HIPAA violations continue to surge across the healthcare ecosystem, and the data tells a clear, yet troubling story. According to HIPAA Journal, 508 healthcare data breaches were reported as of August 2025, with 58 breaches impacting 3,789,869 individuals happening in August alone.
A huge chunk of these issues came down to compromised user or administrative accounts, which approximately 31% of organizations have claimed to have dealt with. And with more Protected Health Information (PHI) flowing through cloud apps, SaaS tools, and remote setups, even small mistakes or oversights can quickly turn into compliance issues.
This guide walks through the most common HIPAA violation examples, real case studies, and practical steps any organization can use to stay compliant and reduce risk.
- A HIPAA violation happens when PHI is accessed, shared, or protected improperly under HIPAA’s Privacy, Security, or Breach Notification Rules.
- Common issues include unauthorized access, improper disclosures, weak technical safeguards, phishing attacks, and late breach notifications.Violations fall into administrative, civil, and criminal categories, depending on severity and intent.
- HIPAA fines range from $100 to $50,000 per violation, up to $2M a year, with criminal cases carrying fines up to $250,000 and possible jail time.
What is considered a HIPAA violation?
A HIPAA violation happens any time Protected Health Information (PHI) is accessed, shared, used, or handled in a way that fails to comply with HIPAA standards and rules. In simple terms, it means PHI wasn’t properly protected or was accessed by someone who shouldn’t have access to it.
The Office for Civil Rights (OCR) investigates HIPAA violations, and depending on the severity of the violation, fines, penalties, and legal consequences may be imposed.
Not all disclosures count as violations. HIPAA makes room for incidental disclosures, the kind that’s unavoidable even when reasonable safeguards are in place. For example, a patient’s name being overheard by a nurse is usually considered coincidental and not a violation. A violation occurs when safeguards are missing or ignored, or when PHI is used or shared without a valid reason.
It’s also important to understand the difference between a HIPAA violation and a HIPAA breach.
- A violation means a rule was broken.
- A breach means PHI was actually compromised, lost, or exposed.
- All breaches involve a violation, but not all violations lead to a breach.
To learn more about HIPAA violations, watch our video
Different types of HIPAA violations
HIPAA violations are usually grouped into three broad buckets—administrative, civil, and criminal violations. Each type reflects a different level of severity and intent, but across all three, the same patterns recur: improper access to PHI, unauthorized disclosures, weak security practices, and inadequate training or procedures.
Let’s look at the three types with examples:
1. Administrative violations
These occur when an organization fails to follow the required administrative processes outlined in HIPAA. They usually don’t involve intentional misuse of PHI, but they do reflect noncompliance. Examples include:
- Using incorrect transaction or billing codes
- Missing required HIPAA documentation or policies
- Not having a Business Associate Agreement (BAA) in place
- Poor or outdated internal procedures
These violations often serve as red flags that security or privacy gaps may exist elsewhere.
2. Civil violations
Civil violations happen when privacy, security, or breach notification rules are broken due to negligence rather than malicious intent. Common examples include:
- Denying patients timely access to their medical records
- Not conducting proper risk assessments
- Lacking basic safeguards that lead to PHI exposure
- Improper disposal of documents or devices
These are typically handled by the HHS Office for Civil Rights (OCR) and can result in tiered financial penalties depending on the level of negligence.
3. Criminal violations
Criminal violations are the most serious and involve intentional misuse of PHI. These occur when someone knowingly obtains or discloses individually identifiable health information.
Penalties can include heavy fines and even imprisonment, with harsher consequences when the violation is committed for profit or malicious purposes.
Top 10 Examples of HIPAA Violations With Real Cases
Most HIPAA violations take place because employees working in hospitals or medical institutions aren’t aware of its rules and what breaks them. In fact, a 2021 survey says that 24% of employees were not trained in security awareness in the healthcare sector.
This can have serious consequences like huge financial losses and even imprisonment. Here’s the list of examples of HIPAA violations:

1. Healthcare employees divulging patient information
The privacy rule of HIPAA covers all kinds of patient information, whether written, oral, or electronic. It gives individuals the right to set limitations on who can look at their health information and requires consent to do so.
So, if anyone looks at, talks about, or shares patient information, they are committing a privacy breach of patient privacy. This is one of the most common violations of HIPAA committed by healthcare professionals and can also lead to potential jail time. The following case explains how.
Case 1: Snooping on Britney Spears’s medical information
In 2008, Britney Spears was admitted to the Los Angeles (UCLA) Medical Center where 13 employees were fired for looking at her medical records without consent. Apart from that, 6 physicians were also suspended.
After this happened, UCLA released a statement:
“All staff members are required to sign confidentiality agreements as a condition of their employment and complete extensive training on HIPAA-related privacy and security issues.”
2. Medical records falling into the wrong hands
Physicians and hospital employees may have to carry patients’ health information on their laptops, mobile devices, tablets, etc. It is unavoidable for daily operations, but is it safe? A very common HIPAA violation example is assets getting stolen and patient information getting disclosed to unwanted parties.
There is no liable insurance for theft, but there are ways to protect the information contained in these assets through encryption, password protection, multi-factor authentication, etc. Let’s understand this better with a case.
Case 2: Children’s Medical Center in Dallas suffered a loss of $3.2 million
There were several incidents of HIPAA violations in the Children’s Medical Center of Dallas as reported by Health Care IT News. In one of these incidents, there was a loss of 3,800 PHI data from a stolen Blackberry device that had no password protection or encryption.
The center had to pay the full fine because it mishandled patient information and continued to let employees use electronic devices without sufficient protection. This is one of the worst breaches in US healthcare history.
During the case, the Acting Director of OCR said
“Ensuring adequate security precautions to protect health information, including identifying any security risks and immediately correcting them, is essential.”
Save 80% of man hours spent on HIPAA
3. Sharing PHI using non-secure methods
According to HIPAA’s security rule, you must use or share patient information securely that upholds its privacy. Hackers and other unauthorized individuals can easily access information that is passed over any unsecured network.
Hence, sharing patients’ health information through texting, video conferencing applications, phone calls, personal emails, and common file-sharing services counts as a HIPAA violation. This can result in e-PHIs being readily available on the network for security breaches and attacks. Here’s a close case to this.
Case 3: Non-secure file-sharing exposed 11k patients’ information
Lanap & Dental Implants of Pennsylvania violated HIPAA rules by posting about 11,000 dental records on a torrent site for file sharing. These records were available online for four years. The data wasn’t encrypted, just obfuscated, which means anyone with basic technical skills could access it.
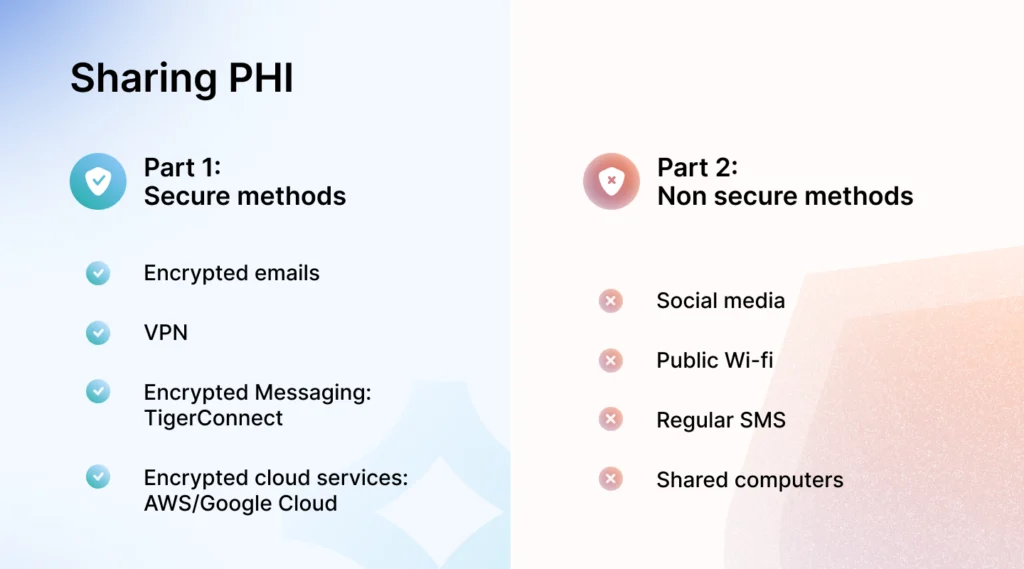
Know more about HIPAA-compliant text messaging applications.
4. Posting PHI on social media
Under no circumstances can healthcare facilities or other individuals post any health information about patients on social media, including online reviews, LinkedIn, rating platforms, etc. Even if the individual does not mention the patient’s name, this is not allowed and falls under unauthorized disclosure of PHI.
Melanie Fontes Rainer, Director of OCR (2023) explains:
“OCR continues to receive complaints about health care providers disclosing their patients’ protected health information on social media or the internet in response to negative reviews. Simply put, this is not allowed,”
Case 4: Health Center responded to a negative online review with PHI
Manasa Health Center is a psychiatric service provider in New Jersey. They had disclosed a patient’s protected health information in response to a negative online review.
Following an OCR investigation, it was found that Manasa Health Center violated HIPAA Privacy Rules by disclosing patient information and failing to implement proper policies. They paid $30,000 to settle the case with HHS and agreed to a corrective action plan.
5. Accessing patient files without authorization
Under HIPAA, no one has the right to access health records without patient authorization or under false pretenses. Even if the information is not used for any wrong reasons, stolen, or sold, it cannot be accessed. This holds true for doctors or healthcare staff, too.
Individuals must remember that written consent is required to access PHIs, and without it, access will be regarded as a HIPAA violation. Let’s look at an example that highlights this.
Case 5: Doctor H suffered prison time for unauthorized access
Dr. H immigrated to the States from China, did some research in the country, and had access to patient records. He was serving his notice period during the violation and accessed personal health records in the state healthcare system during his free time as he was curious about colleagues, celebrities private lives.
He was unaware of the rules of HIPAA at the time and did not know he couldn’t access health records without proper authorization. However, he didn’t use any information for personal gain or share it with anybody. After his termination, he was charged with HIPAA and had suffered four months of jail time with a $2000 fine.
6. Using weak third-party technology
A large number of healthcare providers use third-party tracking applications to collect user data and track their online activities. The company later uses this information to provide a better patient experience.
However, if the third-party applications used in this scenario are not secure enough, it can lead to identity theft, user harassment, stalking, and even data leaks containing patient activity. Here’s a similar case.
Case 6: Hospital websites sent patient data to Facebook
The Markup found that 33 of Newsweek’s top 100 hospitals in America used a tracker called Meta Pixel, which sent Facebook data whenever someone clicked to schedule a doctor’s appointment.
This tracking tool collected sensitive, identifiable health information, including details about medical conditions, prescriptions, and appointments labeled with IP addresses, and shared it with Facebook.
David Holtzman, a health privacy consultant and former senior privacy adviser at HHS, said on this “I cannot say [sharing this data] is for certain a HIPAA violation. It is quite likely a HIPAA violation.”
Keep in mind:
The IP address is one of the 18 identifiers of PHI under HIPAA. Learn about the 18 identifiers of HIPAA.
7. Delaying breach notification
The HIPAA Breach Notification rule clearly says that all affected parties should be notified about a breach without delay and within 60 days of discovering any incident.
The covered entities should provide them details like the type of information leaked, protective measures taken, and contact information. Failing to do so qualifies as a HIPAA violation and can incur substantial fines. Below is a similar example.
Case 7: OSU-CHS paid $875,000 for failing to provide notification
On January 5, 2018, Oklahoma State University—Center for Health Sciences (OSU-CHS) reported a HIPAA breach in which a hacker accessed a web server containing the ePHI of 279,865 individuals.
The breach was initially reported to have occurred on November 7, 2017. However, under investigation, it was revealed that it began on March 9, 2016. This was marked as a HIPAA violation for delayed notification of affected individuals and HHS, among other violations.
As a result, OSU-CHS had to settle with the HHS by paying $875,000 and including a strong corrective action while being monitored for two years.
8. Absence of risk management
A powerful risk management process is necessary for healthcare organizations. If you do not conduct thorough, regular risk assessments and internal audits of your access controls and processes, you’ll never know where your vulnerabilities lie, which creates an open field for attackers.
Under HIPAA’s security rule, all covered entities are required to conduct an organization-wide risk analysis. As stated in the HHS website, the process requires you to:
- Assess potential risks to e-PHI;
- Implement suitable security measures to mitigate identified risks;
- Document the security measures and their justifications; and
- Ensure continuous, adequate security protections.
What are the consequences of not having a HIPAA risk management plan? The next case.
Case 8: DHH paid $1.7 Million for not managing their security risks
The Alaska Department of Health and Social Services (DHSS) faced several HIPAA violations from the U.S. government in 2012 for risk management failures. As a result, they had to settle the dispute by paying a $1.7 million fine.
During the investigation, OCR discovered that DHSS lacked proper policies and security protocols to protect patient’s health information. Among other things, the main issue was that they had not done a risk analysis or put enough measures in place to manage risks.

9. Not having an incident response plan
The HIPAA security rule requires you to respond with reasonable steps to fix issues or stop a violation if they feel their e-PHI is compromised in any way during an incident. They must promptly address any security measures lapses to ensure patient information is protected.
Imagine facing a data breach without a clear plan. Panic sets in, response times are slow, and the breach could spread further, affecting more patients and potentially leading to legal trouble.
An effective incident response plan ensures timely notification of the breach while enabling measures to minimize its damages.
Case 9: UMMC failed to respond to breaches & paid $2.75 Million
The University of Mississippi Medical Center (UMMC) faced a $2.75 fine for a HIPAA breach involving unsecured ePHIs of approximately 10,000 individuals. The investigations discovered that they knew about risks since long but failed to address them until after the breach.
Furthermore, UMMC did not notify affected individuals whose ePHI was believed to have been accessed or disclosed, causing another violation.
10. Disposing of e-PHI improperly
“Even in our increasingly electronic world, it is critical that policies and procedures be in place for secure disposal of patient information, whether that information is in electronic form or on paper.”
– Director, OCR
When medical records of patients expire their retention date, or they are no longer required, medical institutions are supposed to remove them permanently and securely. By securely, we mean they should not be readable or accessible, regardless if they are digital or paper records.
For hard copies, methods like shredding or pulping may be used and for e-PHI, degaussing, physically destructing portable devices, or data wiping may be used.
Failing to do so may result in expensive violation fines like the ones discussed below.
Case 10: A small pharmacy paid $125,000
Cornell Prescription Pharmacy, a small pharmacy in Denver, settled with HHS for violations of the HIPAA Privacy Rule for improper disposal of PHI. They paid $125,000 as monetary penalties and agreed to adopt a corrective action plan to address deficiencies in their HIPAA compliance.
The Office for Civil Rights (OCR) found that Cornell failed to implement required written policies and procedures on the disposal of patient information. The investigation found documents containing the PHI of 1,610 patients disposed of unsecurely.
Ready to get HIPAA certified? Download our “How to Get HIPAA Certification – A Short 7-Step Checklist!” This easy-to-follow guide breaks down the process into seven simple steps, making your path to compliance straightforward and stress-free.
Download Your HIPAA Certification Checklist
HIPAA violations and fines that follow
HIPAA doesn’t treat all violations the same. Penalties depend on the severity of the violation, whether it was intentional, and the speed with which the organization took steps to rectify the issue. The Office for Civil Rights (OCR) employs a tiered system for civil penalties, with separate punishments for criminal violations.
Here’s a breakdown of how HIPAA enforcement works and what organizations can expect if they fall out of compliance:
Civil penalties (The most common type)
Most HIPAA violations are subject to civil penalties. These apply when an organization fails to follow HIPAA rules, usually due to negligence rather than malicious intent.
OCR uses four tiers:
Tier 1: Unknowing violations
- The organization was unaware and couldn’t have known about the violation.
- Penalty: $100 to $50,000 per violation.
Tier 2: Reasonable cause
- The violation occurred due to a lack of proper precautions.
- Penalty: $1,000 to $50,000 per violation.
Tier 3: Willful neglect (Corrected)
- The organization was aware of the issue and addressed it within a reasonable timeframe.
- Penalty: $10,000 to $50,000 per violation.
Tier 4: Willful neglect (Not corrected)
- The most serious category where the organization was aware of the violation and failed to take action.
- Penalty: Minimum $50,000 per violation, up to an annual maximum of $1.9–$2M (varies year to year due to inflation adjustments).
OCR can assign penalties for every record or action involved, which means fines can stack up and escalate quickly.
Criminal penalties (For intentional misuse)
Criminal penalties apply when someone knowingly obtains or discloses PHI under false pretenses or for personal gain. These are handled by the Department of Justice and can include:
- Up to $50,000 in fines and 1 year in prison for knowingly obtaining or disclosing PHI.
- Up to $100,000 in fines and 5 years in prison if done under false pretenses.
- Up to $250,000 in fines and 10 years in prison if done for commercial advantage, personal gain, or malicious harm.
Beyond fines and prison time, OCR may also require organizations to:
- Enter into Corrective Action Plans (CAPs) that can last for years
- Implement stricter privacy and security policies
- Upgrade technical safeguards like MFA and encryption
- Improve audit logging, monitoring, and incident response
- Retrain the entire workforce
- Strengthen vendor management and BAAs
These actions often cost organizations far more than the fines themselves.
The most significant HIPAA violation fines
To understand how costly HIPAA non-compliance can be, here are some of the most significant fines ever issued and what actually went wrong in each case.
1. Cyberattack and massive PHI exposure: Anthem’s $16M settlement
The largest HIPAA settlement to date was made by Anthem, which paid $16 million after attackers stole credentials and accessed systems containing 78.8 million patient records. The breach went undetected for months. OCR found weak system monitoring and insufficient access controls that allowed attackers to move freely across Anthem’s network.
2. Phishing attack led to $6.85M fine for Premera Blue Cross
Premera Blue Cross paid $6.85 million after a phishing attack gave hackers long-term access to systems storing PHI for 10.4 million people. OCR found that Premera had identified but failed to fix key security gaps, such as unpatched systems and incomplete risk assessments.
3. Poor risk assessments cost Excellus Health Plan $5.1M
Excellus Health Plan paid $5.1 million following a cyberattack that went undetected for over a year and exposed over 9 million records. OCR found that Excellus had not conducted an adequate risk analysis or properly monitored network activity, allowing attackers to operate unnoticed.
4. Repeated privacy failures resulted in a $2.15M penalty for Jackson Health
Jackson Health paid $2.15 million after OCR uncovered years of privacy lapses, including staff accessing patient records without authorization and delays in issuing required breach notifications. The recurring nature of these issues led to a multi-year corrective action plan focused on access monitoring and enforcement of policies.
How to prevent HIPAA violations
Most HIPAA violations stem from the same underlying issues: weak policies, inadequate access controls, missing safeguards, or employees who are unclear about the rules. The good news is that many violations are completely preventable with the right guardrails in place.
Here’s how organizations can strengthen their HIPAA compliance and prevent violations by implementing a combination of administrative, physical, technical, and training-focused measures.
1. Administrative safeguards
These are the foundation of HIPAA compliance and ensure your workflows, documentation, and vendor relationships stay consistent and secure.
Key actions include:
- Conducting regular HIPAA risk assessments to spot vulnerabilities early
- Keeping policies and procedures up to date (privacy, security, breach response, device use, etc.)
- Maintaining proper documentation and following standardized workflows
- Ensuring all Business Associate Agreements (BAAs) are signed and reviewed
- Assigning a clear HIPAA Security & Privacy Officer role
- Having an incident response plan that outlines steps for detection, containment, and reporting
2. Physical safeguards
Physical safeguards reduce the risk of PHI exposure in the real world, whether through lost devices or unauthorized access to workspaces.
Best practices include:
- Securing offices, storage areas, and server rooms
- Using badge access systems and visitor logs
- Locking screens and storing paper records in locked cabinets
- Enforcing clean desk policies
- Implementing secure disposal for paper and hardware (shredding, degaussing, certified destruction)
3. Technical safeguards
This is where most HIPAA violations occur today, especially with the rise of ransomware, credential theft, and cloud-based workflows.
Core technical controls include:
- Enforcing encryption for PHI at rest and in transit
- Implementing multifactor authentication for all PHI access
- Using Role-Based Access Controls (RBAC) to limit who can view what
- Maintaining audit logs and automated monitoring for unusual activity
- Applying regular patching and vulnerability management
- Using secure messaging and file-sharing tools instead of personal apps
- Segmenting networks and enforcing least-privilege access
4. Workforce training
Even the best systems fail if employees don’t know how to use them safely. Ongoing training helps reduce mistakes, prevent phishing incidents, and support a culture of compliance.
Important training topics include:
- How to handle PHI safely in daily workflows
- Recognizing and reporting phishing emails
- Using approved, HIPAA-compliant apps
- Proper device use (e.g., no saving PHI locally, no personal cloud storage)
- What to do when something goes wrong (quick reporting reduces fines)
Steer clear of HIPAA violations with Sprinto
By now, we know that not being compliant with HIPAA and violating its rules can have serious repercussions. In the examples and cases above, we have talked about financial penalties and jail terms, but severe reputational damage also happens.
So if you’re not yet compliant with HIPAA, you should seriously consider it your top priority. And if you are, then you should conduct a HIPAA risk assessment to understand your posture.
Remember:
Compliance shouldn’t get in the way of your business, it should keep up with it.
With Sprinto, you opt in not just to become HIPAA compliant but to stay compliant for the long run. It makes HIPAA compliance easier by automating the checks, reviews, and monitoring tasks that typically slip through the cracks, the same gaps that often lead to violations and fines. With Sprinto AI, you get faster insights, smarter alerts, and proactive compliance support.
Here’s how Sprinto helps:
- Continuous monitoring: Sprinto automatically tracks HIPAA-required controls (such as MFA, encryption, logging, and configurations) and flags issues in real-time.
- AI-powered insights: Sprinto AI identifies risks, recommends solutions, and helps teams resolve compliance gaps before they escalate into violations.
- Automated access reviews: User onboarding, offboarding, and quarterly access checks are run on autopilot, ensuring PHI remains tightly controlled.
- Vendor & BAA tracking: Sprinto identifies vendors, flags missing BAAs, and highlights risky integrations instantly.
- Automatic evidence collection: Logs, screenshots, and training records are gathered in the background so audits are always stress-free.
- Instant alerts for drift: Sprinto notifies you the moment something falls out of compliance, whether it’s a missing safeguard, a misconfiguration, or weak access control.
- Unified compliance dashboard: See your HIPAA posture in real-time, with every requirement mapped and monitored continuously.
FAQs
A HIPAA violation happens when protected health information (PHI) is accessed, used, or shared in a way that doesn’t follow HIPAA’s Privacy, Security, or Breach Notification Rules. This includes things like unauthorized access, improper disclosures, weak security controls, or failing to report a breach on time.
The most common ones include snooping on patient records, emailing PHI through unsecured channels, using non-compliant apps, losing unencrypted devices, falling for phishing attacks, and missing breach notification deadlines.
Consequences can include corrective action plans, financial penalties (from hundreds to millions of dollars), lost trust, operational disruptions, and in extreme cases, criminal charges for intentional misuse of PHI.
Tools like WhatsApp, Gmail, iMessage, SMS, Slack (free tier), and most personal cloud storage apps are not HIPAA compliant unless they offer a Business Associate Agreement (BAA) and proper security safeguards.
If a breach occurs, affected individuals must be notified within 60 days of discovery. Larger breaches also need to be reported to HHS and sometimes the media. Violating these timelines can result in additional fines.
Yes. If an employee knowingly accesses or discloses PHI for personal gain, malicious intent, or under false pretenses, they can face criminal penalties, including fines and jail time.
Yes, if they store, process, or transmit PHI. Vendors must sign a Business Associate Agreement (BAA) and implement the required safeguards. Without this, both the vendor and the covered entity are at risk.
Common HIPAA identifiers are the patient’s phone number, email address, social security number, IP address, account number, and medical record number.
For small companies, the cost of being HIPAA compliant can be around $15,000 to $50,000 and for large companies, it is the cost is up to $200,000. The cost depends on the organization’s type, size, amount of data, employee training, current compliance posture, and the state of IT infrastructure.
Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Explore more
research & insights curated to help you earn a seat at the table.



























