A Guide to PCI DSS Risk Assessment
Gowsika
Jan 05, 2024

Risk assessment is critical to comply with the Payment Card Industry Data Security Standards (PCI DSS). It helps organizations identify and mitigate threats to cardholder data.
As we know, PCI DSS is a set of security compliance standards developed by the PCI Standard Security Council to protect cardholders’ data; hence, it is mandatory for all businesses dealing with cardholder data to perform a PCI DSS risk assessment regularly. Failure to comply may cost them hefty penalties.
This guide will provide an overview of the PCI DSS risk assessment and how it helps achieve compliance.
What is PCI DSS risk assessment?
PCI DSS risk assessment is a requirement under PCI DSS compliance that requires organizations to identify potential threats and vulnerabilities that could compromise the cardholder data.
According to the PCI DSS requirement 12.2, any organization that processes or handles cardholder data must perform the risk assessment annually or whenever there are significant changes in the card data environment.
The risk assessment typically involves identifying all systems that process cardholder data, detecting potential threats or security gaps, and helping mitigate them effectively.
What does a PCI risk assessment policy include?
The PCI risk assessment policy consists of precise guidelines to manage and mitigate risks effectively. Some of the categories the policy should include are listed below:
Scope: The scope of the policy defines the individuals and systems on which the policy will be applicable. It generally includes the information systems, servers, databases, processes, and the individuals or people involved in the handling of the cardholder data.
Roles and responsibilities: These include the roles and responsibilities of the individual involved in the risk assessment process, such as conducting the assessment, analyzing, and reporting.
Methodologies: It describes the methods, tools, and techniques used for conducting the risk assessment, the risk scoring criteria, and the mitigation strategies. The techniques generally involve penetration testing, gap analysis, and internal/external vulnerability scans. The risks are categorized based on severity and addressed accordingly.
Scheduling: It includes a schedule for conducting regular assessments to identify and address risk on an ongoing basis.
Reporting: The reporting section consists of requirements such as the reporting format, the frequency, and the individuals involved in carrying out the PCI DSS risk assessment. The report generally includes the executive summary, scope, risk assessment methodology, threats and vulnerabilities identified, and results (actions taken to mitigate threats).
How to conduct PCI DSS risk assessment?
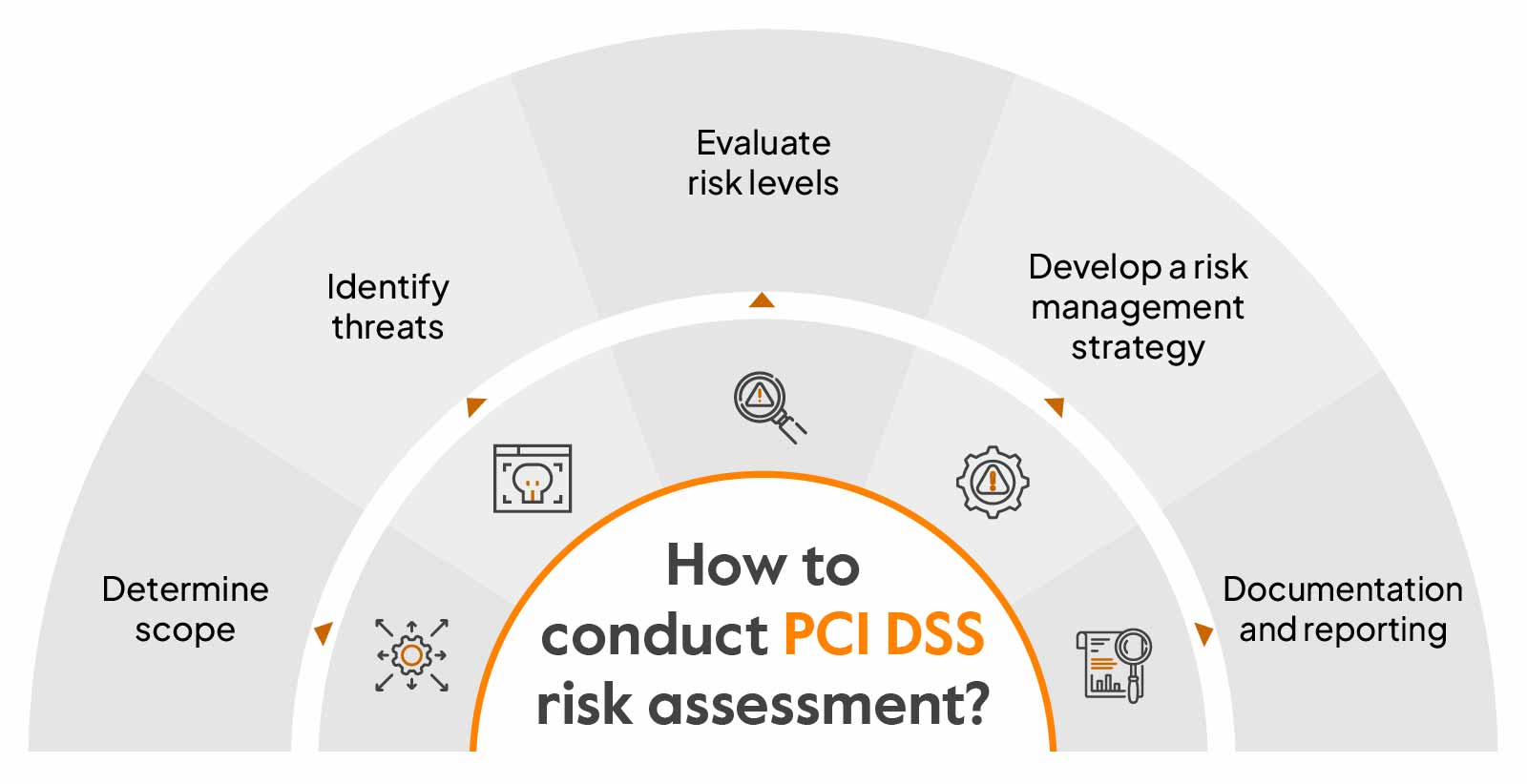
The PCI DSS standard doesn’t specify any particular steps to conduct the PCI DSS risk assessment. However, you can follow these five general steps to identify and manage risks:
Determine scope
The first step before performing a risk assessment is to determine your scope by identifying areas you need to secure. To map out the scope, you need to consider all assets, such as the processes, people, and systems that are involved in the process and transmit cardholder data.
Identify threats
Your next step is to identify potential threats and vulnerabilities that includes assessing people, processes, and technologies. You need to consider all factors that are involved in the transmission and storage of data, such as internal, external, digital, physical, and environmental vulnerabilities, that can affect the cardholder data environment.
Evaluate risk levels
Analyze identified risks based on likelihood—the probability of the risk occurring and potential impact on the cardholder data. Rank each risk based on the potential impact or severity.
Develop a risk management strategy
Develop an effective risk management strategy that covers how to address the identified risks, the tools and techniques required to mitigate them, strategies for implementing security controls, and initiatives for improving the existing risk management process.
Documentation and reporting
Have a team set up to monitor and document the risk assessment processes regularly. The document should include the summary, scope, risk assessment approach, threats, vulnerabilities, and risk assessment results, and it should be reviewed adequately to ensure compliance.
If you are still interested, here is a downloadable template that you can refer to:
Download your PCI DSS Risk Assessment Report
Who should be performing PCI DSS risk assessment?
Any cloud-hosted organization that processes, transmits, or stores payment card information should be performing PCI DSS risk assessment. It needs to be performed at least once every year as per the PCI guidelines.
The risk assessment can be performed by your internal risk assessment team by following the standard policies. You can also outsource this process to an external risk assessor to identify threats and vulnerabilities and fix them.
Why is conducting PCI DSS assessment important?

Conducting PCI risk assessment establishes a security foundation to avoid potential breaches. It is not only about following the security standard but about protecting crucial data and creating a safe cardholder environment. Let’s have a look at why it’s important:
Helps you prioritize security: Risk assessments help identify the cardholder data that is not fundamental for business operations and can be removed from an organization’s environment and enables you to prioritize data that need protection, saving you from unnecessary investments and giving you a better scope.
Helps establish best practices: Conducting risk assessments regularly gives you insights into mitigation strategies and helps you stay compliant continually. This would also give you an idea of resources you should invest in for effective mitigation.
Protects you from data breaches: Performing a PCI DSS risk assessment helps you identify and understand the potential risks and enable you to implement needed security controls and also helps enhance employee awareness of security risks and strengthens the security infrastructure, and safeguards you from potential data breaches.
Protects you from financial risks: Non-compliance with PCI DSS could cost you hefty penalties and consequences. Conducting risk assessment helps you stay compliant and prevents you from legal risks that you cost your reputation.
Simplify PCI Risk Assessments with Sprinto
To sum up, PCI risk assessment can help you proactively identify vulnerabilities and address them before being acted upon by hackers. The PCI DSS risk assessment process can be daunting, but bypassing it puts you in danger, costing you both money and credibility.
The most effective way to ease your PCI DSS risk assessment process is automating PCI risk assessment with a compliance automation solution like Sprinto.
A comprehensive platform like Sprinto can help you streamline compliance and get organizations, irrespective of size and complexity, audit-ready quick. Don’t believe us? See for yourself. Book a demo.
FAQs
What is the PCI DSS requirement for risk assessment?
The PCI DSS requires all organizations that process and handle payment card data to conduct a formal risk assessment annually when there are significant changes in the cardholder data environment. The assessment should identify potential threats and vulnerabilities and assess the security controls involved.
Does PCI require risk assessment?
Yes, As per the PCI DSS requirement of 12.2, all organizations that handle payment card data must conduct a risk assessment.
When to do PCI risk assessment?
You should conduct a PCI risk assessment once a year or whenever you make any significant changes to the cardholder data environment. You also need to do a risk assessment before you outsource any part of the CDE to a third party.
Gowsika
Gowsika is an avid reader and storyteller who untangles the knotty world of compliance and cybersecurity with a dash of charming wit! While she’s not decoding cryptic compliance jargon, she’s oceanside, melody in ears, pondering life’s big (and small) questions. Your guide through cyber jungles, with a serene soul and a sharp pen!
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


