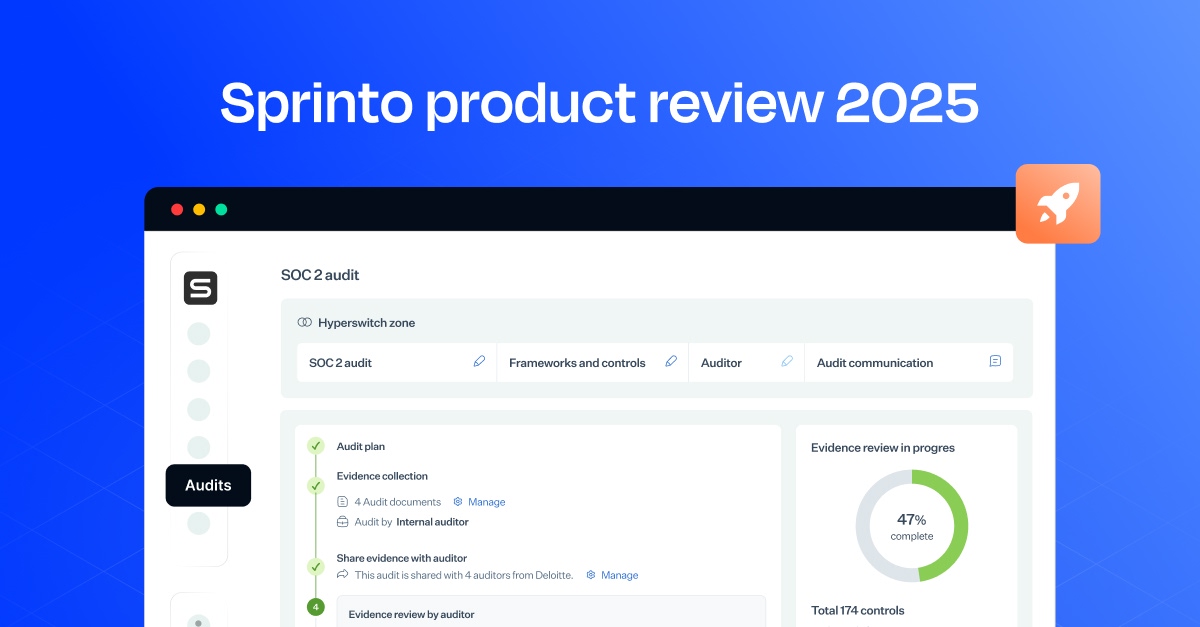
A Comprehensive Sprinto Review 2025
Sprinto is a compliance automation designed for cloud-first companies. It offers instant time-to-value with streamlined workflows and a self-serve approach to put you in control. Engineered for speed and simplicity, the tool enables you to achieve compliance milestones quickly, saving both time and effort from day one. Fast-growing tech companies worldwide trust Sprinto for its…
Complementary User Entity Controls: The key to Enhanced Security
Imagine if a bank provides you with a vault equipped with a high-quality locking mechanism and surveillance systems, you assume that you are protected from all theft and your assets are safe. However, if you are negligent with your key and pass code, the bank cannot safe-keep your assets. The vault’s features and user entity…
What are Cloud Vulnerabilities – How to Manage Effectively ?
A recent report states that 4 out of 5 security vulnerabilities in organizations across all sectors originated from the cloud. The swift transition to complex cloud environments has given rise to a spectrum of cloud security issues. According to Google Cloud Forecast 2025 paints a stark picture of the evolving threat landscape. The sheer number…
Protecting What Matters: Cybersecurity for Critical Infrastructure
There’s a saying—if you can access something remotely, so can hackers. The increasing connectivity and convergence have, on one side, diminished physical perimeters, for the good. But they have also brought an increased influx of new threat classes. When it comes to critical infrastructure, though, the stakes are much higher—disruptions can impact essential services and…
Cybersecurity Benchmarking: The Key to Unlocking Maturity and Resilience
Comparisons are often seen in a bad light– whether it’s your personal life, or your business performance. Sure, there’s no one size fits all, and why should you care what the others are up to? But what if benchmarking influences you in a better way? What if understanding what the competitors are doing better helps…