Hackers don’t stumble into systems; they’re deliberate, calculating, and patient. They look for weak spots: the misconfigured firewall, the unpatched vulnerability, or the employee who unknowingly clicks on a carefully disguised email. And once they’re in, it’s rarely a smash-and-grab. They move silently, escalating privileges, mapping out networks, and embedding themselves deeper before launching their attack.
To truly protect your systems, it’s not enough to put up defenses and hope they hold. You need to think like an attacker. You need to understand how they operate, what vulnerabilities they exploit, and how an attack unfolds.
Behind the wall, understanding the hack itself.
When most people think of hacking, they picture a lone individual in a dark room, typing furiously as streams of code flash across a monitor. It’s a dramatic visual—a favorite of Hollywood—but it’s a caricature, far removed from reality. The truth is both more mundane and infinitely more unsettling.
At the heart of this lies the zero-day vulnerability. Rare, elusive, and immensely valuable, a zero-day represents a defect in software that even its developers are unaware of.
The strategy of it all
Hacking begins with reconnaissance—a meticulous process where attackers gather information about their target, identifying potential weaknesses. This phase doesn’t involve breaking anything; instead, it relies on Open-Source Intelligence (OSINT), mapping the digital terrain, and analyzing the software architecture.
Once a target is understood, hackers search for entry points. These cracks—vulnerabilities in code—are the lifeblood of modern cyberattacks. Zero-days are the ultimate prize: bugs so deeply embedded that they evade even the most rigorous quality checks.
Zero-day; the crowned jewel of cyber exploitation
Think of software as a high-performance Formula 1 car. Every line of code is like a precision-engineered part—hundreds of thousands of components working in perfect harmony to deliver speed, efficiency, and control. But even in the most meticulously designed machines, there’s room for error. A tiny crack in the chassis, an overlooked flaw in the engine, or a bolt that isn’t tightened to spec can lead to catastrophic failure on the track.

Discovering a zero-day vulnerability is like finding that critical weak point in an F1 car’s design. Identifying requires relentless precision, technical expertise, and often sheer persistence. And once uncovered, the stakes are immense. It requires an extraordinary combination of skill, resources, and patience—attributes that are in short supply but high demand.
Consequently, a thriving underground marketplace has emerged, where zero-days are traded like commodities.
“A vulnerability for two hundred bitcoins please”
The zero-day market operates in layers, each more secretive than the last. At the surface, we have white markets—big bounty programs where ethical hackers sell vulnerabilities to software vendors for a reward. These programs aim to strengthen security by incentivizing transparency.
Below this layer lies the gray market, where governments and private organizations quietly acquire zero-days for espionage or offensive operations. And at the bottom is the black market, where criminal networks buy and sell these exploits for ransomware campaigns, data theft, or worse.
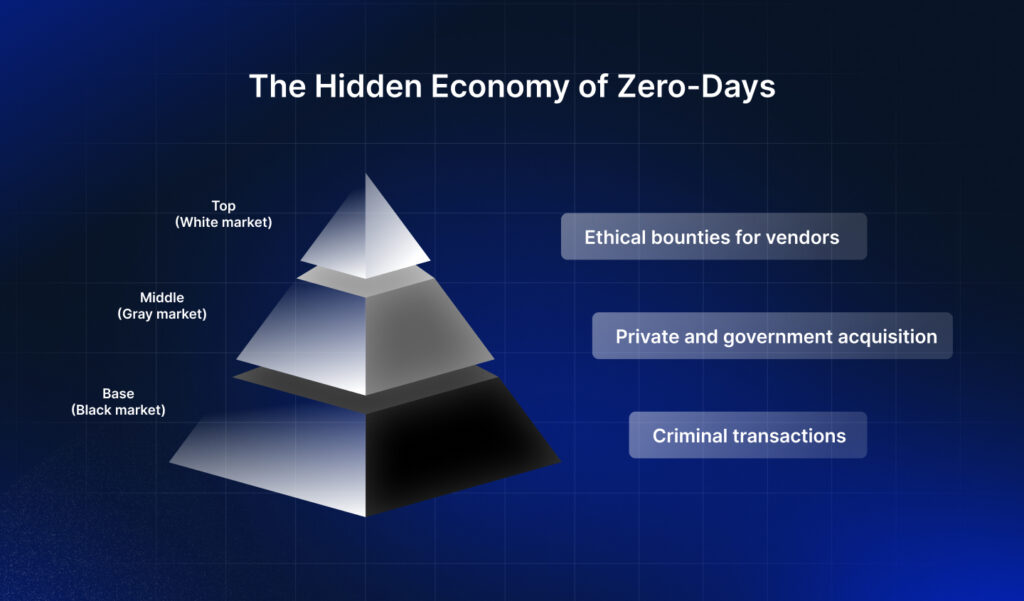
What makes this market unique—and troubling—is its opacity. Transactions are often brokered anonymously, with millions of dollars changing hands for a single exploit. A well-placed zero-day can grant access to anything from personal devices to critical infrastructure. For example, the MOVEit attack in 2023 leveraged a single zero-day to breach over 2,500 organizations, affecting millions of individuals and extorting untold sums.
From flaws to exploit
At the risk of fangirling, the meticulousness with which each exploit is carried out is almost admirable.
First, the vulnerability is either uncovered through painstaking analysis or acquired on the underground market. Once identified, hackers craft a bespoke exploit—an attack designed to reliably bypass defenses and take advantage of the flaw.
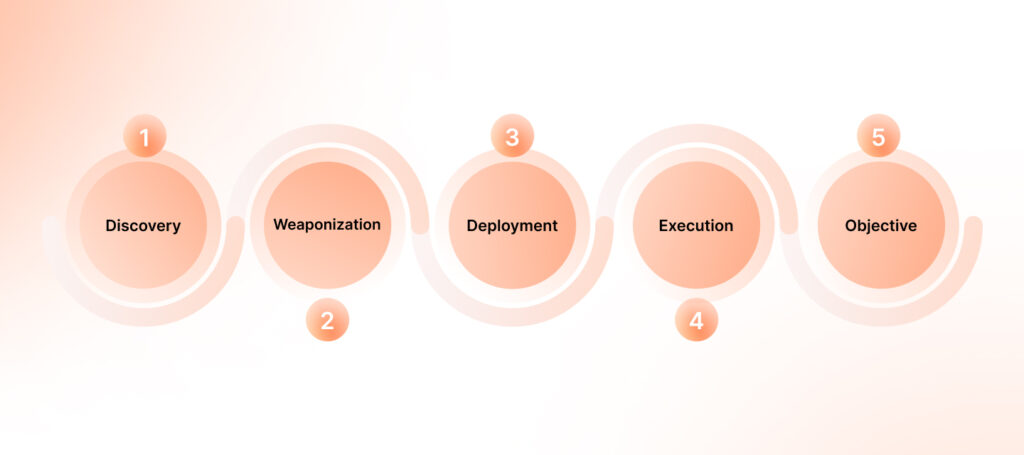
The exploit is then deployed, often through phishing emails, malicious websites, or even zero-interaction methods that require no action from the victim. Once inside, attackers waste no time escalating their privileges, leveraging additional vulnerabilities if necessary to deepen their foothold. From there, their actions align with their objectives: extracting sensitive data, deploying ransomware, or silently monitoring the compromised system.
Preparing for the Inevitable
Even the most synchronized GRC framework and layered defenses can’t guarantee invincibility. But that’s not the point. The goal is resilience—the ability to detect, withstand, and recover from an attack.
For instance, a zero-day attack might bypass your perimeter defenses. Still, internal monitoring could detect unusual lateral movement, and strict access controls might confine the attacker to a limited environment. Meanwhile, your governance structures ensure clear communication during the incident, and compliance measures mitigate reputational and regulatory fallout.
Defense in depth
DiD is about resilience. It’s not about preventing every breach—an impossible task—but about ensuring that when attackers break through, they are met with continued resistance, detection, and containment at every step. This layered philosophy reflects a fundamental truth: security isn’t binary. It’s a spectrum of measures that collectively reduce risk.
Anatomy of layered defense
Defense in Depth is built on the redundancy principle, where multiple layers complement one another to fill gaps left by individual components. These layers can be broadly categorized into preventive, detective, and responsive.
- Preventive layers
Preventive measures are the first line of defense designed to stop attackers before they gain access.- Firewalls and perimeter security: Create a boundary that filters and blocks unwanted traffic. However, modern attackers often bypass these, making deeper layers essential.
- Endpoint protection: Antivirus and endpoint detection tools protect devices against known threats but can struggle with zero-days.
- Access controls: Least privilege and identity verification (e.g., multifactor authentication) prevent unauthorized access and limit the blast radius of any breach.
- Detective Layers
No system is impenetrable. Detective measures ensure you know when an attacker has broken through.- Monitoring and logging: Security Information and Event Management (SIEM) systems aggregate logs and flag anomalies.
- Behavior analytics: Machine learning and pattern recognition identify deviations that signal malicious activity.
- Intrusion detection systems (IDS): These detect unauthorized actions and alert security teams to intervene.
- Responsive Layers
When prevention and detection fail, responsive layers minimize damage.- Incident response plans: Predefined processes guide the organization in isolating, investigating, and recovering from attacks.
- Data backups: Regularly updated backups ensure continuity, even in the face of ransomware or data destruction.
- Forensics and lessons learned: Post-incident reviews improve future defenses, turning failures into growth opportunities.
The problem with synchronization
While these layers provide comprehensive coverage, their effectiveness hinges on synchronization. Misaligned defenses can create blind spots, while redundant layers waste resources and erode trust in the system’s reliability. For example, overlapping tools may trigger false positives, overwhelm security teams with noise, and reduce their ability to respond effectively.
Governance, risk, and compliance should be your P0.
When a zero-day exploit threatens to unravel your defenses, GRC ensures that every decision is deliberate, every action is aligned with business priorities, and every risk is accounted for. The foundation keeps your security strategy focused and adaptable, providing the clarity and coordination to face even the most unpredictable challenges. Without it, even the best tools and processes risk falling apart when you need them most.
Governance
In the fog of a zero-day attack, clarity is everything. Governance creates that clarity by aligning security measures with business priorities, ensuring swift, informed, and deliberate decisions. The strategic compass keeps your defenses focused where they matter most.
What’s worth protecting?
Not every system in your organization is critical. Governance frameworks help prioritize resources toward protecting what attackers are most likely to target—customer data, operational infrastructure, or intellectual property.
A zero-day exploit targeting your central financial systems could grind your business to a halt, while one targeting peripheral devices might be less devastating. Governance ensures you’re not spreading resources thin but concentrating them where they count.
Who’s in charge?
When a zero-day strikes, confusion is your worst enemy. Governance establishes decision-making frameworks and assigns accountability long before an incident occurs. This eliminates ambiguity and allows your organization to act with speed and precision rather than wasting valuable time debating who’s responsible.
How do you communicate?
Every breach has a ripple effect—on your operations, customers, and reputation. Governance frameworks dictate how and when information flows, ensuring internal teams, regulators, and stakeholders are informed in a way that minimizes panic and maintains trust. Transparency, handled well, can be the difference between a crisis and a catastrophe.
Risk
Zero-day vulnerabilities thrive in uncertainty; risk management is your organization’s best tool for navigating that uncertainty. It’s about identifying the likely weak points in your defenses and building contingencies that ensure you’re ready when—not if—a zero-day strike.
Where are the weak spots?
While you can’t predict the next zero-day, risk assessments help pinpoint the areas most likely to be exploited. Legacy systems, unpatched software, or critical applications with high exposure are prime candidates for attack. By understanding where the risks lie, you can focus your defenses on shoring up these vulnerable areas.
What happens when it hits?
Preparing for the unknown requires running simulations. Scenario planning, red-teaming, and tabletop exercises test your organization’s ability to detect, contain, and respond to zero-day exploits. These exercises expose gaps in your defenses and ensure your team knows exactly what to do when facing an attack.
How do you contain the damage?
A zero-day breach doesn’t have to mean widespread chaos. Risk management ensures that attackers can’t move freely through your systems when an exploit happens. Network segmentation, strict access controls, and privilege management create barriers that confine attackers to isolated parts of your environment, minimizing the blast radius.
Compliance
Compliance is the guardrail that ensures your security measures aren’t just theoretical—they’re practiced, enforced, and continually improved.
Mandating the basics
Frameworks like ISO 27001 or NIST don’t stop zero-days outright, but they establish baseline controls—encryption, access management, and regular updates—that reduce the likelihood of unrestricted exploitation. Compliance ensures these measures are implemented consistently across your organization.
Tracking the attack
When a zero-day exploit occurs, tracing its path is crucial for containment and recovery. Compliance frameworks require robust logging and monitoring, creating the audit trails that forensic teams need to understand what happened, where, and how to prevent it in the future.
Demanding accountability
Regular audits and assessments expose weak links in your defenses. By holding systems and teams to high standards, compliance frameworks push organizations toward constant improvement, ensuring your defenses are functional and reliable under pressure.

The GRC-DiD Symbiosis
Zero-day vulnerabilities are a litmus test for your organization’s ability to adapt, recover, and grow stronger in the face of adversity. Defense in Depth provides the technical foundation, but GRC turns that foundation into a living, breathing defense strategy. It harmonizes people, processes, and technology into a unified approach that not only mitigates the impact of zero-days but also ensures the organization can thrive in an unpredictable world.
When governance aligns your strategy, risk management drives foresight, and compliance enforces discipline, your defenses aren’t just reactive but resilient. That’s the difference between surviving an attack and emerging stronger from it.
Little known reason for zero-day vulnerability
When zero-day vulnerabilities strike, the spotlight often falls on exploited software or unpatched systems. But lurking in the shadows of many organizations is a less visible culprit—Shadow IT.
Shadow IT often emerges from a gap between the tools employees need and the solutions their organization provides. The rise of cloud-based tools and the demand for instant solutions have only fueled this behavior, allowing teams to bypass IT governance in favor of convenience and functionality.
The real solution lies in a deliberate, thoughtful approach to technology adoption. Tech leaders must assess which functions require depth, where priorities lie, and which processes demand technological intervention.
By choosing tools that not only meet specific needs but also integrate seamlessly, organizations can eliminate the root cause of shadow IT. This integration ensures that applications communicate effectively, enabling transparency, data sharing, and collaboration while reinforcing governance and control. A well-balanced, cohesive tech ecosystem doesn’t just improve productivity—it closes the gaps that shadow IT thrives on.
Build resilience, not perfection
Zero-days are inevitable. They expose not only the flaws in your software but the weaknesses in your strategy. Surviving them isn’t about building an impenetrable fortress but creating an adaptive, resilient ecosystem. Governance aligns your strategy, risk management prepares you for the unknown, and compliance ensures discipline in execution. Together, they form the foundation of a defense strategy that doesn’t just mitigate attacks—it ensures your organization can recover, rebuild, and emerge stronger every time.
Heer Chheda
Heer is a content marketer at Sprinto. With a degree in Media, she has a knack for crafting words that drive results. When she’s not breaking down complex cyber topics, you can find her swimming or relaxing by cooking a meal. A fan of geopolitics, she’s always ready for a debate.
Explore more
research & insights curated to help you earn a seat at the table.




















