
Quick question: If we secure an asset with a password that only the intended user should know, add security questions that only they can answer, confirm their identity through something only they could possess—like their smartphone—and even layer on security tokens or smart cards, we should be airtight, right? Wrong!
More than 78% of companies globally have used MFA to protect their critical systems and data. Yet, 28% of them are breached in some way.
For instance, the researchers only took one hour to bypass Microsoft Azure’s MFA systems. Okta, one of the largest identity authentication tech providers, had its MFA system compromised recently in 2022.
The problem? Low redundancy, flawed security design, and a misplaced belief that MFA alone guarantees security.
There is no such thing as a silver bullet in cybersecurity, not even MFA. And with the growing complexity of threats that involve social engineering, prompt bombing, alert fatigue, phishing as a service rental kit, and sophisticated AiTM technology, MFA that exists in a vacuum of solid security principles is no longer enough.
This article explores high-profile case studies where MFA vulnerabilities were exploited and bypassed, uncovering critical lessons to bolster security practices and ensure MFA serves its purpose: keeping hackers out of your systems.
TL;DR
| MFA requires additional security layers to be effective, as attackers can bypass it using tactics like unlimited login attempts and exploiting IoT connections. |
| Attackers employ sophisticated techniques such as MFA fatigue and AiTM attacks, which leverage human error and system vulnerabilities to gain unauthorized access. |
| Strengthening MFA includes adopting zero-trust principles, enabling push-to-approve features, and comprehensive coverage to mitigate risks and enhance system security. |
MFA can not protect in a vacuum
Threat actors’ most common routes are to compromise any possible account in a business, evade detection, gain additional privileges, and escalate the attack.
For example, if you have implemented MFA for a particular service, but the service has no cap on sign-in attempts. A threat actor willing to try all one million combinations of the standard 6-digit authentication code, rainbow tables, and capable hardware can gain access to the account.
From there, the threat actor can interact with other devices on the network, infect them, explore files, and escalate their privileges, leading to a full-blown breach.
Thus, it becomes essential to supplement MFA with additional measures like limited login attempts, a robust system to notify account owners in case of an attempt, timeframe-based access denial, and in-network protections that prevent escalation of privileges from IoT networks.
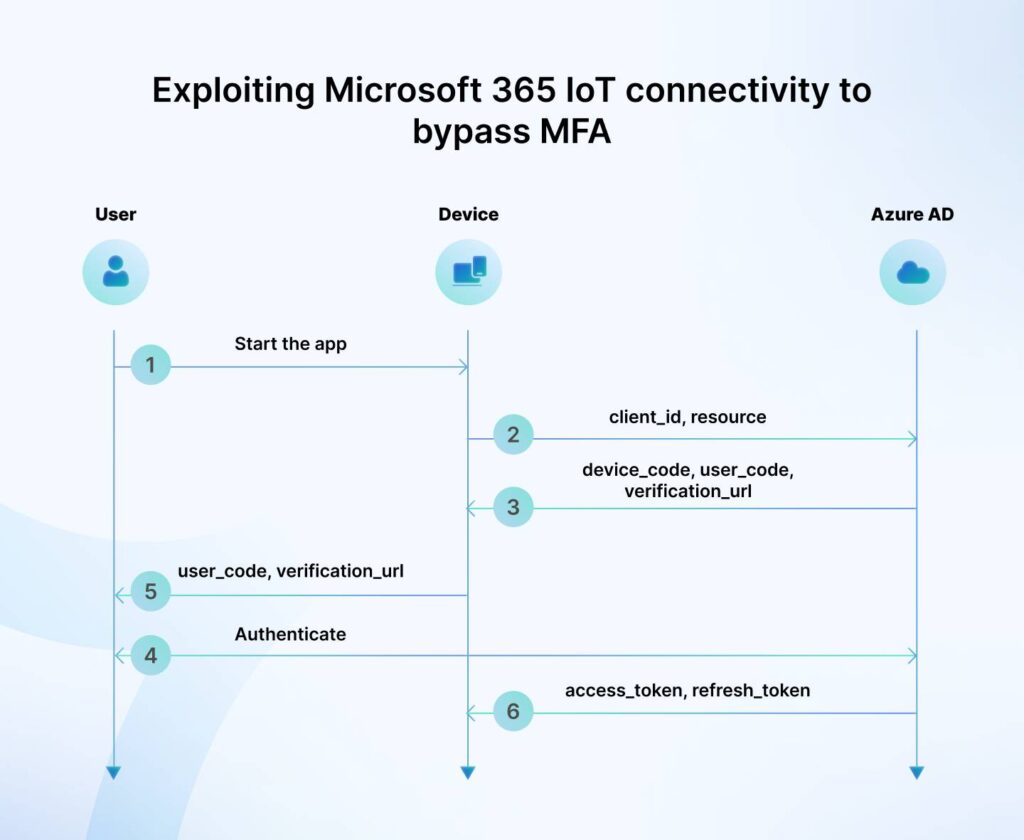
Case in point: Exploiting Microsoft 365 IoT connectivity to bypass MFA
The authentication system for Microsoft 365 allows users to log in to input-constrained devices like SmartTV, Printers, and other IoT devices using a sign-in code. For example, to connect a Smart TV, it will display a code that you can enter into the Office365 authentication window to connect the device.
However, the same can be used by threat actors to bypass MFA.
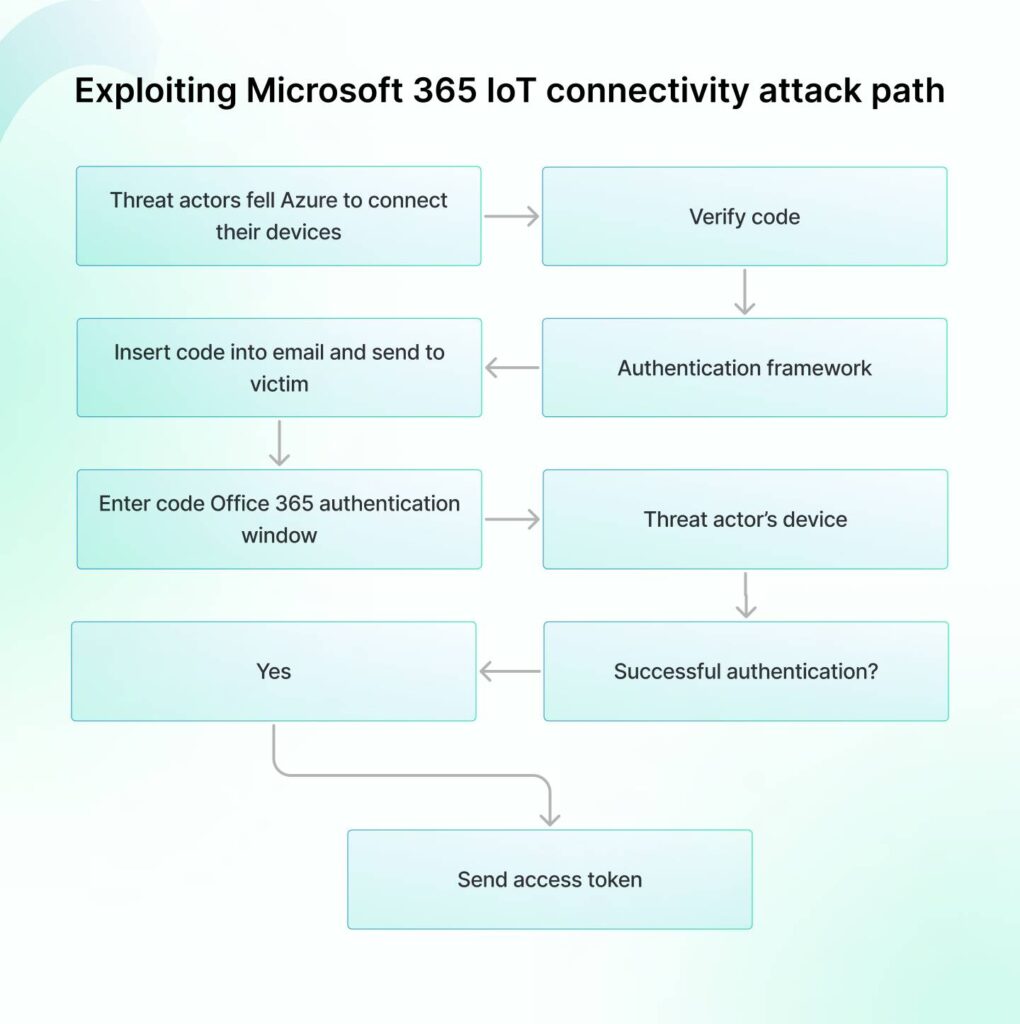
Attack pathway:
- Threat actors tell Azure to connect their devices.
- The authentication framework asks them to verify a specific code.
- The attacker inserts this code into an email and sends it to a victim.
- The victim checks the email and enters the code on their Office365 authentication window.
- Once the threat actor’s device gets authenticated, an access_token is sent back to the threat actor’s device.
- The threat actor gets the token and can now easily access the account or take ownership.
- In this entire scenario, MFA doesn’t even get a chance to work. The user successfully bypasses MFA.
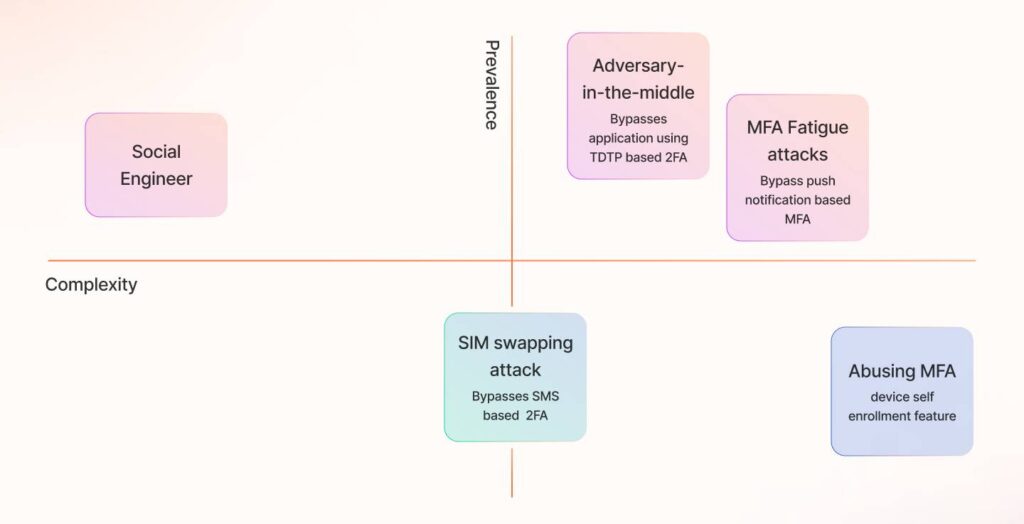
How does MFA get bypassed?
Human oversight remains a critical factor in MFA security. Attack pathways that exploit or manipulate human behavior can bypass MFA defenses. While bypassing MFA is challenging, it is far from impossible.
Threat actors have adapted familiar tactics, such as social engineering, to develop more sophisticated techniques like adversary-in-the-middle (AiTM) attacks, SIM swapping, and other methods that target MFA’s weakest link—the human element.
Each of these attacks differs in complexity, success rate, and prevalence. Looking at the left of the quadrant, it is clear that social engineering is the attack that’s easier to execute for an attacker but is low in prevalence. While AiTM attacks are the most dominant method to bypass MFA, they are more complex than usual, and so on.
Let’s explore these most commonly used attack pathways to bypass MFA via real-life case studies:
1) State-sponsored attack abuses MFA device self-enrollment vulnerability to bypass it
In 2022, CISA and FBI declassified an attack on an NGO that exploited the MFA self-device enrollment feature.
Even though it’s uncommon, attackers usually abuse MFA self-enrollment vulnerabilities. They typically target orphaned accounts within an organization or accounts of new joiners who have not yet enrolled in MFA. Attackers exploit the initial setup phase, registering their devices to gain unauthorized access to these unprotected accounts despite MFA protocols.
The attack usually starts with the threat actor gaining account credentials via phishing, brute-force, or other methods. Once inside, the goal is to register their own device for MFA so they can eventually stay in the network to exploit other vulnerabilities until they dominate the network entirely.
For this NGO, the threat actors attack path was this:
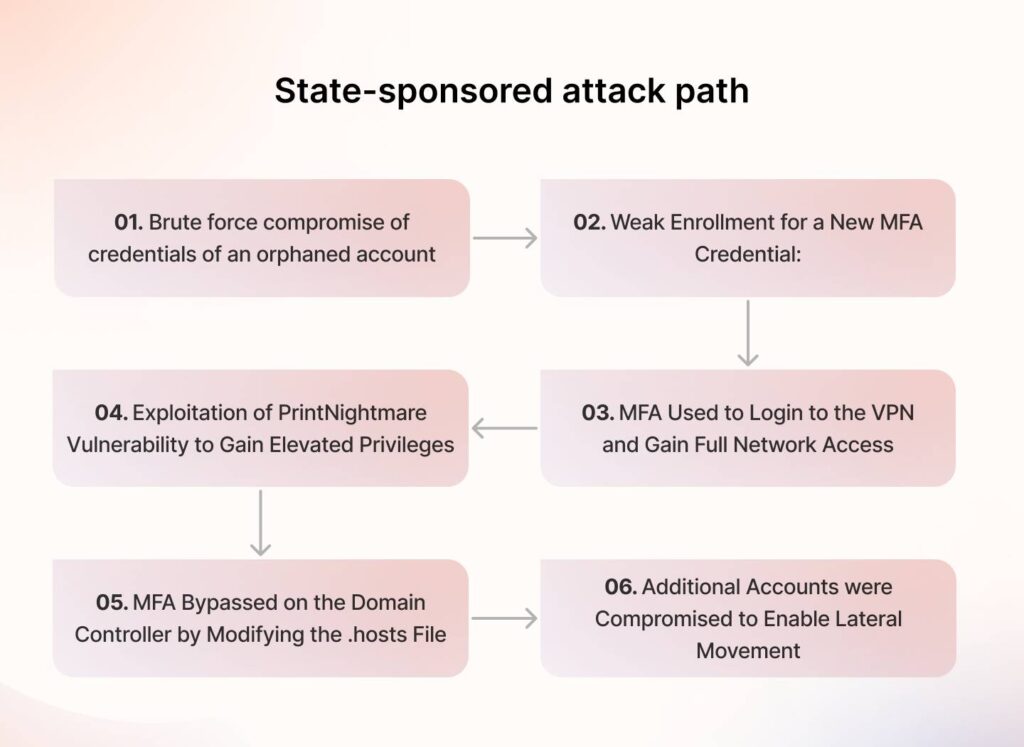
1) Brute force compromise of credentials of an orphaned account:
The attacker used brute force to guess and eventually compromised a weak password associated with the account of a user who no longer worked for the company.
2) Weak Enrollment for a New MFA Credential:
The attacker enrolls for Multi-Factor Authentication (MFA) with their device using the compromised account. The enrollment process only required the initially stolen password, lacking additional verification steps to authenticate the user’s identity.
3) MFA Used to Login to the VPN and Gain Full Network Access:
Once the threat actors had MFA set up, they accessed the VPN to bypass trust-zone-based security measures and gained unrestricted levels of access to sensitive areas of the network.
4) Exploitation of PrintNightmare Vulnerability to Gain Elevated Privileges:
With higher levels of access, the attacker exploits the PrintNightmare vulnerability, a critical flaw in Windows Print Spooler, to escalate their privileges within the network. This allows them to execute arbitrary code on the victim’s machine with system-level permissions.
5) MFA Bypassed on the Domain Controller by Modifying the .hosts File:
To further maintain their access, the attacker bypassed MFA on the Domain Controller (DC by modifying the .hosts file, which redirects requests for the MFA server to the localhost (i.e., the machine controlled by the attacker,) which effectively neutralized MFA checks.
They achieve this by modifying the .hosts file, redirecting requests for the MFA server to the local host (i.e., the attacker’s controlled machine), and effectively neutralizing MFA checks.
6) Additional Accounts were Compromised to Enable Lateral Movement:
Having gained high-level privileges, the attacker compromises additional accounts from the Domain Controller. This facilitates lateral movement across the network, allowing the attacker to access other systems and exfiltrate or manipulate data at will.
2) Prompt Bombing, MFA fatigue attack that compromised Uber
Prompt bombing, or MFA fatigue, exploits a critical weakness in MFA systems — relying on socially engineered scenarios where users are distracted or frustrated, hastily approving an MFA prompt just to resume their daily tasks.
Case in point: Breach at Uber by Lapsus$
On a late evening, Uber’s security systems flagged unusual activity – a relentless storm of MFA requests targeting an employee in their system. Lapsus$, an infamous group involved in multiple ransomware attacks, got hold of an employee’s account credentials, presumably by using a chain of phishing and orchestrated social engineering attacks.
Subsequently, they bombarded the employees with MFA prompts, hoping to exploit human vulnerability—the desire for peace and the cessation of incessant notifications.
To emphasize the point, the threat actor posed as a member of Uber’s IT team and contacted the victim directly, convincing them to approve MFA requests.
This act of seeming desperation was a calculated step to gain unauthorized access.
Once inside the system, the attackers navigated Uber’s network until they stumbled upon a Microsoft PowerShell script containing administrative credentials. This discovery allowed them deep access, including the ability to view source code and details from Uber’s bug bounty program, revealing vulnerabilities that had not yet been addressed.
Here is the attack path they followed:
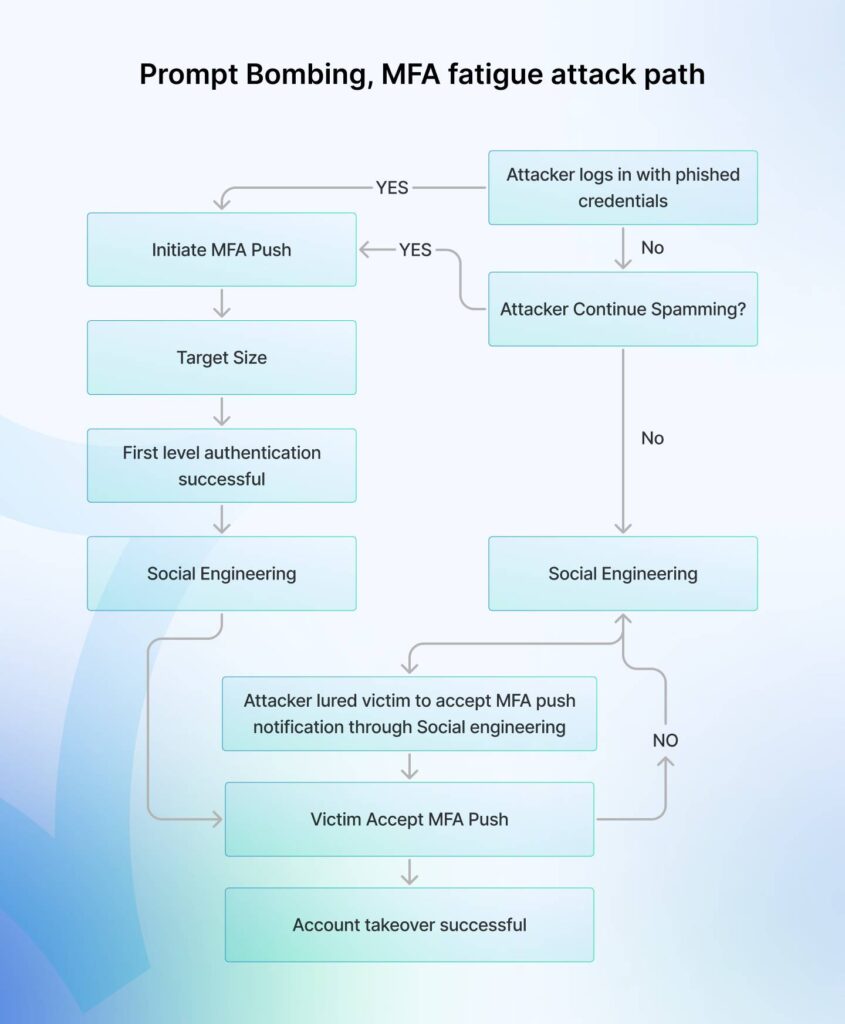
Step 1: Attacker gained credential Access
The hacker obtained the employee’s Active Directory (AD) password through phishing, brute-force attacks, or exploiting any other vulnerability.
Step 2: MFA fatigue initiation
The employee was flooded with Multi-Factor Authentication (MFA) notifications, leading to MFA fatigue or prompt bombing. This created a scenario in which the employee might approve a malicious login attempt just for the sake of peace.
Step 3: Social engineering
To accelerate authentication, the threat actor posed as Uber IT support contacted the employee and convinced them to approve one of the MFA requests under the pretense of resolving a security issue.
Step 4: Network access and lateral movements
Once the MFA was approved, the hacker quickly traversed the network laterally and logged in to the company’s VPN, thereby gaining full network access, which may include access to sensitive areas restricted to most users.
Step 5: Privilege Escalation
In this case, the malicious actor discovered and leveraged a Microsoft PowerShell script within the network that contains admin credentials for Privileged Access Management (PAM), elevating their access to administrative levels.
3) AiTM attacks
To bypass MFA, An Adversary-in-the-Middle (AiTM) attack occurs when a threat actor positions themselves as a passive yet observing layer of the network between the victim and the targeted service. This setup allows the attacker to intercept, relay, and manipulate the communication, including sensitive information such as credentials and session tokens.
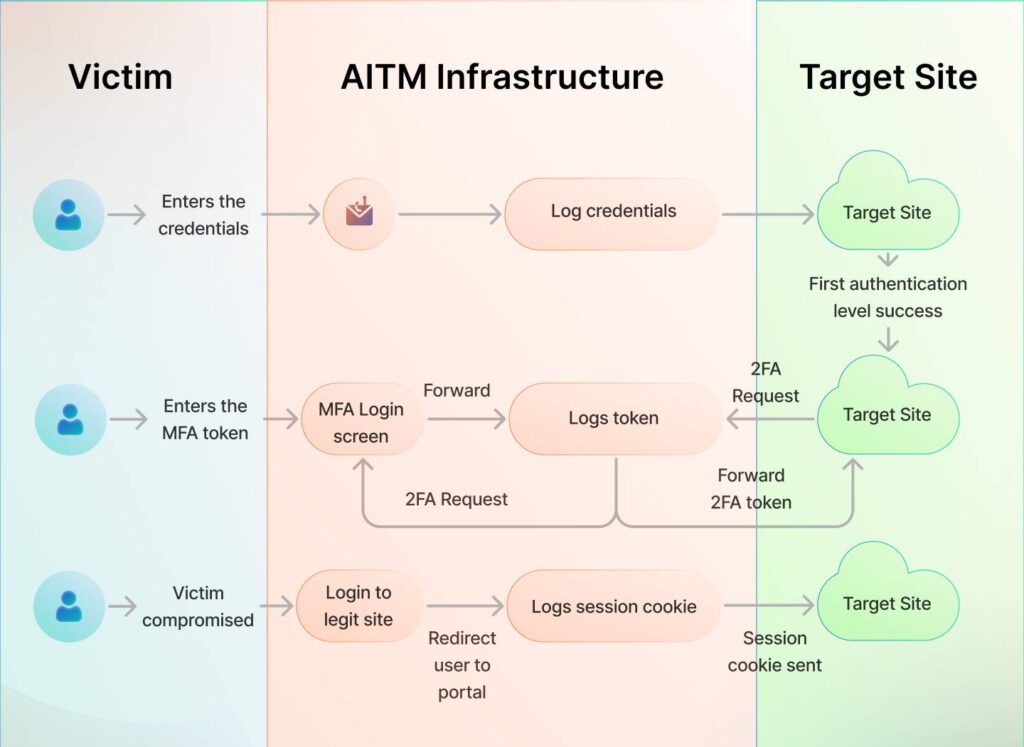
Attack Path to AiTM Attack to bypass MFA:
1) Phishing
A victim receives a malicious link via email or sms, from another trusted service they use daily.
2) Harvesting credentials
The victim is taken to a login page of a respected service, such as Microsoft, but via the actor’s network in between. This way, as soon as they enter their credentials, the attacker has access to them as it is relayed back to them through their infrastructure in the middle.
3) Credential relaying
The captured credentials are related to the threat actor, and they escalate the attack further.
4) Intercepting MFA
If the target site requires MFA, the authentication request is relayed to the victim. The victim enters the MFA code, which the attacker intercepts and forwards to the target site. The threat actor also captures the session cookie so that the victim can log in as and when needed.
5) Unauthorized access with session cookies
Once the threat actor gets access to session cookies, they can use the stolen session cookie to access the victim’s account on the target site without needing the username and password, bypassing the login process entirely.
How to strengthen your MFA
The problem with MFA is that attackers have found a way to engineer circumstances to intercept MFA keys the same way they used to intercept passwords.
To add to the problem, humans remain the weakest link, and the most prevalent MFA attacks, like MFA fatigue attacks, are highly dependent on human judgment.
However, some steps can be taken to strengthen MFA. Learning from these instances, here are the best practices to ensure that MFA is not bypassed, and even if it is, the attacker can not make great use of it.
“We have seen the success of attacks against MFA-protected accounts increasing over the past couple of years.”
The National Cybersecurity Centre.
The problem with MFA is that attackers have found a way to engineer circumstances to intercept MFA keys the same way they used to intercept passwords.
To add to the problem, humans remain the weakest link, and the most prevalent MFA attacks, like MFA fatigue attacks, are highly dependent on human judgment.
However, some steps can be taken to strengthen MFA. Learning from these instances, here are the best practices to ensure that MFA is not bypassed, and even if it is, the attacker can not make great use of it.
Zero trust principles
Usually, organizations balance convenience and security and thus set up trust zones within a VPN. The devices on this network get elevated privilege access to ease business and collaboration. However, this principle of establishing a trust zone is also the most exploited one.
Zero trust principles work on a simple rule – never trust, always verify. This prevents compromised accounts from gaining further privileges within the system. To implement Zero Trust, you can start with:
- Contextual access control policies: Develop and enforce dynamic access policies that consider the context of access requests, such as location, device security status, and access time.
- Micro-segmentation: Utilize micro-segmentation to limit lateral movement within the network, even if an attacker bypasses MFA.
- Behavioral Analytics: Use behavioral analytics to detect anomalies in user behavior that could indicate a compromised account, even after MFA verification.
Enable push-to-approve
As we saw in the case of the attack on NGOs, code-based MFAs are vulnerable. Push-based MFAs with biometric or geofenced verification can add another layer of security to ensure that MFA works as intended.
Ensure MFA is enabled on all access points
Requiring Multi-Factor Authentication (MFA) not just for initial login but also for sensitive actions within a system significantly enhances security by adding an extra layer of verification.
Lastly, it is crucial to adjust default configurations to enhance security, such as implementing strict account lockout policies and requiring more robust verification processes during MFA enrollment. Additionally, identity governance is focused on regularly auditing and eliminating orphaned accounts, thus minimizing unnecessary access risks.
Resilient practices are often rooted in simplicity and discipline
As we scrutinize the role and robustness of Multi-Factor Authentication (MFA) in our security arsenals, it’s clear that MFA isn’t a silver bullet but a fundamental layer in a multi-dimensional defense strategy. By adhering to disciplined security practices and maintaining simple, user-friendly methods, organizations can enhance their resilience against increasingly sophisticated cyber threats. Ultimately, the key to enduring security lies in the continuous evaluation and adaptation of our protective measures, ensuring they meet current challenges and are poised to counter future vulnerabilities.
“Most of the time, security is about discipline and processes around crucial activities that you do continuously. These include common things such as how you onboard or offboard employees or how you just push code to production”
Girish Redekar
FAQ
What are the common types of MFA?
- SMS and Email Codes: A code sent to your phone or email.
- Authentication Apps: Generate time-limited codes on your device.
- Hardware Tokens: Devices that generate a code at the push of a button.
- Biometric Scanners: Use your fingerprint, facial recognition, or retina scans.
- Push Notifications: Authentication requests you approve from a registered device.
Is MFA foolproof?
While MFA significantly increases account security, no security system is entirely foolproof. It can still be vulnerable to sophisticated phishing attacks, man-in-the-middle attacks, or if a device used for MFA is stolen and unlocked.
Can MFA be bypassed?
There are methods to bypass MFA, such as SIM swapping or exploiting vulnerabilities in the recovery processes. To mitigate these risks, using strong, unique passwords, secure recovery processes, and the most secure forms of MFA are crucial.
Virgil
Virgil is a marketer at Sprinto who combines his media savvy with his cybersecurity expertise to craft content that truly resonates. Known for simplifying complex cybersecurity and GRC topics, he brings technical depth and a storyteller’s touch to his work. When he’s not busy writing, he’s likely exploring the latest in cybersecurity trends, debating geopolitics, or unwinding with a good cup of coffee.
Explore more
research & insights curated to help you earn a seat at the table.




















