
Vulnerability & Risk Management: Not the Interchangeable Words We Think They Are
When it comes to asset protection, two terms crop up in the boardroom conversation: vulnerability management and risk management. Even though the two may seem like synonyms frequently used in the same contexts, they refer to different methods of tackling security issues. It is important to note that vulnerability management is about concentrating on the…
Jan 21, 2025
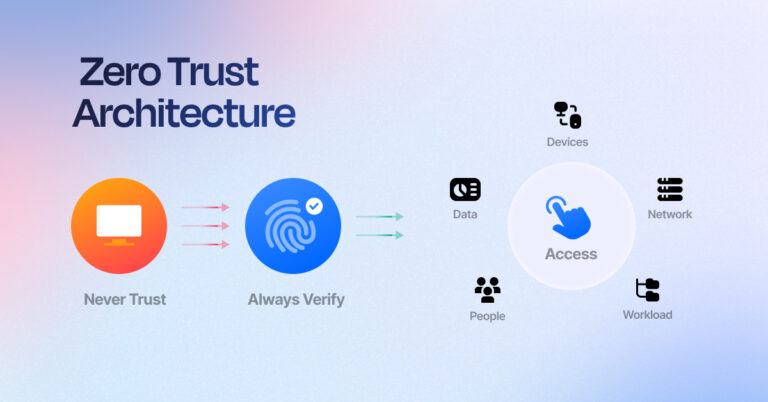
Rethinking Trust: How Zero Trust Architecture Redefines Cybersecurity
“Murphy’s Law has a way of creeping into things, and it does so in cybersecurity too—’Anything that can go wrong, will go wrong.’ And lately, every marketer and tech vendor has taken this as their cue to sell you their version of ‘Zero Trust.’ Flashy tools, big promises, and buzzwords galore. Zero Trust isn’t about…
Jan 17, 2025

Ransomware as a Service: Cybercrime’s New Business Model
Let me paint a picture for you: a world of cybercrime where instead of elaborate heists, people can buy goods that can freeze entire businesses. That is not a fantasy or an imaginary future shown on Black mirror, it is Ransomware as a Service (RaaS). These are the dark web enterprises that are offering prepackaged…
Jan 03, 2025

Build Your Vendor Risk Management Framework Now: Because ‘Too Late’ Hurts
There are very few names with as much authority in the financial sector as Bank of America. Ironically, though, this colossus was in a precarious position. In November 2023, cybercriminals made 57,000 BofA customers’ data public. The cause? It was a breach of Infosys McCamish Systems, the vendor, rather than an attack on their systems….
Jan 02, 2025

When Crisis Strikes, Be Ready: Creating a Business Continuity Policy That Works
In March 2024, AT&T experienced a massive data breach affecting 73 million customers. This incident has prompted companies across various sectors to reassess their continuity and disaster recovery strategies, underscoring the critical importance of having a robust business continuity plan in today’s digital landscape. The breach that exposed users’ sensitive information, including SSNs, passcodes, and…
Jan 02, 2025
Cybersecurity Audit: What Is It and How to Conduct One?
Technology has made significant advancements in just the last decade as we went from smartphones to smart homes. We’re more connected than ever before but we’re also more vulnerable than ever before. Cyberattacks occur every 39 seconds on an average, affecting 1 in 3 Americans every year. That’s why cybersecurity has had a paradigm shift…
Jan 02, 2025