HIPAA-Compliant Data Storage Requirements
Srividhya Karthik
Mar 17, 2024

Healthcare data storage requires stringent rules and protocols given the sensitivity of the patient health information they deal with. The United States Health Insurance Portability and Accountability Act (HIPAA), therefore, defines the general guidelines on best practices for storing and protecting protected health information.
HIPAA’s Privacy, Security, and Breach Notification rules give a fluid overview of the security framework for healthcare organizations to implement a HIPAA-compliant data storage practice.
Wondering what exactly HIPAA-compliant data storage requirements are? We will be discussing all of it and whether your cloud service provider should be HIPAA compliant too, the ramifications of noncompliance, and much more.
What is HIPAA-Compliant data storage?
HIPAA-compliant data storage refers to the data storage practices that organizations need to follow to align with HIPAA requirements to safeguard PHI. In simple terms, it means that the organization’s data storage solution should ensure the confidentiality, integrity, and availability of the data to safeguard it from unauthorized access and theft.
The data storage solutions generally include best practices and measures such as implementing encryption, access controls, and data security policies to safeguard sensitive data.
Go beyond Continuous Threat Identification & Remediation
Why do you need to secure your data as per HIPAA?
You must secure your data as per HIPAA if you are a covered entity (healthcare providers, health plans, and healthcare clearinghouses) or their business associates (vendor, subcontractors, researchers, and hybrid entities) with access to PHI. With the bulk of PHI slowly moving to cloud storage, it gets much more critical for organizations to buttress their security posture.
Note that when a covered entity stores PHI in the cloud, the cloud storage service automatically becomes a covered entity’s business associate (bound by a business associate agreement). HIPAA offers a well-thought-out structure for the implementation of data storage best practices.
Still, wondering why you need to secure your PHI as per HIPAA? Well, for one, HIPAA is enforceable by law. HIPAA is a federal law standardizing best practices to protect patient information, termed protected health information (PHI).
PHI constitutes health information that identifies an individual (such as name, address, and health conditions) and is maintained or exchanged electronically or in hard copy. Such protected health information is protected under HIPAA from being disclosed without the patient’s consent or knowledge.
Two, noncompliance with HIPAA can attract heavy penalties, civil and criminal consequences, and loss of reputation and business. Civil penalties can range from $25,000 to $1.5 million per year, while criminal penalties can include fines of up to $250,000 and 10 years in prison. More on this later.
Three, it increases the risk of exposure of patient data by way of leaks and breaches if you don’t store them in a HIPAA-compliant manner.
For instance, it may open up patients to targeted spam for very profitable fake drugs or an elaborate phishing scam for “laundering” prescription drugs worth a bunch on the black market. When stolen, PHI can lead to identity theft, security breaches, and much more.
Case in point: According to credit rating agency Experian, stolen medical records sell for over $1,000 each on the dark web. In contrast, credit card numbers sell for around $5 each, while social security numbers were available for as little as $1 each.
Data storage in a HIPAA-compliant way adds many checks and balances, such as access control, multi-factor authentication, and data encryption, to ensure PHI doesn’t get compromised or leaked easily.
Also find out: HIPAA rules that every software must adhere to
What are HIPAA data storage requirements?
The US Department of Health and Human Services has defined four main HIPAA storage requirements under the Security Rule to comply with the regulation. These include:
- Organizations must ensure the confidentiality, integrity, and availability of ePHI by implementing various security measures such as strong encryption, password protection policies, and so on.
- Organizations should conduct regular risk assessments and data monitoring to identify and safeguard data against potential security threats.
- Organizations must protect PHI against unauthorized physical access or disclosures by implementing the necessary IT security policies and access controls and performing regular data security audits.
- Organizations should conduct regular training sessions so that the staff adheres to the HIPAA rules and regulations to prevent any data storage security lapses.
Get HIPAA compliant without the stress
How does HIPAA apply to data storage?
Unlike other industries that can get away with a slap on their wrist in case of a data breach, the ramifications for the healthcare industry can get somewhat serious. As we mentioned earlier, HIPAA violations can cost money, and PHI leaks can cause irreparable damage to patients and healthcare organizations.
Know that the guidelines for proper HIPAA data storage cover both digital and physical checks that healthcare organizations can implement to secure PHI. Depending on the size of the organization, its capabilities, the costs of the specific security measures and the operational impact, organizations can implement their security measures.
So, while picking your cloud service provider (CSP), look for HIPAA-compliant ones. Here’s a look at some of the HIPAA-compliant data storage requirements.

HIPAA requires healthcare organizations to store PHI on a redundant, isolated, secure database and web servers. Other physical safeguards include limited facility access, access controls, policies for access and use of workstations, and restrictions on the transfer, removal, disposal, and/or reuse of electronic media and electronic private health information.
Note that the BAA must clearly call out the shared as well as individual responsibility in securing stored PHI.
Also check: HIPAA data retention requirements for medical records
How do the HIPAA Rules affect data storage services?
There are three rules within HIPAA that apply to data storage: the privacy rule, the security rule, and the breach notification rule.
But before we dive into how these rules apply to data storage, let’s quickly get an overview.
Privacy Rule: The Privacy Rule sets the standards for those who may have access to PHI to establish the integrity of PHI and protect it from unauthorized access (alteration and destruction). It applies to PHI, which may be in electronic, oral, and paper form, and grants patients control over their data and medical records.
Security Rule: The Security Rule sets the standards for ensuring that only those who should have access to EPHI will have access. Data storage operations fall under the Security Rule. The Security Rule, as per HIPAA, is based on the fundamental concepts of flexibility, scalability and technology neutrality.
Breach Notification Rule: The Breach Notification Rule defines the actions healthcare organizations must take in case of a data breach or leak. It defines the timeframes and methods for disclosure to government officials and the media.
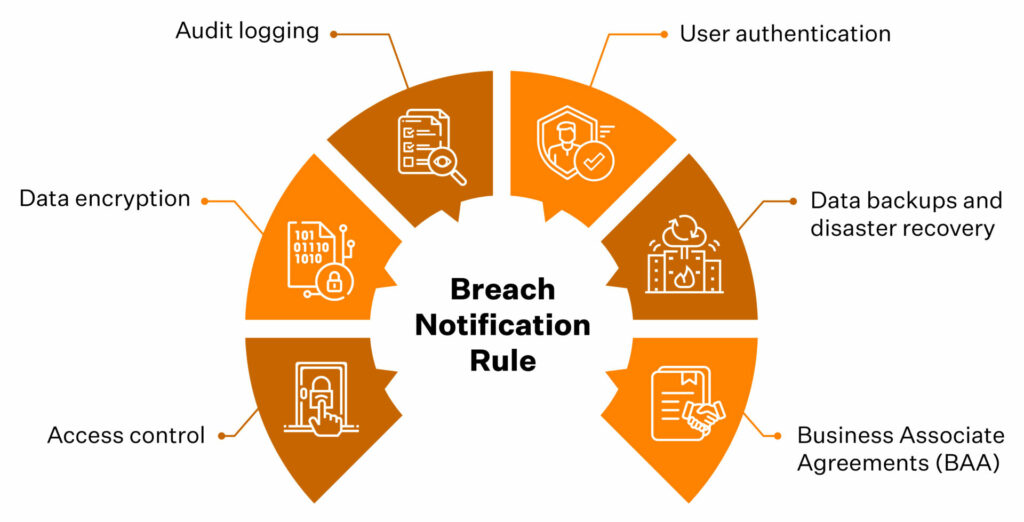
Broadly, HIPAA requires healthcare organizations to implement these cybersecurity measures to ensure compliance:
HIPAA file storage as per the privacy rule
HIPAA requires covered entities and business associates to maintain reasonable and appropriate administrative, technical, and physical safeguards to prevent intentional or unintentional use or disclosure of PHI. Some of these safeguards under HIPAA-compliant file storage as per HIPAA privacy rules include shredding PHI documents before disposal, securing them with a passcode, and limiting access using access control.
PHI and ePHI must be stored in a way to:
- Restrict their access and use
- Facilitate access and use cases that are required
- Implement minimum necessary disclosure
These requirements have a bearing on the locations and configurations for storing PHI and ePHI, as organizations must closely monitor access to ensure it’s permitted or required. Note that HIPAA-compliant cloud storage must also incorporate all the required controls to ensure the confidentiality, integrity and availability of ePHI.
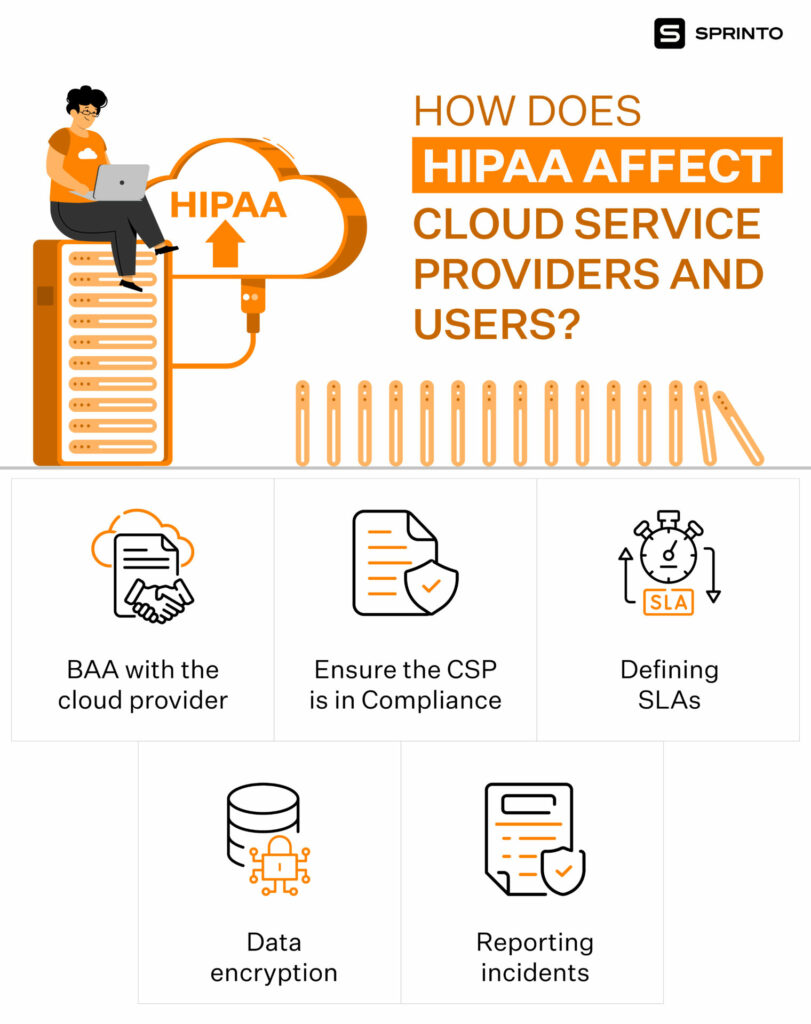
HIPAA file storage as per the security rule
The HIPAA compliant file storage as per Security Rules requires three kinds of safeguards: administrative, physical, and technical. Organizations are free to design their program around these three safeguards.
Administrative safeguards: These constitute the administrative functions that must be implemented to meet security standards. They include assignment or delegation of security responsibility to an individual and security training requirements, among others.
Physical safeguards: These constitute mechanisms to protect electronic systems, equipment and the data they hold from threats, environmental hazards and unauthorized intrusion. They include restricted access to EPHI, key fobs, passcodes, and retaining off-site computer backups. It also covers protocols surrounding data backups and data disposal.
Technical safeguards: These constitute automated data protection and access control processes. They include authentication controls, strong passwords, periodic data audits, and encryption and decryption of data when it is stored and/or transmitted.
Since the security rule is based on technology neutrality, HIPAA doesn’t identify any specific types of technology. So, the covered entity or business associate must determine the security measures and the specific and appropriate technologies for implementation.
For instance, let’s look at the specifications underlined for access control. Access control should grant authorized users access to the minimum necessary information to perform job functions. It must grant rights and privileges to authorized users based on a set of access rules that the covered entity implements.
The four implementation specifications associated with the Access Controls standard include:
1. Unique User Identification (Required) – A unique user identifier allows an entity to track specific user activity. This helps hold users accountable for the functions performed on Information Systems with ePHI when logged into those systems.
2. Emergency Access Procedure (Required) – Covered entities must determine the situations requiring emergency access to an information system or application containing ePHI.
3. Automatic Logoff (Addressable) – Automatic logoff helps prevent unauthorized users from accessing ePHI on workstations left unattended for some time.
4. Encryption and Decryption (Addressable) – Encryption allows organizations to convert PHI into encoded text such that it can be decrypted only by authorized users with a decryption key. HIPAA requires PHI data to be encrypted in storage and transit.
Note that required safeguards are necessary, and addressable safeguards are optional, provided the organization can justify the decision. It is advisable to implement the addressable measures as they are HIPAA best practices.
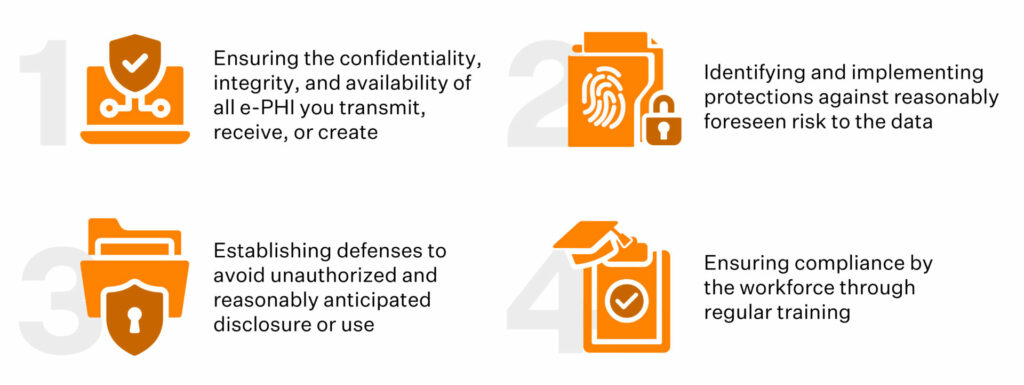
The security rule, on the whole, makes allowance for four specific HIPAA storage requirements:
HIPAA Compliant File Storage Breach Notification
The breach notification rules make it mandatory for organizations to notify the government and media on nearly all occasions of a breach. There, however, are a few exceptions:
- Encrypted data that’s been breached but is encrypted to the standards of HIPAA
- Breach by way of access to (authorized or not) or use of information, which was done in good faith and not further used unlawfully
- If the unauthorized person wouldn’t have been able to retain the information
What would be the penalty if the data is stored incorrectly?
As we mentioned earlier, HIPAA recognizes that each covered entity is unique and varies in size and resources and that there isn’t a fully secure system. So, the penalties for noncompliance are a function of the level of negligence.
We can divvy HIPAA fines and charges into two categories: Reasonable Cause and Willful Neglect. While the penalties for reasonable cause range from $100 to $50,000 per incident (doesn’t involve any jail time), the fines for willful neglect range from $10,000 to $50,000 for each incident (can also result in criminal charges).
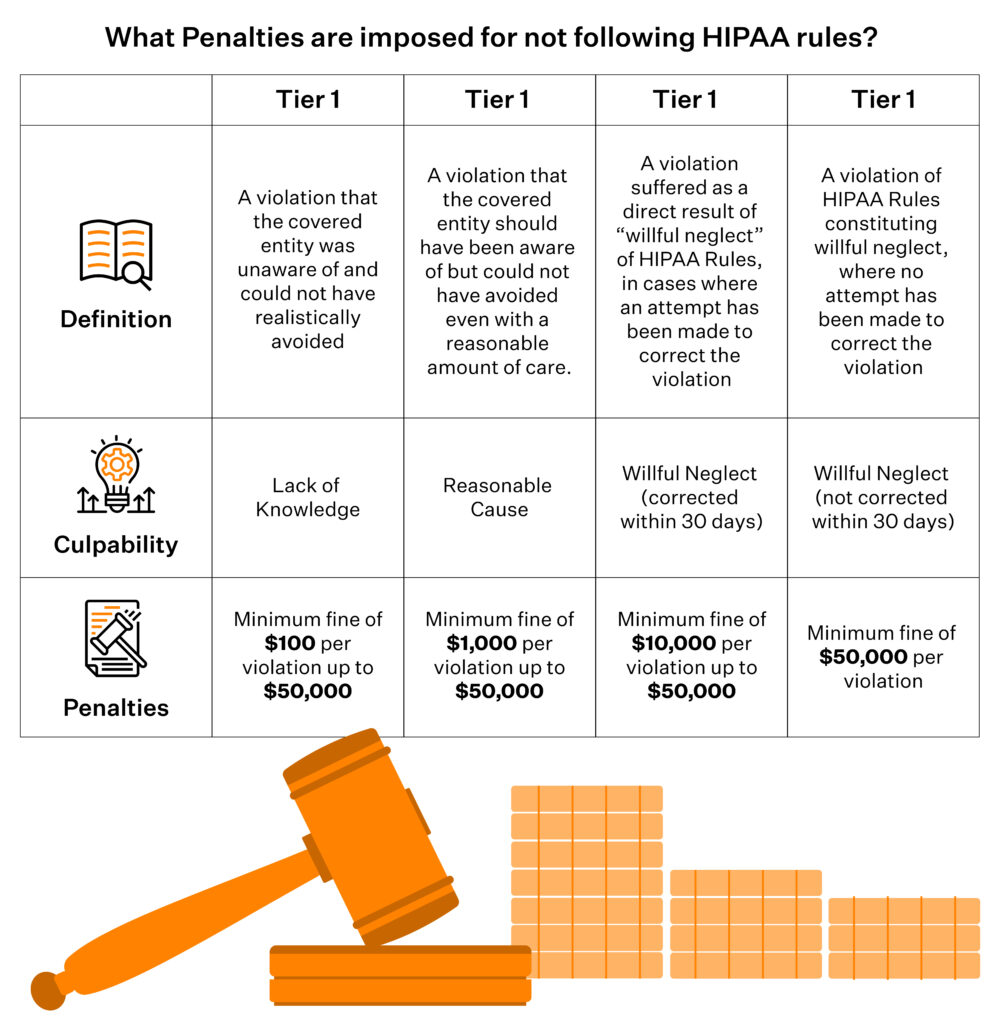
If an organization carries out HIPAA violations, the State Attorney General may impose fines of up to $25,000 per year per violation category, and the Office for Civil Rights (OCR) can impose fines of up to $1.5 million per year per category of violation. Individuals who violate HIPAA can also face fines and criminal penalties of up to 10 years in prison.
Find out what Sprinto recommends when it comes to HIPAA-compliant data storage and security
Sprinto has a comprehensive security controls’ list that takes from the security best practices across frameworks such as HIPAA, SOC 2, ISO 27001 and NIST. So, when you work with Sprinto for your HIPAA compliance, your security protocols measure favourably against the best of the best.
Join Sprinto’s 450+ satisfied compliance conquerors
So, if you are a business associate with a cloud-hosted business, Sprinto’s automated compliance platform can help you get HIPAA compliant in an easy and error-free way. Armed with in-app features to monitor your HIPAA safeguards and vendors to conduct staff training, Sprinto offers a quick, reliable and effortless way to become and stay HIPAA compliant.
Talk to us today to learn about how to automate your compliance with HIPAA.
FAQs
Where should confidential documents be stored?
Confidential data and documents should be stored on redundant, isolated, secure databases and web servers. Also, the physical copies should be stored in a secured room under surveillance with access controls.
Can HIPAA data be stored in the cloud?
Yes, organizations can store ePHI in the cloud if they have a Business Associate Agreement in place. However, the organization needs to follow the same HIPAA security requirements for safeguarding ePHI that they would have followed to secure the ePHI on-premises.
Srividhya Karthik
Srividhya Karthik, is a Content Lead at Sprinto, she artfully transforms the complex world of compliance into accessible and intriguing reads. Srividhya has half a decade of experience under her belt in the compliance world across frameworks such as SOC 2, ISO 27001, GDPR and more. She is a formidable authority in the domain and guides readers with expertise and clarity.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


