
Cybersecurity Maturity Model Certification (CMMC) Compliance Guide
Your organization’s data is perhaps your most valuable asset. Protecting its security, confidentiality, and integrity is key to keeping your organization safe. This need to preserve information gets even more pronounced when you work with the Department of Defense (DoD), the United States of America, which values Cybersecurity Maturity Model Certification (CMMC) Compliance. The CMMC…
Jan 18, 2025

StateRAMP Compliance: Process, Requirements, Benefits
Like all organizations, government agencies use cloud solutions. StateRamp provides a ‘verify once, serve many’ model for these agencies to trust their third-party service providers. In this article, we’ll learn all about StateRAMP, including who requires it, who its members are, the compliance process, its security statuses, and its benefits and challenges. TL;DR Compliance with…
Jan 17, 2025
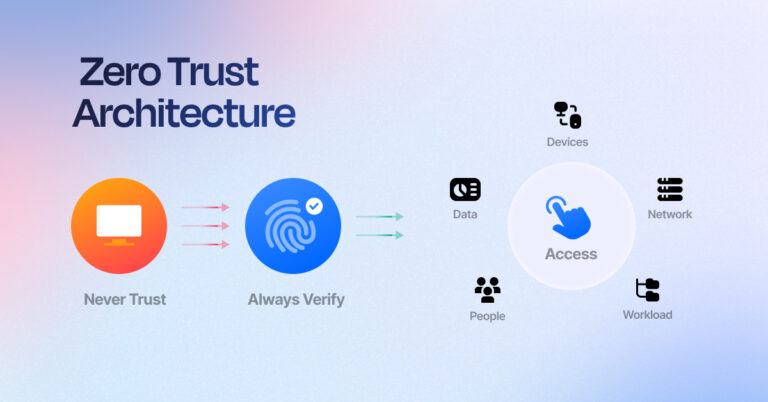
Rethinking Trust: How Zero Trust Architecture Redefines Cybersecurity
“Murphy’s Law has a way of creeping into things, and it does so in cybersecurity too—’Anything that can go wrong, will go wrong.’ And lately, every marketer and tech vendor has taken this as their cue to sell you their version of ‘Zero Trust.’ Flashy tools, big promises, and buzzwords galore. Zero Trust isn’t about…
Jan 17, 2025

10 Best ERM Software Review
Back in August 2021, fast food giant KFC failed to meet their meat demands and had to take down menu items due to supply chain disruptions. In 2018, they shut down 900 UK outlets after delivery issues – all due to poor risk visibility. While such incidents cannot be fully avoided, it can be minimized…
Jan 16, 2025

What Is Risk Control: Types, Example & Identification
Risk control is important for any kind of business. It safeguards your company’s assets while maintaining sustainable growth. But how effectively are you managing risks in your business? Are you following the essential control measures to eliminate and manage your cyber threats and vulnerabilities? The current threat landscape is volatile, and mastering how your risk…
Jan 16, 2025

Protecting What Matters: Cybersecurity for Critical Infrastructure
There’s a saying—if you can access something remotely, so can hackers. The increasing connectivity and convergence have, on one side, diminished physical perimeters, for the good. But they have also brought an increased influx of new threat classes. When it comes to critical infrastructure, though, the stakes are much higher—disruptions can impact essential services and…
Jan 16, 2025