The Ultimate Guide to the ISO 27000 Series of Standards
Anwita
Feb 10, 2024

If your business handles, manages or processes sensitive customer data in any capacity, information security must be a priority. With the number of data breaches going up, more businesses look for vendors who can protect their sensitive data. To provide that guarantee, you need to maintain the highest security standard.
The ISO 27000 series of standards empower your business to gain a robust security posture by certifying your policies, processes, and controls.
In this article, you will learn what ISO/IEC 27000 standards are all about, why they are important, and what each standard of the family is concerned with.
What is ISO/IEC 27000 series of standards?
ISO/IEC 27000 is a series or a family of standards published by the International organization for Standardisation and the International Electrotechnical Commission. Also abbreviated as ‘ISO27K’, it combines a range of information security standards to form a comprehensive framework to help organizations strengthen their information security management system (ISMS).
ISO 27000 provides a glossary of terms and definitions for the ISMS family of standards. It was developed and published in joint collaboration by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It applies to organizations of all sizes.
The ISO 27000 family of standards can be broadly classified into four categories of standards based on its function. Each has a purpose and can be normative or informative.
Normative elements are used to describe the scope of each standard and how to comply with it. These elements include recommendations, requirements, and possibilities.
Informative elements are descriptive in nature and help to understand the concepts. It provides context, background, additional recommendations, and relation with other elements.
Only the normative standards can be audited for compliance.
| Purpose | Standard Name | Type |
| Overview and terminology | ISO 27000 | Informative |
| Requirements | ISO 27001, ISO 27006, ISO 27009 | Normative |
| General guidelines | ISO 27002, ISO 27003, ISO 27004, ISO 27005, ISO 27007, ISO 27013, ISO 27014, ISO 27021, TR 27008, TR 27016 | Informative |
| Sector-specific guidelines | ISO 27010, ISO 27011, ISO 27017, ISO 27018, ISO 27019 | Informative |
List of ISO 27000 series of standards
The ISMS family of standards are interrelated and focus on ISMS requirements. Here’s a summary of what each describes and is concerned with:
ISO 27000
ISO 27000 provides an overview, definitions, and introduction to the ISMS family of standards.
ISO 27001
Concerned with normative requirements to develop and operate ISMS. Helps with controls to mitigate risks associated with data assets specific to your business needs.
Also check out: ISO 27001 requirements
ISO 27006
Provides guidance and specifies requirements to organizations that offer auditing services and ISMS certification as per ISO 27001. These service providers must demonstrate competence and reliability in keeping with ISO 17021 requirements.
ISO 27009
Outlines requirements to use ISO 27001 in a specific sector. It also specifies how to include additional requirements, refine those, and add controls in addition to those specified in ISO 27001.
ISO 27002
Guides to select and implement common information security controls to bolster your information security. It provides best practices and guidance to use these controls.
Check out ISO 27002 Guide
ISO 27003
Explains and guides how to implement ISMS as per ISO 27001 successfully.
Check out ISO 27003 complete guide
ISO 27004
Guides and assists organizations to evaluate and measure performance of ISMS to fulfill ISO 27001:2013, 9.1 requirements.
Further deep dive into ISO 27004 standard
ISO 27005
Guides organizations to implement risk management as per ISO 27001.
ISO 27007
Guides organizations to conduct ISMS audits and competence of ISMS auditors as per ISO 27001.
ISO 27013
Guides organizations that intend to
a) Implement ISO 27001 when ISO 20000-1(standard for service management system) is already in place or implement the latter (ISO 20000-1) when ISO 27001 is in place
b) Implement both ISO/IEC 27001 and ISO/IEC 20000-1 together
c) Integrate their management systems as per ISO/IEC 27001 and ISO/IEC 20000-1.
It also helps organizations understand the similarities and differences between these two.
ISO 27014
Guides organizations on principles and processes to monitor and manage information security.
ISO 27021
Intends to help a number of entities such as
a) Individuals who wishes to demonstrate their competence as ISMS professionals or gain the knowledge needed to work in this field
b) Organizations hiring ISMS professionals
c) Bodies who certify ISMS professionals
d) Organizations or institutes who offer courses to educate or train candidates for ISMS
TR 27008
Guides organizations to review implementation and operation controls in keeping with the specific needs of the business.
TR 27016
Enables organizations to value their data assets, make informed decisions on the assets in a way that offers economic sustainability, and gain insight into the economical consequences of their decisions.
ISO 27010
Guides and provides controls to initiate, implement, maintain and improve information security with other organizations and sectors.
ISO 27011
Helps telecommunication organizations to implement information security controls. It helps them meet security management requirements like integrity, confidentiality, and availability.
ISO 27017
Guides cloud service providers to implement security controls as per ISO 27002.
ISO 27018
Establishes control objectives, controls, and guidelines to protect personally identifiable information (PII) for cloud computing as per ISO 29100.
ISO 27019
Applies to process control systems used by the utility industry. Guides them to control and monitor production, transmission, distribution or generation of energy.
Also check out: What is asset management under ISO
How ISO 27000 series of standards streamlines security management
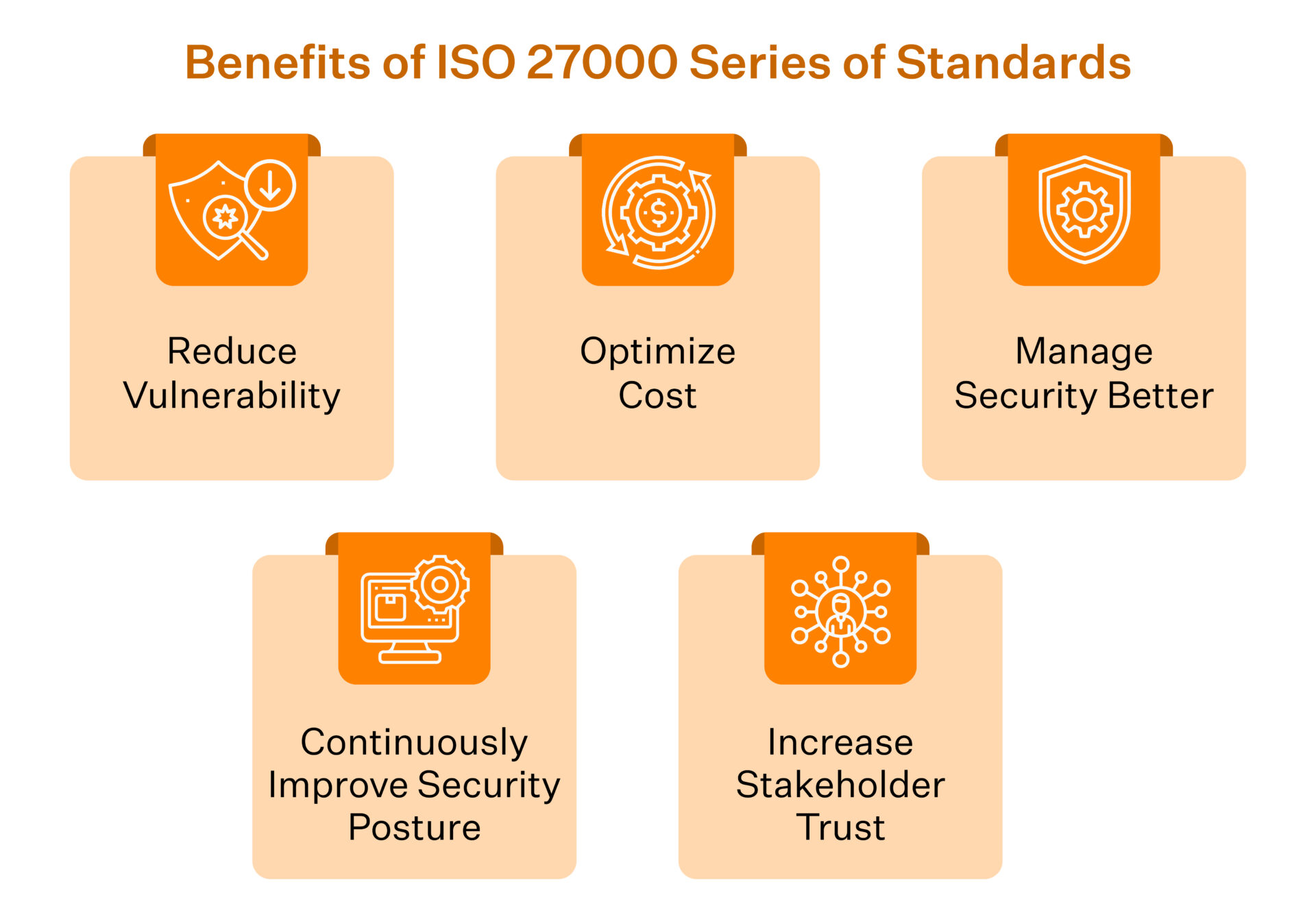
- When you implement ISMS, it reduces vulnerabilities across your IT infrastructure. It enables you to gain sustainable security success.
- It is a structured framework that helps you implement and maintain a comprehensive and cost effective process across all operations.
- It assists you to manage security holistically and responsibly through better education and training.
- When you implement an internationally accepted standard of security, it gives you the flexibility to continuously improve controls to keep up with dynamic security needs.
- It empowers you to manage information security in an economical way and increases stakeholders’ trust.
Why should you implement ISO 27000 standards?
ISO 27000 series of guidelines provide a framework for your organization to assess risks and implement custom security protocols. But it does more than provide guidelines – you gain a host of benefits.

Highlights gaps in security management
As a business owner, you may assume that your organization’s functions and the process you adopted are the right way and make sense to you. This is called paradigm blindness and prevents businesses from overcoming challenges.
Implementing new controls and systems may seem difficult at first. But knowing your security status highlights existing gaps and encourages you to fix those. ISO 27000 series of standards helps your organization to identify gaps, eliminate roadblocks, discover growth opportunities, and manage better.
For example, the ISO/IEC TR 27008 document guides users to implement and check the operation of controls against the already established infosec standards. This will inevitably surface your gaps and enable you to fix those. As a result, you can improve your security posture and performance.
Check out how to perform ISO 27001 gap analysis
Prevents costly incidents
Breaches don’t just cost you money – they cost you your reputation. Damage control is time-consuming and a hassle nobody wants. The solution? Buckle up your security. The benefits of a strong security posture outweigh the cost of implementing it, especially in the long run.
ISO 27001 helps you develop controls necessary to mitigate risks within your organization. ISO/IEC 27005 provides a comprehensive guidance on risk assessment. You can use these to identify malicious behavior and mitigate them before it affects your system.
As malicious actors become smarter, so should your IT infrastructure. With the number of breaches rising, you can no longer afford to consider security as an optional investment.
Gives competitive advantage
Businesses don’t want their data mishandled or tampered with – they want a trustworthy partner. ISO 27001 is an internationally accepted security standard that is a great way to establish trust. An industry respected standard helps you efficiently manage third party financial data and intellectual property. It shows that you take data security seriously.
A survey conducted by ISO in 2021 shows that more than 10000 information technology companies were ISO 27001 certified in 2021.
When you are compliant, and your competitors are not, sales prospects are more likely to partner with you.
Also read: ISO 27001 certification cost
How to Get ISO 27000 Certified
A common misconception out there is that ISO 27000 is a certification. Just to clarify, it is not a certification but a guideline that helps you comply with its regulations. ISO 27001 is a certification you get after an external auditor has reviewed your organizations’ security policies. So how do you get ISO 27001 certified?
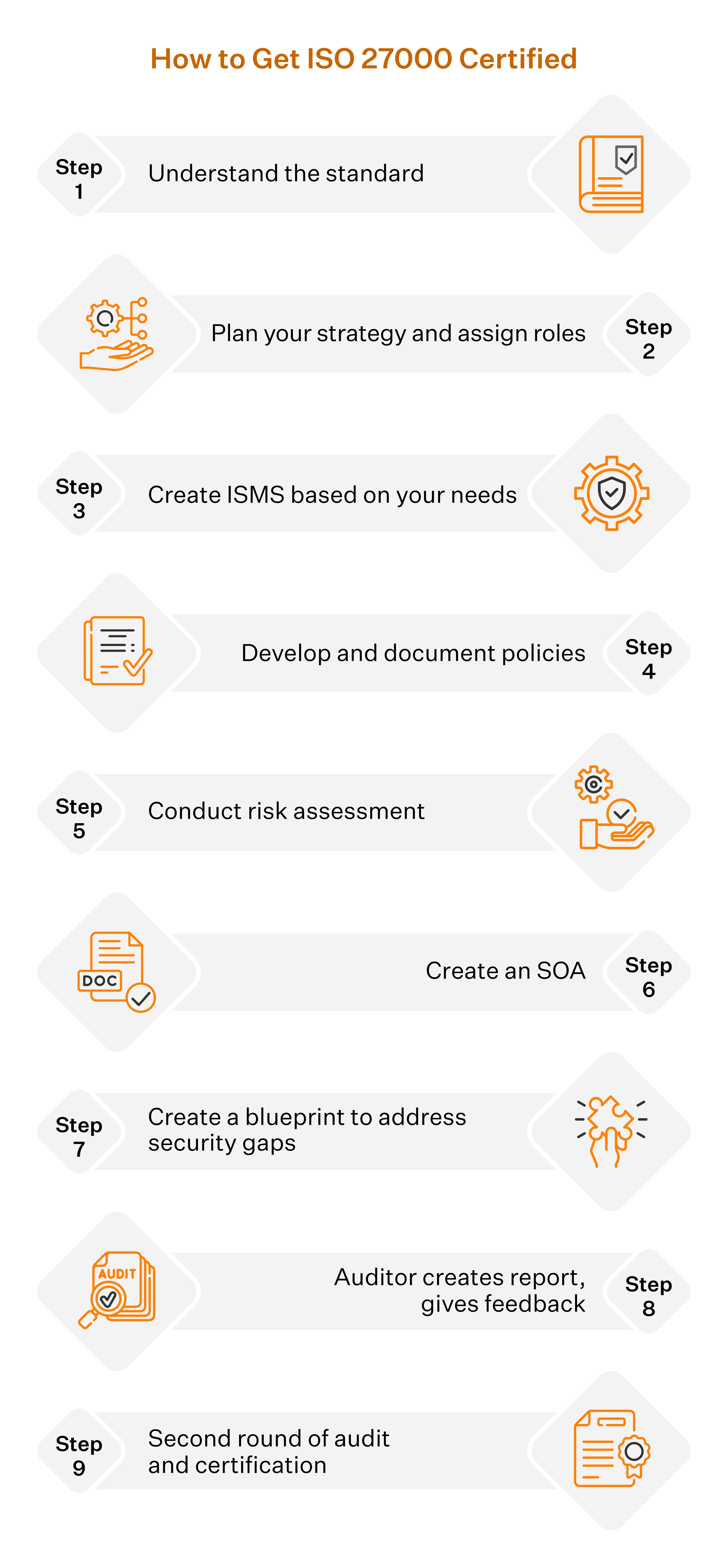
Step 1:
Before starting this process, it is crucial to understand the guidelines well. Read the standard carefully before you proceed to implement it.
Step 2:
Plan the minor details with the relevant departments or stakeholders and assign roles as appropriate so that no confusion occurs later.
Step 3:
Create an ISMS scope based on your infrastructure, type of assets, business needs, products, and other relevant information.
Step 4:
At this stage, you need to develop policies and procedures and document the same. As the ISO 27001 is a lengthy list of requirements, this step can be time-consuming. Document all the steps in detail. During the audit, this will be used to provide appropriate feedback and properly conduct the assessment.
Step 5:
Conduct a thorough risk assessment to identify the existing gaps in your infrastructure. Understand what part of the ISMS can be improved, what is missing, and what is applied incorrectly.
Step 6:
Create a statement of applicability (SOA). The SOA is a list of controls applicable to your business. It should show which controls you have chosen along with a justification for the exclusion of those you didn’t choose.
Step 7:
Create a blueprint to address those gaps. Implement the necessary controls and applicable processes. You may consider training your employees as they play a significant role for a robust security policy.
Step 8:
You are ready for an internal audit. The ISO 27001 accredited auditor will review your policies, controls, and documents. They will look for gaps and create a report based on their observations. When you have the feedback, you can use it to rectify the gaps wherever you fall short.
Step 9:
An external auditor will conduct another round of audit and provide you with an audit report. After this, you will undergo another round of audit where the auditor checks if your business is operating as per the standards and provides you with a certification.
Automate your ISO 27001 compliance with Sprinto
Compliances are complicated and confusing, but they don’t have to be.
Sprinto offers an automated solution that uncomplicates your compliance journey. It takes care of every manual task – from policy creation to mapping security controls and overseeing gaps in security posture. Sprinto also offers an in-app staff security training and tracking feature that helps your employees stay educated and updated on the latest in cybersecurity as well as fend off breach attempts, such as phishing.
Wondering how much ISO 27001 certification would cost you? Have more questions? Book a demo with us to learn more about how we can make your compliance journey hassle-free.
Anwita
Anwita is a cybersecurity enthusiast and veteran blogger all rolled into one. Her love for everything cybersecurity started her journey into the world compliance. With multiple certifications on cybersecurity under her belt, she aims to simplify complex security related topics for all audiences. She loves to read nonfiction, listen to progressive rock, and watches sitcoms on the weekends.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


