Quantum computing & Post-quantum Cryptography: GRC’s Y2K Moment?

Imagine a world where your personal messages, health records, banking transactions, and confidential information are exposed in seconds because someone could break the encryption methods you trust. A decade ago, this would have seemed like a sci-fi plot, but today, it has the potential to become a very real possibility. As we look toward 2025, trends are pointing toward a quantum leap in cybersecurity—nations and tech giants are closely watching the horizon as quantum threats loom.
The ones on the calmer side of this seismic shift are investing heavily in post-quantum cryptography (PQC) to prepare for the quantum era. PQC is the only way to fight this next big challenge because, in a world already dealing with an all-time high number of breaches, it is the only strong line of defense.
Read this blog to understand the quantum threat and how you, as a GRC leader can prepare for a quantum-secure future.
TL;DR
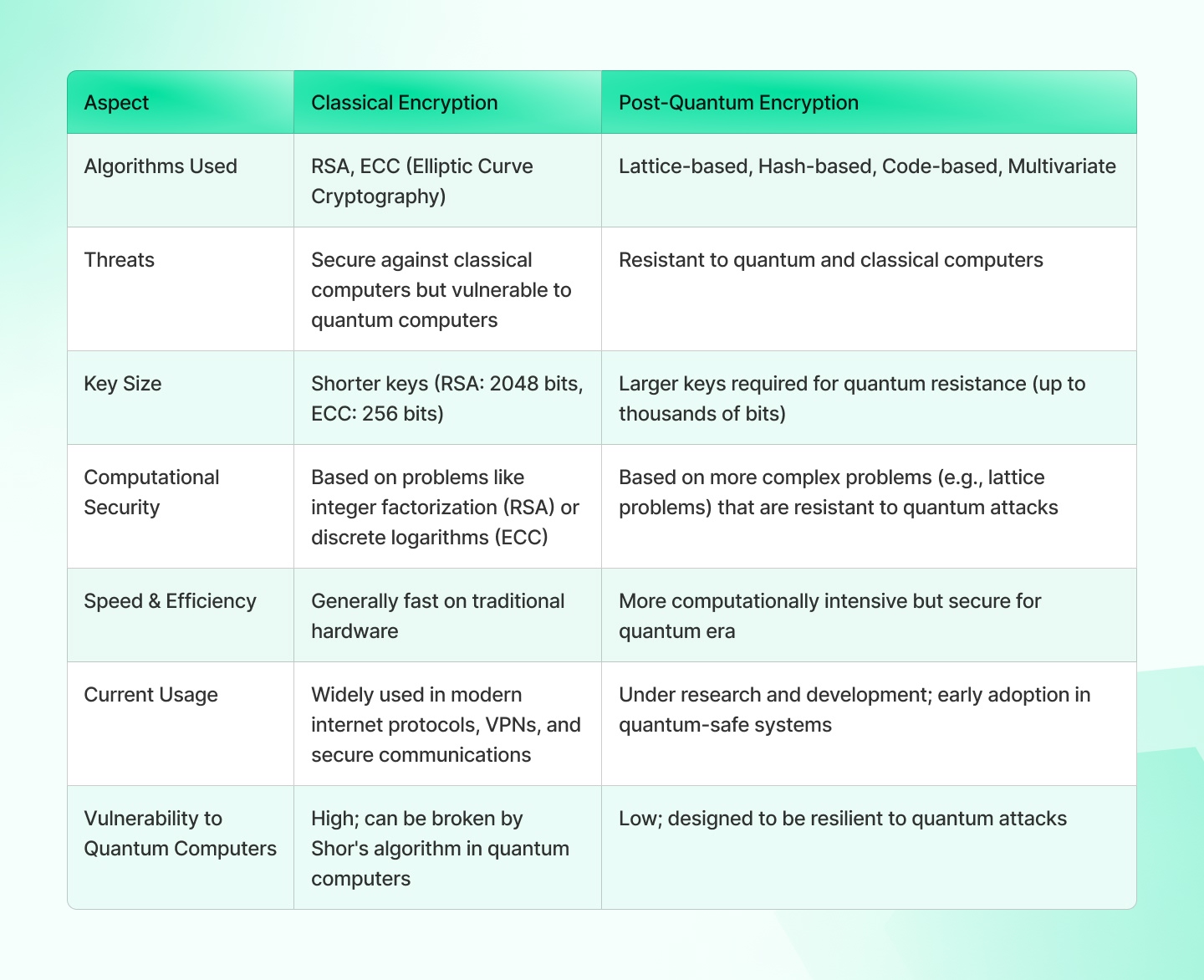
| Quantum computers have the power to break complex codes used by traditional encryption methods like RSA and ECC, posing a threat to security. |
| Post-quantum cryptography is an encryption algorithm that stands powerful against quantum computers. Some popular techniques include lattice based, multivariate, hash-based, code-based and isogeny-based cryptography. |
| GRC leaders must prepare for this Y2K bug by inventorying all systems that use traditional cryptography, prioritizing key assets, having transition budgets ready and staying ahead of the curve. |
Understanding the Power of Quantum Computing
Quantum computing is a computer science field that uses quantum mechanics to solve complex problems much faster than traditional computers. Unlike conventional computing, which represents data as 0s and 1s, quantum computing uses quantum bits, also known as qubits, to process various possibilities simultaneously.
The year 2025 has been declared the “Year of Quantum Computing” to celebrate advancements in quantum science. However, like artificial intelligence, it is a mixed blessing, particularly for cybersecurity. Quantum computing is expected to bring new threats, with the biggest concern being its ability to break encryption at an astonishing speed.
Is the quantum threat really this decade’s ‘Y2K bug’?
Security officials are engaging in discussions around quantum readiness for 2025 because quantum technology poses a threat to current encryption methods.
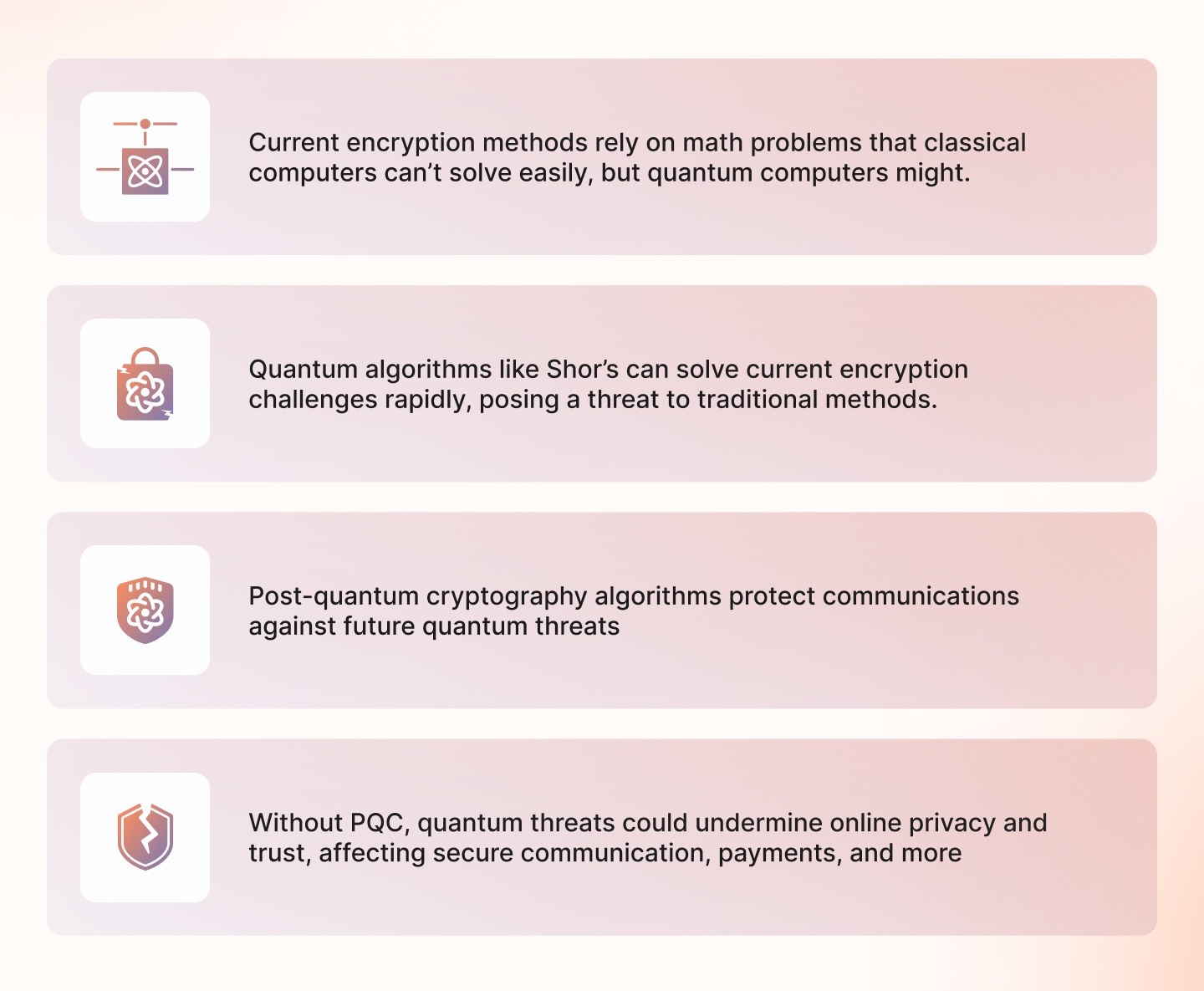
- Existing cryptographic algorithms are efficient against classical computers, as they take enormous time to solve complex problems. However, quantum computers can solve these mathematical problems at a snap, threatening data security and privacy. This is especially concerning for industries like healthcare and finance that store and transmit large amounts of data in an encrypted format.
- Here’s the thing: Public-key encryption methods, such as RSA and ECC, use mathematical problems to secure communication among parties. With these encryption algorithms, a public key is used to encrypt the message, and only the original sender with the key can decrypt the code. However, quantum computers can decrypt this message without the key as they can solve complex mathematical problems, making the code legible–courtesy: Shor’s and Grover’s algorithm).
- Shor’s algorithm can factor large numbers into prime numbers, even when the numbers grow larger. This wasn’t possible with classical computers and that is why it has a direct implication on RSA (Rivest Shamir Adleman) or public-key cryptography.
- Grover’s algorithm is used to search unstructured databases at a quadratic speed. So if the classical computer is searching items one by one and following ‘N’ steps, the grover’s algorithm can speed up this process by taking √N steps. Grover’s algorithm is a threat to symmetric key systems.
- Even if we argue quantum computers are not powerful enough to break current encryption at the moment, we have a looming threat of ‘store-now-decrypt-later’. This means that the attackers can store the encrypted data today and wait until the computers become powerful enough to decrypt it later.
- The anticipated disruption is being metaphorically tagged as the ‘Big Crunch of 2025’. Just like the Big Crunch in cosmology represents the universe collapsing, experts hint at the dismantling of existing encryption systems with quantum computing.
- It is also being compared to the Y2K bug because of the urgent need to update systems. In the year 2000, organizations across the globe had to update their systems to minimize date formatting issues, causing widespread chaos across industries. At that time, the severity of the impact on systems was uncertain, and so it is this time. It can even take years for quantum computers to become powerful enough to break encryption systems, but nobody knows the exact timeline, and so the best time to prepare for it is today.
What is quantum-resistant cryptography in simple terms?
Quantum-resistant cryptography, also known as post-quantum cryptography, is an encryption algorithm that is designed to be powerful against quantum computer attacks. It develops cryptographic systems that protect the data from unauthorized access or tampering from quantum computers.
PQC offers an alternative that uses complex codes and locks that are hard for quantum computers to break.
The cryptography technique uses the following methods to protect against quantum computers:
- Lattice-based cryptography: Uses mathematical structures called lattices, which are grid-like structures made up of multiple points.
- Multivariate cryptography: Uses a system of polynomial equations that limits possible solutions to secure data.
- Hash-based cryptography: Creates digital signatures based on cryptographic hash, the security of which depends on the strength of the hash function.
- Code-based cryptography: Uses error-correcting codes that transform words and phrases into a jumbled or hidden message.
- Isogeny-based cryptography: Utilizes unique pathways between points on elliptic curves called isogenies to create strong codes.
Also the catch is that PQC algorithms use larger key sizes as compared to existing methods. So if AES (Advanced Encryption Standard) uses 128-bit keys, the PQC algorithm will maybe use 258-bit keys to stay protected against quantum computers.
Driving the Quantum Shift: Key trends to watch for in 2025
There will always be signs, they say! Here’s what the experts are hinting at for everything quantum computing cybersecurity:
- The UN has declared 2025 as the International Year of Quantum Science and Technology. It is expected to boost innovation in various areas, such as medicine and cybersecurity.
- An interesting application of quantum computing will be its power to enhance AI and ML capabilities. Another prediction says that AI solutions will become more influential in 2025, and the intersection will enter key businesses.
- While Gartner says that asymmetric cryptography will become unsafe by 2029 (it does say the time to prepare for it is now), according to a Forbes article, 2025 could also see the ‘Q-day.’ This will be the day when quantum computers become sufficiently powerful to invalidate existing encryption systems.
- IBM has outlined a detailed roadmap for quantum computing. Rumors say it will begin selling 1000-qubit quantum computers in 2025. IBM has already partnered with Japan’s National Institute of Advanced Industrial Science and Technology (AIST) to create a 10000-qubit quantum computer.
The implications could be far-reaching, driving advancements in cybersecurity capabilities and increasing the urgency to adopt more secure encryption strategies. - The banking and finance sector will see a faster adoption of quantum computing technology. Top finance players such as JPMorgan Chase, Standard Chartered, and HSBC are already exploring it.
Can this impact PCI DSS encryption requirements and other data protection protocols? The chances are high! - The Office of Management and Budget (OMB) has asked federal agencies to prepare an action plan report on Post-Quantum cryptography (PQC). The agencies can adopt the NIST post-quantum encryption standards to create a migration strategy to PQC.
“The transition to a secured quantum computing era is a long-term intensive community effort that will require extensive collaboration between government and industry. The key is to be on this journey today and not wait until the last minute.”
Rob Joyce, Director of NSA Cybersecurity
How should organizations prepare for the Big Crunch?
The error-corrected quantum computers are still in their early phases, but that shouldn’t stop you from planning for the transition to quantum-safe encryption. Businesses that choose the ‘stay risk resilient’ mindset over ‘manage risks when they arrive’ are the ones that thrive in the end.
Here’s your Kickstarter guide to preparing for quantum cybersecurity risks:
1. Inventory all systems that use cryptographic algorithms
Use automated inventory solutions to catalog all systems that use cryptographic algorithms for encryption, digital signatures or any other data exchange. Map any dependencies on vendors involved in such crucial exchanges and understand their plans for migrating to quantum-resistant cryptography.
2. Plan prioritization criteria
Now, here’s the challenge. The new algorithms require high-performance systems, and not all of your current infrastructure can support PQC. So, begin by identifying legacy systems that cannot maintain the speed of encryption and decryption. This will ensure that any dependence on such systems does not impact the migration process because of the interconnectedness involved.
Next, you’ll have to identify high-value assets that must be prioritized if we are looking at phased adoption. Not every organization can afford to transition at once, and some assets will require gradual adaptation. So, to prioritize the assets, consider systems that store critical data and also the shelf-life of data, i.e., the time for which the data needs to be kept secure. The longer the period, the more protection is required.
According to a McKinsey report, these are the industries that are at risk based on shelf life and system life cycle:
3. Have your transition budgets ready
When forecasting your transition budgets, factor in the following:
- Hardware and software upgrades to support new algorithms
- Cost of additional infrastructure to build performance agility
- Vendor support fees
- Funds for pilot programs and testing
- Personnel recruitment and training
- Any compliance costs if there are regulatory updates
- Maintenance costs
There can be other additional factors, too, but we have accounted for the key areas requiring the most allocation.
4. Stay ahead of the updates
As we are all moving into an unknown path, it is crucial to stay updated and informed to minimize any resistance to change. Start by staying updated on the NIST PQC standardization processes. NIST has standardized three selected algorithms to withstand quantum attacks—CRYSTALS-Kyber, CRYSTALS-Dilithium, and Sphincs+. A fourth draft is also planned for anytime soon.
Also stay connected with industry peers and any relevant vendors or suppliers to stay abreast of the trends.
A good way to do this is to be a part of a community. Join here to meet with link-minded people.
5. Start training the teams
The centralized policies and the pilot programs will only succeed when the workforce feels empowered with cryptography knowledge. Train them on the need for migration and the action plan for transition. They must know how the existing algorithms work and why they need swapping.
Hey GRC leaders? We are in this together
As we stand at the brink of this new era, things seem to be an uphill battle. But you are not alone in this. To sail through this transformation, it is vital to be proactive, build a resilient foundation, and stay connected with the top minds. Let’s build a future-ready approach together.
As a new-gen GRC platform, Sprinto is committed to implementing forward-thinking security strategies and strengthening defenses across industries. We’ll keep you updated on regulatory changes, help you draft policies with quick templates, provide the required training modules and get you compliant across 25+ compliance frameworks or even custom frameworks.
You can count on us for anything GRC and take a platform tour to know us better.
Payal Wadhwa
Payal is your friendly neighborhood compliance whiz who is also ISC2 certified! She turns perplexing compliance lingo into actionable advice about keeping your digital business safe and savvy. When she isn’t saving virtual worlds, she’s penning down poetic musings or lighting up local open mics. Cyber savvy by day, poet by night!
Related blogs
research & insights curated to help you earn a seat at the table.




















