ISO 27003: Implementation Guide [Section Wise Breakdown]
Anwita
Oct 01, 2023

The ISO 27000 family of standards is an internationally recognized set of guidelines to help organizations implement, improve, or certify their information security.
ISO /IEC 27001 is the central standard on which a number of supporting standards are outlined – such as ISO 27003.
In this article, we discuss what ISO 27003 is, its importance, how it aligns with related standards, and what the official guide covers.
What is ISO 27003?
ISO 27003 is a set of guidelines that helps to successfully implement ISO/IEC 27001. It gives the background to implement an information security management system (ISMS) as per ISO 27001. ISO 27003 is known for Information technology — Security techniques — Information security management —Guidance. This document provides recommendations and explores possibilities, and permissions related to 27001.
The ISO 27003 standard is strictly a guideline-specific supporting document and should be used only as a reference. Other guideline-based standards in the ISO 27000 family that expand on ISO 27001 are ISO 27002, ISO 27004, ISO 27005, ISO 27007, ISO 27013, and ISO 27021.
Its purpose is only to provide information around implementation in detail and not a certification – you cannot be ISO 27003 certified. You can get ISO 27001 certified and use ISO 27003 for reference. Note that it is not mandatory but recommended, as this is an official set of instructions that makes your job easier.
ISO 27003:2017 is an updated and revised version of ISO 27003:2010. The main areas of revision include:
- The scope and tile now includes explanation and guidance on the latest edition of ISO 27001, updated in 2013.
- The structure is now aligned with that of ISO 27001 to make it easier to understand.
- Compared to the previous edition which explained on the basis of the order of activities, the current edition explains requirements irrespective of the order of implementation.
Importance of ISO 27003
As security incidents continue to rise, building cyber resilience should be a priority – especially when you have access to sensitive client data. Recovering from attacks is not easy and costs you time, money, and effort.
Only 14% of organizations are well-equipped to defend against cyber incidents. 81% of CISOs feel that staying ahead of attackers is a difficult and constant battle.
When you implement a globally accepted, gold-rated standard, it helps you establish best security practices strengthen the overall efficiency of security processes and gain compliance. Compliance implementation is easier said than done – which is why a supporting document like ISO 27003 is necessary to help you understand the right approach to it.
ISO certification shows your clients that you take infosec security measures seriously and establish brand authority. You can use the ISO 27003 implementation guide to meet the requirements specific to your business and get certified.
As previously stated, the ISO 27000 standards are interrelated and interdependent with 27001 as the central framework. While ISO 27001 details requirements to establish, monitor, implement, operate, maintain, and review ISMS, ISO 27003 provides a basic yet comprehensive guide to implement ISO 27001 requirements.
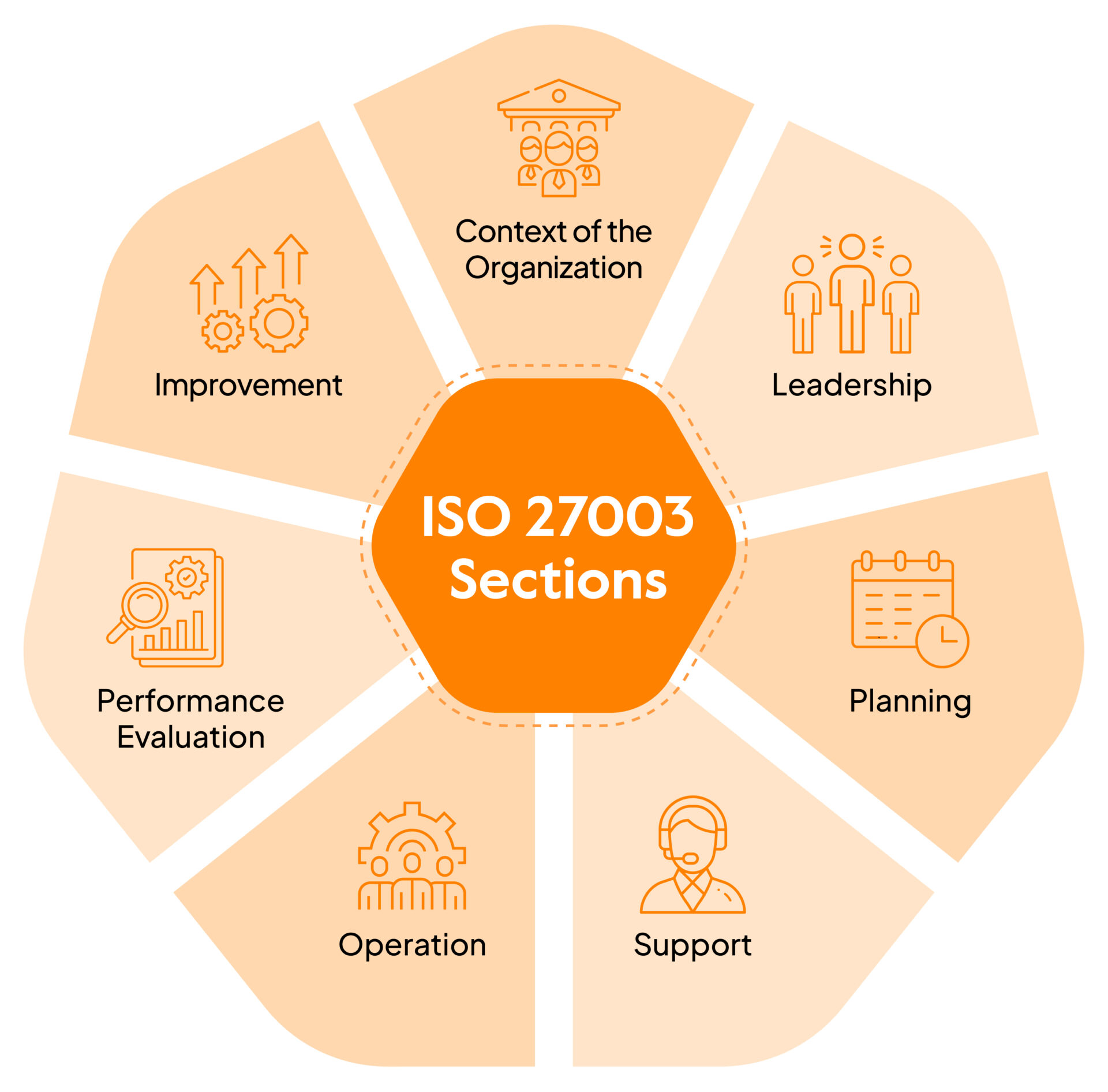
In order to maintain the structural integrity of all standards, ISO 27003 maintains the format of ISO 27001, which has seven main sections. These are:
- Context of the organization
- Leadership
- Planning
- Support
- Operation
- Performance evaluation
- Improvement
ISO 27003 Implementation Guide: section wise explanation
The official ISO 27003 PDF lists the required activity stated in 27001. It offers a brief explanation of what it means and guidance on how to approach and implement that requirement.
The table below lists the requirements and what you can expect from each.
| Required Activity | ISO 27003 Explanation and guidance brief |
| 4. Context of the organization | |
| 4.1. Understanding the organization and its context | Continuously analyze internal and external issues that affect information security and how to manage it to meet the organization’s objectives. It explains the purpose of analysis, what constitutes external issues, organization specific external issues. It further guides how to identify these issues with examples. |
| 4.2. Understanding the needs and expectations of interested parties | Defines what constitutes interested parties within and outside the organization. Requires organizations to identify the requirements of the interested parties and document how they impact the scope or constraints. |
| 4.3. Determining the scope of the information security management system | Describes where the scope is applicable and where it is not. It lists the factors that may affect the determination of the scope and the instances that affect its implementation. The guidance provides a multi-step approach to establish the ISMS scope and what to include in its documentation. |
| 4.4. Information security management system | Requires organizations to meet ISMS requirements. Does not provide any specific guidance or information. |
| 5. Leadership | |
| 5.1. Leadership and commitment | Defines top management, its roles and responsibilities. Guides them to establish leadership and commitment. |
| 5.2. Policy | Describes the strategic importance of ISMS and directs infosec activities. The guidance provides what the security policy should cover, its extent, what it should reflect, statements to include, format and language, and to whom it should be communicated. |
| 5.3 Organizational roles, responsibilities and authorities | Top management should ensure that all roles and responsibilities to fulfill ISMS requirements are assigned. The guide lists security activities that require resources. |
| 6. Planning | |
| 6.1.1. Actions to address risks and opportunities | Explains the goals that organizations should aim for in order to align their risks and opportunities based on internal issues, external issues, and requirements from interested parties. It further explains the possible reasons behind the risks connected to these goals. It illustrates examples of how opportunities change the type of risks. As per the guidance, organizations should determine risks based on goals and plan to implement the action, and measure the effectiveness of those actions. |
| 6.1.2. Information security risk assessment | Defines how organizations should define and implement security risk assessment processes, such as what the process should maintain, identification of risks, and analysis of the same. It guides to establish the risk criteria based on several factors. |
| 6.1.3. Information security risk treatment | Defines what information security risk treatments are. The guidance provides risk treatment options, what the appropriate measures should ensure, what the Statement of Applicability (SOA) should contain, how to formulate a treatment plan, and how to obtain approval from risk owners. |
| 6.2. Information security objectives and planning to achieve them | Explains the importance of information security objectives, what constitutes it as per ISO 27001, and what organizations should determine while planning how to achieve it. The guidance sets examples of how infosec objectives can be expressed and what to include in its documentation. |
| 7. Support | |
| 7.1. Resources | Lists the categories of resources required to perform any activity. The guide details the responsibility of organizations to maintain, review and acquire resources. |
| 7.2. Competence | Explains what competence is, its types, how new competence can be acquired. The guide explains how organizations should manage, evaluate and document roles to gain maximum competency. |
| 7.3. Awareness | Explains what employees of an organization should understand and accept about information security. Guides organizations to help employees gain awareness. |
| 7.4. Communication | Details where communication can take place. Guides organizations to determine what to communicate and how to identify requirements for it. |
| 7.5. Documented information | |
| 7.5.1. General | Explains what documented data is needed for and what it can contain. Provides examples of documented data that can be important for organizations to boost ISMS efficiency. |
| 7.5.2. Creating and updating | Details in which forms the document can be maintained and how to create a structured data library. |
| 7.5.3. Control of documented information | Provides guidance on what the data library can be used for, classification requirements, change requirements, distribution process, retention rules, and responsibility for documents from external sources. |
| 8. Operation | |
| 8.1. Operational planning and control | Explains which plans and activities organizations must perform to meet their ISMS requirements. It explains what to ensure and determines when these processes are outsourced. The guide details what to consider and implement, how to plan changes, handle unintended changes and manage outsourced suppliers. |
| 8.2. Information security risk assessment | Explains how to approach risk planning, management, and incident response. Guides on what to determine if incidents occur. |
| 8.3. | Details which sub guides to follow to implement infosec risk treatment plan. |
| 9. Performance evaluation | |
| 9.1. Monitoring, measurement, analysis and evaluation | Explains the objectives of monitoring and measuring security performance and what to establish. The guide details good practices and the generic types of measurement. |
| 9.2. Internal audit | Lays down the principles of auditing and what requirements to include in the organization’s internal audit. The guide helps to manage audit programs, evaluate auditors, perform the audit, and list the supporting standards for more information. |
| 9.3. Management review | Explains the terms related to its purpose and the frequency of management review. Guides management to review performance reports of ISMS and lists the topics that should be addressed in the agenda of the management review. |
| 10. Improvement | |
| 10.1. Nonconformity and corrective action | Lists the types of nonconformities with examples and reference guides for corrective actions. The guide defines the handling processes based on which organizations should react to non-conformities, processes for corrective actions, and documentation requirements. |
| 10.2. Continual improvement | Talks about how organizations should approach ISMS to gain continuous improvement. Lists the factors to analyze while assessing the relevant elements. |
Also check out: A handy checklist of ISO 27001
ISO 27003 made easy
Compliance is a checklist in the to-dos of your that you should complete to take your organization in the right direction. The journey isn’t always an easy one – the formal language, tone, and lengthy requirement list can be discouraging.
Sprinto makes this easy for you by automating the processes. It contains all policies and controls you may possibly need not just to gain compliance, but maintain it with least human intervention – so you can focus on developing your business.
Talk to our experts today to learn more about how Sprinto makes your ISO 27003 compliance process easy!
FAQs
What is the purpose of ISO 27003?
The purpose of the ISO 27003 standard is to provide a background to implement the requirements of ISO 27001 successfully.
What is the difference between ISO 27002 and ISO 27003?
ISO 27002 lists the common control objectives and best practices to use as an implementation guide while choosing and implementing controls to gain information security. ISO 27003, on the other hand, explains the requirements of 27001 and offers guidance on implementing those.
Anwita
Anwita is a cybersecurity enthusiast and veteran blogger all rolled into one. Her love for everything cybersecurity started her journey into the world compliance. With multiple certifications on cybersecurity under her belt, she aims to simplify complex security related topics for all audiences. She loves to read nonfiction, listen to progressive rock, and watches sitcoms on the weekends.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


