups. This helps avoid confusion and ensures the information assets remain consistent and up-to-date.
Data corruption or alteration can occur due to both intentional and unintentional actions. Information assets face a constant risk of mischievous tampering and sabotage. Whether deliberate or accidental, any unwarranted changes to your data can have dire consequences for the reputation of your company alike: not only could it threaten customer trust in you, but even lead to legal repercussions.
To prevent this from happening, here’s what you need to do according to the second principle:
- Keep your data safe with regular backups
- Protect your business from data loss and corruption
- Construct a data inventory to easily monitor the movement of your data and pinpoint where it was altered
- Store the backup in one place so that you instantly update whenever an authorized change is made to the original file
Availability of data
ISO 27001 Principle 3 – Availability of data – is essential to ensure your systems remain functioning and accessible. One example is an online retail store, where customers can access the website 24/7 to purchase products.
If the website is unavailable when a user attempts to access it, its effectiveness doesn’t matter as they can’t complete their desired interaction.
This highlights why Availability of data is so critical among ISO 27001 basic principles – it pertains to your data being available when required by organizations.
How Sprinto Can Help You?
Sprinto’s automated system guarantees you complete compliance with ISO 27001 principles, from Governance and Asset Management to Cryptography Policies.
Automating time-consuming and repeatable tasks of your compliance journey makes it easier for you to manage your business’s compliance posture.
Our experts are here to explain in detail for those who need clarification on how Sprinto can make the journey faster. Sprinto makes the difference – no more endless hours of tedious paperwork!
FAQs
What are the ISO 27001 standards?
ISO 27001 (ISO/IEC 27001:2022), developed by the International Organization for Standardization, offers a comprehensive structure and clear guidance to create, execute, and maintain an Information Security Management System (ISMS).
What are the 4 P’s in security?
The 4 P’s of security are policies, processes, people, and products. They must be carefully crafted with expectations, rules, and governance.
Why do you need to implement ISO 27001 requirements?
You must implement ISO 27001 requirements because it is an internationally recognized standard developed to help companies protect the confidentiality, integrity, and availability of a system’s information assets.
Meeba Gracy
Meeba, an ISC2-certified cybersecurity specialist, passionately decodes and delivers impactful content on compliance and complex digital security matters. Adept at transforming intricate concepts into accessible insights, she’s committed to enlightening readers. Off the clock, she can be found with her nose in the latest thriller novel or exploring new haunts in the city.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


