The Digital Operational Resilience Act (DORA) is an EU Regulation (2022/2554) aimed to improve digital security and mitigate financial entities’ cyber risks. It applies to all financial services businesses and third parties supporting ICT (information and communication technology).
DORA is legally binding in the EU region and has nine chapters with 64 articles! It focuses on ICT risk management, incident tracking and reporting, penetration testing, policies and procedures, and the overall uniformity of security measures.
This article breaks down the DORA regulation’s mandatory and non-mandatory requirements and discusses how financial businesses must approach this new regulatory framework.
| TL;DR DORA is an EU regulation aimed at improving digital security and mitigating cyber risks for financial entities and their ICT providers. DORA has four mandatory requirements (ICT risk management, incidence response and reporting, digital operational resilience testing, and TPRM) and one non-mandatory requirement (Information sharing). Financial entities must comply with DORA by January 17, 2025, or face significant penalties, including fines up to 2% of annual global turnover. |
Are you in scope for DORA?
The financial entities under the scope of DORA (Digital Operational Resilience Act) as identified by the European Commission include:
- Credit institutions (banks)
- Investment firms
- Payment institutions
- Account information service providers
- Electronic money institutions (E-money institutions)
- Insurance and reinsurance undertakings
- Insurance intermediaries, reinsurance intermediaries, and ancillary insurance intermediaries
- UCITS management companies
- Managers of Alternative Investment Funds (AIFMs)
- Central counterparties
- Central securities depositories
- Trading venues
- Trade repositories
- Crypto-asset service providers and issuers of asset-referenced tokens
- ICT third-party service providers designated as critical
- Crowdfunding service providers
- Data reporting service providers
- Institutions for Occupational Retirement Provision
- Credit rating agencies
- Administrators of critical benchmarks
- Securitization repositories

What’s the deadline to comply with DORA, and the consequences of non-compliance?
The deadline for complying with the DORA regulation is January 17, 2025. Time is running out, and the regulation enforces sky-rocketing penalties to ensure high compliance standards across financial entities and their ICT providers.
Here’s what the penalties look like:
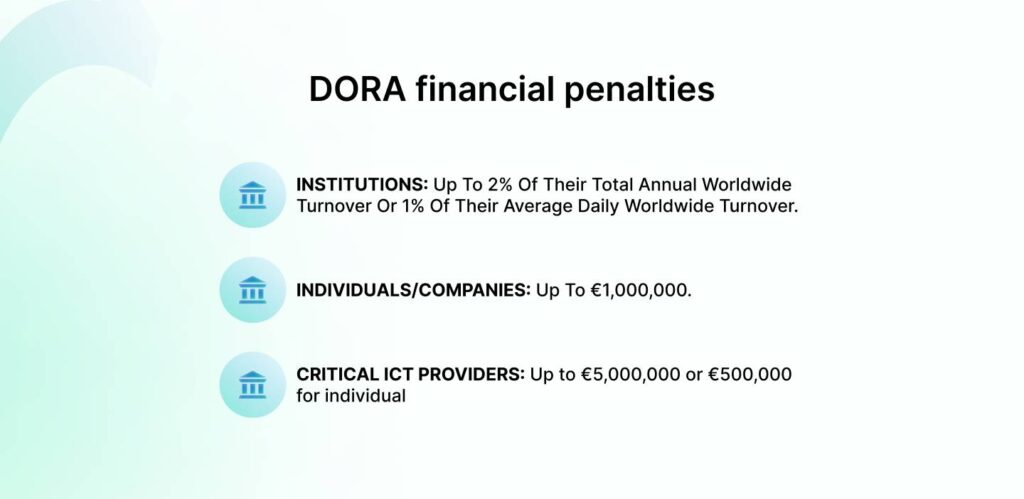
- Institutions can be fined up to 2% of their total annual worldwide turnover or 1% of their average daily worldwide turnover.
- Individuals and companies may face fines of up to €1,000,000.
However, ICT service providers termed as ‘critical’ have even stricter fines:
- Third-party ICT service providers could be fined up to €5,000,000 for non-compliance.
- Individuals associated with these providers could face penalties of up to €500,000.
Mandatory and non-mandatory requirements under DORA
The guidelines under DORA mention four mandatory components or requirements:
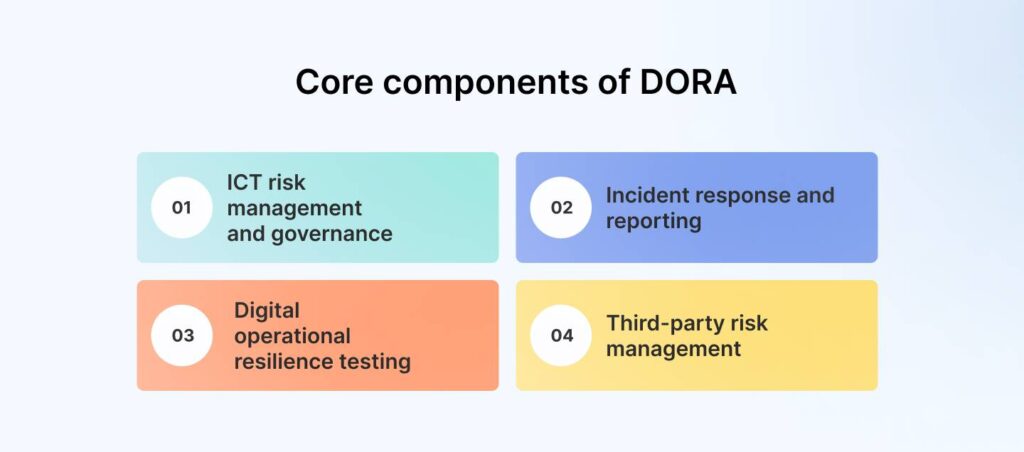
1. ICT risk management and governance
DORA mandates that all financial entities have a strong ICT (information and communications technology) risk management and governance framework. But at a security controls level, what does this mean for you?
- Develop ICT security policies addressing encryption, network security, and asset management.
- Perform regular ICT risk assessments to identify vulnerabilities, threats, and potential business impacts.
- Assign clear roles and responsibilities for ICT risk management to ensure accountability.
- Implement a governance structure that includes senior management oversight and periodic reviews of ICT risks.
For an even sturdier framework, consider using automated tools to track and document your risks and mitigation processes. This also makes room for a centralized dashboard, enabling real-time monitoring of risks and resilience metrics.
Comprehensive Risk Monitoring & Mitigation
2. Incident response and reporting
Risk management and governance are incomplete without an incidence management strategy to detect, respond to, and report ICT-related events and incidents. There need to be clear procedures for incident detection, escalation, containment, and recovery.
Furthermore, there are guidelines for reporting incidents to competent authorities within the specified timelines. This must be done parallelly while maintaining detailed logs and evidence supporting incidents for regulatory reporting and investigations.
Some handy tools here are SIEM (Security Information and Event Management) solutions that implement automated incident reporting for timely and accurate evidence submissions.
3. Digital operational resilience testing
If you fall under DORA’s scope, you need to emphasize the importance of regular testing to validate that your systems are resilient against operational and cyber threats. Implement penetration testing, vulnerability assessments, and red team exercises like real-world simulation attacks.
To ensure data integrity, check if your backup and recovery systems are working properly. Breach and attack simulation tools (BAS) like Attack IQ, XM Cyber, and Picus Security can automate such processes.
4. Third-party risk management
DORA recognizes the ‘critical’ role of ICT third-party providers and mandates financial entities to manage associated risks proactively. These risks must be assessed and documented according to given technical standards and included in contractual agreements (E.g., timely patching and reporting).
Note
The requirement of ‘information sharing’ is not a mandatory request by the DORA, but it is highly encouraged.
Non-mandatory: Information sharing
Information sharing among financial institutions is encouraged as a key practice to bolster the overall cybersecurity posture of the financial sector. How do you participate in this?
- Join platforms like ISACs (Information Sharing and Analysis Centers) or industry-specific cybersecurity networks to exchange threat intelligence and best practices.
- Share information about newly identified threats, vulnerabilities, and mitigation strategies with peers and regulators.
- Use automated tools such as Threat Intelligence Platforms (TIPs) for structured and secure exchanges.
Implementing DORA as per Regulatory Technical Standards (RTS)
The first batch of RTS (Regulatory Technical Standards) was finalized under DORA in January 2024, and along with the second batch, the final draft was released in July 2024.
From July 2024 to January 2025, financial entities in the EU had six months to implement these standards to ensure compliance with regulatory requirements. Combining the two batches of RTS, here’s what the implementation of DORA looks like in a glimpse.
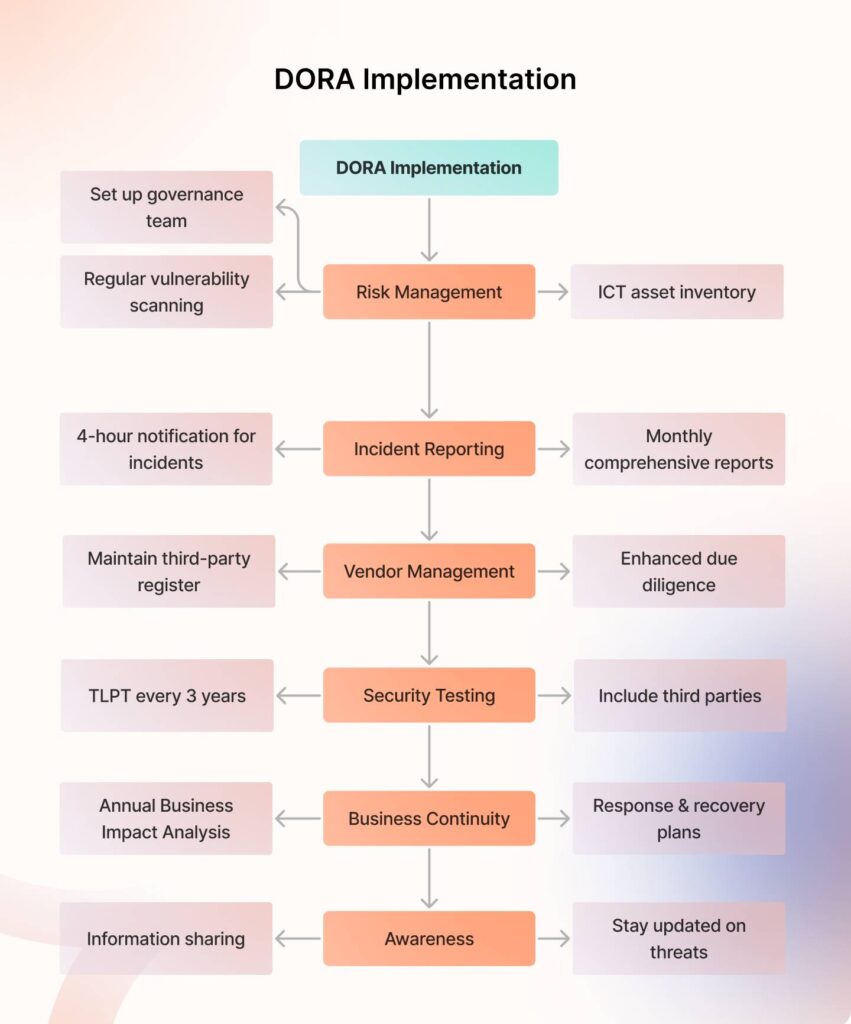
1. Prioritize risk management with clear policies
Per DORA’s technical standards, your risk management framework should be governance first. This means that everyone must know who is in charge of ICT risks. Assign roles and set up a team (or even a committee) to keep everything in check.
Stay ahead of risks by using tools to scan for vulnerabilities and conducting penetration testing every six months. Keep an up-to-date inventory of every ICT asset, right down to when its support ends. Segregate critical systems, enforce firewall rules, and use tools like SIEM for real-time monitoring.
2. Set up a strong incident reporting system
Begin by classifying all incidents using clear rules set forth in Article 18. For example: how many clients were affected? How critical was the service? What was the duration of the incident? What was the geographical impact?
Notify regulators within 4 hours of a significant incident and submit a comprehensive report within 1 month. Use templates for consistent incident documentation and maintain detailed, tamper-proof logs.
3. Track your vendors constantly
Third-party providers are an essential part of your ecosystem. As per requirements, keep a third-party register to document critical provider details, including services, contract duration, and risk levels. Update this register regularly or after significant changes.
To further strengthen your third-party management:
- Differentiate providers by criticality and perform enhanced due diligence for high-risk providers.
- Ensure providers submit incident response plans and meet SLAs for timely reporting and resolution.
Note
EU regulators (ESAs) will directly oversee critical ICT third-party providers. The European Commission is finalizing the criteria for identifying these “critical” providers. Once designated, a lead overseer will enforce DORA compliance and can block providers from contracting with non-compliant financial firms or ICT providers.
4. Conduct advanced Threat-Led Penetration Testing (TLPT)
Except for microenterprises and other entities mentioned in Article 16(1), all financial entities must conduct Threat-Led Penetration Testing (TLPT) every three years.
You must also include your third parties while conducting the TLPT and ensure that they comply with DORA guidelines. DORA lays out specific guidelines depending on whether you’re going forward with external or internal testers for TLPT.
For external testers:
- Testers must be reputable and demonstrate expertise in threat intelligence, penetration testing, and red team operations.
- They must be certified by a recognized body or adhere to ethical frameworks and formal codes of conduct.
- They must provide independent assurance or audit reports covering risk management, protection of confidential information, and business risk mitigation.
- Contracts must ensure sound handling of TLPT data, including generation, storage, reporting, and destruction, to avoid risks to the financial entity.
For internal testers:
- The use of internal testers must be approved by the relevant competent authority.
- Authorities must verify sufficient resources and avoid conflicts of interest during test design and execution.
- Threat intelligence must be sourced externally.
5. Focus on ICT business continuity (response and recovery)
DORA focuses on the fact that financial entities must have enough policies and processes maintain operational continuity even if there’s an ICT-related incident. This calls for a comprehensive business continuity policy, response and recovery guidelines, and a crisis management function.
As per the guidelines mentioned in Article 11, you also need to conduct a Business Impact Analysis (BIA) at least once per year.
Furthermore, detailed records of all activities during disruption events should be kept. Share test results with relevant authorities and, if asked, estimate the costs and losses caused by major ICT-related incidents.
6. Raise awareness around cyber threats
A key reason DORA encourages information sharing is to raise awareness and limit the spread of cyber threats in the financial sector. However, to ensure reliability, knowledge should be shared only within trusted networks of financial entities.
To participate, must have the team and tools needed to identify vulnerabilities and cyber threats. Stay updated on new technologies and evaluate how these affect your cybersecurity and operational resilience.
Furthermore, remember that sharing must follow strict protocols that:
- Protect sensitive business and personal data (complying with GDPR)
- Adhere to business confidentiality and competition policies
- Define clear rules of conduct
How does Sprinto help financial entities comply with DORA?
Sprinto collaborates with implementation partners who assess the financial entity’s infrastructure, processes, and policies to “right-size” DORA requirements. The implementation partner designs specific controls based on DORA criteria, aligning them with the organization’s unique context.
The platform shall translate the recommended DORA-aligned controls into actionable items and automate control checks to monitor compliance in real time while reducing manual effort.
If you already comply with other cybersecurity standards, Sprinto’s CCF (common control framework) eliminates redundancy by identifying overlaps between DORA controls and existing frameworks.
With Sprinto, financial entities can confidently implement and maintain DORA compliance without being overwhelmed by its complexity. Ensuring digital operational resilience while meeting regulatory expectations: See Sprinto in action.
Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Explore more
research & insights curated to help you earn a seat at the table.


















