Top 5 Components of HIPAA
Anwita
Feb 06, 2024

The Health Insurance Portability and Accountability Act of 1996 (HIPAA) ensures that health service providers i.e Business Associates (BA) and Covered Entities protect PHI (Protected Health Information) while offering healthcare services.
In this article, we discuss the main components of HIPAA and how each serves the purpose stated above.
What are the Components of HIPAA?
The components of HIPAA comprise five titles to serve multiple purposes and address issues concerning patients and healthcare workers.
It protects healthcare workers who change or lose their jobs with continued insurance, secures patients’ private medical data and standardizes the flow of medical information.
Title I: Health Care Access, Portability, and Renewability
The health insurance reform of HIPAA aims to protect healthcare workers and their families when they change their employment or lose their job. It requires insurers to issue policies to individuals leaving group plans and provide alternate plans for discontinued plans.
This reform prevents health plans from denying or limiting coverage due to pre-existing conditions and regulations such as the Employee Retirement Income Security Act of 1974 (ERISA).
ERISA guides employers to manage benefit plans but does not require them to offer benefits. The Tile I of HIPAA fills this gap with regulations centring around continuous coverage after employment change.
Long-term health care plans, dental, vision, or other limited plans are exempted from Title I requirements.
Title II: Administrative Simplification
HIPAA administrative simplification requires healthcare providers to standardize the process of healthcare transactions across the country. In addition, it offers various programs to prevent fraudulent practices within health care.
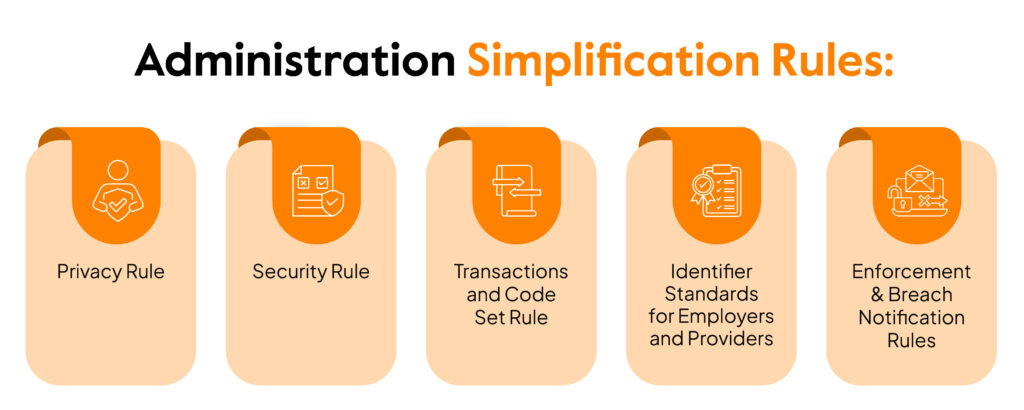
Established and published by the U.S. Department of Health and Human Services (HHS), it seeks to protect the security and privacy of Protected Health Information (PHI). It covers five rules that include:
Privacy Rule: Lays out the standards to protect medical records and PHI. It sets limits and conditions on how to use and disclose PHI data without permission from the owner.
Security Rule: Lays out standards to protect ePHI (PHI in electronic form) that is created, transmitted, stored, and used by covered entities. It requires PHI handlers to implement physical, technical, and administrative safeguards to ensure the security of ePHI.
Go beyond Continuous Threat Identification & Remediation
Transactions and Code Set Rule: Health plan providers or care providers who transfer health information must comply with this standard. It requires them to use a national standard code set to identify diagnoses and procedures to standardize the exchange of PHI.
Identifier Standards for Employers and Providers: Requires employers to have an Employer Identification Number (EIN) to help identify them on standard transactions.
Enforcement & Breach Notification Rules: Enforces security and privacy laws through corrective actions. Covered entities must notify with the required details in event of unauthorized disclosure of PHI.
Also, read more on the HIPAA breach notification rule
Title III: Tax-Related Health Provisions
This title provides guidelines for standardizing pre-tax medical expenditure accounts and comprises updates in regulations related to insurance. It applies to small medical businesses or self-employed individuals and covers the medical plans they offer.
Title IV: Application and Enforcement of Group Health Plan Requirements
Title IV outlines group health plans for individuals with pre-existing conditions requiring continuous coverage. It also offers clarification of continuous coverage requirements and the Consolidated Omnibus Budget Reconciliation Act of 1985 (COBRA).
Title V: Revenue Offsets
Offers provisions that center around life insurance provided by businesses. It includes the treatment of patients who have lost their citizenship and includes ex-citizens in the public record. Additionally, it repeals the financial institution rule to the interest allocation rule.
Conclusion
Lost in piles of compliance documents? Don’t know where to start but want full compliance?
Sprinto is designed to enable Business Associates to implement custom policies and controls and assists them with an automated solution. It breaks down your requirements into simple steps and continuously monitors the environment for non-compliance. In addition, it trains your employees to offer a holistic approach to compliance by combining people and processes.
Continuous compliance is the next big thing! Get there first with Sprinto
Talk to us today to kickstart your HIPAA compliance journey.
FAQs
What is the key concept of HIPAA?
HIPAA aims to protect patients’ medical records and data by implementing standards that guide covered entities securely use and disclose protected health information (PHI).
What are the primary aspects of HIPAA?
The key aspects of HIPAA are administrative safeguards (policies and processes to manage and secure PHI), physical safeguards (physical measures and procedures to secure electronic systems containing PHI from natural or environmental disruptions), and technical safeguards (technology or policy to secure PHI).
Anwita
Anwita is a cybersecurity enthusiast and veteran blogger all rolled into one. Her love for everything cybersecurity started her journey into the world compliance. With multiple certifications on cybersecurity under her belt, she aims to simplify complex security related topics for all audiences. She loves to read nonfiction, listen to progressive rock, and watches sitcoms on the weekends.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


